// Privacy NEWS // China Is Installing Monitoring Apps on Some Tourists' Smartphones
At border crossings adjacent to Central Asia, Chinese customs officers sometimes install spy applications on tourists' smartphones to detect "prohibited" content.

Backpacker friends who plan to travel to China via the old Silk Road, be careful: your smartphone could turn into a real snitch.
According to articles in several publications - New York Times, The Guardian, Vice etc. - there is no evidence of this.
Chinese customs officials at some land border crossings discreetly install an application called BXAQ or Fengcai.
The application is a real snoop since it scans your messages, contacts, calendar and files on your phone. More precisely, it checks that you are not in possession of one of the 73,000 prohibited files (images, texts, videos, sounds) that it lists.
The idea here is not to scrutinize all tourists from China - not likely to happen to you in Shanghai or Beijing - but to keep its western part under control, especially Tibet and Xinjiang.
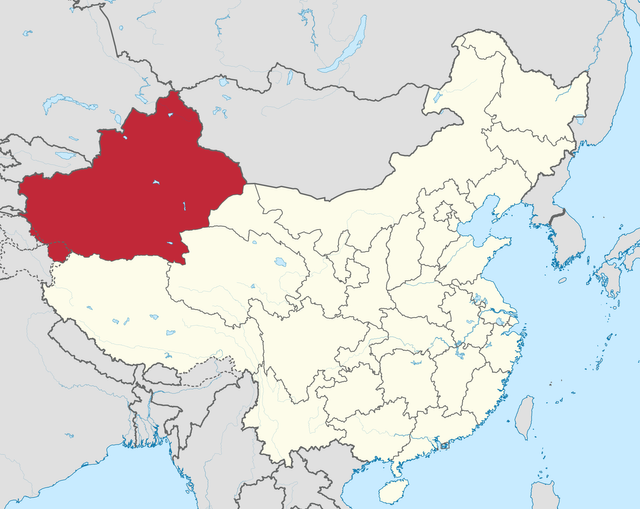
It is mainly this region that is targeted: it is at Kyrgyzstan's border crossings that tourists and journalists have reported that they have been forced to give their phones to the authorities so that they can install the spyware.
The reason is that the large Turkish-speaking Muslim minority - the Uighurs - has been under increasing pressure from Beijing for years, sometimes turning into radicalization.
The application's main purpose is to detect files linked to terrorist organizations.
But the app goes much further by scanning the camera for possible portraits of the Dalai Lama, pages in Arabic (even simple dictionary pages) and according to the reports of the different media even a song by a Japanese grindcore group ("Cause and Effect," by Unholy Grave for those who might wonder).
How do we know everything that the BXAQ (Fengcai) application is looking for? Simply because Western media have managed to extract the apk, the installation file from the Android application.
If you want to play with fire - or help the Cure53 research group that produced the analysis report - you can even download the apk on GitHub.
The experts at Cure53 were thus able to classify from "proven" to "supposed" all the spying operations that the application operates - the collection and transmission of information is proven, the MD5 hash of files and apps as well as the presence of backdoor go from "supposed" to "unclear".
No jealousy as to who has the most secure terminal: according to The Guardian, iPhones are connected to a device that scans the entrails of the device once but completely, while the authorities install the app on the target terminal.
It is thanks to the negligence of some police officers who are supposed to uninstall the app before returning the terminal that we were able to get our hands on the program and unpack it.
If the Chinese government's initial approach seems to be the detection of radicalized individuals - who will quickly take the plunge of putting nothing sensitive in their phones - this situation is alarming for individual freedoms and a perfect example of the abuses of the surveillance society.
Sources : New York Times, The Guardian and Vice

I've made a lot of articles with tools, explanations and advises to show you how to protect your privacy and to secure your computer, GO check them out!
This is my guide To Secure your PC after a fresh installation of Windows
If you think that your Phone or your PC has been hacked, you have to check it right now!
That's how you can be more Anonymous on the internet!
The Future of Cyber-Security, what to expect?
The best Crypto debit card – Wirex!
These are the best VPN to protect your numeric life: NordVPN, ExpressVPN and CyberGhost!
Your PC is slow? That's why!
Why is it important to Be Discreet on the Internet
Feel hot? Your Computer also!
How an Adware works?
That's how you should guard against Trojan!
What are the different Types of hackers?
