That's how you can know if you have been hacked or to prevent further attacks
There are 18 victims of cyberattacks per second, 30.000 hacked websites a day, 6000 new viruses a month, and approximately 87 days to realize that we have been hacked.
I don’t think I need to remind you that cyber-threats must be taken very seriously. You have to be proactive and do everything possible to avoid of being hacked, but you also have to be reactive and know how to immediately detect a problem. This is the purpose of this article.
HERE ARE SOME SIGNS THAT SHOULD MAKE YOU REALIZE OF A POTENTIAL HACKING:
Direct signs
These signs should put you in an emergency. Here are the main ones:
• Account suddenly inaccessible (using the usual password)
• Mouse cursor or graphic elements that move "on their own"
• Direct message from hacker or malicious program (ransomware)
• Unauthorized and/or unknown purchases from your bank account
• Unusual activities on an account such as a post on your behalf (ex: on Facebook)
Indirect signs
These signs are not necessarily obvious to spot and do not necessarily mean that you have been hacked. Here are the main ones:
• Suspicious account access (generated alert email)
• Computer suddenly slow at startup
• E-mails marked as read without having read them
• Click on a program that has no effect or leads to an error
• Deleted, moved, renamed files
HOW TO KNOW IF YOU ARE HACKED IN 6 STEPS:
Here are 6 investigation steps that will allow you to know for sure if you are hacked. Don’t miss the 6 one, it’s the most effective 😉.
I will do an example simulation at the same time.
1. Observe network activity of programs
Usually, malicious software will seek to communicate with the outside world, either to receive orders or to send stolen informations.
The problem is that a lot of software also communicate legitimately. So we have to understand the network activity and know how to extract the content that interests us.
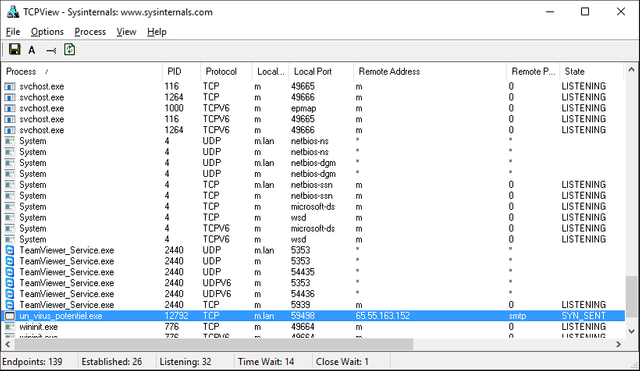
For that, you can install TcpView, and launch it to observe the programs on your computer that communicate with the outside:
Obviously, a program that appears to be a virus has made a network connection with the following remote address: 65.55.163.152.
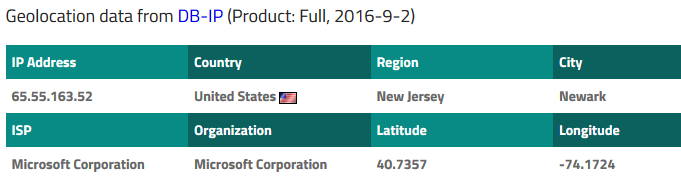
By looking at iplocation.net, we see that the address belongs to Microsoft:
But what is Microsoft doing here?
In fact, in the column "Remote Port", we see "smtp", meaning that the program in question has just sent an email probably using a Microsoft account.
There are distinct reasons (malicious or not) to send an email, a keylogger could for example send your personal information to a hacker.
2. Observe the history of downloaded files
This is the first thing to do if you suspect a program of being the source of hacking. The history of downloaded files is usually accessible through the web browser. It normally memorize the download date and the place where the program was stored on the computer.
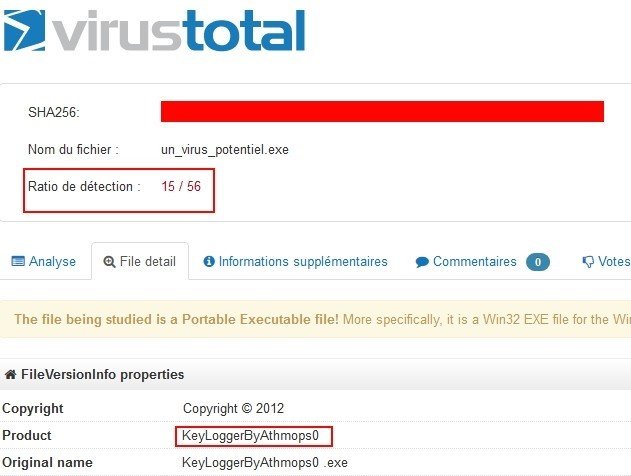
If you spot a suspicious program, do not delete it immediately, but scan it with VirusTotal and/or Malwr:
Bingo, this is a keylogger.
