Introduction to Mobile Networks - Security in 2G (GSM) Networks

source: pixabay
The first GSM networks started appearing around the world in the early 1990's and their adoption by the general public grew at an ever faster pace. By the dusk of the last millennium around 50% of the adult population in the developed world owned a mobile phone. The trend continued moving linearly in the up directions until almost reaching 100% by the end of the last decade. Mobile phones had become truly ubiquitous and many people wondered how one could live a normal life before the ascent of mobile technologies.
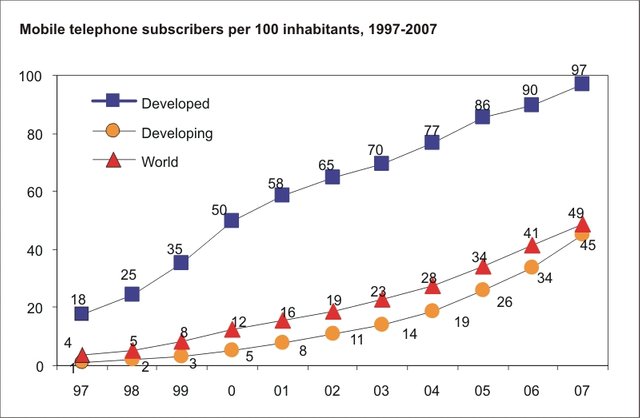
source: ITU
One reason for this incredible expansion is the democratization of call / SMS rates in the mid-1990's, the success in reducing the cost of manufacturing handsets and constant improvements in miniaturizing the technology. While the first generations of analogue mobile handsets were bulky and mostly confined to vehicles, the handsets of the 1990s became wearable and early fashion statements.
But all these major improvements would have been fruitless if it wasn't for a key aspect of the technology: security.
Security is what allows a mobile operator to be sure that a subscriber is who he/she claims to be. It is the reassurance that no two people can share the same identity and therefore eliminates the chance of identity theft and fraud. Security also provides confidence to customers that their communications cannot be tapped upon and/or modified.
The strong security provided by mobile networks all hinges on one shared secret, referred as Ki in 3gPP specifications, which must be stored securely within the operator's network and within the subscriber equipment. The Ki is a 16 octet value which must never be revealed to other parties than those involved in implementing the authentication procedure.
On the network side, all subscriber IMSIs and Ki values are stored within a network element called the Authentication Center (AuC), usually collocated with the HLR. The HLR/AuC resides within the building infrastructure of the network operator, making it hard to be physically accessed by unauthorized individuals. Furthermore the Ki values themselves are normally stored in encrypted form in the AuC, ciphered with an encryption key usually not available to authorized staff. This makes it very difficult in principle for an attacker to get access to the clear form of the secret keys.
The challenge on the subscriber side was to store sensitive subscriber information, in particular the secret key Ki, while making sure that this information could not be accessed by any individual, including the subscriber himself.
The solution to this problem had to meet the following requirements:
- Be able to store various information in non-volatile memory (should persist when power is turned off)
- Allow the authentication algorithm to execute on the same platform as the Ki value itself so that the Ki never has to be supplied to an external hardware element.
- Have some basic computing capabilities in order to execute authentication algorithms.
- Protect access to key functions through a subscriber passcode (the PIN)
- Make some information only available to the operator itself through the use of other passcodes.
- Be small so that it could be easily inserted into handsets.
- Have low power consumption.
What resulted from all these requirements was a fantastic feat of engineering that managed to match the success of mobile phones in every way: the Universal integrated circuit card (UICC), familiarly known as the SIM.
The SIM: The Most Ubiquitous Microchip

source: pixabay
The SIM is not just a memory card. It is also an integrated circuit capable of processing instructions, similar to a mini central processing unit (CPU).
SIMs store information in files organized in non-volatile memory using a basic file system structure.
Files have various permission levels. Access to the SIM files by the mobile terminal (e.g. handset) can be read only, read/write or completely unreadable. File access can be protected through a set of administration (ADM) codes.
Files can also store small programs. The first such program that was selected to be installed on the SIM is COMP128 which works the following way.
Taking a random challenge (RAND) from the network and combining this challenge along with the secret key Ki using cryptographic algorithms, COMP128 produces:
- A response value to be sent back to the network: RES
- A session key to be used to encrypt/decrypt all traffic exchanged over the GSM radio interface: Kc
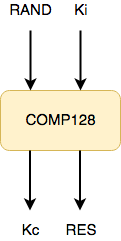
source: Original illustration for Steemit
The cryptographic algorithms have been carefully designed so that the secret key Ki cannot be derived from the result RES, Kc and RAND value. In other words COMP128 is a one-way only algorithm by today's known mathematical principles.
