[Quantum Computer & Blockchain Security] Chapter 3. Janus-faced quantum computer Quantum Parallelism and Quantum Communication Security
Hello. It is @hunhani.
Thank you for your interest and support in the previous posts. I will do my best to meet your expectations.
Last time, We have learned about the magical phenomena of nature that are caused by quantum superposition and quantum entanglement, especially the measurement of quantum states and quantum transitions.
Chapter 3. Janus-faced quantum computer? Quantum Parallelism and Quantum Communication Security This time, let's talk about how quantum parallelism due to quantum superposition and quantum entanglement relates to quantum communication security.

Simple Review
As a result of the measurement, the initial quantum state can not be known.
- Acquiring information about a system through measurement inevitably disturbs the state of the system.
Quantum entanglement transcends the principle of locality.
- If we determine the state of one of the two quantum entangled quantities through the measurement, we can immediately determine the state of the other.
- Quantum teleportation is transferring information from one location to another without having to move real physical particles.
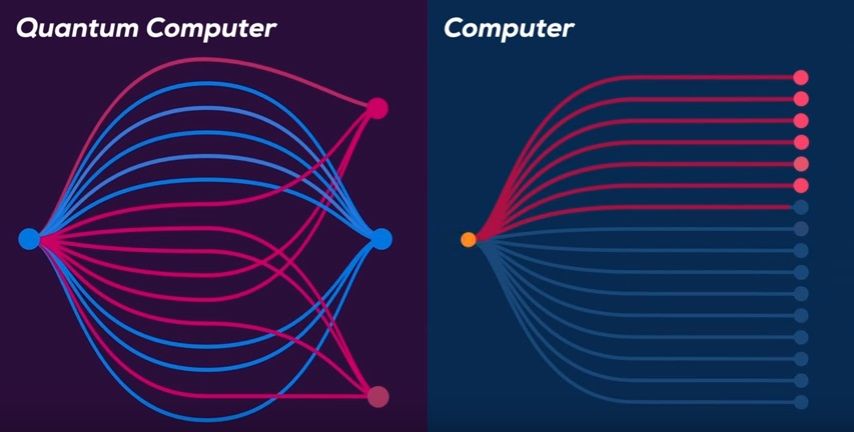
Use the quantum parallelism!
The superposition and entangled quantum states allow to manipulate all states in a single operation. This characteristic is called quantum parallelism. Quantum parallelism enables quantum information processing, quantum communication, and quantum cryptography to solve problems that conventional computers can not solve. Today, we will look at two topics, quantum communication and quantum cryptography.
.png)
It is impossible to copy any quantum states!
The two interchanges, the acquisition of information through measurement and the disruption of the state of the physical system, are a kind of quantum mechanical random sampling. This implies that quantum mechanical information can not be copied perfectly. If it is possible to make a perfect copy, it is against the basic axiom of quantum mechanics because it is measured with a copy instead of the original, and the measurement is done without disturbing the original system.
It may seem that you can not handle the quantum state at our disposal because measurement can inevitably affect the state. But this is very attractive. This allows us to establish a quantum key distribution cryptosystem that can not be absolutely stolen in communication security.

Classical communication technologies use one fixed coding scheme, so if someone intends, any users can steal and read information. However, the quantum key distribution cryptosystem uses a variety of coding schemes to generate and measure information. If someone do not know exactly what coding scheme is used at random, someone will not be able to read the information sent by the sender completely. Above all, this external measurement action damages the quantum information sent by the sender, so the act of stealing information of sender/receiver is immediately detected. In other words, when the user detects eavesdropping, the information is broken at the moment of eavesdropping and all the user need to do is to abolish the communication channel and create a new key.

Quantum computers with both sides of communication security?
Currently widely used public-key cryptography is based on the fact that it is very difficult to decompose a large number of prime numbers. A quantum computer that can solve a large number of prime numbers quickly can easily solve such a password. A quantum computer poses a major threat to modern communications security that employs public key cryptography, while it can provide a quantum cryptography transmission method that is absolutely impossible to eavesdrop. It can literally be a double-edged sword.

Today’s quantum communication security
Various physical, human and functional security techniques related to confidentiality, integrity and availability are required in the operation of communication system. Among them, functional security using cryptographic algorithms and protocols is the most important. Key distribution, encryption, authentication, and other features must be able to run reliable cryptographic algorithms and protocols that work properly. Various quantum cryptography studies such as encryption decryption, signature, secret sharing, indefinite transmission, bit delegation, and multiparametric computation have been carried out. However, due to the present technical limitations of quantum memory and quantum computing, only quantum key distribution and quantum random number generation have been commercialized. The above-mentioned quantum key distribution that can not be eavesdropped is alss based on the quantum random number generation system.

Next time, we will deal with what is the qubit and how does it used for quantum information processing.
I want to deliver it as easily as possible, but this topic is very difficult for everyone. If you comment your question, I will reply to you as easily and concisely as I can.
The following chapter is introduced.
Chapter 4. Quantum Information Processing using Qubits
Please do not take your eyes off!
Previous Story
- [Quantum Computer & Blockchain Security] Chapter 0. Introduction
- [Quantum Computer & Blockchain Security] Chapter 1. Quantum computer! What the hell is different with ordinary computer?
- [Quantum Computer & Blockchain Security] Chapter 2. Magical phenomena of nature, Quantum Superposition & Entanglement.
- [Next-generation Transportation] Hyperloop! Why is it so special?
- [Review] 18 Stories to See “Interstellar” Movie More Fun with Physics
- Engineer Dream Diodes with a Graphene Interlayer
- All images used in this post are from Google Images.
# YHH
I understand not everything but it's fascinating. I'll follow you because I'm a geek and technology. Good job, thanks
Thanks for following. I hope you enjoy this.
I think the response for the advent of quantum computing cracking security will cause us to create "quantum encryption" or something like that. In this case, the technology that is disruptive to security will also be our saving grace shortly after. To put this into perspective I ask, "what came first, a computer virus or Antivirus Software?"
Quantum computers and quantum cryptography are complementary relationships that overlap each other. The development of quantum algorithms and quantum processor technology for quantum computer development is itself associated with the development of quantum cryptography. There must exist ways to compete against the rising danger of quantum computers. I'm going to talk about this topic in the following chapters!
Oh so impressive article, though my knowledge is very limited.
Please up vote me, i am starving for steem power.
Thanks for visiting.
Thanks for sharing. Re-steemed
Thanks for resteem it!
Amazing, nice post, do not forget view my post, now i upvote and follow you, follow me back, thanks you, may we be good friends, best regards
Thanks.
You lost me at "Quantum Computer"...
Forget about understanding...
let's talk about how quantum parallelism due to quantum superposition and quantum entanglement relates to quantum communication security.
All jest aside. Great post.
Did take me a while to re-read it a few times to let it really sink in. I'll be "trying" to read more of your posts in the future. I enjoy your work.
Thanks for the compliment. This topic would be difficult for everyone. I hope you enjoy my posts and get the insight.
Quantum mechanics and dynamics in relation to cryptocurrency security is one area of computing that has remained largely untapped due to the complexity of the nature of particles.
Nice piece there
Indeed. At the same time, It is not easy to overcome the current technical limitations.
I know it's considered a no-no to post simple comments, however, I am using Steemit like I once used other social media. So, some comments are long and others are short and to the point -- all are sincere. Thank you for this series, truly.