The CIA Project "HIVE" Unveiled By Wikileaks
In this article I present the recent findings of the malicious software "Hive" uncovered by the Wikileaks foundation.

I am the eagle watching over you and for you own safety
image source
CIAs remote data collection mechanism
Just 3 weeks ago Wikileaks made yet another important contribution to the database of publicly available classified files.
Unveiling the mischief of the CIA has been an important past time of Wikileaks in 2017 and after uncovering 23 different secret tools this year (Vault 7) - in this batch (Vault 8) - the project HIVE is added to the list.
The leaked files contain information about a significant component of the CIA software architecture: The Hive is a Command-and-Control Server that communicates with malware on infected computers and allows the agency to send commands to the targets to extract further information.
You can imagine the Hive as a an command center that governs over multiple infected users simultaneously.
Let's learn from the pro's
The architecture is designed to prevent the public associating malware to the CIA. To ensure this, the Control Server includes a public website that acts as a decoy and a multi-level VPN stage.
"Using Hive even if an implant is discovered on a target computer, attributing it to the CIA is difficult by just looking at the communication of the malware with other servers on the internet"
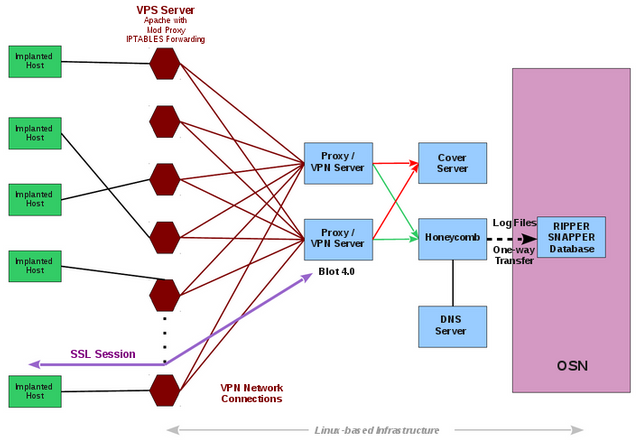
image source
In the picture presented by Wikileaks, you can follow how it works. On the far left you have infected user machines and on the far right you have the CIA command center. In the middle, the blue boxes are components of the clever multiple VPN stage that is used to deceive anyone snooping around for evidence.
A key component is the cover server: The fake domain displays "innocent" content to a user who might visit the domain by chance. A regular visitor would not suspect that something is hidden beneath the normal website. The delicate feature is only visible to technically sophisticated people - the server has the HTTPS Optional Client Authentication enabled. The obscure feature is barely used elsewhere - it allows users browsing a website to authenticate themselves. (Usually it is the other way around: The website is requesting you to perform an authentication procedure, not you offering it.)
This is how the Hive can differentiate between implant traffic and regular traffic; Regular users will be redirected to the fake website, while the implants that send collected data will authenticate themselves and are redirected to the "Blot server" and then forwarded to the "Honeycomb" which extracts the data and associates it with the target.
In order to avoid anti-virus software picking up the background activity, the malware implants use fake digital certificates for Kaspersky Lab.
"Digital certificates for the authentication of implants are generated by the CIA impersonating existing entities," WikiLeaks says.
"The three examples included in the source code build a fake certificate for the anti-virus company Kaspersky Laboratory, Moscow pretending to be signed by Thawte Premium Server CA, Cape Town."
This way, if the target tries to inspect the outgoing network traffic, it is likely to mistake the CIA data extraction for a harmless entity.
Conlusion
Yes, the CIA is really doing this. If it were not for brave men (and women) like Julian Assange and his Wikileaks team, we would not have insight into how these organizations are messing with us on a regular basis. Wikileaks has released the complete source code of this project and made it publicly available to forensic experts and anyone interested.
Do you find this information scary? Me too, that is why we need it to be public knowledge. Amazing work, Wikileaks!
Here, check it out yourself: https://wikileaks.org/vault8/#Hive
Information sources: https://wikileaks.org/vault8/#Hive
More Articles like this:
Do you want to learn how Uber deceives regulators?(Read article)
Do you want to know what a former Facebook Exec has to say about it? (Read article)
- Nick ( @cryptonik ) -

The majority of viruses and malware being produced by the government and it's intelligence agencies doesn't sound so far fetched anymore does it?
I appreciate the sentiment but it's not quite true. The majority is being produced by kids who think that a copied script makes them "hackers" and lowly scammers who think that stealing the money of others is legit form of income.
However the CIA produces especially effective malware because they:
With every leak Wikileaks delivers, we take away one of their weapons.
I guess I could have clarified that I think a large portion of the virus script may originate from the CIA or other intelligence agencies but then of course gets picked up and copied by others. Maybe I am wrong on that, I'm sure you have done more research then I have.
Good piece.
Thank you :)
Jesus Nik, this is terrifying : (
Unbelievably clever and sophisticated.
And who knows what else they have. We might as well say there is pretty much zero privacy on the web in 2017 and beyond. .-----Not quite sure how the "honyecomb" works?
The truths that Wikeleaks reveals are more frightening than some conspiracy theories. They are on a dedicated mission to keep the masses enslaved. There is almost zero privacy, or rather the consent on your data is signed when you 'agree' to the terms and conditions on any app. The question you should always ask is: "Is the comfort this app offers worth the data I have to give up in return?". It's time people realized that Facebook & Co. is not a charity.
The system in this post applies only to machines infected by CIA spyware.
The honeycomb module is the part of the system that performs association of data to user so that the collected information can be examined easily. The 'blot' server receives multiple streams of data from multiple sources. The honeycomb is responsible for validating the source and sorting the information i.e.: Data A, B,C -> User 1, Data D,E -> User 2 and so on.
Thanks Nik
@originalworks
The @OriginalWorks bot has upvoted and checked this post!
Some similarity seems to be present here:
https://thehackernews.com/2017/11/cia-hive-malware-code.html
This is an early BETA version. If you cited this source, then ignore this message! Reply if you feel this is an error.
This post has received a 0.16 % upvote from @drotto thanks to: @banjo.