[TUTORIAL] Basic Computer Security [11] - THE END

This is the last episode, where the remaining subjects are discussed. After you read this, you should have a pretty good understanding of computer security and you probably will reduce your malware exposure risk by >99%.
Read the previous episodes to know what I am talking about:
- 1) Hardware Selection & Proper Usage 1
- 2) Hardware Selection & Proper Usage 2
- 3) Kernel Defense 1
- 4) Kernel Defense 2
- 5) Kernel Defense 3
- 6) User Space & Device Driver Security
- 7) Switching to Open Source Applications
- 8) Anti-Virus Philosophy
- 9) Getting & Verifying Applications
- 10) Responsible Methods and Behaviors to Reduce Malware Infection Risk
So in the last episode we discussed how to avoid malware by changing our behavior of using the computer and browsing the web. I have detailed there what kind of files are usually safe to open, however if we would only stick to those our computer experience would be very poor.
Obviously we will open other files too in the course of our computer usage, sometimes it’s business sometimes it’s pleasure, but essentially security should never be ignored.

UNSAFE FILES
So in the past episode I revealed the usual safe file formats that have a very low probability of being malware. I mean essentially anything could be malware, but not without the collaboration of the software that opens the file.
Accidental Malware
So for instance a .txt file containing the text “Hello World” could be malware if the text viewer software has a backdoor in it that executes something bad when it comes across that line.
So everything could be malware, but this is why we use open-source software so that we avoid obvious backdoors like this. Now there are of course memory buffer attacks and whatnot, usually making the file crash and then the hacker can obtain root access to the system or things like that.
So the rule of thumb is the more simple the file is, the more safe it is. Like a .jpeg picture file is probably in 99.999% of the cases safe to open, unless at the same time the image viewer software has some bug that makes it crash when the file is opened and then a potential hacker exploiting that situation, leading to privilege escalation.
Probable Malware
Now we don’t really worry about the previous case, just keep all softwares open source and updated as detailed in previous episodes, that is all that we can do in that case. However there are file formats that intentionally have questionable parts in it, that probably can be malware.
Risky Files & Handling Them
So if you really think that a file that you have just downloaded (maybe you shouldn’t even had done that) is suspicious, it should really be handled inside a VM, possibly on a disposable/dedicated computer if you really think that it’s not worth the risk.
I mean if you are a system administrator at a big corporation for instance, and you get a shady .pdf file from the “Nigerian Prince”, would you risk the safety of a multi million dollar system, or would you buy a throwaway airgapped computer for 100$ and view it there? That is the question.
Now you might not be in that situation as a general user, but the malware is getting smarter and your digital data is getting more entangled with your real life. I mean you have all financial (bank, card, payment processor), government (pension, tax account, etc..) and tons of other important digital data on your computer, and after cash is eliminated, it will be even more risky. Now do you want to risk that or would you do anything you can to mitigate the risk?

HANDLING POTENTIALLY UNSAFE FILES
So let’s take each file format and see how to handle them, one by one:
- Simple Images: jpg,jpeg,png,bmp,gif, etc..
In my opinion there is no security issue here, unless it’s an accidental exploit in the image viewer itself. In Linux you have a built-in image viewer that is updated with it’s desktop package, so it should be safe by 2017. There is however a HUGE privacy problem with pictures: the metadata. I mean literally I see people on Steemit upload a picture file and it has all sorts of metadata in it like GPS coordinates, phone OS version and brand, software version (which if the potential hacker knows the probability of a successful exploit becomes higher) and things like that.
Metadata has to be scrubbed, always:
https://steemit.com/privacy/@profitgenerator/how-much-info-does-metadata-leak
Text Files: .txt, .csv or other ASCII text files
Well there is nothing here, just use gedit as your text editor, it’s easy and simple to use and has been analyzed tons of times so a problem with it is unlikely.
- Music Files: .mp3 and similar
Well normally the .mp3 format should be safe however we have to keep in mind that the .mp3 format is proprietary and it requires a special codec to run. So if you want to stay safe and open source then just use the .ogg format files. Ogg is the open source multimedia format, not restricted by immoral patents plus it’s actually even higher quality than .mp3 in some cases.
Well it does contain metadata, however it’s not your metadata, since you are listening to other people’s music, it’s the metadata added by the recording studio into the file.
Still it can be cleaned using the method described here.
- Video Files: .mp4, .avi and similar
It’s the same thing, most of these formats are proprietary and always need a special codec to run. Just switch to open source video formats like Ogg. Video files also contain metadata which can be cleaned with the method explained above.
- .PDF files
PDF files are tricky, they can contain all sorts of macros and javascript, which doesn’t have any real purpose but to just serve you ads, adware, and decrease your privacy. I mean the javascript inside a PDF can track when you open a document and how you use it. It’s horrible it makes no sense but that its how it is.
Use only Evince to open PDF files. It disables javascript and other macros by default, in fact it doesn’t even support it. It’s a clean PDF viewer with no support for anything fancy so it should be theoretically safe to open PDF files in that.
If the PDF file is really shady however (remember the PDF is an executable binary) then only view it from a disposable environment.
- Office Files
Well switching to LibreOffice is the first step. Then I guess you should configure LibreOffice to a secure setup by disabling macro support and all other fancy stuff there. If you just want to view a document, there is no need for those and it causes more harm than good.
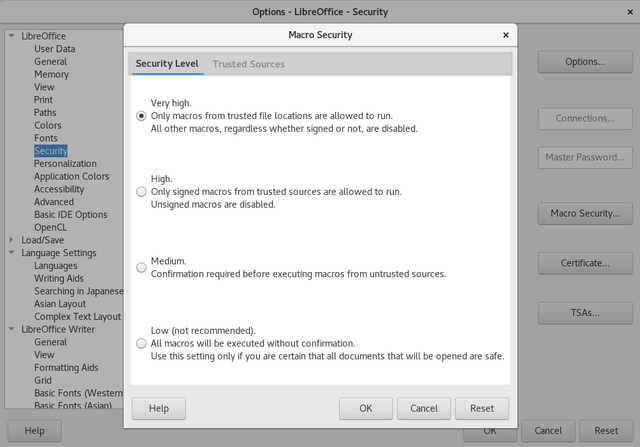
Go to Tools>Options and there click on Security on the left side, and click on the Macro Security, set that to Very High.
That should eliminate the risk coming from shady macros, you will not need them, it is a very bad implementation of a more rich programming environment inside the document, but for that you can just use Python anyway.
That’s about it just remember to clean Metadata with one of these tools:
THE END – CONCLUSION
That’s pretty much about it, the end of this 11 part series on computer security. Now this was just the basics, I am not an expert, but I have shared here with you pretty much most of my knowledge. There are a few more things but I don’t want to complicate it.
If you know and remember this, and follow these procedures, you have pretty much eliminated >99% of the risk of malware. Of course there is never 100% safety. There are things like malware that can infect the header of USB drives, and it becomes very hard to clean it, and things like that.
But for a general user I think this is enough, certainly if you have read the entire series you definitely are more educated now than you were when you started.
Even if you are a newbie user, this tutorial was hopefully helpful to get a grasp of the dangers that lurk out there and to have some methods to defend yourself against it.
It all comes down to you in the end, no antivirus will save you if your behavior is reckless. Just use your computer responsibly and things will be fine.
Sources:

I really liked that series, it is clear and very informative! Keep posting!
Thanks, did you learn anything useful that you didn't know before?
Yes, the qubes OS looks pretty nice, I will give it a try! There are few opensource things in the tutorial 7 that I learned about and its always good to refresh the basics! Thanks!
Great Tutorial