// NEWS // Government Cookies Have Been Discovered on Google Play
An Italian spyware was distributed on the application store, probably as part of interceptions. But questions arise about this system’s legality.

Source
That governments use Trojan horses to conduct administrative or judicial tapping, we already knew and it is quite legal. However, that they use Google Play to distribute them is new. The association Security Without Borders (SWB) has detected on this application store a spyware program called Exodus, which has clearly been used by the Italian law enforcement agencies.
This malware is hidden under the innocent airs of a marketing promotion application or utility software. Once installed, this fake application downloads a second software that will hack the phone and siphon its data. It can, among other things, access the call and navigation history, the calendar, the address book and the data of various couriers. It can also start audio recordings.
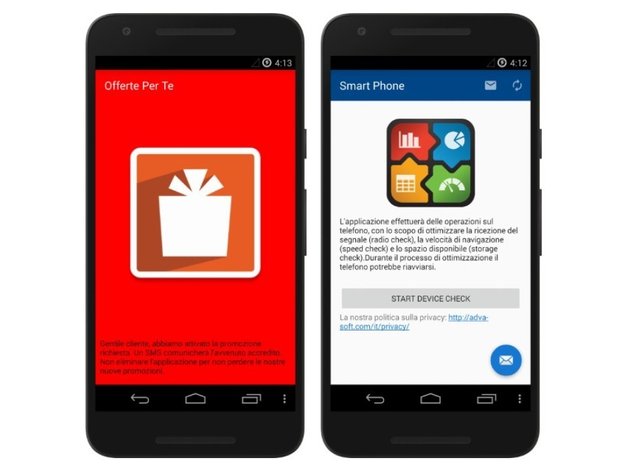
Security Without Borders -
SWB researchers have found almost 25 different versions of Exodus on Google Play over the last two years. The technical analysis of this malware reveals that it was developed byeSurv, an Italian company that was originally specialized in video surveillance and would have started the intrusion software’s development in 2016.
Public documents show that the company has in the past won a call for tenders from the Italian police to create an "active and passive interception system". It received, for this work, a payment of 307.439,90 euros in November 2017.
Contacted by researchers and by Motherboard, Google did not specify the exact number of installations related to these Trojans, but still reported that it was between 350 and 1000, all in Italy. It's weak and it's normal, because state spyware is usually used for targeted attacks. What is less normal is the way this interception software works.
According to a Motherboard source, operators first put it on Google Play before prompting the victim to download it. In a way, the Google store served as a guarantor not to raise suspicion with the user.
Illegal operation
Another problem, this software did not target its victims correctly. Tests conducted by SWB have shown that the spy software is automatically downloaded to any terminal. In addition, the malicious program opened a port through which operators could access a shell interface. But in reality, this access was open to anyone: there is no authentication or encryption.
In other words, Exodus risked not only innocent victims, but also significantly degraded their security level. Which cannot be in the legal interception’s interest. According to the experts interviewed by Motherboard, this way of doing things would even be illegal under the Italian law.
Contacted by SWB and Motherboard, eSurv officials did not comment. For its part, Google has removed all instances of Exodus.

I've made a lot of articles with tools, explanations and advises to show you how to protect your privacy and to secure your computer, GO check them out!
This is my guide to secure your PC after a fresh installation of Windows
If you think that your phone or your PC has been hacked, you have to check it right now!
That's how you can be more Anonymous on the internet!
The future of Cyber-Security, what to expect?
The best crypto debit card – Wirex!
These are the best VPN to protect your numeric life: NordVPN, ExpressVPN and CyberGhost!
Your PC is slow? That's why!
Why is it important to be discreet on the Internet
Feel hot? Your computer also!
How an adware works?
That's how you should guard against Trojan!
What are the different types of hackers?

Thanks for this post, a lot have been going on the internet lately,that is one needs to update is Cyber protection knowledge
The knowledge is the only key to protect as mush as possible his numeric life.
Decentralization and FOSS needs to be gain more introduction and usage by people. That seems to be the only solution. Centralization makes only problems.
The next global economic crisis will help the decentralization of a lot of things. Sadly, only crisis can change an entire way of working.