3. Track a hacker
Hackers are not always as smart as people think. Some use the tools of others without even knowing how they work. This suits us well, because we can potentially find the author of a malicious program, provided that we have already identified the program in question.
In this case, we can find the coordinates of the pirate ... in his own program.
Here is an article that talks about it.
4. Observe the logs
Logs are automatic records of the state of certain software, or the system. For example, if a software starts to crash, a message will probably be written in the logs indicating the time of the crash and perhaps even the reason of it.
Logs do not only record error messages, but contain other valuable information, such as computer boot time, installed programs, launched programs ...
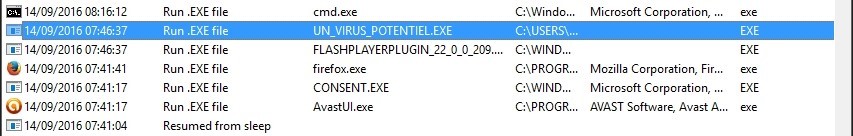
So, to a certain extent, you can remonstrate the history of the computer with this program: LastActivityView
Re-Bingo, it seems that a certain "potential virus" launched at the same time as Flashplayerplugin, about 5 minutes after starting the computer:
Far from us the idea to accuse Flash Player of trying to hack us, but it seems rather that a malicious program is hidden in the plugin, if it’s already the real Flash Player plugin.
Speaking of that, I wanted to mention the site haveibeenpwned which allows you to enter your e-mail address to determine if a site on which you registered with your e-mail address has been hacked in the past.
5. Observe the processes
This is a straightforward way, quite complicated for a novice, to observe the programs launched on the computer at a given moment.
Here, we have already spotted the name of the malicious program, but we could have done it with a task manager. I say "a" task manager because there are several, and even if the one delivered by default with Windows is sufficient in most cases, there are advanced task managers like Process Explorer. The term "advanced" refers to the additional features that this tool brings.
With for examples the direct VirusTotal analysis, signature verification, more pleasing graphics, and (very) detailed information about each process.
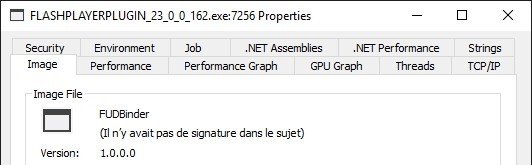
Here is what can be observed by displaying the properties of the program supposed to be Flash Player Plugin:
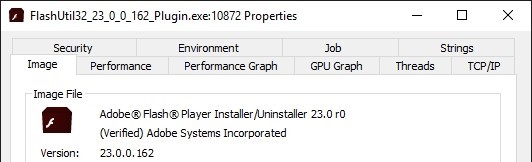
And here's what the properties of a real Flash program look like:
The "Verified" indication indicates that the program signature has been verified. In short, when the program is published, the publisher digitally signs it. This signature can then be verified by an authority. And the slightest change in the program directly invalidates the signature, indicating at the same time that the program is not authentic.
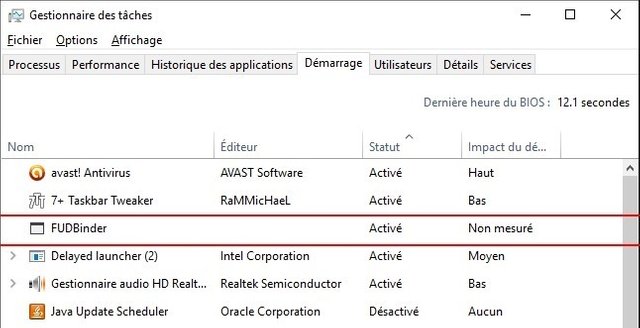
6. Watch programs started at startup
This is one of the most effective ways to detect malware. We could have placed it first, but the order does not necessarily matter. Malware likes to get started every time the computer starts. The reason is obvious: they can continue their activity indefinitely because they will be launched automatically by the operating system when you start your computer, without you even having to touch anything.
The fastest way to view programs started when you start your computer is to open the Windows Task Manager, "Startup" tab:
CTRL + SHIFT + ESC or CTRL + ALT + ESC
Then you start at the boot of my computer without permissions? 
Important notes
These are of course examples given in this article. Each case should be studied separately as there are other ways to get hacked (without a keylogger program).
The article does not consider the case of programs called "rootkits", which hide various information from the eyes of security programs. There is also no mention of wiretapping or "AIR-GAPPED" COMPUTER piracy. Of course, launching an antivirus scan and using common sense are your best protections.


Loved the post. I liked that you went into relative detail.
Happy to teach you stuff like that! Followed you for your Fortnite games and tips ;)
great post! thanks for the insights
With pleasure!
Great insights and indicators!
Resteemed.
Thank's a lot man!
Thanks for sharing this......
Thanks for upvoting my post! :)