WikiLeaks Vault 7 part III - Marble Framework - The CIA's cloaking device for hackers
WikiLeaks' newest Vault 7 release, titled Marble Framework, discusses a host of tools used to hide the CIA's tracks. It does this in a very unique way, however, by replacing the code for a given malware program with another language AND its encoding equivalent, including such languages as Chinese, Russian, Korean, Arabic and Farsi.(1) This then gives CIA malware the appearance of having originated from one of these language groups as a means to throw off forensic investigators. In addition, Marble Framework may have provided support for sending encrypted communications as well.
This release is unique for WikiLeaks in that it is not an actual set of Wiki pages or emails. Rather, this is a .zip file containing literal source code to components of Marble Framework. This material is extremely technical, but I am able to share with you some of the more interesting finds from within these files. Marble Framework itself was developed in C++, so this could have been implemented on any number of possible platforms.
The components of the Marble Framework include:
- Marble
- Mender
- Mibster
- Farble
- Stringobfuscation
Top image is of the Temple of Athena taken by Travelpod.com
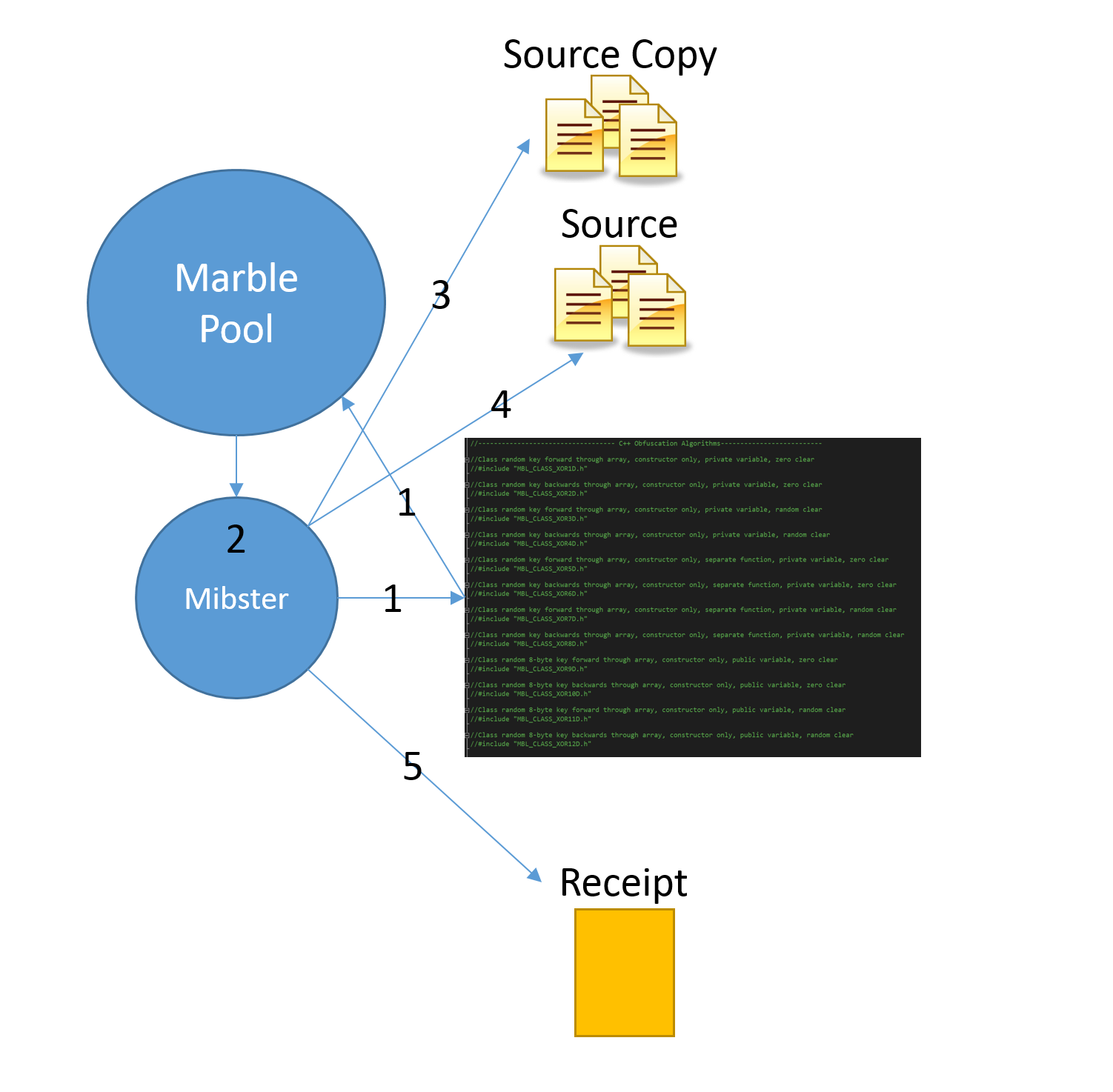
Marble
Upon installing the Marble Framework to a device, the user then runs a utility known as Mibster, or the Marbler, to disguise the Marble Framework, its components and communications in another language:
This will implement the actual string scrambling, copy originals and replace * code.
Source: Mibster.cpp
Mender can then be used to return Marble Framework to its original state:
The mender is the post build execution step in the Marble Framework. The * Mender restores the code to its original state after having been modified by the * Mibster.
Source: Mender.cpp
Farble
Farble appears to be a dialog window interface for the Marble Framework which gives the user various options and commands to run. For instance first function in Main Dialogue file (MainDlg.cpp) is PreTranslateMessage(MSG* pMsg). It appears various options, buttons and check boxes are given to encrypt, or "scramble" these messages using, such as CMainDlg::OnBnClickedEncrypt(WORD, WORD, HWND, BOOL&). The receiver of these messages can then use Farble to decrypt them and read the original message with functions like CMainDlg::initDescramble(farbleType fType, bool RXOR)
The source code for these projects also give us brief, but interesting insights into the personalities of these CIA malware developers. For instance, here are 4 lines of code in which a peculiar choice of variable and array names are chosen:
//UIUpdateChildWindows();
// wchar_t bitch1[] = {L'\x7FD9',L'\x7FB0',L'\x7FC4',L'\x7FA7',L'\x7FCF',L'\x7FFE',L'\x7FFE'};
// for( int i = 6; i > 0; i-- ) bitch1[i] = bitch1[i-1] ^ bitch1[i]; bitch1[0] = bitch1[0] ^ 0x7FBB;
// BYTE bitch2[] = {'\x7B69','\x7B00','\x7B74','\x7B17','\x7B7F','\x7B4D','\x7B4D'}; for( int i = 6; i > 0; i-- ) bitch2[i] = bitch2[i-1] ^ bitch2[i]; bitch2[0] = bitch2[0] ^ 0x7B0B;
StringObfuscation
A tool, br_angry, was developed alongside Marble Framework to facilitate these hiding functions on Android and iOS. As stated earlier, as it is written in C++, this program could have been run on any number of possible platforms.
Conclusion
While this release is fairly small compared to the others in Vault 7, it is no-less important to note and study. Now that WikiLeaks has the tools necessary to decrypt these encoded programs and communications, it may be possible for them to find and attribute attacks to these CIA tools. Stay vigilant, and stop to consider this fact the next time the mainstream media attributes cyberattacks to foreign hackers.
Note: I already tried to compile these but it appears a lot of core files are missing or edited. Anyone else care to run this on a professional version of Visual Studio to see if they compile or at least can open the project files? Link to source code .zip on WikiLeaks