Introducing DNS Resolver for Tor

In case you haven’t heard yet, Cloudflare launched a privacy-first DNS resolver service on April 1st. It was no joke! The service, which was our first consumer-focused service, supports emerging DNS standards such as DNS over HTTPS:443 and TLS:853 in addition to traditional protocols over UDP:53 and TCP:53, all in one easy to remember address: 1.1.1.1.
As it was mentioned in the original blog post, our policy is to never, ever write client IP addresses to disk and wipe all logs within 24 hours. Still, the exceptionally privacy-conscious folks might not want to reveal their IP address to the resolver at all, and we respect that. This is why we are launching a Tor hidden service for our resolver at dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion and accessible via tor.cloudflare-dns.com.
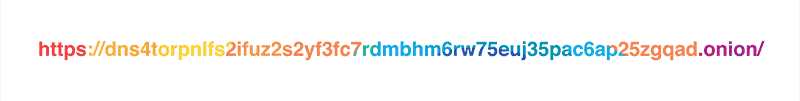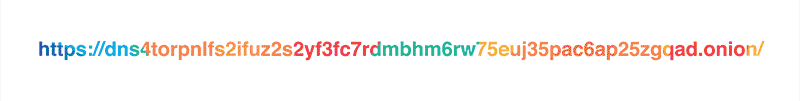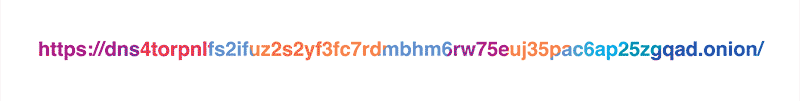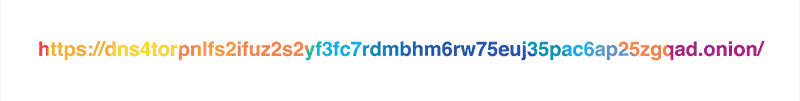
NOTE: the hidden resolver is still an experimental service and should not be used in production or for other critical uses until it is more tested.
Crash Course on Tor
What is Tor?
Imagine an alternative Internet where, in order to connect to www.cloudflare.com, instead of delegating the task of finding a path to our servers to your internet provider, you had to go through the following steps to reach Cloudflare:
- You calculate a path to your destination, like this:
You -> Your ISP -> X -> Y -> Z -> www.cloudflare.com.
- You encrypt your packet with Z’s public key, then with Y’s, and finally with X’s.
- You submit the result to X, who decrypts with their private key;
- X submits the result to Y, who decrypts with their private key;
- Y submits the result to Z, who decrypts with their private key to get the original packet;
- Z submits the packet to www.cloudflare.com.
If everyone plays their roles correctly, it is possible to ensure only the entry relay X knows your IP address and only the exit relay Z knows the website you’re connecting you, thereby providing you with privacy and anonymity. This is a simplified version of Tor: a collection of volunteer-run computers and servers around the world acting as relays for a huge network built on top of the Internet where every hop from one relay to the next peels one layer of encryption, hence its name: the onion router.
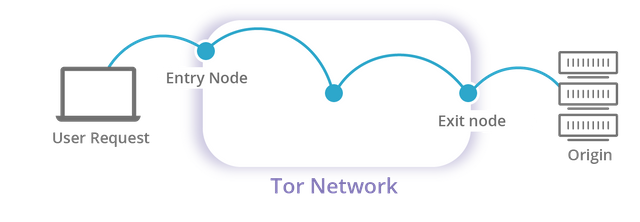
What are Tor hidden services?
Keeping internet users anonymous is not the only function of the Tor network. In particular, one caveat of the procedure above is that the connection is still accessible by the exit relay and anyone sitting between there and the destination, including network providers. To solve this problem, and to also provide anonymity for content publishers, Tor allows for hidden services. Hidden services are Tor nodes that advertise their public key, encoded as an address with .onion TLD, and establish connections entirely within the Tor network:
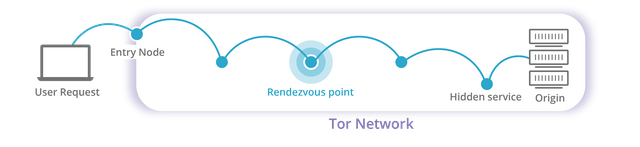
How do you resolve a domain while using Tor?
