Solitaire Encryption: Low Tech High Security. A how to
The Solitaire Cipher
source
In this post, I'm going the explain how to encode and decode using the low tech, high-security Solitaire encryption designed by Bruce Schneier and featured in Cryptonomicon as the pontifex cipher but before I go too far I'm let me suggest some additional reading.
First is my previous post examining just how staggeringly complex a deck of cards really is Whats in a deck of cards.
and Second
Cryptonomicon by Neal Stephenson Written 1999.
Without any exaggeration, this book is the most educated work of fiction I have ever read for may this book may feel like a chore but I could not put it down.
This prophetic book set in the two times frames of World War II and the 1990's is nearly a mathematics essay if they were ever to put a fiction book of the maths syllabus at high schools this should be it well this and Flatland.
In the WWII timeframe, we follow a group of code breakers employed to combat Axis encryptions including Enigma and have amazing supporting real-world characters like Alan Turing and Douglas Mac Auther it is amazing how much you will learn from this fictionalized Bletchley Park and Alan.
It turns prophetic when we are in the 90's time frame following a group of people whose ultimate goal is the establishment of a cryptographic data haven, to facilitate anonymous internet banking, and to use cryptography to develop "Digital Gold" that would function just like cash but for the net.
Yeah 10 years before the Bitcoin whitepaper this book was laying the foundation, yeah, that's right our mate Satoshi was probably a Stephenson fan.
The Encryption.
Just a heads up this is a manual process it is not quick either to explain or to do and despite its name does not involve playing a game of solitaire.
Imagine your in some dystopian world where the government tracks all your digital information via some hyper-advanced system I don't know maybe its called PRISM perhaps they go a step further and outlaw any device that can transmit messages they can't read what to you do.
Encryption is so damn old the Ancient Greeks knew about it
What you'll need.
Paper
Decks of cards including the two jokers.
Patience this is complicated
Useful References.
Card values to get to the output cards.
J = 11, Q = 12, K = 13
Value of output cards
A♥ through K♥ = 1 through 13, A♠ through K♠ =14 through 26
Solitaire Algorithm.
I will explain keying the deck in a little bit but let's assume I have keyed the deck and produced this sequence.
Feel free to arrange a deck and follow along when arranging your deck notice the single A and B these represent the two jockers, the jockers in most decks are usually different in design and you will need to decide which one will be "A" and which will be "B". If your jokers are identical you will need to mark them in some way to identify them.
Decide what message you want to encode for this example I'm going to use the phrase "STEEM POWER" there are two reasons for this, one because everyone loves steem power and two because it fits with the secret spy tradition of grouping the characters of a message into sets of five. "LIKEI FTHIS WASTH EMESS AGEXX"
Holding deck face up the find Joker "A" and swap it with the card directly below it then find Joker "B" and move it two cards lower in the deck. think of the deck as a loop e.g. Joker "b" was the bottom card it would be placed under the second card on the top in addition always perform the movement of "A" first.
Next, we make a triple cut, that is we swap everything above the joker closest to the top with everything below the last joker in the deck. Leaving everything between the two in its place
EXAMPLE
If these cards represent your entire keyed deck with jokers in place.

These show the joker shifts.

And these show how the triple cut works

Now we do a count cut look, at the card at the bottom of the deck and put it aside for a second, convert it to a number between 1-53 using that reference "card values to get output cards" I made for you above.
If you have been followed along with a deck you should have the Q♥ so the Q = 12 plus 26 for the ♥ and we get 38. Count out 38 cards from the top being careful not to shuffle any out of order and put these on the bottom of the deck except we put that card you put aside back on the bottom.
EXAMPLE
If these represent your cards after the joker triple cut the 3♣ means a count cut of 3 cards.
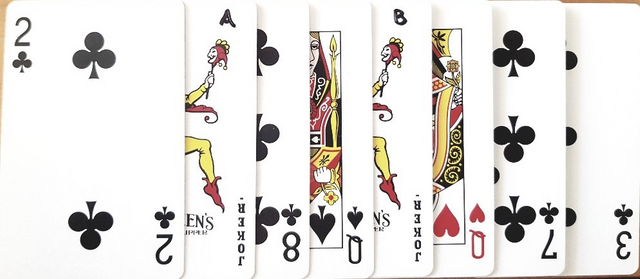
These show the cut and the 3♣ remaining in position.

