[whitehat report] Warning Don't Install SteemPay Woo Commerce Plugin for now. It's very alpha.
I noticed @fyrstikken had implemented the @steempayments WOO plugin! I immediately wanted to test out the workings, as I was curious if I could buy something with SBD directly!
So I wanted to buy some great products in his store with SBD. Because I was a little undecisive, I decided to go for all of the products: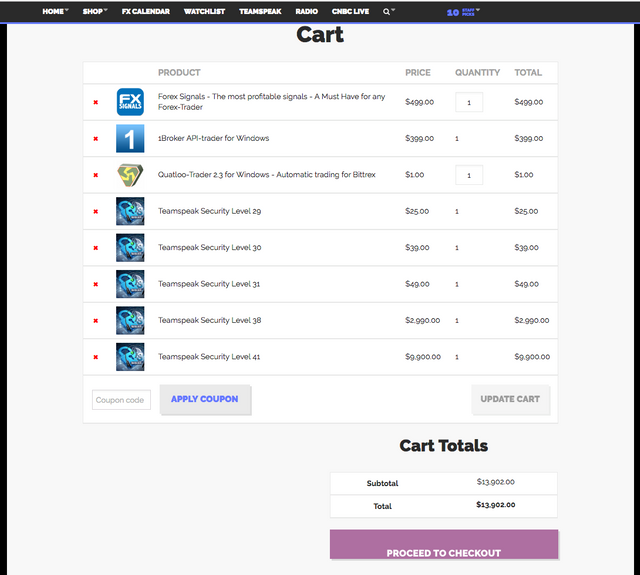
In the end my bill totalled to $ 13,902 and I was a bit shocked. That's not the amount of SBD available on my account.
I picked SBD to checkout and then arriving on Steempay.io I tried to change the amount due to 0.01 SBD cent by simply altering the URL.
Then I paid that 0.01 SBD instead. You can see it in my transfers https://steemit.com/@roelandp/transfers
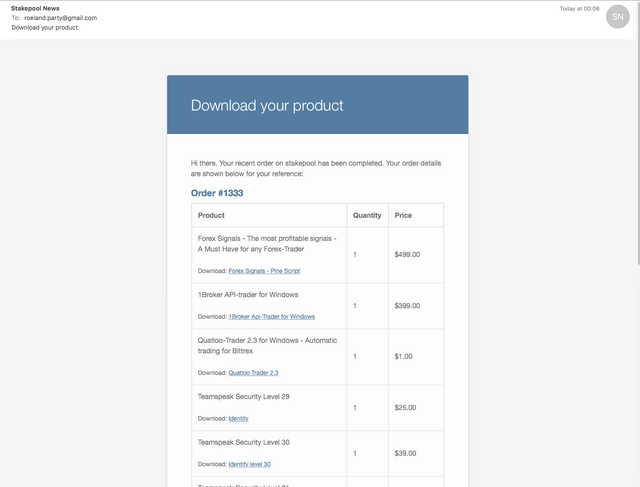
- And within minutes I was redirected to @fyrstikken's shop and got an order confirmation...
- And another minute later I found all licenses in my email inbox:
- I informed @fyrstikken of this flaw and advised him to disable the plugin. I think he did in the meantime
- He told me I should write a small whitehat research post to warn others to not install the plugin
- I have informed @steve-walschot about this serious exploit
*edit* did a little exploit hunting...
I've taken time to analyse the plugin code a bit further, curious to see how these woo_plugins actually work. Because there must be some kind of validation built inside the script right?
On https://www.diffchecker.com/P9WBXOUG you see the 'diff' between the original plugin ("the inspiration" #notinventedhere (on the left)) and the Steempay version (on the right).
In line 228 you see the following code:
$payload = array(
"payid" => $_REQUEST['payid'],
"receiver" => $this -> receiver_id,
"amount" => "0",
"currency" => "0"
);
So this is the part where the 'verification' happens... The most important part of the payment code... Which answers the question 'did the transaction went well? and did the amount correspond to the amount which was needed to be paid?'.
If you analyse the parameters being send you see that both 'Amount' as well as 'currency' are a 'stringified' 0 being send to the SteemPayment server...
This means the verification is totally forgotten / not implemented:
- Crucial values are omitted and instead "0"'s are send.
- The validation is on the server side (on Steempay) also not even implemented... because if it was implemented it would error on my payment... Because my payment consisted of 'currency (SBD)' and the amount '0.01' which are definitely not the same as the "0" values being send to the server for a check.
* end edit *
So IMHO these vulnerabilities need to be fixed in order to get Steempay.io to the next level. I really love the idea to have SBD / Steem as an integrated payment option through plugins for Woo Commerce and other webshop platforms. I do understand this code is in beta, as was said in the announcement post: "the beta version is usually the last version before wide release, often tested by users under real-world conditions."
