Tomshwom's Advanced Crypto Security Guide (Part 3) - Creating a Secure Wallet
Purpose
We're finally going to create a customizable wallet solution that is cheap, secure, and not too complicated. While simply following the steps in this guide will give you a wallet that is resistant to malware and other online threats, it does not guarantee total security of your funds. To be truly secure, you must practice good security and follow the guidelines for how to actually maintain and use the wallet.
I highly recommend looking at part 1 of this guide to better understand security and privacy in cryptocurrencies.
If you're wondering about the security of existing wallet solutions, see part 2 of the guide.
Overview
I refer to this as a "wallet solution" rather than just a hardware wallet because it encompasses more than just some USB drives you stick in your computer. The way you decide to distribute the passwords and keyfiles, store the USB drives, and document your solution will all have pros and cons, and these are decisions left up for the user to determine. We will go over the security and convenience tradeoffs near the end of the guide, so I recommend you read the entire guide before you start.
This part of the guide relies on free & open source software1,2,3, cheap hardware, and a bit of time in order to produce a system where sensitive data can be stored securely, accessed safely, and backed up easily. It follows the idea of security controls1,2 to implement physical, technical, and administrative safeguards, but is left up to the user to ultimately choose which ones and how to implement them.
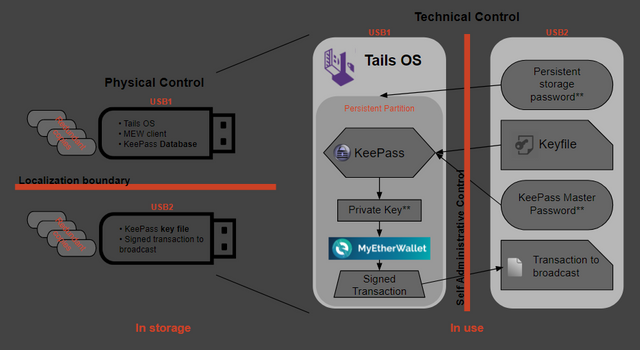
We are essentially creating our own hardware wallet that has multi-factor authentication built in and no single point of failure (like a backup seed). The goal is to end up with 2 USB drives (more for redundant backups) that are used for:
- Booting into a secure offline OS
- Accessing doubly-encrypted sensitive data like private keys
- Securely signing transactions
The multi-factor authentication depends on how you choose to implement this system. You can have as many or few separate physical USB "keys" and passwords required to unlock your wallet as you want, and the way you backup and distribute them is also up to your discretion. Read through the rest of the guide for some recommendations and discussion about the pros and cons.
Procedure
Gather needed materials
- A computer with internet access capable of booting to a live OS on a USB drive (almost any PC or laptop)
- Minimum of two flash drives larger than 4GB, more for redundant backups - USB 3.0 is a bonus
- A way to view this guide and other ones I'll be linking to on a different computer during the offline portions
Downloads
The first step is to download the MyEtherWallet client so we can sign transactions from the offline wallet. You can get the latest release of MEW here. You want the dist-vX.X.X.zip file. Only download from this official source. Please verify all links before you click them. If you're looking to use this for cryptocurrencies other than Ethereum, download the appropriate wallets that support offline use now too.
Next, we need the latest release of Tails. Tails is a bootable OS that runs off a flash drive. It has lots of useful programs pre-installed, like KeePass, Tor, and even the Electrum Bitcoin wallet. Additionally, Tails is an amnesic OS, meaning it forgets everything you do after a restart. It does not save anything unless you configure it correctly. We will need to download a couple more pieces of software, but for now we move on to the Tails installation.
Install Tails
Know that you will have to be doing this on a recent version of Mozilla Firefox if you don't want to use a torrent client. Once you're on the Tails website, follow the Tails Installation Assistant. When it asks, we are going to be installing from Windows (or whatever OS you're running), NOT "from another Tails".
I'm not going to cover the installation of Tails since their assistant does a much better job than I could hope to. Feel free to ask questions in the comments if you're having trouble.
Once you have downloaded the MEW client .zip archive and finished mounting the Tails .iso file using the Universal USB Installer to a USB drive, you need to shut your computer down, unplug the ethernet cable from it (or disable your wireless driver / unplug your router if you're using wireless), and then start back up. This is a precaution that you should take to avoid any sort of unwanted network traffic like malware "phoning home" and sending your keystrokes, clipboard contents, or screenshots to its host.
