[SECURITY HOW-TO] How anyone can avoid losing access to their Steemit Account with LastPass and Duo
Set up a Password Manager with Out-of-Band Authentication to Secure your Steemit Account
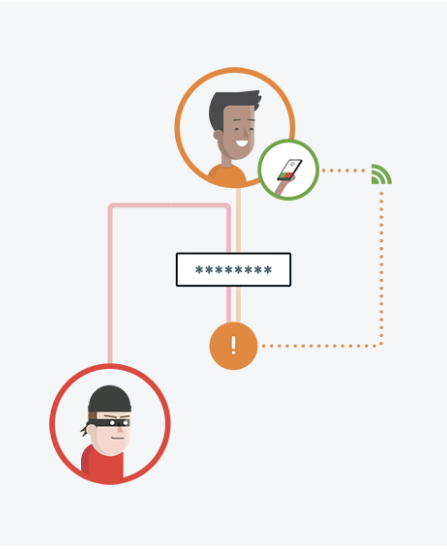
Steemit accounts are growing in value rapidly, making them a desirable target for attackers looking to make a quick buck. Whether by spear-phishing (harpooning?) whales in order to compromise your computer, or by brute-force guessing your password via a dictionary attack, when there is hard-earned SD on the line, extra precautions should be taken in order to prevent takeover and loss of your funds. One easy way to give your account security a major upgrade is to require a second factor to login to your password manager vault. I'll show you how to achieve this in the following tutorial by using LastPass as a password manager, coupled with Duo as a multi-factor authentication provider.
Step #1: Download LassPass and Create an Account

Go to the LastPass homepage and download the browser extension by clicking "Get LastPass Free."
Go here to create a LastPass account. Note: make sure that your master passphrase is strong and unique. And whatever you do, don't lose it! I suggest a memorable 4 to 5 word phrase that you invent yourself on the spot. (i.e. 3Dwordsmithpranksterhelper DON'T USE THIS)
Log into LastPass from your browser by clicking the extension.
Step #2: Change Your Steemit Password and Add It to LastPass
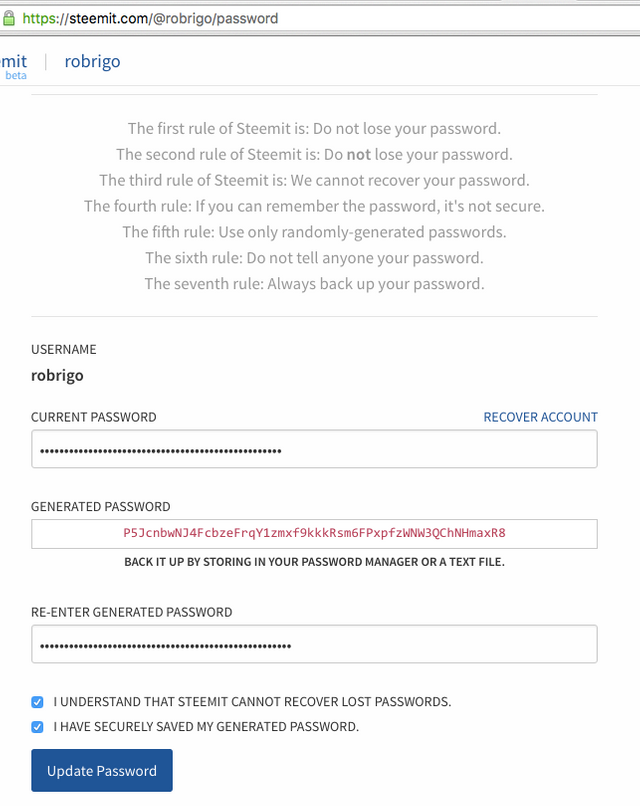
Login to your Steemit account and navigate to your profile's password reset page and copy the generated password.
Next, save the newly generated password. To do this, open LastPass by clicking on the extension and then "Sites."
