Every Person Is Under A Big Threat - Or A Frightening DDoS
The attack, in which users can not gain access to certain resources, called DDoS-attacks, or a problem called "Denial of Service". The main feature of these hacker attacks is a simultaneous request from a large number of computers around the world, which are aimed mainly at the servers of well-protected companies or government agencies.

Network security experts identify several types of DDOS-attacks
Bandwidth. Today, almost every computer has got a local network, or simply connected to the Internet. Therefore, there are cases of network flooding - a large number of requests with a malformed and senseless system to specific resources or equipment with an aim its failure or malfunction (communication channels, hard drives, memory, etc.).
UDP-flooding. This type of attack is somewhat similar to the previous one, but instead of the ICMP packets, attackers use the UDP-packets. The essence of this method is to replace the IP-address of the victim with the address of the attacker and completely overload bandwidth, which also leads to a system crash.

Exhaustion of the system. Such a DDoS attack on the Samp server is held to control physical memory, CPU, and other system resources, due to the absence of which the attacked object simply is not possible to fully operate.
Looping. Endless checking of data and other cycles force the object to spend a lot of resources, thereby clogging up memory before its complete exhaustion.
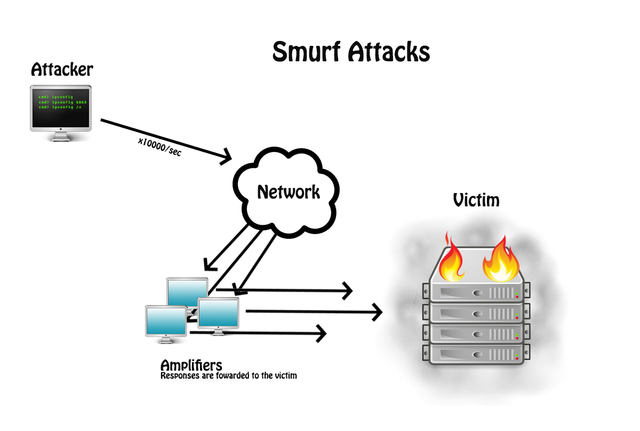
Smurf attack. This is one of the most dangerous species. A hacker sends the victim a fake ICMP package through a broadcast channel, where the victim's address is replaced with the attacker address, and all nodes begin sending responses to the ping request. This DDoS attack is a program that is aimed at the use on a large network, requests processed through 100 computers, will be amplified by 100 times.
HTTP protocol. Hackers send the HTTP-packets with special encryption, a resource, of course, does not see that there will be a DDoS attack, the program for the server, doing its job, transfers backpacks with a much larger capacity, thereby clogging up the bandwidth of a victim, the server stops working.
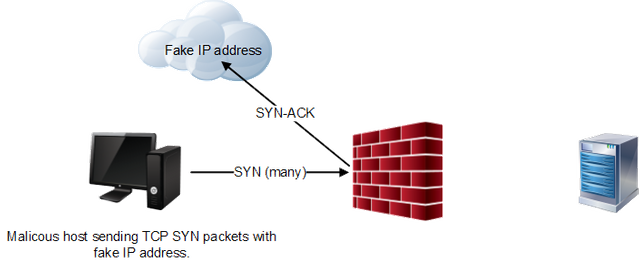
SYN-flooding. Attackers try to run a large number of TCP-connections through SYN-channel with the wrong or non-existent return address at the same time. After several attempts, most operating systems place the problematic connection in the queue and after the n-th number of attempts, it is closed. The flow of SYN channel is quite large, and soon after a number of attempts, the victim core refuses to open any new connection, blocking the entire network.
"Heavy packets". This view gives an answer to the question: "What is DDoS attack server" Hackers send packets to the user server, but the overload of bandwidth does not happen, the action is directed only at the CPU time. As a result, these packets lead to failure of the system, and it denies access to its resources.
Log files. If the quota and rotation systems have security gaps, an attacker can send packets of a large volume, thereby taking up all the free space on the hard disk of the server.
