[TUTORIAL] Basic Computer Security [5]

A few more things came to my mind so let me make another quick post. I still haven't finished the part about the kernel security because really that is the most important part. Apps and userspace security is trivial, but it always goes back to the kernel. If the kernel is exposed then the entire system is compromized. So it has to be protected massively.
Here are the previous parts, make sure your read them all if you want to stay up to date:
- 1) Hardware Selection & Proper Usage 1
- 2) Hardware Selection & Proper Usage 2
- 3) Kernel Defense 1
- 4) Kernel Defense 2
Okay so in the previous part I have discussed a strategy of "boxing" malware inside a Virtual Machine so that it will be kept quarantined from the Kernel, and of course several VM's used for compartimentalization between sensitive work and casual work.
Now that is all cool, and you can really setup your computing experience that way, but it will probably be hard for a novice and in fact there is an even easier way and in fact safer way to do it.
It's not just that setting up Virtual Boxes is hard for a newbie, but it's also very uncomfortable to work that way, and in fact in may not even be as secure as you think.
Problem with VM Setup
Don't get me wrong it's infinitely more secure than what you are using now, but it's still not an ultimate setup. Since the VM software itself is just too complex and it's GUI so it has to rely on QT and many other packages, and we know that the more complex something is the more prone it is to undiscovered bugs. So why complicate it? What if there were a system that would both be ridiculously easy to use (even for Linux newbies) and also much more secure, and it would also eliminate the human error (of messing things up), since the compartimentalization and the VM destruction is already configured for use.... ? Well there is, it's called QUBES.

Qubes
Qubes is like a dream come true for a security enthusiast. Everything that I described in episode 4 can be done in Qubes, much more easily and literally pre-configured so it's just a couple of clicks for people.
Qubes is an operating system built for compartimentalization and virtualization of computing activities. So there is really no reason to do what I described in episode 4, just install Qubes only and everything you need is built into it.
Qubes is running something called a hypervisor performed by Xen which would be the equivalent of VirtualBox, but instead it runs in the kernel, and I think it's probably better hardened and more safe than VirtualBox.
The hierarchy inside the Qubes environment is like this:
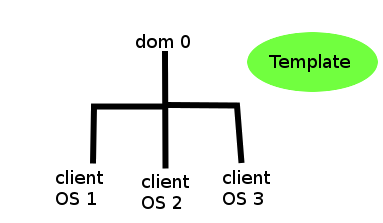
So you have the “Main OS” as described in the previous episode, but here it’s called dom0 for some reason. It’s the Main OS part that can only be used for administrator maintenance, updating the kernel and things like that. I don’t think it even allows to install any additional software here.
Then you have a Template (Fedora,Debian & Whonix), so you can use this to restore or create new VM from this template. Also the template can’t be used, but only updated I think, so this removes any possibility of a malware compromizing it (not to mention it probably already is linked to trusted repos with a GPG key, so only signed updates can be downloaded & installed by default).
And then you can create as many client OS’s as you want from the Template. You have a Fedora, a Debian and a Whonix OS as a template but I think other ones can be installed too. So a Fedora can be setup in like 2 minutes and then that can be used as an OS for a certain activity.
Fedora is like a casual OS, while Debian is for security (since it’s fully open source) and Whonix is a privacy oriented distro. So you can choose which one you want to use, and again others can be installed too, but it needs additional configuration.
The basic features are that:
- Guest OS’s I think can’t communicate between eachother, so your Banking OS and your Porn OS is totally separated. However information can be sent over, but through a hardened channel controlled by
dom0which is allegedly totally safe as much as Xen can provide, but only with the authorization of thedom0, so rogue elements inside can’t leak out. - The
dom0I think can insert files into a Guest OS, but a Guest OS can’t communicate directly with the dom0 without it’s authorization. - There is a possibility to create a non-networked OS, for cold storage.
- There is a possibility to create an anonymous OS where the internet is routed through a VPN or Tor.
- There is a possibility to create a micro OS that can be destroyed even after 1 operation (so like opening an untrustworthy .PDF file, reading it, and then closing it, and self-destructing the VM with it)
And despite how complicated it would sound, it’s literally very easy to use that even your grandpa can use it. It’s all GUI so even your Linux novice can use it, although console experience might be required for updating and management of the system.
I have tried and downloaded Qubes about a week ago and it’s pretty easy to use, but I only use it on my other computer, I usually keep this one for casual stuff. It was very easy for me to get used to it, so I really can recommend it to everyone who wants security. But install it in a different computer as a clean install, DUAL BOOT IS NOT RECOMMENDED EVER!