Now, click on "Add Site".
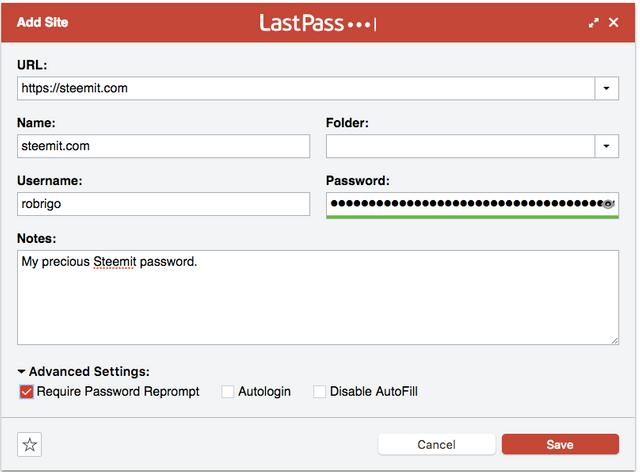
Paste your password into the password field and continue to fill out the rest of the site details. Make sure "Require Password Reprompt" is checked under Advanced Settings.
Step #3: Integrate Duo and LastPass.
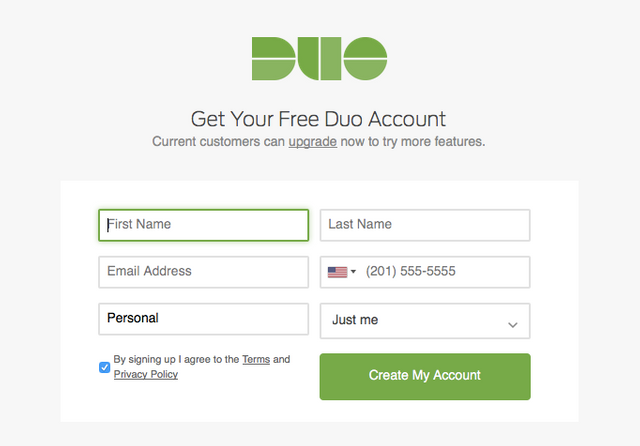
Go to the Duo signup app here and register for a free personal account. Be sure to select "Just Me" for number of users.
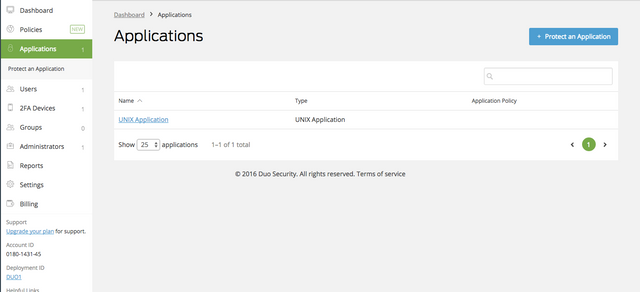
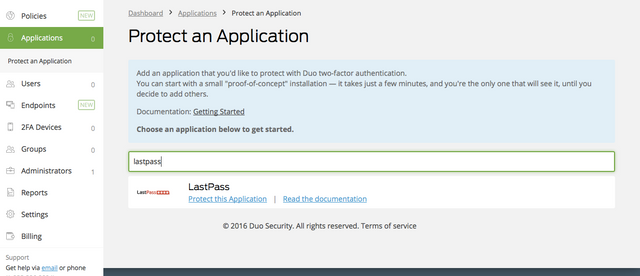
After you are signed up, log into the Duo admin panel, navigate to the "Applications" tab and click the blue "Protect an Application" button
Search for LastPass and click the "Protect This Application" link.