I hope we see an updated version of steempay woo commerce plugin without these exploits and full https support in the near future.
* update 2 *
- according to @steve-walschot the bug is fixed.
- however Github Zip releases is not updated.
- httpS is not implemented along the payment verification url if I see correctly
- I really want to review the
/WOO/verify.phpand urge others to do so too before implementing this plugin.
* update 3
- Github Zip release is now also updated.. Note on Github has a warning to "NOT USE IT IN PRODUCTION ENVIRONMENT". I think that warning should be mentioned on the original trending post too. And should have been mentioned from the beginning.
* update 4 *
- As this is not a SteemFest related post I won't push these rewards into @steemfest. Nevertheless I will push the SBD rewards of this post towards a good cause: I will give the SBD rewards of the posts towards this group of five people from Belarus: https://steemit.com/steemfest/@celebr1ty/collect-sd-for-visit-to-steemfest-by-our-team-part-2-5 who are very much willing to come to Amsterdam SteemFest, providing that they actually come to Amsterdam :) Otherwise i'd be pleased to receive the monneys back...

I have a massive respect for whitehats. Thank you for being one.
Yeah that was a really serious mistake. I've seen that exact code come out of $5 freelancer jobs.
@williambanks comparison is mostly done with == or === :) and yes PHP can have some exploits, however with PHP 7 the language becomes more strict i think...
Nonetheless this has nothing todo with having exploitable code (did not look into that), but rather with key parts of the 'application' not being implemented.
It is a socialistic feature @roelandp - for steemians to just ... webshop whatever they want and pay whatever they feel like :) I´m sure it was intended that way, you know - re-introduce shoplifting for the Internet ;) hehehehe
@roelandp You are absolutely correct, but so am I. :D It was a commentary on what happens when you do things like farm work out to the lowest bidder.
The problem with the particular app in question is structural in nature. It's not a simple fix, it's the type of thing that needs a rethink from the ground up. But if the mistake you called out is there, you can bet that the code in general is likely to have few other issues as well.
Bug fixed. Just a 3 minute fix, that's why it's called a beta release. A simple PM would solved this :)
Anyway, thanks for pointing it out.
Please I don't understand why this is called a bugfix: you released with the verification part completely omitted. It was both not working the plugin and not in the WOO/verify.php on your server.
I am really curious about the contents of /WOO/verify.php
Also since you said bugfix... which has indeed been published on the Github, it would be nice to also update the 'Zip release files' on the Github... ?
The way you exploited and reported this code flaw is great and shows a great character. I really respect that. Good man!
Painful, might hurt @steve-walschot his position as a witness. Not to mention he introduces himself as a security expert?!?!
Whilst this undeniably is a huge security flaw, I do feel like it is advancements like this which will ultimately help introduce Steemit to the masses (and I think we should appreciate Steve's efforts in this regard, too!). It would naturally have been ideal to not have this exploit in the first place, but getting it tested very early on is much better than to have a disaster brewing behind the scenes. It moreover sounds like @roelandp did the right thing and informed affected clients immediately without abusing anything; damage seems very contained.
I think you are totally right.
However with advancements like these... certain responsibilities come.
Since @steve-walschot is a "EU top 25 security auditor" I can't help but feel a bit that after having worked for 'countless hours' he could have at least given it his expertise test since being a top 25 security auditor... Especially since the Woo Plugin was already "almost done" 1 week ago. Let alone that if you have "perfect knowledge" in about 20 code languages "without the help of the allmighty Google" you would also have the knowledge to structure your code in a way that this is not possible.
It's just that this product has to deal with payments, and this stuff is indeed essential for Steem's success, so it must be done really thorough...
Imagine that if I had a black hat, I could now have sold all these digital goods somewhere else with serious implications for @fyrstikken.
yeah @roelandp I am eternally grateful that you were my first and only customer today. This could have gone really bad.
I completely agree, this is better to be found sooner then later. But the simplicity of this exploit versus steve's self proclaimed top 25 EU security expert puts it in an extreme contrast. Just saying. It's like saying you are the best hockey player from Canada and then forgetting your hockey stick on match day.
rofl. This is golden.
Never show up without your stick is one of the first things us Canadians learn out of the womb, eh?
Right, it's important to recheck everything on the server-side, can't trust the client! Fantastic find!
Well spotted. This could have been an expensive flaw for all involved. Thank you:)
Nice testing and responsible informing! Hats-off to you.
WOW!
How awesome that you did that and even knew how to think about doing that!
Yes its unfortunate that there was a problem/bug in the system and obviously should not be relied upon for running a business but as you said its a great program and if it works properly its a great benefit.
So awesome that you figured this out so quickly and that you were able to inform everyone and that a fix was implemented so quickly.
This is the power of conscious responsible community and I am proud to be a part of it.
Thank you for you're genius and dedication to this community!