The process of returning an IP address given a domain name is called DNS resolution. Since Tor still uses IP addresses, you still need to do DNS resolution to browse the web over Tor. There are two common methods to resolve a domain name when using Tor:
- Resolve the name directly, then talk to the IP address through Tor;
- Ask a Tor exit relay to resolve the name publically and connect to the IP.
Clearly, the first option leaks your IP to your DNS resolver and, unless your client uses DNS-over-HTTPS or DNS-over-TLS, it leaks your destination name to your ISP. What is less obvious is that the second option can open you to manipulation attacks such as DNS poisoning or sslstrip by bad relays. This is where our new service comes in:
- Ask a hidden resolver service!
How does the Cloudflare hidden resolver work?
In a few words, our hidden resolver service is a Tor hidden service which forwards all communication on DNS ports to the corresponding ports on 1.1.1.1, hence the apparent client IP is an internal IP rather than yours. There is, however, more than meets the eye.
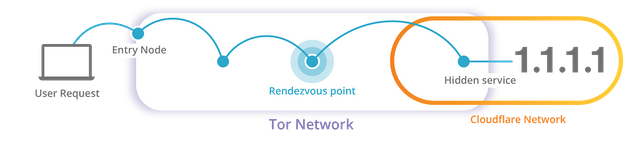
##Is the hidden resolver secure?
One glaring difference between using 1.1.1.1 and this service is that the .onion address is "dns4tor" plus 49 seemingly random alphanumeric characters. This 56 character long string, in fact, contains a full Ed25519 public key which is used to secure communication with the hidden service. This poses a number of challenges towards usable security:
- How can the users make sure that that the address is correct?
We simply bought a certificate with tor.cloudflare-dns.com as subject name and the .onion address as a subject alternative name. This way, if you’re in the right place, you should see this:
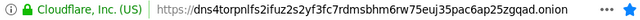
- How can the users remember this address?
We don’t think you should need to remember this address. Ideally, all you would need to do is go to https://tor.cloudflare-dns.com and have the browser route your request to the .onion address. This is possible using the "Alt-Svc" HTTP header which is an optional header notifying the browser that the resources can be accessed from an alternative network location, possibly using a different protocol. Thanks to Mozilla, using .onion addresses as alternative services is now possible in Firefox Nightly.
Think of this feature like opportunistic encryption: once your browser receives an Alt-Svc header indicating that a .onion address is available for tor.cloudflare-dns.com, if it knows that .onion addresses can be accessed (for instance through a SOCKS proxy), it attempts to check that the alternative service has the same or a higher level of security. This includes making sure that it is possible to connect to the hidden service using the same certificate and Server Name. If that is the case, the browser uses the alternative service instead, therefore ensuring that your future requests do not leave the Tor network.
Is the hidden resolver fast?
Here is a thought experiment: suppose between each two points on Earth there is a fiber-optic cable, capable of lossless transmission of packets at the speed of light.
Using a back-of-the-envelope calculation it’s easy to see that, on average, each packet traverses a distance equivalent to a quarter of the circumference of the Earth in about 33ms, while each Tor packet takes about 200ms to go one and a half turns around the Earth before reaching a hidden service; that’s three turns for a round trip that ensures anonymity of both parties.
Cloudflare, however, does not require anonymity for its servers, which is why we can reduce the number of relays to just three by enabling an optional setting for hidden services that prioritize lower latency over location anonymity of the service. To emphasize, this does not impact client privacy or anonymity whatsoever. Indeed, as you may have noticed, in the first hidden service image the origin is three hops away from the rendezvous point whereas our hidden service is only one hop away.
We are actively working on developing ways to make this service faster and ensure it has as little downtime as possible.
Why should I use the Cloudflare hidden resolver?
First and foremost, resolving DNS queries through the Tor network, for instance by connecting to Google’s 8.8.8.8 resolver, guarantees a significantly higher level of anonymity than making the requests directly. Not only does doing so prevent the resolver from ever seeing your IP address, even your ISP won’t know that you’ve attempted to resolve a domain name.
