HOW TO : securise Tor Browser - Be anonymous on the INTERNET #1
How to securise Tor browser
What is Tor?
Tor is free software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.
Using Tor does not make you totally anonymous, indeed, the fingerprint of your browser can identify you.
What's the fingerprint ?
An user can be tracked on the internet by his cookies, his MAC address or by his IP address. But it is also possible to follow a user through the footprint of his browser. This fingerprint is calculated from browser-accessible data such as the operating system used, screen resolution, time zone, fonts on your computer,the UAS (User Agent String User Agent String, String containing information about your browser), plugins installed, list of accepted MIME types ...
So the more your browser will be different from other Tor users, the more unique you will be, so more easily identifiable. Likewise if you walk down the street with atypical clothes. While if you are dressed like everyone else, you will be fused into the mass and you will be more anonymous
1. Ask for web pages in English
To avoid appearing different from other browsers it is better to ask for the pages in English.
The first time you use it, Torbutton asks you if it should ask for the pages in English.
If you did not say yes, I think you can activate this option by clicking the Torbutton icon and then clicking the "Edit details that distinguishes you from other Tor Browser users" The "Security Settings" tab.
To check, in a new tab type about: config
Look for the following values:
extensions.torbutton.spoof_english --> Must be set to True
intl.accept_languages --> Must be on the value en-us, en
general.useragent.locale --> Must be on en-US value
2. NoScript & JavaScript
Enabling NoScript is required.
Click on the S at the top left and then on "Forbid Scripts Globally (advised)"
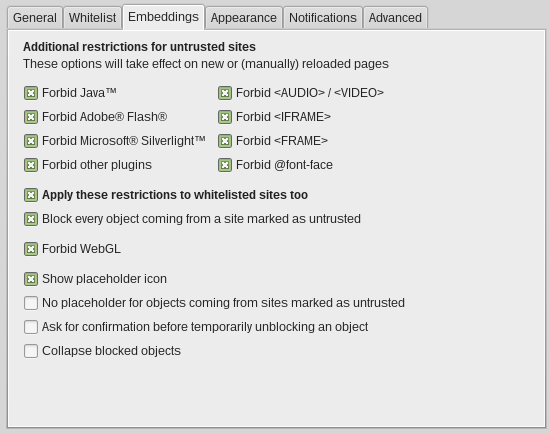
Click on the S again, go to "Options", on the "Embedded objects" tab and check all the boxes that correspond to scripts as well as Audio / Video, <IFRAME>, <FRAME>, @ font-face and WebGL.
If you do not trust NoScript to block JavaScript open a new tab at: about: config.
Find the value javascript.enabled and double-click it to go to false.
3. Browser extension
On Tor Browser, NEVER install any extensions.
Sites can view the list of extensions installed on the browser.
This alters its fingerprint and makes it a little more unique.
4. Downloads
Unless you have disabled it, when you upload a file with TorBrowser,
You should have a warning with two options:
- Open the file
- Save file
Especially never choose to open a file directly! You would expose your real IP address (not your Tor address) to the site.
Never download executable files from the clearnet with TorBrowser unless you are using an HTTPS connection with a valid certificate.
5. HTTP Referer
Wikipedia wrote:
The HTTP referer (originally a misspelling of referrer[1]) is an HTTP header field that identifies the address of the webpage (i.e. the URI or IRI) that linked to the resource being requested. By checking the referrer, the new webpage can see where the request originated. In the most common situation this means that when a user clicks a hyperlink in a web browser, the browser sends a request to the server holding the destination webpage. The request includes the referrer field, which indicates the last page the user was on (the one where they clicked the link). Referer logging is used to allow websites and web servers to identify where people are visiting them from, for promotional or statistical purposes.
If you come from a search engine this is not embarrassing. On the other hand if the referer indicates the address of a site of sale of weapon or another site in .onion it exposes it.
To do this we return to about: config
network.http.sendRefererHeader --> Change from 2 to 1. If you set 0, some sites may no longer work.
network.http.referer.spoofSource --> Pass it to True instead of False
The best way to avoid referring is to copy / paste the link.
6. Bridges obfs3
If you aren't using a VPN and you think Tor's use is endangering you, you can use obfs3 bridges to connect to the Tor network. This confuses communications and makes it difficult to locate your use of Tor. However, your navigation will be slower.
The list of bridges (bridges) obfs3 is not public. On the other hand, there is no
An infinite number of nodes and scarcity is possible. Use them only if necessary.
If you need it, when starting Tor Browser click on configure.
In the questionnaire, click on next until the question "Is your ISP blocking connections to the Tor network?" And indicate yes.
After clicking again next, the questionnaire will ask you to select which type of bridges you want to use.
Normally, obfs3 is selected by default. If not, select it and click Connect.
7. Tracking by ETAG
Your browser often saves pages in its cache. This saves bandwidth.
On each given page, the server gives the browser an ETAG. It is a sequence of numbers and numbers that will change if the page is changed. Normally used for useful purposes (do not consume too much bandwidth) its use can be diverted by giving a unique ETAG to each browser.
The only way to protect yourself is to empty your cache very regularly or to prohibit its use.
The best solution is to go regularly to the Tor Button menu and click on "New Identity" (Ctrl + Shift + U) .
8. Canvas HTML
A canvas is an image to be generated by your browser
Taking into account your hardware like the graphics card and other parameters.
This canvas allows to gather a lot of information on your browser and your computer. The result is sometimes unique.
To protect themselves from it, it is enough to disable the scripts in NoScript (since it is often JS script).
If you leave your Javascript, the Tor browser will notify you if a site tries to generate a canvas. Always choose to block it.
Even all scripts disabled Tor browser will display an alert when attempting to extract an HTML canvas.
9. Security Slider
The Security Slider allows you to define security levels and reinforce the browser by removing as much as possible the available attack surface.
It is accessed by clicking on the Torbutton and then on Privacy and Security Settings.
The higher the level, the more the browser will disable possible attack vectors. I advise to put him at the highest.
All boxes must also be checked.
10. PDFJS Viewer
PDF.js Viewer is the Firefox PDF reader (and therefore Tor Browser). Recently a vulnerability has been discovered that allows access to sensitive files. To prevent
It is better to disable it in about: config.
pdfjs.disabled --> Set it to True.
source :
http://neckara.developpez.com/tutoriels/securite/empreintes_navigateurs/
FWD


Good article
Congratulations @juanpierre! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard!
Participate in the SteemitBoard World Cup Contest!
Collect World Cup badges and win free SBD
Support the Gold Sponsors of the contest: @good-karma and @lukestokes
Congratulations @juanpierre! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!