When you start your machine back up, you can continue with the intermediary Tails installation by going to your boot manager and selecting the flash drive you put Tails on. If you need help with this, I suggest googling "how to boot from USB" and then the OS you're using and/or model of laptop.
When you get to the Tails welcome screen, add the additional setting to "Disable all networking". Continue to add this setting any time you see this option. Once you're done installing the final Tails, follow step 7 on their guide to create an encrypted persistent storage.
Choose an appropriate password for the persistent storage volume depending on how you plan to store the password. You can't copy/paste this password from a secondary drive since it needs to be entered before Tails is completely loaded, so a randomized password is going to be annoying to look up and type each time.
If you're going to store it in memory only, I recommend using an easy-to-remember password and sharing it with a trusted party like a family member who can also remember it. You may even want to use one of their memory-only passwords if they have one. This is a safety measure for the case where you become unable to recall the password yourself. The better solution is to clone your Tails USB key containing the database, but create the persistent volume under a different password that your trusted party knows. They can't access the database without also having the master password and keyfile, so this should be relatively safe.
Alternatively, if you're going to store this password in a password manager separate from the wallet USB keys, I suggest a strong passphrase that isn't based on lyrics, books, quotes, or other publicly available works. This makes it easy to remember and type, but Make sure the password database is stored redundantly so that it isn't lost. If the master password to this database isn't known by another trusted party, you risk losing access to your funds.
Again, it's more important that you remember the password easily so you don't have to write it down (where somebody could find it) or store it on another system (where it can be stolen). Being able to draw it from memory will also be convenient since you can't copy/paste it.
Set up MyEtherWallet
Shut down your machine, unplug the Tails drive, and boot back into your normal OS. Either format the USB that you installed the intermediary Tails on, or get another one and put the MyEtherWallet dist-vX.X.X.zip file on it. You can do this ahead of time if you are following my advice to read all the instructions first.
Reboot into Tails, disable networking, and enter your persistent volume password.
Plug in your second USB with the MEW .zip file on it, and copy it to the persistent Tor directory. The MEW client uses a browser to navigate the html files, and Tails already has Tor installed. Tor cannot access files outside of it's assigned folder, and the MEW files need to be in the Tor folder located on the persistent directory if you want them to exist after a reboot.
Unzip the archive and open index.html to verify everything works. You may have to close some dialogue boxes Tor generates since you aren't connected to the internet.
Set up KeePass
Now we need to create a password to generate our private key and UTC file using the MEW client. Run KeePass from applications (top left corner) > accessories > KeePassX. Enter a master password that is different from the one you used for the encrypted persistent volume. This password could be memorized (taking into account the discussion above), randomly generated and stored on a drive separate from the Tails drive, or ignored completely. Obviously, choosing to ignore the password or use the same one as the persistent volume is less secure. If you are already using a memory-only password for the encrypted volume, I recommend using a recorded password that is stored in a separate password manager.
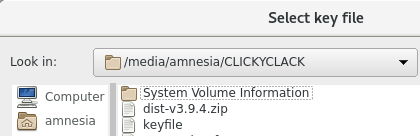
Click the option for a keyfile and create it. Save this to the second USB drive, NOT the Tails drive. Locating the other drive can be done by going to the "/" directory > media > amnesia > your drive.
Generate your cold storage address
Create an entry for your MEW password and use the password generator to give you a long random password.
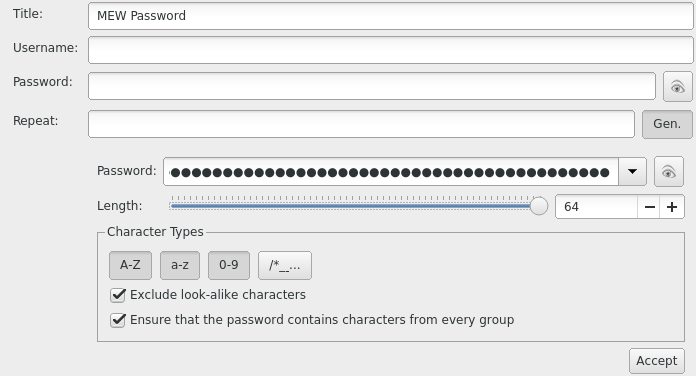
Go back to the MEW client and put this password in to generate a new wallet. Download your Keystore File. In KeePass, open your password entry and attach the keystore file in the advanced options. Now you have your password + keystore in one place (which is equivalent to your full private key). Save your actual private key in KeePass also. Delete the keystore file, we only want it to exist in KeePass. Don't store the private key or keystore anywhere other than your encrypted KeePass database.