DDoS attacks: how to protect yourself
There are a lot of methods of protection against DDoS-attacks. And all of them can be divided into four parts: passive, active, reactive and proactive. Let's talk about them in detail.
Software protection
Some software and hardware manufacturers can offer quite a lot of effective programs to stop DDoS attack on the website. A separate small server aimed to defend the computer from small and medium DDoS-attacks.
Filtration
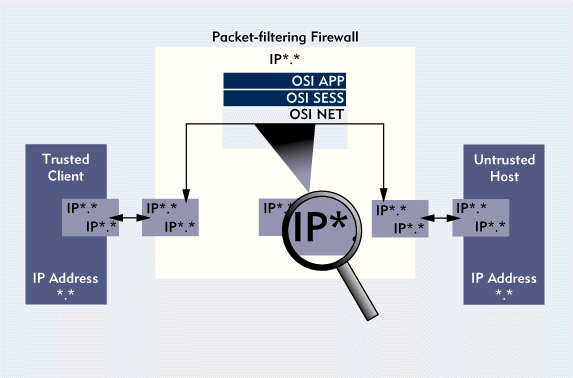
Lock and careful filtering of incoming traffic will not only reduce the likelihood of attacks. In some cases, the DDoS attack on the server can be completely ruled out. There are two basic ways to filter traffic - firewalls and access control list. ACL allows you to filter out the secondary protocols, without breaking the TCP performance and not reducing the speed of access to the protected resource. However, if the hackers are using botnets or high-frequency requests, then the process will be ineffective. Firewalls are much better against DDoS-attacks, but their only drawback is that they are made only for private networks.
Mirror
The essence of this method is to redirect all incoming traffic back to the attacker. This can be done thanks to a powerful server and competent professionals who don’t only redirect traffic, but also are able to incapacitate the attacker equipment. The method will not work if there are errors in the system services, software codes, and other network applications.
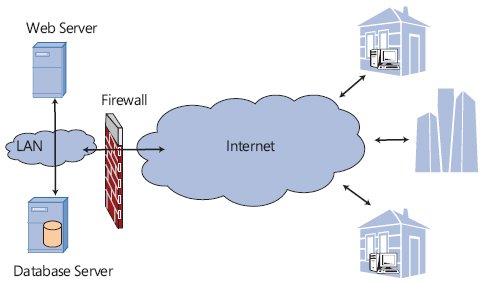
Distribution of systems and resources
Duplication of resources and distribution systems allow users to work with your data, even if your server is attacked at this moment. A different server or network equipment can be used for distribution, and it is recommended to divide the services to different backup systems (data centers).
Evasion
The main feature of this method is the withdrawal and separation of the attacked object (domain name or IP-address) - all working resources located on the same site should be divided and arranged on the other network addresses, or even in another country. This will help to survive any attack and keep the internal IT structure.
In conclusion, I would like to say that today DDOS - attacks are widespread and the fight against this problem is a matter of every person. And if you have a desire to experiment and attack any server, think about the consequences, firstly - it is illegal, and secondly, you will harm a lot of innocent people, and this is not good!
Image credit: 1, 2, 3, 4, 5, 6, 7
Follow me, if you are a geek like me or want to learn more about technologies and scientific/educational topics
Alex aka @phenom
Good post.
I would not say "every person" but "every website" or "every person having a website", which would be more correct :)
Actually, you can be even ddosed in your local network if the one will send a huge amount of packets to your ip address, so your computer will spend its computational power to reject this garbage packets and you'll be not able to perform any action. Even mouse cursor will move glitchy
That's true, but you still need a local network :)
Interesting article, I advise you to read about a coin for DDOS attacks with Proof-of-DDoS algo)
DDoSCoin — New Crypto-Currency Pays Users for Participating in DDoS Attacks
This post has been linked to from another place on Steem.
Learn more about linkback bot v0.4. Upvote if you want the bot to continue posting linkbacks for your posts. Flag if otherwise.
Built by @ontofractal
Congratulations @phenom! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honnor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPIf you want to support the SteemitBoard project, your upvote for this notification is welcome!
I have a few questions. Did you ever hear about CloudFlare for DDoS protection?