HIGHRISE | Wikileaks Reveals Android Malware That Steals And Redirects Data Via SMS
An SMS Proxy App That Sends Stolen Data Between Target and Listening Post.

Today WikiLeaks published further documents from their Vault 7 CIA archive. Developed in 2013 HighRise is malware designed for Android mobile devices running Android 4.0 - 4.3. The HighRise malware is hidden in an application called TideCheck and once installed allows the operator to redirect SMS messages from a targets device.

HighRise is a SMS proxy that provides greater separation between devices in the field (“targets”) and the listening post by proxying "incoming" and "outgoing" SMS messages to an internet listening post. One use for it would be to intercept SMS's messages generated by Indicator of compromise (IoC) tools that use SMS messages for communication.
Indicator of compromise (IOC) — in computer forensics is an artifact observed on a network or in an operating system that with high confidence indicates a computer intrusion.
Typical IOCs are virus signatures and IP addresses, MD5 hashes of malware files or URLs or domain names of botnet command and control servers. After IOCs have been identified in a process of incident response and computer forensics, they can be used for early detection of future attack attempts using intrusion detection systems and antivirus software.
Uncovering Indicators of Compromise (IoC) Using PowerShell, Event Logs and a Traditional Monitoring Tool - SANS Institute -
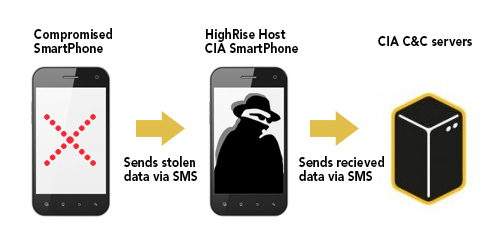
Highrise provides a communications channel between the HighRise field operator and the listening post with a TLS/SSL secured internet communication.
This malware is slightly different than most other computer viruses as it collects internet data from internet traffic and sends it via the SMS network which is a separate network all together. using this tewqunique allows the operator to keep a greater distance from the target. The HighRise manual shows that the tool must be manually downloaded, installed and activated on the "target" device. This means that the attacker either needs to gain physical access to the smartphone or they need to trick the "target" into installing it themselves.
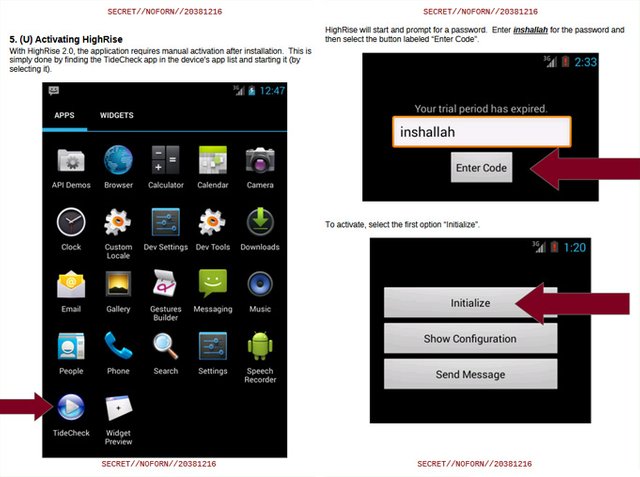
Manually activating the app requires the user to download and open the TideCheck app. Next they would need to “Initialize” it from the options menu by entering “inshallah” as the password (Arabic for “God willing”). After being activation and the device rebooted it will automatically stay running in the background.
The document states in the release logs that this malware was first created in December 2013. Since then Google have upgraded all the Android versions so I doubt this malware still works today. But we all know these things can be cauaght, copied and manipulated for other nefarious activities as we see has happened in this article below.
Android Malware About to Get Worse: GM Bot Source Code Leaked - Security Intelligence - February 19, 2016
IBM X-Force threat intelligence has found that the source code for Android malware GM Bot was leaked on an underground board in December 2015. The leaked code for the malware and its control panel have since been further propagated to different users, making this popular Android Trojan accessible to fraudsters for free, with a tutorial and server-side installation instructions to match.
GM Bot will be available to cybercriminals who can recompile the code, create new variants and use the leaked sources to build, sell or deploy this malware for fraud scenarios.

Woke stuff as always! Would have been nice if this stuff got leaked a bit sooner.
Yes, many questions to ask about timing and the WikiLeaks narrative...
https://steemit.com/wikileaks/@www.oye.news/breaking-news-assange-and-wikileaks-a-covert-intelligence-operation-uncovered
This post gets a 0.18 % upvote thanks to @fortified - Hail Eris !
thanks for info man!
I even made my infographic this time...
Some elements of the CIA are soooooo dirty- but they're in the process of being taken out
Yes and it's wonderful to watch.
Better late than never. This is why I bricked my old phone, which was KitKat that the vendor had promised to upgrade to lollipop, but didn't. I did, and hadda buy a new phone lol.
I don't mean this specific 'sploit, but rather the improved security that comes with newer Android.
Thanks for this post! upvoted and resteemed
Thank you.
Yes anytime I buy a new phone the first thing I do is root it.
??? @fortified you do know what that means in Australia don't you?
haha. Yes reading back on it now I see what you mean. I think if prob means the same thing in lots of the parts of the world.