The RES value is returned to the network upon authentication for verification while the Kc is passed on to the mobile terminal (handset) to use as a session key for all encryption/decryption taking place over the radio interface.
Within the network the same COMP128 algorithm is used to produce the same results. The RES is supplied to the VLR while the Kc is passed on to the BTS.
The VLR is thus in a position to check the returned RES from the UE against the value supplied by the AuC. From the BTS point of view it can now encrypt and decrypt traffic using the same session key as the UE.
GSM Authentication and Ciphering Procedure
Using the above and what we have learned in the previous post (GSM CS Attachment ) we can now illustrate how the authentication and security mechanisms take place within a normal procedure between the UE and the network:
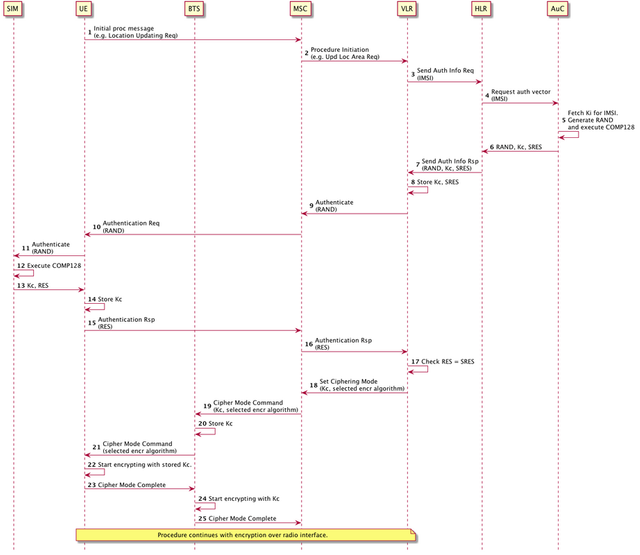
source: original illustration for Steemit
- The UE initiates a procedure by sending an initial message to the network, for example a Location Updating Request to initiate CS attachment (see GSM CS Attachment). All traffic transmitted over the radio interface is currently sent in the clear.
- The MSC receives the UE message and initiates the appropriate procedure with the VLR (e.g. Update Location Area)
- The VLR decides to authenticate the subscriber. It sends a Send Authentication Info Request to the HLR along with the IMSI of the subscriber.
- The HLR requests the AuC for an authentication vector, supplying the IMSI.
- The AuC retrieves the secret key Ki associated with the IMSI. It then generates a random 16 octet value RAND and execute the COMP128 algorithms using Ki and RAND as input. This returns a new ciphering key Kc and expected result SRES.
- The AuC returns the authentication vector (RAND, Kc, SRES) to the HLR.
- The HLR returns the authentication vector to the VLR in a Send Authentication Info Response message.
- The VLR stores the SRES and Kc for later use.
- The VLR requests the MSC to authenticate the subscriber. It supplies the RAND.
- The MSC an Authentication Request to the UE, supplying the RAND.
- The UE invokes the AUTHENTICATE program on the SIM, supplying the RAND.
- The SIM executes COMP128 supplying the RAND and the securely stored secret key Ki.
- The SIM returns to the UE the generated Kc and RES values.
- The UE stores the ciphering key Kc for later use.
- The UE sends back an Authentication Response to the MSC with the calculated RES.
- The MSC responds to the VLR authentication response, supplying the RES returned by the UE.
- The VLR verifies that RES = SRES. If this check is verified, then the SIM is storing the same Ki as in the AuC and therefore the subscriber is authenticated.
- The VLR now can use the stored Kc to request the BTS/UE to start encrypting all traffic exchanged over the radio interface. It does so by sending a Set Ciphering Mode message to the MSC, supplying the Kc and a chosen encryption algorithms supported by the BTS and the UE.
- The MSC requests the BTS and UE to start ciphering by sending a Ciphering Mode Command. The Kc and encryption algorithm is supplied.
- The BTS stores the Kc for later use.
- The BTS sends the Ciphering Mode Command to the UE with the selected encryption algorithm.
- The UE activate encryption on the logical channel using the stored Kc as ciphering key.
- the UE sends a Ciphering Mode Complete back to the BTS.
- The BTS starts encryption on the logical channel using the stored Kc.
- The BTS forwards the Ciphering Mode Complete to the MSC.
- All traffic sent in both directions over the radio link is now encrypted.
