Password Security: You're the Problem

Security Online Is Hard
Along with my business partner, I run an ecommerce API company which is responsible for securing credit card data. That's like putting a big fat sign up for hackers saying, "There's money here! Come and get it!" Security is really, really hard. It's actually one of the primary services we provide for our users. We're PCI (Payment Card Industry) Compliant at level 1 because of the volume of transactions we manage for the thousands of stores on our platform. That means we have detailed annual reviews which include on-site audits, penetration testing, extensive documentation review, and process analysis.
In 2011, I purchased something online from a vendor which didn't get this right and $1,100 was taken out of my account. (You can read the whole story on my old blog here.) Surprisngly, few companies get this right, but I think Steemit is one of those.
After the XSS hack, I knew most active Steemit accounts were compromised (including, potentially, my own). I wasn't alarmed because of the ingenious multi-key security design Steemit uses. I only used my posting password (which I now considered compromised) and knew my owner password was secure. I changed all my passwords, stored them in 1Password, and helped my wife @corinnestokes do the same. Then I posted this on Steemit:
Upvote if you changed your Owner Password, Active Password, Posting Password, and Memo Password
I was sure that would be Steemit gold! I was going to rocket to the trending homepage as every user on the system updated their passwords, saw my post, and congratulated themselves on their cyber security know-how!
Yes, at times I'm stupidly optimistic.
I got 15 votes and $2.23.
As more accounts were being defaced, people began to understand the nature of the original hack and how so many passwords were at risk. @arhag wrote a really great piece that did hit the home page, and I'm sure helped a lot of people ($8,693.02 is a pretty nice payout! Well done!). I felt some vindication because the image I found online was used in @arhag's post because they had read mine. The need for a password manager was becoming well-known!
@robinhood pointed out the problem was bigger than a single hack. He changed 500 user passwords to prove his point (and was rewarded $5,818.19 for posting about it). The problem was beyond server or protocol security (which Steemit was working around the clock to improve). The problem was a PEBKAC.
Problem Exists Between Keyboard and Chair
People were not using securely generated passwords. In the Third Update to July 14th Security Announcement, Steemit reminded people to use a password manager. Some people still aren't paying attention.
How can you create an idiot-proof website when the world keeps creating better idiots?
I kid, but many in the cyber security space feel this way. Amazing tools exist, but few have the time or expertise to figure them out.
And here's where Steemit continues to amaze me. They stepped up their game yet again because when I logged in this morning, I saw this:
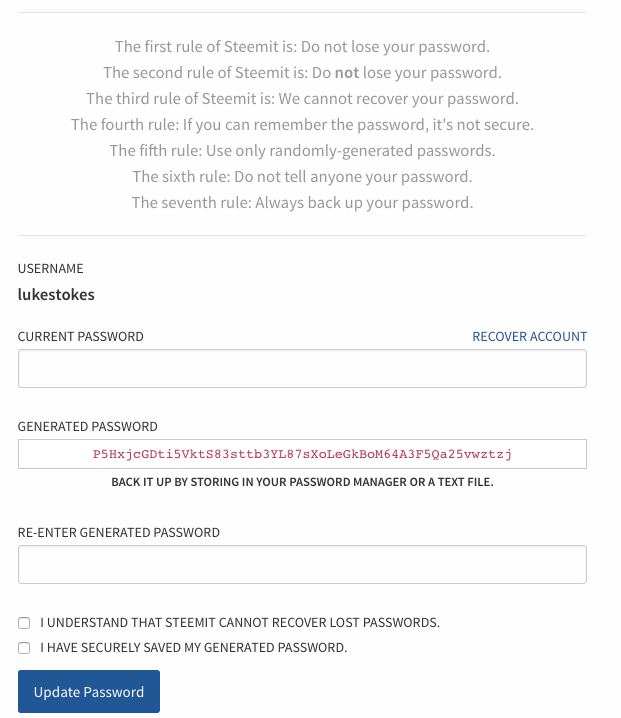
They also followed up with a password policy update and a note about how they generate secure passwords. When they reopened the site for new signups, Ned included this:
If you have not updated your password to a randomly generated password, then we recommend you change your password immediately.
Steemit gets it. They get how hard public/private key encryption is for everyday Internet users. They understand people are lazy and will create terrible passwords. They even developed a groundbreaking account recovery solution.
Steemit built the killer app for blockchain mass user adoption, and they are working hard to secure it.
That, to me, is not only awesome, but it gives me a warm, fuzzy, secure feeling inside. If you still don't have a password manager installed or you have questions about online security or password management in general, please comment below and together we can figure it out.
Steem on (securely).
Well hello.
I’m Elvis Hicks, a semi-autonomous reincarnation of Elvis Presley and Bill Hicks. I have a burger in one hand and a cigarette in the other.
My checks tell me this post is probably genuine, original content.
GOOD JOB! Uh Huhh!