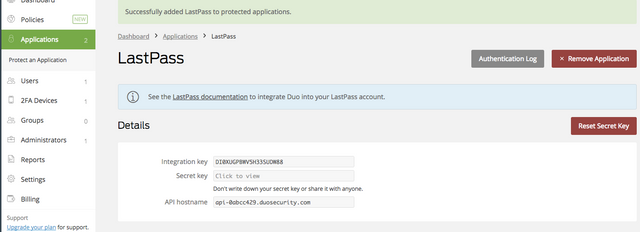
You're almost there! The page you're redirected to contains some mandatory information to complete the setup. Keep the integration key, secret key, and API hostname handy.
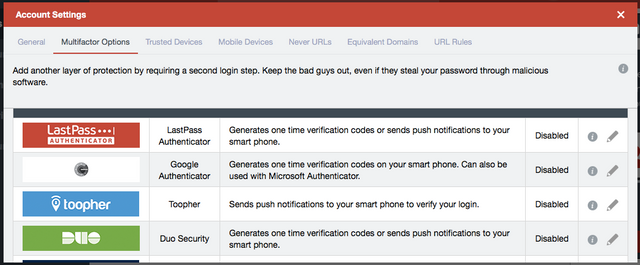
Access your LastPass vault via the extension installed earlier, and navigate to the "Multifactor Options" tab in Account Settings. Scroll down to Duo and click the Edit button.
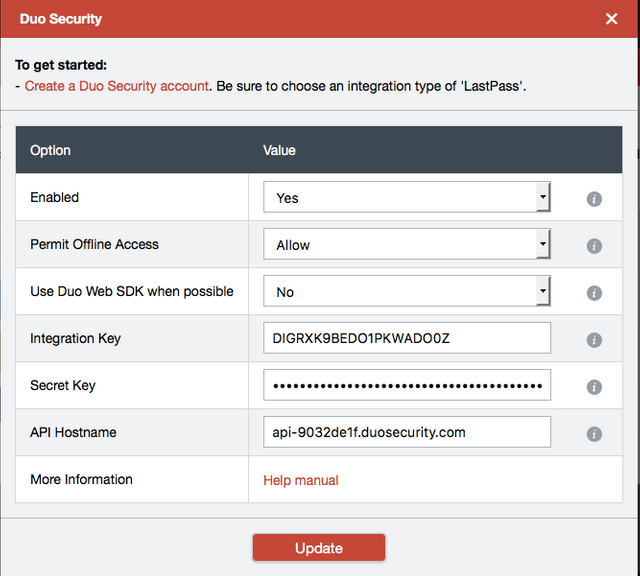
Now it's time to copy the information to link Duo to LastPass. Set "Enabled" to Yes, "Permit Offline Access" to Allow, and "Use Duo Web SDK when possible" to No. Also copy the fields mentioned in #4 from the LastPass application in Duo.
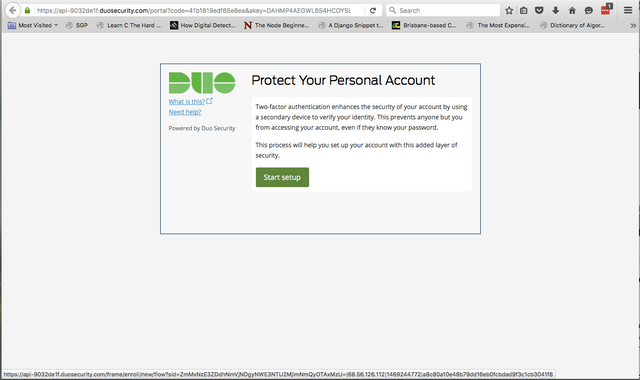
When you hit Update, you'll be prompted to re-enter your LastPass master password that you created earlier. Then you'll be prompted to enroll your smartphone with Duo. To do so, you will need to install Duo Mobile from your device's trusted app store (Play on Android, App Store on iOS). This allows you to use out-of-band two factor authentication, delivered as a push notification.