Before you exit KeePass, go to Database > database settings and click the "benchmark" button.
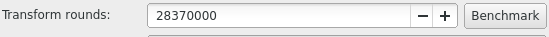
This determines how many rounds of encryption can be run on the database in 1 second. It drastically improves the security of the database against brute force attacks while only being slightly inconvenient (takes 1 second for decryption).
You should now have your password, MEW UTC keyfile, and private key saved in the database.

Save your KeePass database to the persistent directory.
Reboot your machine back into Tails. Once you're in, launch the MEW client and access your cold storage address using the UTC + password stored in the KeePass database. You will have to save the keystore file from KeePass to the persistent Tor directory in order for Tor to be able to use it in the MEW client. Access the address again using the private key. Remember, you need the password and the keyfile to open the database, and you should've stored the database keyfile on the second USB.
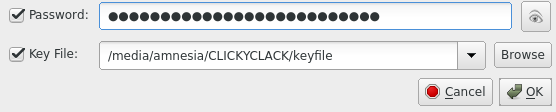
If everything is done correctly, you should be able to access your address using the private key and the UTC keystore + password. Go through both of your drives and verify that everything is where it belongs:
On your Tails drive
- Tails installed with persistent volume password stored in memory*
- KeePass database (in persistent Tor directory) with password in a secure location*
- MEW client (in persistent Tor directory)
On your secondary drive
- Keyfile for the KeePass database
- Additional passwords*
On an optional tertiary drive or in a password manager
- KeePass database backup
- KeePass keyfile* OR KeePass password* (never store these on one device, especially one with the database)
- Persistent volume password*
* only recommendations, can be changed at discretion of the user
We keep the KeePass database located on the Tails drive so that the most sensitive information (private key) is encrypted by both the database and persistent Tails volume. Separating the UTC file and password while never storing the raw private key is another option, but I don't see any security benefits to it.
Once you're sure that everything is set up correctly the way you want, test the address by sending a small amount of Ether (.001) to and from the address using the offline transaction signing in the MEW client. Remember to use low gas prices to save Ether.
Review and document the system
At this point, I recommend documenting how your system is set up so that you and/or a trusted party can access your funds if you ever forget or become unable to. These entries should have their location, quantity, and purpose recorded:
- Tails OS with KeePass database and MEW client - stored redundantly on multiple USB drives. Recommended for database to contain MEW UTC file + password and private key
- Tails persistent volume password - recommended to be memorized and simple, can set up secondary Tails with different password to make it easy for trusted party to also access
- KeePass master password - recommended to be unique and secure from brute force and dictionary attacks. Can store encrypted on a separate system unrelated to the wallet drives
- KeePass keystore file - recommended to be stored redundantly on multiple USB drives, encryption is a plus
Create Backups
Now that you have things working, you can store your KeePass keyfile on other drives and locations both digitally or physically for redundancy. If it exists on an online system, it should be encrypted.
To create a backup of your Tails drive, boot into Tails and go to applications > Tails > install by cloning. Also, copy the KeePass database and MEW client from the persistent Tor directory to a temporary location on a different physical drive. Boot into the new Tails installation, set up the persistent volume again, and move the KeePass database and MEW client into it from the temporary drive. Format the temporary drive (full, not quick) to erase any traces. Look into Darik's Boot and Nuke for ultra secure drive wiping.