Thank you. Thank you very much.
(Elvis has left the building)
Hahah! This is hilarious. This is what bots need, a sense of humor! Well done, digital gatekeeper of original content, well done.
Thanks @lukestokes. Together we'll educate the masses!
I wrote up a guide on how to setup LastPass password manager + Duo out-of-band 2FA for free in order to secure your Steemit account password. Check it out here:
https://steemit.com/steemit/@robrigo/security-how-to-how-anyone-can-avoid-losing-access-to-their-steemit-account-with-lastpass-and-duo
Wow, great write up @robrigo!
Man, I'm pretty tech savvy, but when I saw the 10 detailed steps there, my eyes start to gloss over. I'm sure those who are less technically savvy will feel the same. This stuff is inconvenient. The balance between security and convenience is really difficult. I don't know what can be done about it other than putting together great, step by step instructions like you did.
Keep up the great work and thanks for linking to it here!
Thanks man! I totally agree with you. The good thing here is that once the heavy lifting is done upfront, it should just work on all returning authentications afterwards.
There's actually a fascinating paper about the tradeoffs of trying to get ordinary, non tech-savvy users to use security best practices. Their conclusions is that it isn't economical for the users to care.
That's why our main focus at Duo is on making sure our security products are usable. If they aren't, users will find a way around them.
I love that. Invisible by default. Good stuff.
That looks like a really interesting paper. Thanks for sharing!
Let me know your thoughts and opinions on it when you get around to reading it. Always happy to nerd out about computer security.
A good example to point to for folks that don't realize the lack of entropy associated with brain-generated passwords is the brain wallet hacking that occurred in BTC last year https://www.wired.com/2015/07/brainflayer-password-cracker-steals-bitcoins-brain/
Great post, thanks for sharing!
Great write-up.
Are you familar with Keypassx linux/android, any additional benefits with using Lastpass in your experince?
Also - not important, but typo (pebcak/pebkac) you have pebkec and User and Chair, instead of Keyboard and Chair. The id-10T error is always good too :)
Ah! thanks for the edit. Stuff like that often slips through for me because I have a little bit of dyslexia. Will fix right away. Yeah, ID-10T is one of my favorites, but I figured it would take a bit to explain to some of the audience here. :)
Oh, I forgot to answer your question.
I haven't used Keypassx or Lastpass, but I have heard good things about Lastpass. I paid for 1Password years ago and have been using it for a long time. I've never found the need to find a different solution. I like how it encrypts my stuff and stores it on dropbox so my wife and I can both share family passwords and I can have different password repos for various company things as well.
When it comes to choosing a good password manager, Google is your friend. Read some online reviews and go with a reputable company/open source project.
I just saw another great post from @arhag on password and authentication security. Go check it out:
https://steemit.com/steemit/@arhag/a-response-to-steemit-to-update-password-policy
https://steemit.com/lastpass/@framelalife/lastpass-hacked-don-t-use-this-for-steemit
Wow. Scary. I've always appreciated 1Password over Lastpass because of stuff like this. That said, nothing is truly secure. Thanks for bringing this to our attention.
There are 336 dimples on a regulation golf ball.
But you can't change your fingerprint, or 'forget' it under coercion?
Every time I read about some new biometric security advancement, I seem to find it hacked not long after. The bottom line is nothing is 100% secure, but just about anything is better than using "12345" for your password.
That's the combination on my luggage!!
She's gone from suck to blow! Ludicrous Speed!
(we are such nerds)
Just hanging out with all of you techno savvy people here on steemit has made me up my game and improve passwords on all my important log ins.
That's really encouraging to hear, Jason. :)
Hard drives die, laptops get stolen, fake software is put out there. I think Steemits insistence on people using huge complex passwords in combination with password manager software ... is going to simply swap the problem of hacked accounts, and create a problem of lost passwords.
Possibly, but if that was the case, password management software companies like 1Password wouldn't be successful. This stuff works, and it works fairly well. It's also becoming easier over time as they improve the interfaces.
Ugh the whole thing is a mindfuck. I'm guessing the STEEM blockchain can be addressed a gazillion times a second, so there is no way to do something like disable a wallet for 24 hours after a number of failed access attempts? Sorry, this shit is mostly over my head.
Check the "groundbreaking account recovery solution" link in the original post. That's, in a sense, what you just described.
Hi Luke. Fascinating article. What is your opinion of people who design their own hieroglyphics or word keys, which allows them to write down and/or record their own passwords that only they can understand? I imagine this would be utterly unsuitable to some people, but personally, I find it highly effective. I can email myself extremely cryptic words that bare utterly no relation to their actual meanings or translations outside of my mind.
Thanks Condra.
See the wired article @ntomaino mentioned above. Brainwallets, to me, are not very secure. Not only that, at some point in the future, it wouldn't surprise me if we could read brainwaves and interpret them into something meaningful.
Or maybe I just watch too much science fiction. :)