It looks like this:
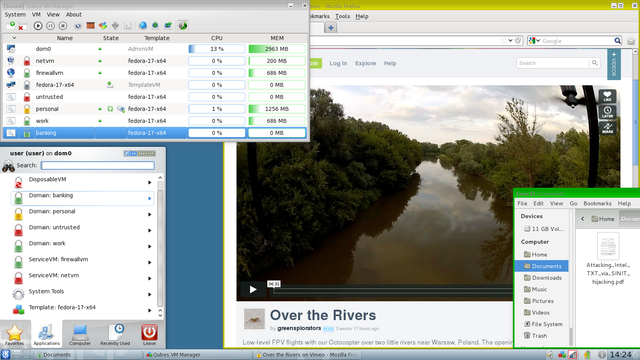
By Brunogabuzomeu GFDL or CC BY-SA 3.0, via Wikimedia Commons
As you can see in the picture above a yellow color coded VM was opened (you can basically set it to any color you want, to differentiate between workspaces) which corresponds there to “Personal”, so this particular VM would be for example handling photos of yourself or your family that you don’t want to mix or taint with malware or even spyware from other softwares.
Like for example VAC is allegedly a spyware that has been reported by many to be too invasive, allegedly scanning through files on people’s computers, watching out for running softwares, logging IP history and things like that:
- https://www.reddit.com/r/privacy/comments/1y0btj/rumor_valves_anticheat_vac_allegedly_snoops_your/
- https://www.reddit.com/r/privacy/comments/721cql/when_malware_gathers_large_swaths_of_information/
So if people think that they don’t want any kind of software that would have the capacity to spy on files to have access to their personal photos and videos, then quarantining that user space against potential apps that would do that would be a smart move.
You can even run Windows inside a VM inside Qubes, so you can totally play all games or whatever that you would need on Windows, but isolate everything else that is really important from it.
So all the security benefits as suggested in episode 4, and even more, and none of the drawbacks from that system. With Qubes you can have the entire compartimentalization system on 1 DVD.
In fact it’s even safer since you can verify the DVD afterwards and the downloaded .iso, so you don’t have to rely on downloading everything by yourself. Just 1 .iso file, that’s it.
Get Qubes
1) Download the latest Qubes from here:
2) Verify that the website is HTTPS, cerfified via COMODO CA Limited
3) Verify the HTTPS certificate SHA256 fingerprint:
0A:E2:2E:D9:8E:54:F8:7A:E1:D8:34:3D:60:F3:62:08:EA:73:17:62:59:7C:CD:67:1E:A3:EC:E6:02:2C:79:CC (expires on 01/12/2018)
4) Import the GPG key it should have the following fingerprint:
C522 61BE 0A82 3221 D94C A1D1 CB11 CA1D 03FA 5082
5) Download the .iso through torrent or the file, with the signature and verify it by typing in:
gpg --verify Qubes-R3.2-x86_64.iso.asc
6) You can double or triple check it if you are paranoid, and if everything is ok, you can just burn it to a DVD.
7) Backup all your important files, and then just install, a clean install of Qubes, this will wipe all your files away, so make sure you have backed them up, or they will be lost.
8) Enjoy Qubes!
Getting Started
Now at first glance it may look foreign but you will get used to it, here is a very easy series that will teach you how to use it:
And you find many more videos on Youtube and you can always read the documentation if you have a question:
Last but not least Qubes is social, so you can join many social groups:
- https://www.reddit.com/r/Qubes
- https://www.facebook.com/QubesOS
- https://twitter.com/QubesOS
- https://www.qubes-os.org/news/
- https://www.qubes-os.org/mailing-lists/
Disclaimer: I am not affiliated with QubesOS.
Sources:
- https://pixabay.com
- Qubes logo by Qubes OS GPL, via Wikimedia Commons

Citrix Xen is designed as a bare metal hypervisor with clustering support via resource pools. Everything is compartmentalised into domains,
dom0is domain 0, or host domain, the privileged domain dom0 has direct hardware and kernel access, it initialises first and loads/manages domU, the unprivileged domains (VMs). Dom0 arbitrates access to resources such as hardware or network on behalf of domU.This abstraction can provide security, but shared resource, hardware pass-through or direct access is possible for domU, it depends on how you set it up. It is possible to have a malware-test VM that shares networks and physical NICs with your host, not very secure at all. Just educate yourself about how to isolate VMs & networks, or else you'll get something nasty from a VM cross over to dom0 or out via network and back in through NIC onto all the computers in your home or office network computers.