Weaknesses of GSM Authentication
The security mechanisms described above where largely successful during the expansion of GSM networks. However some issues had been clearly identified by the time the standardization bodies started working on the third generation mobile networks (3G).
The key weaknesses identified were:
- Authentication / ciphering is optional. The network can provide full service without ever authenticating the subscriber and send all traffic in the clear over the radio interface.
- With GSM authentication, the network authenticates the subscriber but the subscriber does not authenticate the network. This combined with the first weakness described above allows attackers to deploy a rogue BTS and provide service to GSM subscribers without their knowledge. Subscribers could place/receive calls and never know that these were tapped by a malicious entity.
- The GSM authentication is vulnerable to replay attacks.
- The traffic is only secured on the radio interface, between the UE and the BTS. This means that all traffic exchanged between the BTS and the rest of the network is normally transmitted in the clear, typically over non-IP transports such as ATM or ISDN.
All of the above issues where addressed in 3G networks and an evolution of the SIM, called USIM, went into force by the time the first UMTS networks were deployed.
This will be the subject of the next post in this series: Security in 3G (UMTS) Networks.
Acronyms and Concepts
| Acronym | Meaning | Description |
|---|---|---|
| AuC | Authentication Center | The network element, usually located with the HLR, storing all subscribers secret keys and in charge of calculating authentication vectors |
| HLR | Home Location Register | Stores all subscriber information such as IMSI, access and service rights, location information, etc. |
| IMSI | International Mobile Subscriber Identity | 15 digits number uniquely identifying a mobile network subscriber across all providers |
| Kc | Key Ciphering | 64bit ciphering key used for encrypting traffic transmitted over the radio interface |
| Ki | Key Individual | A 128bit shared key stored in the SIM and the AuC for authenticating the subscriber to the GSM network |
| PLMN | Public Land Mobile Network | An operator providing mobile telecommunication services |
| RAND | Random Value | 128bit value randomly generated by the AuC and used as a challenge to authenticate the subscriber |
| RES | Result | 32bit value resulting from executing COMP128 with the supplied RAND value and secret key Ki |
| SIM | Subscriber Identity Module | A type of UICC fitted within mobile network terminals (e.g. handsets). Responsible for storing important and sensitive information and capable of processing instructions, including authentication algorithms |
| SRES | Signed Response | 32bit value calculated by the AuC using COMP128 on a RAND value and secret Ki |
| UE | User Equipment | Terminal used by the subscriber to access the mobile network, such as smartphone, modem, IoT device, etc. |
| UICC | Universal Integrated Circuit Card | Commonly known as SIM card. Stores subscriber information such as IMSI and shared key and capable of specific computing |
References
- ITU Statistics
- Specification of the Subscriber Identity Module - Mobile Equipment (SIM-ME) Interface (3GPP TS 51.011)
- Characteristics of the Universal Subscriber Identity Module (USIM) application (3GPP TS 31.102)
- Location management procedures (3GPP TS 23.012)
- Mobile Application Part (MAP) specification (3GPP TS 29.002)
Previous Posts in this Series
Introduction to Mobile Networks
The GSM CS Architecture
GSM CS Attachment
As always do not hesitate to leave comments with your questions and I will make sure to reply with the best possible answers.
I had no idea it was so complicated. My Master courses were in Information Security, and I thought those were complicated. I don't even want to think about 3G or 4G. Is it any fundamental different though? I mean, apart from fixing the problems you have mentioned.
I have followed, so I will read the article for sure :D
Thanks for sharing your knowledge on the subject!
Hi @alexdory. It's complicated when you look at the procedure as a whole but the principles are reasonably straightforward.
3G authentication is an evolution rather than a revolution. Working on that in my next post.
4G re-uses 3G authentication so that's the good news ! ;-)
Thanks for reading!
Great post sir!
I did my internship at Ericsson.
Was fun exploring the world of GSM and WCDMA technologies.
Glad you enjoyed it.
I hope you enjoy my future posts about mobile networks.
Looking forward to them.
You have a minor misspelling in the following sentence:
It should be millennium instead of millenium.Congratulations! This post has been upvoted from the communal account, @minnowsupport, by irelandscape from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
Hello! Affordable, no-contract mobile plans with unlimited talk, text and data have made Ultra Mobile the best choice for those who want quality mobile service while saving money. To better understand this mobile operator and all its advantages and disadvantages, everyone can read the information here https://ultra-mobile.pissedconsumer.com/customer-service.html and this will allow you to understand whether their services can meet all your communication needs.