Still, unless the destination is a hidden service, passive attackers can capture packets exiting the Tor network and malicious Exit Nodes can poison DNS queries or downgrade encryption through sslstripping. Even if you limit your browsing to only HTTPS sites, passive attackers can find out which addresses you’ve connected to. Even worse, actors capable of comparing traffic both before it enters the Tor network and after it leaves the network can potentially use the metadata (size, time, etc.) to deanonymize the client. The only solution, then, is to eliminate the need for Exit Nodes by using hidden services instead. That is what our hidden resolver offers.
Moreover, if your client does not support encrypted DNS queries, using a hidden resolver can secure the connection from on-path attacks, including BGP hijacking attacks. This means having the same level of security for DNS-over-UDP and DNS-over-TCP as DNS-over-HTTPS and DNS-over-TLS provides.
Your personal anonymity, however, is not the only reason why you should use this service. The power of Tor in ensuring everyone’s anonymity rests on the number of people who use it. If only whistleblowers, for instance, were to use the Tor network, then anyone connecting to the Tor network would automatically be suspected of being a whistleblower. Therefore the more people use Tor to browse memes or to watch cat videos on the Internet, the easier it will be for those who truly need anonymity to blend in with the traffic.
One barrier to using Tor for many users is that it is simply slow, so I can try to sympathize with those who wouldn’t sacrifice quick website load times to help keep activists and dissidents anonymous. That said, DNS requests are small in size and since most browsers and operating systems cache DNS results the total traffic is not significant. As a result, using the hidden resolver will only slightly slow down your initial DNS request without slowing down anything else, while still contributing to the overall anonymity of the Tor network and its users.
Why should I trust the Cloudflare hidden resolver?
Using a hidden resolver ensures that your ISP never finds out that you’re resolving a domain, the Exit Nodes don’t get a chance to manipulate DNS replies, and the resolver never finds out your IP address. However, the unique benefit of using the Cloudflare hidden resolver is combining the power of Tor with all privacy-preserving features of the 1.1.1.1 resolver, such as query name minimization, as well as a team of engineers working on improving it at every level, including standards like DNS-over-HTTPS and DNS-over-TLS.
As CEO Matthew Prince said about two years ago, anonymity online is a cause we value at Cloudflare. In addition, when we announced the 1.1.1.1 resolver we committed to taking every technical step to ensure we can’t know what you do on the internet. Providing a way to use the resolver through the Tor network and making it as fast as possible is a big step in that direction.
How to set it up?
The hidden resolver supports every DNS protocol that 1.1.1.1 supports, only over the Tor network. However, since not every DNS client is capable of connecting to the Tor network, some hacking is required to get it to work. Here we will explain how to set up DNS-over-HTTPS provided from the hidden resolver, but for all other scenarios head to our developers page to get the details of how to use the hidden resolver.
Remember cloudflared?
Here is how you can set up cloudflared to start a DNS client that uses DNS over HTTPS, routed through the Tor network:
- First, start with downloading cloudflared by following the regular guide for Running a DNS over HTTPS Client.
- Start a Tor SOCKS proxy and use socat to forward port TCP:443 to localhost:
socat TCP4-LISTEN:443,reuseaddr,fork SOCKS4A:127.0.0.1:dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion:443,socksport=9150
- Instruct your machine to treat the .onion address as localhost:
cat << EOF > /etc/hosts
127.0.0.1 dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion
EOF
- Finally, start a local DNS over UDP daemon:
cloudflared proxy-dns --upstream "https://dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion/dns-query"
INFO[0000] Adding DNS upstream url="https://dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion/dns-query"
INFO[0000] Starting DNS over HTTPS proxy server addr="dns://localhost:53"
INFO[0000] Starting metrics server addr="127.0.0.1:35659"
- Profit!
Tagged with Crypto, 1.1.1.1, Tor
Cloudflare Blog Post
Previous Posts
 Follow Me|| SomethingSubtle.com || New to Steem? || Minnow Support
Follow Me|| SomethingSubtle.com || New to Steem? || Minnow Support
Finally they do....!!
a very good post, a good start to start a work, I like the post you share @somethingsubtle

and i am very inspired. thanks as regards introduction @muktariza011095
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by SomethingSubtle from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.