How to Get Free HTTPS Certificates via acme.sh? (Renewing SSL for api.justyy.com)
Let's Encrypt provides HTTPS Certificates if you are already using CloudFlare which also manages/issues the free SSL certificates for you. However, with Let's Encrypt, it is not so simple/trivial to get a free HTTPS ceriticate as you will need to verify your domain, and get the certificates and sometimes manually combine multiple certs (chain).
Some other organisations such as ZeroSSL offer 3 free certificates each up to 90 days before you have to pay them monthly (around 20 USD) to renew or get more certificates.
Easy HTTPS Ceriticates Issuing with ACME.sh
With acme.sh everything become so easy and simple to issue/renew the SSL Certificates. For more installation you can refer to github: https://github.com/acmesh-official/acme.sh
Step 1: Installation
curl https://get.acme.sh | sh
After installation, there will be a daily crontab job to check the status of all the certificates that have been issued.
Step 2: Issue a Certificate
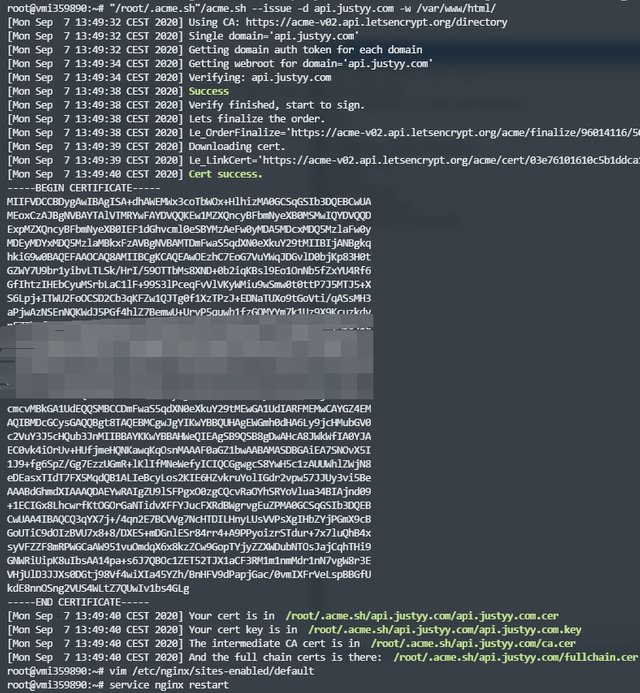
"/root/.acme.sh"/acme.sh --issue -d api.justyy.com -w /var/www/html/
I have issued a new SSL certificate for api.justyy.com here the -w parameter specifies the root folder - which could be Apache2 or Nginx (in order to verify the domain). Then after the HTTPS certificate has been issued - you would need to update the path in the Apache2 or Nginx config file to point to the new certs paths.
The Nginx default site configuration looks like:
root@vmi359890:~# cat /etc/nginx/sites-enabled/default | grep acme
ssl_certificate /root/.acme.sh/api.justyy.com/fullchain.cer;
ssl_certificate_key /root/.acme.sh/api.justyy.com/api.justyy.com.key;
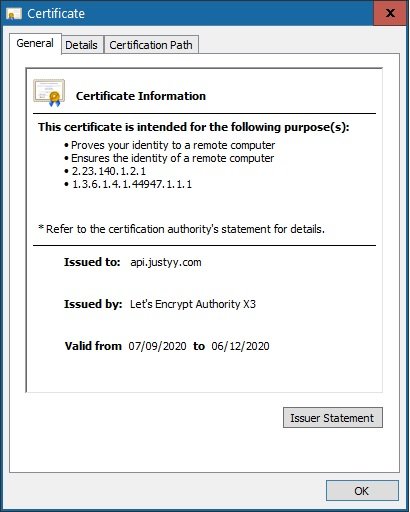
And when we restart the nginx (or apache2) server, you will see the new Certificates issued (by checking the browser padlock).
Automatic Issue Renewal
There will be an entry in Crontab to check daily and renew your HTTPS certs - this is just awesome!
53 0 * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null
We can also run the following:
"/root/.acme.sh"/acme.sh --install-cert -d api.justyy.com \ --key-file "/etc/nginx/ssl/key.pem" \ --fullchain-file "/etc/nginx/ssl/cert.pem" \ --reloadcmd "service nginx force-reload"
That tells acme.sh where to install the certs and tell it how to restart/reload apache2/nginx when HTTPS/SSL certificates are renewed. Please note after this, you have to modify the config to point to the new location of the certs installation path in this case /etc/nginx/ssl
--EOF (The Ultimate Computing & Technology Blog) --
Reposted to Algorithms Blockchain and CLoud
Follow me for topics of Algorithms, Blockchain and Cloud.
I am @justyy - a Steem Witness
https://steemyy.com
Steem On!~
Every little helps! I hope this helps!
If you like my work, please consider voting for me or Buy Me a Coffee, thanks!
https://steemit.com/~witnesses type in justyy and click VOTE
Alternatively, you could proxy to me if you are too lazy to vote!
Also: you can vote me at the tool I made: https://steemyy.com/witness-voting/?witness=justyy
拍拍
感谢,回赞。
拍行长👏🏻
感谢,回赞。