If you want to game on a Windoze VM in domU then you'll probably need to pass through the physical GPU from dom0 to a specific domU or else Windoze & the game will not detect any compatible 3D acceleration GPU support and fail to init. Generally, templates provide a a high ubiquity/compatibility based software graphics device that is well supported.
It is definitely possible to install packages to dom0 via command line, either on console or via SSH, I've had to install zip & unip YUM packages for later versions of XenServer 7 in recent months as it no longer seems to ship with them and that's a PITA for installing updates as they're supplied as *.zip archives.
Wow looks like you are expert on this, while I am just a mere novice.
Well I have tried Qubes and so far it's decent, I would certainly not run any Windows on it and I am conservative about installing stuff as well, but I really need to learn more about configuring networks I am not good on that, so perhaps you are right about those shared resources.
But I thought some of that function is isolated by the CPU isn't it? I mean you have stuff like this:
Doesn't the hardware acceleration provide some framework to isolate guest domain's resources from the main domain?
I work with Xen everyday and manage headless (no GUI) Linux servers from command line, just wanted to share some knowledge. I've seen Qubes, was very interested and would like to experiment, but, time....
dom0 isolates domU from direct hardware access by abstraction, the real hardware isn't presented to the VM, only a software device representing it is, the guest OS has direct access to this virtual device as if it were real, anything this device does/needs is then carried out by dom0 on the real hardware.
HW>hyper>VM>guest OS + DLLA network or networking device can be shared with host & other VMs or it can be private to a specific VM, depending on how it is defined. It's possible to make a network shared between VMs that never leaves the hypervisor or goes out through the physical NIC at all, just passed back and forth between VMs. At any rate, all VM network traffic that traverses the NIC and local network can interact with other hosts on that network.
The isolation of VM private data & working sets is a big and complicated topic, as is network isolation, but the primary concern is the belief that virtualisation has an innate inoculating effect on threats. Consider this:
VM runs in complete isolation. VM has virtual NIC and traffic from VM traverses physical NIC into local network. VM is compromised, let's assume malware. Malware is network aware/capable, let's assume it's a cryptolocker rasomware. After compromising the VM malware will next attack all hosts on local network, including the hypervisor host.
Whether or not the NIC is virtualised or not it still has access to the local network and functions more or less the same as a physical NIC, if it couldn't there'd be no purpose in a virtual NIC. To isolate the traffic would require a second physical NIC in the host system connected to an interface on your networking equipment specifically configured to put this traffic in a separate network, the most common method being a VLAN but some enterprise switches/routers allow for port-specific mapping that allows for strict isolation. Example of NIC2 VLAN:
VLAN100 (default)- switch/router ifaces 1-8VLAN666 (user config)- switch/router iface 9NIC1>CAT6 cable?iface1NIC2>CAT6 cable>iface9This is of course grossly oversimplified for illustration purposes, but assume that VLAN100 is 192.168.1.0/24 with DHCP and all hosts, physical or VM, that connect to it, virtually of physically on interfaces 1-8 of your network equipment, get an address in that range and can chatter away with each other in their happy little world. Meanwhile, Mr Test Gimp™, a salubrious VM of questionable intent, has a dedicated phys NIC passed through hypervisor to it, it's phys conx is to iface 9, and is on LAN 10.1.1.66 with router providing gateway/routing/NAT to internet. Isolated, yet accessible via hypervisor conole (GUI or otherwise), as if it was a box with it's own internet conx.
VM or otherwise, a box is a box is a box, connect them all together in a LAN and infect one, you've risked them all.
It just needs to be kept in mind. Same philosophy as your advice on antivirus not equal to immunity a-la false sense of security equals increased risky behaviour.
I'm glad you take time to share advice and tips on safe computing practices/behaviours with others. I'd write a lot of the same myself, have written some, would write a lot more, but, time...
The ultimate problem with antiviruses is simple. Any clever virus would infect the antivirus first, since the antivirus has total (invasive) control over the PC (not to mention privacy concerns).
Once the virus has infected the antivirus it can do the harm without being detected and the user having a false sense of security afterwards.
It's better to face the threat naked and be prepared for the potential malware by changing the user's behavior (verify software, not clicking random links, not opening attachments ,etc..) into a more responsible computing instead of relying on snake oil software to protect them.