Cybersecurity Demystified: You are so cute and I know where you live, honey!
Lately, a new trend in media is observed. It's a debate related to many rumors about the abuse of power by governments and agencies. Modern society lives in a fear of losing one of their basic rights – privacy. Invigilation and eavesdropping remind people of futuristic visions of total surveillance. Is it a truth that people are scared or a slogan repeated by masses? Are programs like PRISM a real danger, or is there a risk much bigger than that?
In this episode of Security Demystified, we will discuss a problem related to user data and the exposure on platforms like Steemit. It is considered to be a gentle warm-up to reader mindset.

Data, Metadata and Privacy
World is filled with data. They are everywhere and play important role in every aspect of humans life. Basically, a term data means information or its piece, a form of representation of facts or concepts, a set of values of qualitative or quantitative variables. Due to the nature, data can be collected, interpreted, analyzed, processed, visualized. It's done every day, all over the world to speculate stock market moves, forecast weather or invent a new antibiotic.
While it does not require more introduction, a similar one - metadata, seems to be confusing to many. It got a massive attraction since used by a government agency to describe the type of their actions. As a quick reminder: NSA representative said that they do not collect user data, but metadata.
What kind of difference makes that statement? Does it mean, that a user, should not worry. Not necessarily.
Metadata is simply speaking data, that describes or gives a certain information about data. It has a loosely defined scope, which means information like:
- A type of an event.
- A location of an event.
- A time of start and end of an event.
- Involved parties.
And much more depending on an actual event.
The most obvious events are phone calls, emails, photos, visited pages, etc. All these information are carefully gathered and analyzed. To be precise, e.g. in case of phone calls collecting metadata means that the call itself was not recorded. However, in many cases the subject of the call may not be the only important piece. Let’s consider calls like a private psychiatrist, a brothel or a sex line, a suicide prevention line. It does not take much to understand a full the scenario even when the topic of the call remains ‘unknown’.
It is a real problem, but are people really scared about it? Do they actually care about privacy and anonymity?
Internet & Social Platforms. Free Data Giveaway
There is a big misunderstanding between people's expectations and their actual actions. While privacy and anonymity have been treated seriously since 90s by those who understood the range of potential abuse, new generation ignores the subject completely. The need to be accepted by society, liked, followed - to be visible, popular and unique has taken privilege over rational thinking. It has led to the creation of social phenomena like Myspace, Facebook, Twitter or Instagram.
This social paradox creates massive data storages filled with sensitive data – with users acceptance. They are real treasures to both organizations and individuals who want to get information about a person. Who would place a date of birth, an email address and a phone number and a photo all around a city, a country or the whole world? Visible to everyone! Despite a fear of being invigilated, exactly this kind of actions is observed on a big scale. How about check-ins, comments, relationships and work statuses, updates on daily activities? Are these different from metadata collections, mentioned earlier?
There are differences:
- Making it public is a choice (well, so is jumping from a plane without parachute...).
- Public means for everyone, not only to privileged units.
- These data are clearly pointing a subject, categorized and not secured in any way.
STEEMIT. Selling data for SteemDollars.
The platform promotes transparency, honesty and verification over anonymity and safety. It is generally a great way to make friends in real life, but puts at risk people who are unaware of possible consequences.
Every person, who shares information on this platform, makes them public (to view and use). While it is not a @dan's primary goal to make a blockchain-based blog corner, it is fully allowed to use Steemit that way.
Published data let users to infer about the author. Writing articles about photography may imply author's interest in the area. On the other hand, a post about being happy at the beautiful beach on vacations may be interpreted like:
- You may find me here till the end of the week.
- I am here alone.
- I am not at home and I will not be there soon.
Unfortunately, it is where things just start to be interesting. As posts are stored in blockchain, all data is saved permanently with no option to delete them. It makes the full history of a user's activity visible and a future employer, friends, children, random people – everyone have an access to this collection. If that is not enough, more and more tools are created to present users data in an understandable fashion.
Pictures, silent killers.
Pictures make a post unique and attractive to readers. They are also a great source of data and metadata. While media talk about great algorithms which match pictures by content to a specific location, it is the last thing to care about. The real issue is not in a photography which tells your chosen story, but in silently given information related to the photography itself, like:
• A timestamp.
• A type of your camera (including smartphones).
• Software used to edit the picture.
• Picture miniature (original, before crop etc.).
• Geotags.
Why pictures reveal so many secrets? This information (Exif, IPTC IIM and XMP data) should actually make user's life easier. They are used to make files easy to process, categorize, etc. They are not completely hidden, users can see them almost all the time but somehow forget about them when post images in the internet.
How to check it?