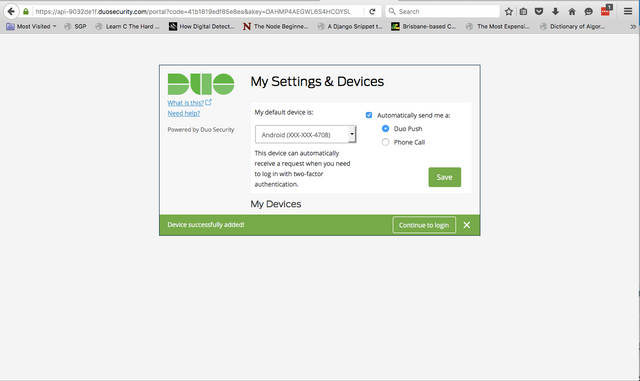
At the end of the device enrollment process, make sure to tick the box that says "Automatically send me a:" and select Duo Push. This will cause a push notification to be automatically sent to your phone via Duo Mobile when you log into your password manager.
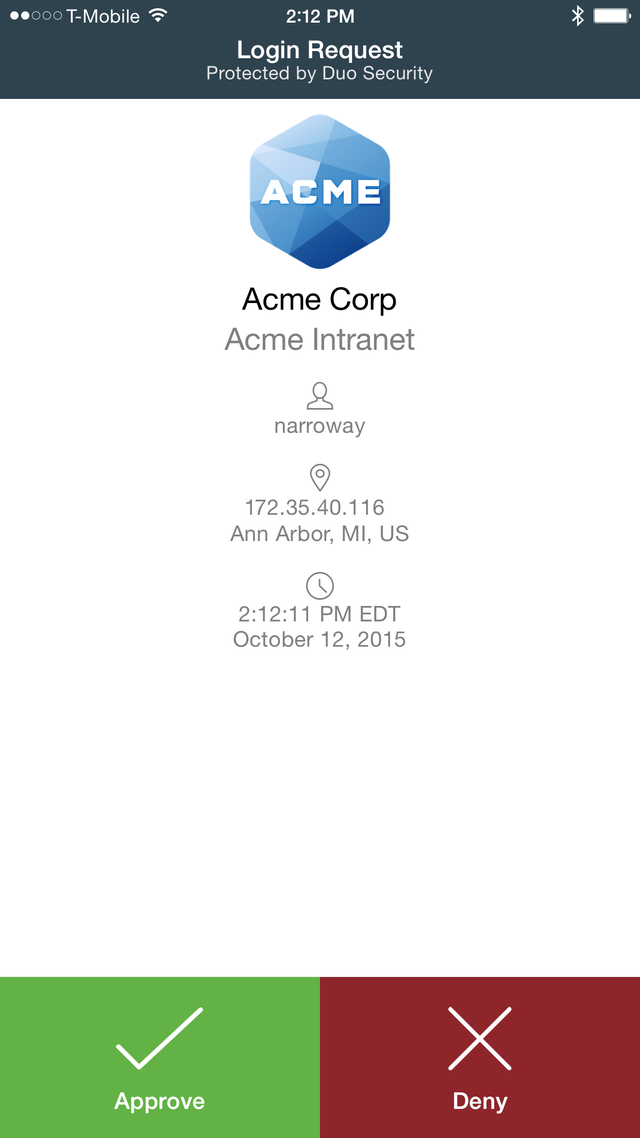
The push notification will have an approve and deny button, allowing you to selectively choose which requests are allowed to authenticate to the password manager. This means that any attacker attempting to access your password manager with stolen credentials, will need to also compromise your smartphone as well. You'll also be notified of this activity because you'll receive a push you did not intend for, allowing you to deny the authentication as fraudulent and thwart the attacker.
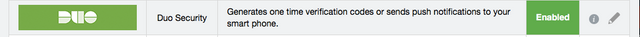
You'll know this all worked out properly if Duo is marked as "Enabled" on the multifactor page in LastPass.