Verify Everything
At this point, you need to take a step back and look at what you're really doing. The whole point of this guide is to give you some tools so you can decide how to arrange your system of security. For a secure system, you need to make sure of at least these things:
- You cannot access your private keys without at least two drives and something you know
- Gaining access to any 2/3 (or any majority) of these does not compromise your system
- Loss of one of the drives does not keep you out of your system / you've made backups
- Chances of losing all of your backups and the main drive of either the KeePass keyfile drive or the database drive is extremely unlikely because they are stored in drastically different secure environments (like a lockbox at home and a safety deposit at a bank)
- You've tested accessing the wallet, depositing funds, and signing transaction offline to withdraw funds
Summary
This is a lengthy guide and is intentionally vague in some areas to encourage users to put thought into it and figure it out on their own. The end result should be a sort of multi-signature, offline accessible, inexpensive, highly encrypted wallet. It is up to the user to maintain their own protocols for accessing the cold storage wallet, namely, to only bring the separate required drives together when accessing the wallet and promptly separating them once they're done. Creating redundant backups is highly encouraged, but don't make more than you can actually store securely. Be careful about the passwords you choose and how they are stored.
Please, let me know about your experiences with this guide. If you have recommendations, leave them in the comments and you may earn yourself a tip! Don't hesitate to reach out for support with any aspect of this guide, I made it to help you.

Hello,
Thank you for this amazing guide! I was able to install everything as you instructed, but I have one big question:
Basically, everything was created offline, so how does my Ether address is updated in the global database, which is online?
Doesn't it need to sync up with the offline wallet first? so my address appears somewhere?
If someone sends me Ether, how can I check my balance, if Tails is always offline?
(I figured the tails system should never be online, like you instructed)
Thanks in advance,
Elad :)
Your Ethereum address already "exists" on the blockchain before you generate the private key to it. Anybody can send funds to it, and you can check the balance using a blockchain explorer like https://etherscan.io/ (which is the way all people should do it since you don't have to use any sensitive information for this).
You're correct in thinking that you need to be connected to the internet to see the current state of the blockchain, and thus the current balance. But it's perfectly safe to use Etherscan on your normal online computer to do this.
For sending transactions out of the address, you generate the transaction via MEW on the Tails drive, drop the signed transaction data onto a secondary drive, move it to an online system, and broadcast the transaction.
It works similarly to a hardware wallet where the unsigned data goes into the secure system, and the signed transaction comes out, but all the sensitive information stays secure.
@tomshwom Thanks so much for writing out this detailed guide. I decided to make things simple by not downloading Tails or the Kee pass yet and simply download the offline MEW wallet on an air-gapped device.
I'm trying to create an offline MEW wallet on my mac. I downloaded the zip file from the official Ether website here, placed it into a hard drive and then connected that hard drive to my Mac which has never been connected to the internet.
I opened the index document which took me to the offline version of the mew browser where I entered a password. Then I clicked generate wallet and it took me to a page where I clicked the "download keystore file" link.
However, no file was downloaded (how does a file get downloaded if you're offline?). What happened was that I was taken to a new tab titled, "blob:file:///xxxxxxxx".
What am I doing wrong? How do I download the UTC file offline on the mac?
I'll happily give a full UV to anyone who can help fix the problem.
You're technically downloading the file from yourself, since you're the "server" in this situation.
My hunch is that there's a dependency issue since you're running on a Mac that's never been on the internet.
I'd recommend downloading the Google Chrome installer and running that on the Mac, then try opening the index.html file using chrome.
If you're already using the latest version of chrome and this isn't working, you may be having issues with javascript. Again, download the latest version of the java installer, and make sure the browser settings aren't blocking it from running.
As a last-ditch option, you could just use the private key instead of a password+keystore. If you want to password protect the private key, throw it into a keypass database. If you really want a keystore too, use the one generated by keepass to access the password database. Then you can have your keepass password+keystore to access the private key.
Thanks for the tip. I downloaded the installer file from a pc with internet, sent that over to the mac to try to install it there but was told that I can't open the application since Microsoft Windows applications are not supported on the mac.
Installer for chrome? Regardless, you want the mac installer since it's going on a mac. I think this should help. https://support.google.com/chrome/answer/95346?co=GENIE.Platform%3DDesktop&hl=en
Hello Tom,
I really like your guide and appreciate you sharing some of your security wisdom. However, I felt something missing in your guide and hoped that maybe someone in the comments would address this question. Although it was 4 months ago, someone did indeed address the question of adding more wallets (for different currencies) to the usb wallet. This is of particular interest for those possessing a diverse portfolio. You answered in the case of NEO that if its wallet were to possess offline support it could be added.
