[TUTORIAL] Basic Computer Security [2]

Let’s continue the series. In this episode I want to talk about wireless. Yeah wireless, because it’s a horrible security threat.
Make sure you have read the previous episode so that you know what I am talking about:

2) Wireless & Internet
Wireless is well known in the compsec community to be very very problematic. First of all the general idea of having everything connected is Marxist nonsense. I have wrote a very good philosophical article demonstrating the need for decentralization:
- https://steemit.com/economics/@profitgenerator/financial-risk
- https://steemit.com/politics/@profitgenerator/the-last-leg-of-communism
Make no mistake about it, this “connect everything” mentality is Marxism. I don’t want to make this a political article, but it is Marxist in nature to centralize and “collectivize” everything. So interconnected people just as much as interconnected devices are Socialist in nature. And we know both politically and technically how bad Socialism is. You must read this article where I have shown that risk must be decentralized:
And this is more important in computer security than anywhere else. Because if you have interconnected devices, then the weakest link is enough to compromize the entire system. This is the endgame of socialized risk. Everything falls apart.

Wireless Router
A wireless router is horrible because anything can connect to it. They literally make now all these smart devices that can just connect to it. Like these stupid products that tell you the weather, or your phone, iPad, washing machine, refrigerator, etc…
No, it has to be a dumb router, as dump as it gets. There are still cable routers available, but the wireless router has to be removed, because any hacker in the radius of it can hack it. So if your neighbor is a shady drug dealer, he can hack your router, do his dirty work on it, and then the police will come to you accusing you of being a criminal.
From the Snowden leaks we know that the router is the easiest hardware to hack:
- https://www.theverge.com/2017/6/15/15812216/cherryblossom-cia-router-hack-surveillance-dlink-linksys-belkin
- https://www.theguardian.com/books/2014/may/12/glenn-greenwald-nsa-tampers-us-internet-routers-snowden
- http://www.infoworld.com/article/2608141/internet-privacy/snowden--the-nsa-planted-backdoors-in-cisco-products.html
So, unfortunately, we can’t be liberal trendies anymore if we are worried about our security and privacy.
All these smart devices are scams and they do more harm than good anyway. And if you really feel the need to put your home full of them, just make sure they can be unplugged, and stay powered off when not in use.

Wireless Keyboard
There is overwhelming evidence that your wireless keyboard can be hijacked and turned into a keylogger:
- https://www.wired.com/2016/07/radio-hack-steals-keystrokes-millions-wireless-keyboards/
- https://hackaday.com/2007/12/02/wireless-keyboards-easily-cracked/
- http://thehackernews.com/2016/02/mousejack-hack-computer.html
- http://gizmodo.com/your-wireless-mouse-and-keyboard-can-be-hacked-to-gain-1760973117
So use only wired keyboard.

Wireless Mouse
The mouse is just as vulnerable. However I guess the mouse itself is not as sensitive piece as the keyboard that you’d use to enter passwords. But still why risk it. Besides these crappy wireless mouses always have their battery die too soon, so I’d just prefer wired mouse.

USB Port
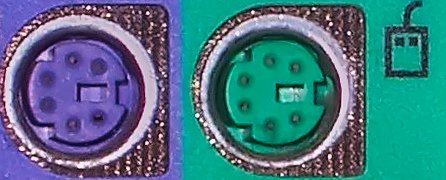
There is 1 more important thing. According to experts the PS/2 port is possibly more secure than USB, since it doesn’t have direct memory access (no possible malware infection) and handled by a different part of the computer. So if you have a desktop computer with a PS/2 port (you know the green and purple round hole), then try finding a mouse and a keyboard that is through PS/2 or get an adapter to it.

Bluetooth
I am not a fan of it either, but it has a short range, like 10m or so, but I don’t really see the need for it in a computer, but it’s not as bad as a wireless router since a hacker would need nearby access to hack it, wheres a wireless router could be hacked from up to 500 meters. So I am neutral on this one, perhaps it’s good if you want to transfer data from your phone to the PC.

Wireless Internet
This is a problem especially for laptops. Unless you really have no other means to connect to the internet, or if you are on the road, I’d really remove the wireless adapter from a laptop. This disables Bluetooth too.
The wireless adaptor can be easily removed (at your own risk) it’s usually depluggable, and if you are at home, then just get your self a RJ-45 cable, with a dumb (no wireless) router , and use the internet this way.
There is no reason why your washing machine should have access to your home network.
And if you use your home network as the internet for your phone or iPad, then buy a secondary wireless router than you connect to the main router. That way the network is more isolated and your main connection not risked. But then again, nothing would stop the hacker from hacking the wireless router anyway. So I think mobile net should be for phones, which is separate from the home ISP internet anyway, don’t mix the two.
Conclusion
So you’d use a wired keyboard and mouse, preferably through PS/2 ports, and cabled internet through a “dumb” router, so that you can only connect secondary devices to it through cable, and avoid neighbor hackers from getting access to it.
If you must use a wireless adaptor, then just remove it (at your own risk) after not in use. But wireless is mostly just for travel, if you are at home, there is no need for it. It’s just an additional attack vector for hackers to exploit, so I’d avoid it whenever it’s possible.
Sources:
- https://pixabay.com
- The Bluetooth logo is a trademark of Bluetooth Special Interest Group

Keep up the good work!