"BASICS OF ETHICAL HACKING:SERIES #4.1"

Hi friends,I am continuing my post of "BASICS OF ETHICAL HACKING SERIES".
You can read my previous post from this below link:
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-1
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-2
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3.1
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3.2
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3.3
https://steemit.com/untalented/@danishali22786/basics-of-ethical-hacking-series-4
I am continuing my post of Malware Research -Trojans and Keyloggers
- Keyloggers are of two types:
1.Hardware Keylogger
2.Software Keylogger
1.Hardware Keylogger



A hardware keylogger is used for keystroke logging.A hardware keylogger is plugged between the keyboard plug and the USB or PS/2 port socket,and it works with PS/2 keyboards and USB keyboards.A hardware keylogger looks similar to a normal USB drive or any other computer peripheral.Due to this the victims can never doubt or catch that it is a keylogger.Hardware keylogger has inbuilt memory,which stores the typed keystrokes.
- KeyGrabber-Best hardware Keylogger
KeyGrabber is one of the most popular hardware keyloggers across the globe.This is primarily because of its large storage capacity.Keygrabber keystroke recorder comes in a standard version -4MB memory capacity, 2,000,000 keystrokes(over 1,000 pages of text) and a Venom version 2 billion keystrokes(over 1 million pages of text) organized into an advanced flash FAT file system.It is compatible with all the three operating systems,i.e Windows,Linux and Mac OS.
Features of hardware Keyloggers:
Observes www,emails and chat usage by children and employess
Monitors employee productivity
Protects children from online hazards and predators
saves a copy of the typed text
Records all keystrokes -even facebook passwords
Huge memory capacity,organized as an advanced flash FAT system
- Software Keyloggers
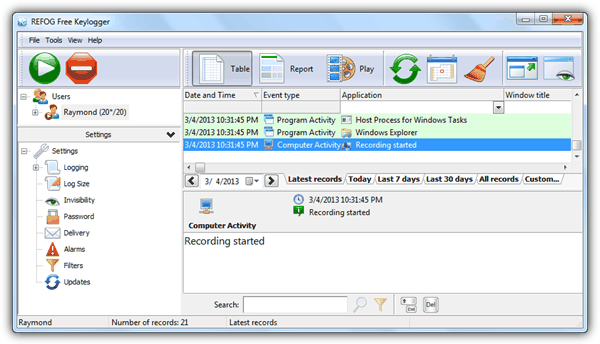
The Hardware Keylogger is useful only if you have physical access to the victim's computer .However,if you don't and if by any chance the victim notices it and knows about your intention,It is only then that the software keyloggers come into the picture.
- Software Keyloggers can also be classified into two types:
1.Local keylogger.
2.Remote Keylogger.
1.Local keylogger:They are used to monitor local computers (even your own pc).They are easy to install and are completely undetectable.However,once installed in the computer,they become really difficult to find them.This is because the keyloggers hide themselves from the "Task manger,Windows Registry,etc.
whenever you want to see logs,screenshots,etc,press a hotkey(example,Shift+Ctrl+F10).
There are hundreds of keyloggers available nowadays.However,some of them are user-friendly and are actually capable of hiding themselves once they are installed.
Some popular local keyloggers are:
Spy Agent
Refog Keylogger
There are many topics in Malware Research -Trojans and Keyloggers,so I will continue it in my next post.
Objectives of writing this post:
My main purpose of writing this post is to inform you all that there is no way to completely protect a network unless one knows what he is up against.Only by knowing how an attack happens,and what all an attacker can do to compromise with a machine,individuals and organisations can properly protect their systems.
Legal issues:
I request to all readers to follow legal procedures under all circumstances because you are hacking in to a system.
The government has made it mandatory to get prior permission before running any of the tools against any network.
There are many cyber laws made by the government,we must follow that otherwise It will be considered as a crime.
I have only basic information of ethical hacking learned from internet and by reading various books but I also want to learn it deeply.I want to join some big organization of ethical hacking institutes.But they are very costly.So I am finding a way to earn money and when I have enough money I will take admission to that ethical hacking institutes.
Thank you friends. If you like my post Please support me..
Hmm,, you are amazingly useful!
Keep in touch
You have my support on Steemit.com
Resteemed!
Thanks for supporting me and resteem my post @greatvideos,you are a very kind person
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by DANISHSTEEMIT from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.