Now we look at the top card and again using "card values to get output cards" convert the card into a number between 1-53 in our case we have A♥ that's a value of 27.
Countdown that many cards with the top card number one write down the card directly under our number so if we count down 14 we record the 15th as our output card, again being careful not to change the order of the deck as we count and not remove it from the deck this set will not change the deck order from what it was at the beginning of step 5. Jokers are a wild if you hit one as you start again from step one with your current deck arrangement.
Our output card, in this case, is 2♥ at this point we use a different value calculation for the output card I have also included this above using those values the 2♥ has a value of 2 its this value that we will use in the encryption of a single character. You will need to repeat this process for each letter of your message, you can now use step 1 - 7 to produce this is done with the deck in its current state
DON'T REKEY YOUR DECK, DON'T DROP YOUR DECK, DON'T SHUFFLE YOUR DECK, THE KEY WILL BREAK, DO TAKE YOUR TIME THIS IS A REPEDATIVE TASK AND A LASP IN CONCENTRATION CAN RUIN A LOT OF WORK, TRUST ME
Encrypting
Convert your message into numbers based on its position in the alphabet and add the plaintext number values with the values of the output cards (modulo 26) that is if the combined value is greater than 26 subtract 26 from the total result, rather than make you go all the way through those seven steps above for each one I have completed the keystream for you aren't I generous.
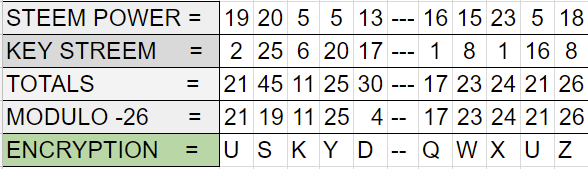
Having added the plaintext values with the keystream numbers and subtracting 26 where appropriate you can then convert the output into the encrypted text based on the outputs corresponding alphabetical position as in the above table.
Decrypting.
Decrypting a message encoded is solitaire is just as time-consuming as encoding one the receiver must obviously have a deck of cards keyed in the same manner as the sender, having the encrypted message and the keyed deck the receiver will be able to produce the same keystream from the deck equal to the number of characters in the encrypted message using the process I described above.
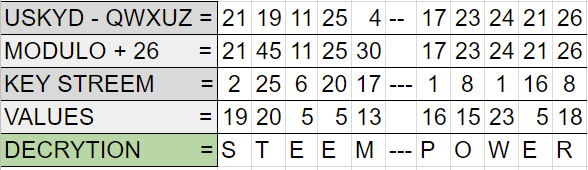
Convert the letters in the encoded message to number values based on their position in the alphabet and subtract the values produced by the keystream. If the value of the encoded letter is less than the value of the keystream we add 26 to the value of the encrypted character before subtracting the keystream.
So S= 19 and keystream = 25 would become 19 + 26 - 25 The values produced by following step 1 above represent the alphabetical position of the original message and when we go ahead and convert those numbers we get back to our original message of STEEM POWER.
Keying the deck.
There are a few options to ensure that both the sender and receiver are working from identically keyed decks.
You can shuffle a deck, jokers included and then arrange an identical deck and give one to an individual that you think you may need to send an encrypted message to at some point in the future the major drawback is that this provides no option for reply without the same key being used which is a major security issue essentially this option should be treated like a onetime pad.
One suggestion is a shared passphrase between sender and the receiver like "Ninjas Rock"
This passphrase will be used in use that as an extra step in the solitaire algorithm inorder to key the deck.
Start with the deck in a fixed order; lowest card to highest card, in the suit order used in bridge order clubs, followed by diamonds, hearts, and then spades, then joker A then B.
A-K♣, A-K♦, A-K♥, A-K♠, A,B Now we do steps 1-4 of the solitaire algorithm but instead of continuing to step 5 we convert the first character of the passphrase into ints alphabetical number value and do a second count cut using that value, remember to put the top cards just above the bottom card in the deck just like in the normal step 4.
The advantage of using a passphrase is that the deck can be keyed for additional messages by progressing down the characters in the passphrase e.g if the first message was coded with a deck keyed by the first letter in the passphrase the response keyed deck can be done with the second and so on..
Congratulations
While it's highly unlikely that you have read all the way down here if you did you now have the information to send encrypted messages with a deck of cards.
Kind Regards
Peter.
My Wife is also a great Steemian worth a follow check out her most recent posts here.
Ulog #5 - 7 Day Positivity Challenge - DAY 5 - Lemonade Scones Mess & Friends
#17-what-is-it-first-to-guess-right-wins




OK, I couldn't get my hands on a pack of cards - yet - but this has really piqued my interest! It sounds like another case of life imitating art - a novel predicting the rise of digital currency, 12 years before it happened. Sounds like one for the reading list.
Really nice approach to explaining the process. Given how much you liked Cryptonomicon, if you haven't read Stephen's System of the World books, you really should.
hahaha I did!! But I'll have to re-read it to totally understand it :) Kidding! I get it and wished I'd had this information when I was in high school so when the teachers intercepted my notes, they would have been clueless ;)
Congratulations @shai-hulud! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!