As it was 4 months ago, I figured that the latest surge in the altcoin world may have aroused some interest in you too resulting in considering to add more different wallets to your portfolio. I have the following questions regarding this:
I am quite new to this space, but am at the same time very much intrigued.
Hi, thank you for tutorial. I'm kinda wondering how to enable tor browser in tails to open local files because I can't open index.html (keep getting denied).
Make sure that the file is located in the right directory. Tor doesn't have access to any files outside the Tor folder, remember to stay in the persistent volume too if you don't want things to be reset. Let me know if that solves it for you!
Yes, that's it. Thank you very much.
Awesome! BTW, I'm running a giveaway for some SBD this week and you're already halfway entered with these comments. If you follow my blog you will have a chance to win a bit over 10 SBD at the end of the week :)
There's still a few days left to enter my SBD giveaway, see this post for more info!
thank you @tomshowom
a most excellent guide.
i have recommended this post.
in my comments to post on buying EOS on MEW>
i wish i could have put it in the body of the post.
https://steemit.com/eos/@marionjoe/totally-mad-eos-up-423-on-www-hitbtc-com
Hey thanks! BTW, I'm running a giveaway for some SBD this week and you're already halfway entered with these comments. If you follow my blog you will have a good chance to win a bit over 10 SBD at the end of the week :)
Thanks for this three part guide! Well written, concise and really informative! I have a question regarding BIP 39/ BIP 44 standards, to which I cannot find a clear recommendation anywhere online.
For security reasons, do you recommend testing the newly generated addresses within your wallet (e.g. bitcoin, ethereum, ripple) with a small in- and outbound transaction, or will the risk of having your public key exposed outweigh the risk of "corrupt" private/public key pairs being falsely generated through the BIP 39/ BIP 44 standard?
Thanks for your reply!
There's no security risk with exposing your public address, but it is a privacy risk. If you don't want that address to be connected to another public address you use, then transfer the amounts from an exchange (they mix coins and give new addresses for every transaction on many exchanges.)
Really though, as long as you can access the public key through the private key multiple times, there's no reason to test it through transactions. You're only testing to make sure the network functionality works for your wallet by doing that, not whether or not you can access the wallet. It's pretty safe to just double/triple check that your private key accesses the same public key.
I say private key, but it could be mnemonic seed phrase or whatever else is used to derive the private key too.
Thanks for your answer! So if I understand this correctly, you are saying that there is no risk that private/public key pairs are falsely generated (do not match!) through the BIP 39/ BIP 44 standard? So if I generate any public key within my wallet there is no need to test whether I can actually access it with the private key (e.g. sign messages, transfer funds)?
I was thinking specifically with MEW in mind, where you input the private key/seed phrase into the "View Wallet Info" tab. With this, you know your private key -> public key without having to send a transaction.
Sorry if it was just bad wording, but this is incorrect. You generate a private key, and the private key's Keccak-256 hash (last 20 bytes) is what ends up being your public key. You do need to make sure that the private key accesses the same public key for every instance of storing your private key, not because the math won't work, but because the private key could've been corrupted or copied wrong.
Thank you! :)
I like it, really great setup.
Really great guide. I followed the steps and it worked fine until I came to the point where I should test MEW in off-line state. Unfortunately, only text and codes shows up on a white background in the Tor browser, it was not possible to generate wallet/keys either.
I've used 'etherwallet-v3.10.7.3.zip', kept the folder structure and activated index.html. I have also tried some earlier MEW versions, and have experimented with different settings in Tor, e.g. allowing 3rd party cookies, nothing seems to help. Any ideas what went wrong?
I'm using Tails v.3.3 with Tor v.7.0.10.
I have a screenshot from Tor, but not sure how to add.
This seems to be something that happened recently with Tor. The Tor Browser persistent volume isn't getting the right permissions in AppGuard so it's not processing CSS. See https://trac.torproject.org/projects/tor/ticket/24243. I still haven't found a solid answer to this, but I think an older version of Tails (without getting updates) will fix things.