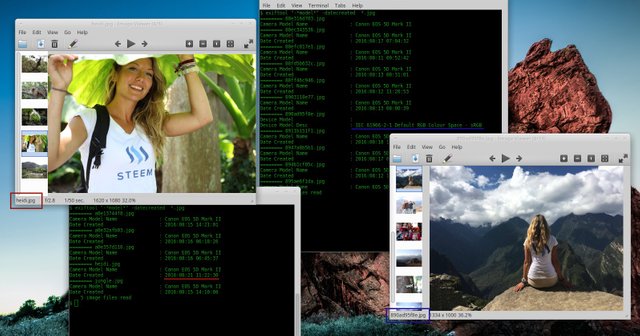
There is a variety of tools available (both command line and graphics editors). A very popular and powerful one is called ExifTool (made by Phil Harvey). Several online tools use it under the hood, among them a popular Exif Viewer. Another popular program is ImageMagick. It is not recommend to use, except photos from known sources, due to the various vulnerabilities found by researchers.
Example I:
In this example ExifTool is used. It has a great tutorial with a set of examples for all platforms. Give it a try! Remember that it is safer for a user to play with any picture at home, not through online tools.
Let's assume we have a file: photo.jpg like the one below:

|
Get all image metadata and safe them to the file:
It returns a lot of information about tested pictures. Get Image Thumbnail:
An image may contain a thumbnail but it does not have to. The important part is that simple transformations like crop etc. does not always modify a thumbnail, which may reveal the complete picture (now, imagine these 'seductive' pictures published in the network...). Still, that is not all! A thumbnail despite its original purpose does not have to contain information related to the actual picture. It may contain a picture before modifications or any other image. Sounds impossible? Test it on the included picture. Get only GPS cordinates:
Picture may show the exact location where it was taken. In this case it is: 38.869184 degrees N and 77.056267 degrees W, which happens to be the Pentagon. Once again, try it! |
| ExifTool | $ exiftool -all= photo.jpg |
| ImageMagick | $ mogrify -strip photo.jpg |
| jpegtran | $ jpegtran -copy none photo.jpg > output.jpg |
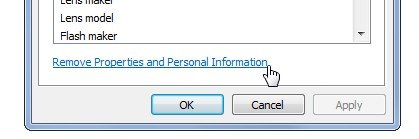
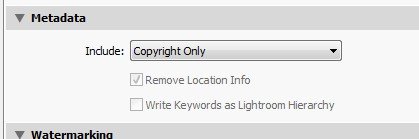
3-rd party platforms
Image metadata can cause many problems bigger than only user exposure (hint: metadata modifications). Therefore, it is often a good practice to remove them during the upload to the server. Big social media platforms like Facebook remove metadata automatically. It is however not enough to keep users safe (it only keeps Facebook safe). Spying tools gather all data from images, check-ins, tags on social plaforms.
Steemit has its own (well, not in legal terms) image hosting, called SteemIMG provided by @blueorgy. It allows users to upload the image without Exif metadata.
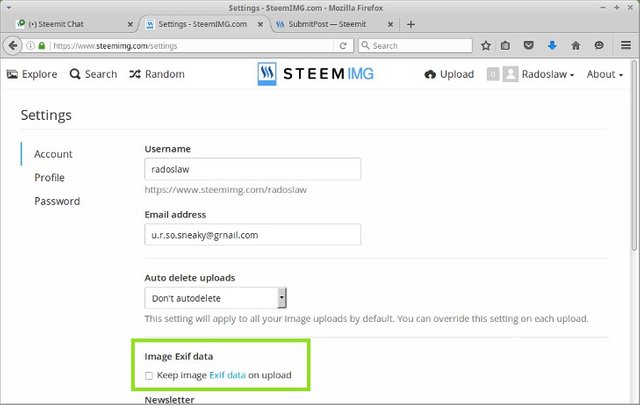
Conclusion
Society is spied by powerful organizations, no doubts about it. The equally or even more serious problem is, however in the number of information published and leaked by unaware people themselves. Repeatedly mentioned precautions like Tor, various VPNs, Tails, PGP etc. do not fully solve this issue.
Steemit is a great platform for content creators, but at the same time, it is a massive source of user data. Therefore, consciousness is highly advised. Simple actions presented in this article may help everyone.
Keep your private data to yourself!
Appendix
- This is the first article from the Steemit series: Cybersecurity Demystified. Learn more.
- Heidi knew about the article before it was published. She agreed to be 'an example'. Tested photos come from her posts: Anarchist in the Jungle and Lost In The Amazon. Thank you!
- More information about image metadata can be find e.g. in the guideline provided by Metadata Working Group. It contains also links to other specifications, therefore these are not listed here.
- The picture of a cute girl from the first example (and the thumbnail) comes from Pixabay.
- Finally, articles found recently on Steemit, you may also find interesting (author's pick):
- Finally, if you have an IPhone THIS may be important to you.
Do you like this article?
Show your support!
A note about the author:
@radoslaw is a software architect from Poland. Highly interested in complex, distributed systems and information security. Author's introduction.
Excellent write up - even if it is a refresher for some it will undoubtedly be new and eye-opening for many. Upvoted and Following
Thank you @timelapse!
the thumbnail was a nice reward for going through the motions as well.
Thanks. I tried not to make it obscene but at the same time give people a kind of reminder what can happen to selfies in underwear ;)
Nice one! I hope this article will be in trending :)
Thank you. Would be nice, it was a lot of work :)
Excellent article @radioslaw
Photo metadata can definitely risk the privacy of people. As the world is using their smartphones more for capturing moments in their life, it creates a huge repository of metadata which is stored in their picture files. Small pieces to the puzzle, which if you know how, can be pulled together to undermine the security, safety, and privacy of people in those pictures.
