WikiLeaks Vault 7 part V: HIVE, Longhorn and the CIA's reign of cyberterror
Whether by design or subterfuge, many have overlooked WikiLeaks releases of the CIA's HIVE infrastructure. The implications presented in this particular leak, however, are dire to say the least. Finally, long-unsolved Internet mysteries of the infamous "Longhorn" and "The Lamberts" trojans can finally be put to bed, but what else lurks in the abyss of the United States Central Intelligence Agency?
HIVE, created by the CIA IOC's Embedded Development Branch (EBD), is a back-end infrastructure malware with a public-facing HTTPS interface used by CIA implants to "rip" information from target machines and open it up to receive further commands from CIA operators.
HIVE is used across multiple malware implants and CIA operations. The public HTTPS interface utilizes unsuspicious-looking cover domains to hide its presence. This sophisticated masking interface is known as "Switchblade".
This article will cover some of the new developments found throughout today's HIVE release, HIVE's components and how it was likely used to besiege anti-virus companies for several years.
Other parts to this series include:
- Part I: The CIA and NyanCat: The hackers and tools of Vault 7's "Year Zero"
- Part II: "Dark Matter" - All your Macintosh are belong to CIA
- Part III: Marble Framework - The CIA's cloaking device for hackers
- Part IV: Grasshopper and more research challenges!
HIVE
All packages for HIVE are installed via "yum", a repository of software packages typically used by Red Hat and CentOS distributions of Linux.(1) HIVE's listening and command-and-control components are managed through an Apache Web Server.(2) For added stealth capability all IPs used by the HIVE infrastructure can be redirected through VPS.(3)
The primary targets for HIVE seem to be opposing web servers (ie. websites):
Switchblade
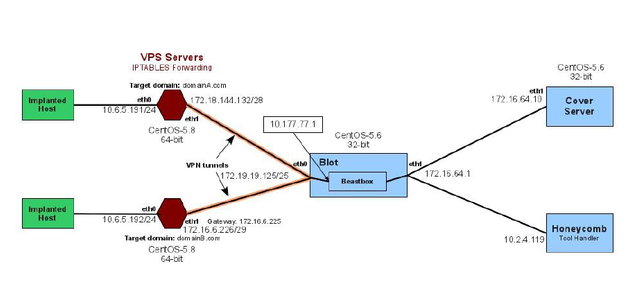
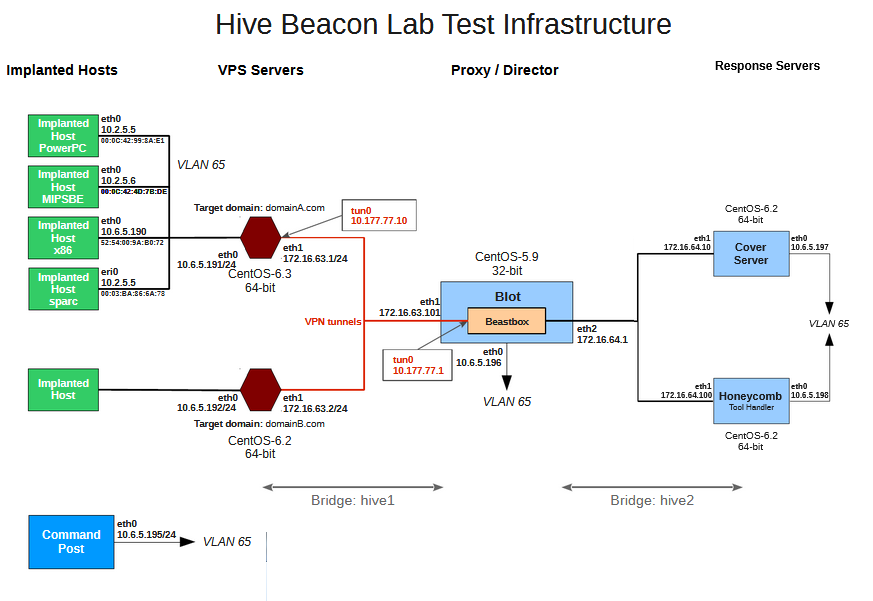
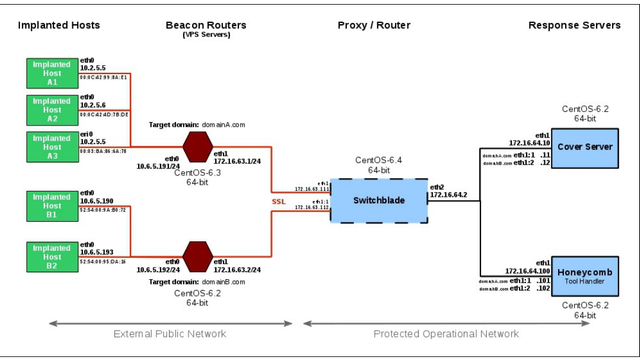
Switchblade is a component in HIVE which disguises traffic between target domains and CIA listening posts.
Beacons from implanted hosts are assigned a beacon router having a cover domain name. Beacon routers are connected to the Switchblade proxy through VPN tunnels to provide security and privacy. Each beacon router / domain has its own dedicated interface and address on the Switchblade.
Some may recognize this as being similar to attacks a few days ago on the Pizzagate Wiki.
Longhorn
In an incredible turn of events, thanks to WikiLeaks' Vault 7, anti-virus provider Symantec was able to attribute the tool once-known as "Longhorn" to malware developed by the CIA.(4)
Longhorn has been active since at least 2011. It has used a range of back door Trojans in addition to zero-day vulnerabilities to compromise its targets. Longhorn has infiltrated governments and internationally operating organizations, in addition to targets in the financial, telecoms, energy, aerospace, information technology, education, and natural resources sectors. All of the organizations targeted would be of interest to a nation-state attacker.
Longhorn was also known as "The Lamberts" to the personal security providers at Kaspersky.(5) Just days ago they published a report discussing some of the details behind the mystery of "The Lamberts" and their targeting of "high-profile" clients in Europe:
Longhorn, which we internally refer to as “The Lamberts”, first came to the attention of the ITSec community in 2014, when our colleagues from FireEye discovered an attack using a zero day vulnerability (CVE-2014-4148). The attack leveraged malware we called ‘BlackLambert’, which was used to target a high profile organization in Europe.
Since at least 2008, The Lamberts have used multiple sophisticated attack tools against high-profile victims. Their arsenal includes network-driven backdoors, several generations of modular backdoors, harvesting tools, and wipers. Versions for both Windows and OSX are known at this time, with the latest samples created in 2016.
Investigators at Kaspersky were able to pry a list of tools that were packaged with "The Lamberts" that may sound eerily familiar in terms of macabre sense of humor and may perhaps be seen again:
- FUNNELCAKE CARNIVAL
- PIZZA ASSAULT
- SPOCKLOGICAL
- GORDON FLASH
- APE ESCAPE
It appears that time is running out for the CIA and that it's only a matter of days before the cover on their mass surveillance and hacking campaign is entirely blown. It seems certain that "The Lamberts" were likely developed and used by the CIA in addition to "Longhorn" in a cyberterror campaign lasting almost a decade.
When will the madness end? When will our taxes stop being used to such nefarious ends?
Stay tuned...


Pizza Assault? That does not sound good...
trigger'd
http://gph.is/28PNQ7e
Lol'd so hard
😂🤣