Congratulations! Now you can be certain only you are able to access your LastPass vault stored in the cloud. You can verify that it is all working by logging out of LastPass and back into it. Your phone should receive a push notification to complete secondary authentication. For the scenario where you don't have access to phone service, you can use the code generated by the Duo Mobile app as a fallback instead.
Remember, don't lose your LastPass master password!
Ingrain this into your brain so you'll never forget it. If you absolutely need to, keep it written down and stored in a locked place (ideally a safe). If you're having any troubles getting this set up, please leave a comment with your issue and I'll help you resolve it. Thanks for reading!
#steem #steem-help #newcomers #account-security #duo #security #2FA #lastpass #password #phishing #attack
#account-security #security #steem-help #newcomers #lastpass #attack #steem #2FA #password #phishing #duo
This is a great guide and it is a very good idea for people to do this.
It is important, however, for this community to understand that this 2FA solution is not the same thing as a Steem-specific 2FA solution (a solution which I describe along with other security improvements that I recommend for steemit.com and the Steem blockchain in this post).
For example, if your computer was hacked, you are only partially protected by using the 2FA in this guide. Partial is still better than nothing, so it is a good idea to enable it.
If the hacker installs a keylogger on your computer that sends the keystrokes back to them, then they will eventually compromise your LastPass master password the next time you log in. As @robrigo mentioned, the 2FA enabled in this guide will prevent the hacker from accessing your LastPass password database using that password alone, which is a great thing.
But if your computer is compromised, the hacker could theoretically install a tool that simply waits until the next time you unlock your LastPass database (this means both entering your master password and approving the log in with the Duo app) and then grabs all your passwords from the database. This would be a far more sophisticated attack (particularly if you use LastPass's password autofill feature rather than copying and pasting the password), but it is still a valid concern.
The ideal 2FA solution for Steemit would not allow a hacker to spend your funds even if they had complete root-level access to your desktop/laptop computer alone. This requires utilizing the sophisticated multisig capabilities already available in the Steem platform, and also a separate computer system providing 2FA services (likely by Steemit for example) that has one of the two keys for your account's active/posting authorities (the other of course being the one generated in the browser running on your desktop/laptop computer). In such a setup (where the 2FA service again used an app such as Duo on your smartphone for the authentication), the hacker would have to simultaneously compromise both your desktop/laptop and your smartphone, which is a much harder task than just compromising the desktop/laptop.
Note: They could also just compromise Steemit servers, grab their half of the multisig keys, and feed you malicious Javascript which steals your half of the multisig keys, but that is a threat that already exists today without multisig. The way around that would be to have a separate Steemit app existing outside of the browser that was signed by cold Steemit keys and in which the user has to explicitly approve upgrades to the app after the existing installation of the app verifies the upgrade software's signature is good. In such a case, a compromise of Steemit's online servers would functionally mean a graceful degradation of the 2FA system to the current 1FA system.
Thanks for clarifying the difference between on-chain 2FA using multi-sig and 2FA for your password manager. I hope to see an on-chain solution that is usable in the near future!
For some reason I can't edit this article, so I'm going to post an addition I wanted to make here.
In order to harden this process, make sure that you never set the LastPass extension to automatically remember your master password. And always log out of your password manager when you aren't using it. These actions should be taken so that any malware that could potentially end up on your local computer cannot compromise the keystore with your Steemit account password.
If you're configured properly, your phone will automatically receive a 2FA when logging back into LastPass extension, and your workflow won't be interrupted too much.
Excellent stuff. Upvoted to get this post up top and I would encourage everyone else to do the same.
I'm glad you're finding it valuable @condra!
@robrigo I'm concerned that by insisting people have huge/complex passwords for Steemit, they may simply be replacing the hacked passwords problem with a new one - lost/forgotten passwords.
My worry with using a third party password management service (online or in software) is that peoples laptops die, or get stolen. Also, when people have huge passwords for certain services, some will end up emailing the passwords to themselves! It's also open to abuse via phishing scams.