Tails v3.2 is bundled with Tor 7.0.6, which does not have the defect mentioned in the ticket linked above, and therefore is usable with local web content. It can be acquired here:
https://web.archive.org/web/20171103181439/https://tails.boum.org/torrents/files/tails-amd64-3.2.torrent
Tails 3.4. is out. Maybe it solves the problem.
Unfortunately, Tails`s 3.4 Tor is not work as well as Tails 3.3. Only 3.2 is working ok!
Tails 3.5 was released on Jan 23, has anyone tried using it? Does TOR work there?
Tested Tails 3.5, but unfortunately same problem exists with TOR. Also tested Tails 3.6, released March 13, same problem again! I've not tested Tails 3.6.1.
I spent some time on this and came up with a suitable workaround. Simply find a portable browser app for Linux and copy it into the Persistent Volume. Just run it from there and open up the MyEtherWallet index.html. I used the Firefox Appimage located here: https://www.linux-apps.com/p/1168996/
Works great! Hope this helps.
Hello Tom, thanks for the guide. The whole point of it is to not go online with Tails. What do you think of "Discreete Linux"?
https://www.privacy-cd.org/
"Discreete Linux is an isolated offline working environment. Discreete Linux considers a reliable and permanent separation of the data and cryptographic keys to be protected from non-trustworthy networks as an indispensable safety line against targeted "Advanced Persistent Threats". Therefore the support for network hardware of all kinds has been removed from the system kernel of Discreete Linux. This is not only important as a protection against the intrusion of Trojan Software, but also for downstream security lines"
Any offline OS will suffice, but they need to be run natively, not in a VM on an online host. I like Tails for the amnesic aspect, which helps guarantee that no malware is present on the system. It is also documented well and has a lot of tools in place that make it a nice option for crypto.
Alright. Another question concerning the guide: You worte to always physically disconnect the internet, e.g. by turning off the router. Wouldn't it be more easy to completely disable the network deamon of Tails? On quora I read " If you really get paranoid go into /etc/init.d subdirectories and disable start of the internet daemon xinitd to assure that nothing can ever connect to you." I couldn't find this daemon on Tails, tough. Do you have any idea?
Physical disconnection is a partial move towards total black-box conditions, like inside a Faraday cage where no electrical emissions are leaking out. Ideally, this is how you'd want to generate/access private keys if you're doing so electronically.
Disabling the device drivers themselves on something like Linux is a valid solution for keeping info from leaking off of that system, but on a phone or other less open-source systems you can potentially still be connected even when wifi is turned off.
Additionally, you don't really want Alexa listening while you recite your mnemonic phrase aloud while verifying it, or your smart phone to be pointed at the screen/keyboard while sensitive info is being used. We surround ourselves with top-quality surveillance equipment, and the privacy-minded person will take all the steps (even ones that can be argued to be excessive) to protect themselves & their most valuable information.
Thank you! Yes, this seems to explain the problem. I will try find a older version of Tails.
i'm so tired of TAILS. they try so hard to be the most private OS ever that you literally can't use anything on it with the exception of stuff designed to run on tails. which is like, monero wallet and thats it.
I guess you missed the use case described in the article above that you have now commented on. If you don't have a use for Tails, maybe just don't use it?
I have installed Tails, but am having trouble using KeePass with MEW. I got to the point of opening a new wallet with the password generated in KeePass. How do I open MEW using this password in KeePass? Where do I store my KeePass database? Thanks for the help...
With MEW, you have two options for accessing your wallet to sign transactions.
It's really up to you where/how you store the password and UTC file. In the guide I recommend storing both along with the private key all in the keepass database so that there's less to memorize and keep up with (which doesn't add to the security of a doubly encrypted system anyway).
As far as using keepass, you use the keyfile (stored on a separate USB) and the master password to access the database. From there, I would just use the stored private key to unlock the wallet in MEW to sign the offline transaction. Otherwise you need to download the UTC file from keepass and drop that into the Tor persistent directory (so that MEW can see it) and also copy the password from keepass.
The actual keepass database should be stored in the persistent volume of Tails. You can make redundant backups of it anywhere though, as long as it's separate from the keepass keyfile and/or master password if you are choosing to store that somewhere.