// Hacking NEWS // How Chinese Hackers Siphoned Metadata from Ten Mobile Operators
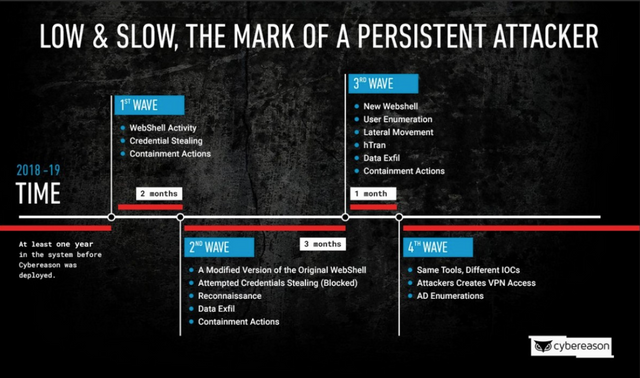
Particularly persistent, the hackers launched several waves of attacks to get their hands on the CDR database, which contains all connection data.
Mobile telecom operators' metadata is particularly useful information.
They make it possible to know who is calling with whom, when, from where and with which terminals.
"That metadata is sometimes more important than the contents of what you're saying," says the firm's principal security researcher, Amit Serper, a security researcher at Cybereason with Wired. "It allows an intelligence service to build a whole picture of you: who you’re talking to, who are your peers and coworkers, when do you wake up and go to bed, where you work, what your route to work looks like. These are valuable pieces of information."
Law enforcement agencies regularly use this data as part of their investigations. Unfortunately, foreign spies also access them illegally.
Cybereason security researchers have discovered that a group of hackers, most likely of Chinese origin, have been accessing metadata from at least 2017 from a dozen mobile telecom operators.
It wouldn't name any of the companies or individuals victimized in the attack, though it notes that they included cellular providers in Asia, Africa, Europe, and the Middle East.
The exact identity of the operators has not been revealed. Cybereason has named this spying operation "Soft Cell".
Well-known hacking tools
To achieve their goals, the hackers used a series of tools that allowed them to infiltrate and take control of the operators' internal network.
In some cases, they have even managed to set up true VPN access to the targeted infrastructures.
Some of these tools, such as the web shell "na Chopper" , the spy software "PoisonIvy" or the server scanner "Nbtscan", are part of the usual arsenal of APT10, a group of hackers certainly led by the Chinese government.
Other techniques, such as data compression, are also reminiscent of this group.
That is why Cybereason believes that its attribution is correct with a gh level of probability.
Security researchers discovered the existence of this operation by analyzing intrusions made on one of the operators.
The target company did not just stand by. On several occasions, it has detected the presence of the attacker in its networks and implemented countermeasures.
But faced with the perseverance of the hackers, who launched several waves of attacks at month intervals, this was unfortunately not enough.
The hackers finally managed to get their hands on the CDR (Customer Detail Records) database, which stores the famous call metadata.
By analyzing the hacker command and control infrastructure, security researchers saw that nine other mobile operators were also in the spotlight.
"Stealing metadata, Serper says, is hardly an unprecedented trick for intelligence agencies. But 10 cellular providers targeted in the same operation is rarer. We know how intelligence services operate, and it’s not something we haven’t seen before," Serper says. "But we haven’t seen this scale."
The company has obviously alerted all operators targeted by this piracy. Hopefully, they've managed to chase away the intruders. But nothing could be less certain.
Chinese hackers are not the only ones hacking into telecom infrastructures.
In 2013, Edward Snowden's documents revealed that the British secret services had hacked into Belgacom's network.
And that the NSA had broken into an underwater cable managed by Orange.
Sources : Cybereason and Wired

I've made a lot of articles with tools, explanations and advises to show you how to protect your privacy and to secure your computer, GO check them out!
This is my guide To Secure your PC after a fresh installation of Windows
If you think that your Phone or your PC has been hacked, you have to check it right now!
That's how you can be more Anonymous on the internet!
The Future of Cyber-Security, what to expect?
The best Crypto debit card – Wirex!
These are the best VPN to protect your numeric life: NordVPN, ExpressVPN and CyberGhost!
Your PC is slow? That's why!
Why is it important to Be Discreet on the Internet
Feel hot? Your Computer also!
How an Adware works?
That's how you should guard against Trojan!
What are the different Types of hackers?