So happy to see you had permission from Heidi (aka @heiditravels)! Very respectful. Well done sir! Keep posting on security.
Perhaps for your next topic, you can discuss the implications of rising facial recognition algorithms with photos. This will be one of the next big privacy leakage problems.
Upvoting and Following you!
Thanks a lot. I am glad you like it :) Facial recognition algorithms is a nice topic, maybe I should. However, I would like to keep the formula of giving people both knowledge and tools to play and it would be a bit hard in the mentioned case (one article could be not enough :) ).
I have several topics in my mind already. Some of them are more informative, others are plain hacking. I have to think about it. Feedback from this one will probably help me to choose the direction.
Even with all the warning, being given for YEARS about the topic over several channels, people still Ignore on purpose how to take care of their privacy. Good, otherwise... How could a noble blackmailer exploit that?
I agree, it should be a fundamental knowledge for everyone. There is a lot of attacks out there which are based on data published by people. It is a bit ridiculous, that after many years, there are so many people completely unaware of the risk.
It's the most informative and very well written.Nice job!
Thank you!
I've published everything on social media publicly for quite some time. To me, I think, it's about risk probabilities. If someone knows personal information about me, what specific risks increase and at what probability? I get the theft of personal property issue if you're on vacation, but for me personally, how likely is that scenario given the neighborhood I live in, the rate of crime in the area, etc, etc? What other risks exist I haven't considered?
Maybe I'm being naive, but some of this fear about sharing personal information online seems irrational to me. If an attacker really wanted to get information about me, there are illegal tools they could (and probably would) use to do so. Heck, a simple white pages search could do it. I get how identity theft could be a concern, but my credit report is on lock by all the major reporting agencies. So what real concerns should I be thinking through?
Thanks for the detailed post.
Thank you for your comment. I consider honesty (even brutal one) to be a priority in my life but a full transparency is something different. It sounds good in theory but in practice it has many consequences and is quite impossible. You are right it is a matter of odds and you take your chances here. Odds are, however, not a constant value in this equation for every single person. I will not convince you without a good example and that needs to be a one that involves you. It requires me to go through all photos of your happy family (which are nice, btw), your all profiles, repeat it for your wife etc. I will not.
First look - you seem to have a kind of stable and happy life already. In terms of age and social aspects (wife, kids, house, job: both selfemployed) you are a mature and very independent one. It makes things a bit less complicated for you at the moment. I don't believe that you actually mean 'everything', even from a quick scroll of you account, but there is no point to argue about it. All I can really say is that I wish you the best of luck :)
As a response I would like to remind you how the Gauss curve looks... you can think about it as my chart of odds of the whole society for you.
I guess my thought is, "Shouldn't this be the ultimate goal?" Instead of living in fear of someone finding out who we are because of any vulnerabilities they might exploit, isn't it better not to have those vulnerabilities as much as possible? I get I'm very privileged, but I also recognize the efforts I've put into getting where I am today. My hope is everyone can be their authentic self without fear, but I understand that's just not reality for most people. Yet.
I think our cultural norms limit what we share publicly, but that is also changing over time as well. Many people think, for example, sex is scandalous. What if in the future we don't feel this way? That would change the types of photos and stories people feel comfortable sharing concerning their sex life. But yes, obviously not "everything" as I still have secrets related to passwords, encryption keys, etc. Thankfully that type of stuff won't leak through my photo metadata. :)
Not really sure what you mean by that, but I think it relates to me probably not being in the average.
Thanks again for a great post.
Thank you once again :)
Quick notes:
Among many other things - Yes :)
I can only blink reading this one ;) More fun another time.
I have a great life now, but it doesn't reflect the challenges and hard work it took to get to this place. My life was harder than most from an early age. Won't bother with the details, but I did not benefit from much support , it was largely myself pushing forward for what I want. Started with nothing.
Very nice tool, thanks, althought I knew about metadata in photos but this can help other people, who are worried about stalkers.
Data, Metadata and privacy is a really big and broad topic. I tried to show some aspects which should be easy to understand and have easy solutions. Still, I will probably touch this topic once again in a very distant future. Nevertheless there are more interesting and 'practical' topics on the way. As I have mentioned - it is a warmup :)
Btw, it is not only about stalkers. I hope I gave some hints to those who would like to e.g. know how to process and categorize images, learn from them or... well, hide something inside.
I really appreciate the insight you provide on privacy breaches and security measures. I'm sure this was very tedious and time consuming to write and I hope it is successful enough to compensate you for your contribution to all of us in an aim to educate and re-educate us all readers.
Definitely must be cautious and discerning about what material and data we allow people to see. Great work, it does not go unappreciated
Thanks a lot! I appreciate your words and hope you will like the whole series.
It was a lot of work but I believe it may help many people to understand how important details can be. It does not take much time to care, while consequences of being careless can be serious.