I wish there was a way to have a 2 step verification process, or that STEEM accounts could only be accessed a limited number of times per day before going into a safe mode for 24 hours.
Very keen to hear your thoughts on all this.
@condra these are all real world concerns to have. Thanks for raising the question- I'll try my best to address it.
The impetus is definitely on the user to understand the risks of using cryptocurrency and understand how to secure it properly. This can be a large burden for people, but it's important they make an honest effort to take the proper precautionary measures. The key is to strike a balance between security and usability. Password managers and out-of-band 2FA help to achieve this balance. There's actually an interesting research paper that concludes it is not worth it economically for users to try following the vast swathes of security advice, but this paper doesn't take into account the fact that password recovery mechanisms don't work for everything, such as services like LastPass and Steemit.
When you make a master passphrase for your password manager, you need to make an effort to change your behaviors to remember that. Like I said, store a copy of it written down in a safe. Or just brainwash yourself to remember it by typing it in over and over again. Like a muscle, remember your passphrases can be viewed as something that needs to be trained. It's a skill that requires practice and dilligence.
One benefit to LastPass is that your vault can be accessed from any device, making it convenient. But this property also means you should put 2FA in front of it, to prevent attackers that are able to successfully guess your username and password for LastPass. By using a password manager, they don't actually have to remember the huge passwords. You let the extension do that lifting by "autofilling" the password into the correct forms. When you store a site into lastpass, when you go to the login form for that site, there should be an autofill icon in to the right in the text input, that will detect the correct login to use for the site that you're on based on the domain.
Also, by using 2FA on your password manager, you only have to 2FA the first time you log into it. Now, best practice would be to log out of the password manager when you are done using it, so it isn't left open, but that's up to you. This way, you don't need to 2FA everytime you log into Steemit if you don't want to. I personally like to log out of my Steemit account when I'm not on it, as well as my LastPass account. This gives me the peace of mind that my accounts are not accessible by someone who has gained access to my laptop.
Oh man. Thanks for such a comprehensive answer. That's a whole post unto itself!
You're very welcome.
Someone tried to add me on Facebook today, using my friends name. They even chatted to me briefly before I busted them.
I've written an article about phishing and social engineering side of things, somewhat separate from password security.
https://steemit.com/steemit/@condra/public-wallets-and-the-target-on-your-back-original-article
Anyway, if you have anything to contribute in the comment section, I'll be sure to credit you in the article.
Brilliant! A few days ago I did this post giving the idea to implant something similar. You make it possible.
Regards!
https://steemit.com/security/@amartinezque/steemit-google-authenticator-2-step-verification-what-do-you-say
I'm glad you're finding it useful!
Great job man! Thanks for sharing this. It's a really valuable starting point for people who have never had to deal with 'real' security before. I'm including this link as a resource for lots of steem newbies! =) cheers!
Thanks for the kind words, my friend! I'm stoked by how well it's working out for the community. With all of the value that Steemit is creating, we need to make sure that it can be protected easily, by anyone.
Thanks for the info!
Really a great article.
I use lastpass but never herd of duo.
I have made a video post- " How to reset your password " and have integrated the link to your article as an expert tip. Perhaps my video is useful too for any newbie who reads this.
https://steemit.com/tutorial/@lichtblick/how-to-change-your-password-on-steemit-my-own-experiences-and-a-video-tutorial
Thank you.
Thanks, glad you enjoyed it!
Duo is an amazing service. I may be biased because I work there. :) Our NPS is higher than Apple, because we are easy to use and add value to businesses by making it really easy to set up and deploy across large environments of users.
The company is working hard to be a trusted security advisor to our customers and the public at large by publishing research on the blog, and by making useful security easy to use for everyone, from individuals, to small businesses and enterprises.
Can I set up Duo with KeePass?
Thanks I was just thinking of setting this up!
It was my pleasure, I'm glad you found value in it. :)