Data Protection from attackers
I am very thankful to all Steemit members and users for giving very strong positive response on my first post of introduction.
As I discussed before I am security researcher and I will share my knowledge on security threats and their solutions in easy words. I will describe my points in very simple words in order to understandable for all.
So start First Topic 99% devices in all over world are vulnerable. Because most are using old non-updated systems and cracked software’s. This is all due to unawareness of users.
The question is that how a hacker can gain access to your System. Mostly users prefer to use free software’s or cracked, patched versions of the software’s.
99.9% cracks and patched are binds with backdoors or keyloggers. When a user installed cracked version then automatically hacker gain access to his/her system because hacker create a backdoor on device and then he can easily gain access on System.
We think that antivirus can protect our system, but I want to say that AV can be bypass. In this way, AV will not be able to detect the virus.
I can make video tutorial where I can show that how to make a backdoor virus which can bypass all type of securities but most people will do misuse of those tools. Therefore, I am not talking about such tools.
After all this everyone is thinking how we can protect our systems and sensitive information.
1- First of all, you have to install latest updated version of windows like as Windows 10 or Linux base window because the company always give the patch of security hole for windows and hackers always try to find the hole in windows where they can penetrate systems. Therefore, it necessary to update windows.
2- Do not run as an administrator of your PC for your day-to-day activities.
3- Keep your computer patched provide by Official authority and up-to-date, not just the OS, but also the installed software.
4- Do not open or click on items that have a “time component”—this could be phishing, especially when it’s from an unknown or unexpected source.
5- If you do receive something questionable, call the person who sent it, make sure it’s from them and that it is indeed urgent, etc. This will save both you and your company!
6- Occasionally inspect your wires. Maybe you do have a hardware keylogger. No one knows how prevalent hardware loggers are because no one checks. Keep your AV (I RECOMMEND ESET SMART SECURITY) updated, and do not install anything you do not need. If a new “search bar” or additional shortcuts appear on your PC, find out what program installed those and remove them all.
Everyone prefer Avast software because of free, but I am telling you from all AV AVAST, Windows DEFENDER, NORTON, MacAfee, AVG can easily be bypass.
Use top rated reviews AV like Bitdefender, Kaspersky or ESET. I recommend ESET SMART SECURITY v10 because its detection technique is different from others.
I also think necessary here to install the latest version of AV. I saw mostly users install old versions. The old version is not being able to detect latest viruses.
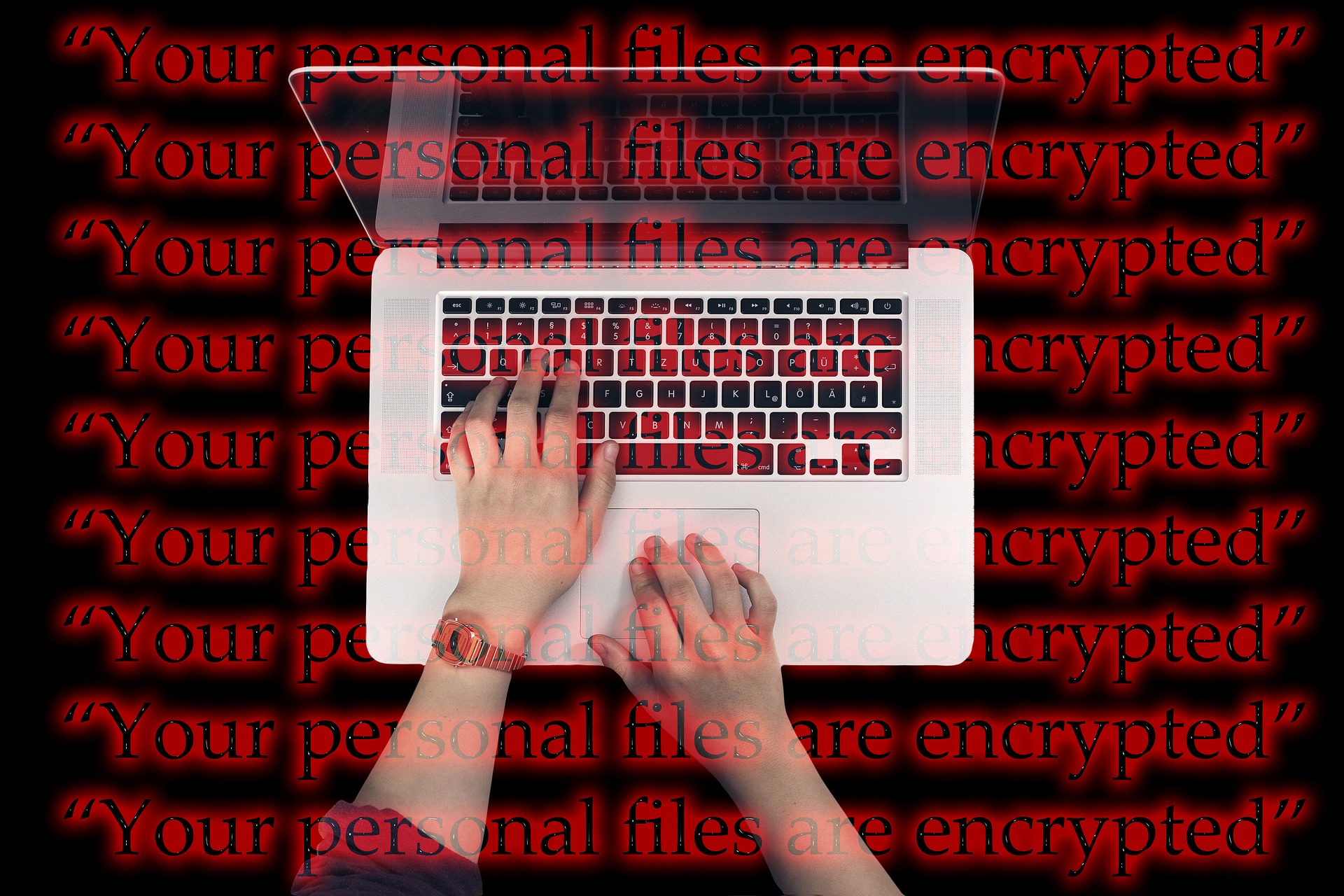
Nowadays a high rated virus called “RANSOMWARE “is spreading fasting. RANSOMWARE is most dangerous malware which will encrypt system data, and you have to pay hacker for decryption of data.
1-Updated version of Windows
2- Latest updated version of AV
3- Latest updated spyware protection (RECOMMEND: Malwarebytes Anti-malware)
4- Always check running process and their paths.
This is a necessary and very basic information by which you can protect yourself and your sensitive data.
I hope you will like my effort. In future I am thinking to post Episodes on Ethical Hacking Training by which you will know the basics of hacking methods and their solutions.
Thanks for reading
Muhammad Aamir Hussain
Follow me @maamirh










nice information..
Beneficial information !
Bad side of hacking. Thanks for it.
Hello, please follow the rules of the group Steemit for Resteem ↕ and you will be resteemed by the most active members in the group.
You have to resteem a post from the group before you post yours there.
Here is : HOW TO RESTEEM ON STEEMIT ?
ok
In this days and age. It is equally important to be security conscious..the walls of Babylon will protect you. We need to armed ourselves with the latest digital security information everyday. Thank you for this enlightening post.
Yes right.