An Ethical Hackers Guide: Part 9 - Network Reconnaissance Using Nmap
Hello Steemstemers, Utopians, Future Hackers and Crackers :]
%20(1).jpg)
It has been far too long since Part 7, and today we're going to be really getting into it. I have spent the last few days, starting and stopping several different projects, for several different communities, but for the time being, I'd really like to just carry on with this guide, as this is what I enjoy, and have already prepared myself to do. I will be continuing to work on these projects in the near future, so please understand these guides may come out a bit less frequently for now.
Nmap; Scanning, & Enumeration
Today, we will be doing what will generally be your first steps upon acquiring a target. Nmap, as fairly well described in Part 5 of my guides, is a network security scanner, used to scan targeted servers, and return many different bits of data about the machines running them. Nmap can be used to retrieve information such as open ports, services running, Operating system, as well as sometimes even device type and more.
The first thing we will need to do, is power on our Whonix Gateways, as well as our Kali VMs. You must FIRST power on your Whonix gateway, then run a 'Whonix check'. After that has completed, Turn on your Kali VMs, and visit https://check.torproject.org/, to ensure that your traffic is being routed through the Tor Network. Your computer should now be quite crowded with VMs, like the image below.
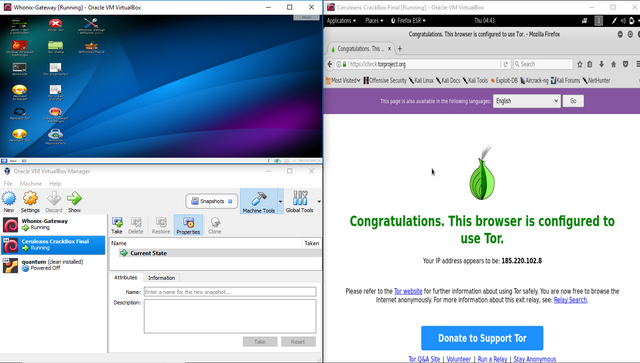
Screenshot
External Web Servers
As this is an ethical hacking tutorial, I will never be teaching you anything Illegal, however, I do want this to have practical use, and hacking in general, is illegal, which though unfortunate, leaves us little room to work within as white-hats. Thankfully, the good people at Nmap have created their own server, which they allow anyone to test on and learn their software, as well as other security scanners.
Find the IP Address
There are many services like this, and until we get into actual bug hunting, this is how we will do the majority of our attacks. The website we will be investigating, is "scanme.nmap.org", and this actually brings us nicely to the first issue when wanting to attack a web server. The URL 'scanme.nmap.org', is simply their domain name. To run many different attacks on a web server, from Nmap, to DDOS, you will often need the IP address of the server. For those of you who don't understand IP Addresses, give them a quick google search, as we wont be discussing that here.
Screenshot
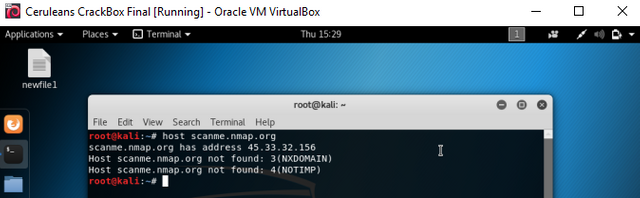
The tool we will use to enumerate the IP address is called 'host', so go ahead and enter into the terminal the command 'host scanme.nmap.org' now. You can replace the URL here with anything you like to do some testing. now that we have learned the IP address, lets note that down into a recon file we will create now. Here we will use the commands "echo 'IP address = 192.168.0.1' > recon-scanme.txt", and this will create a new text file, with our targets IP address noted down for future use.
host scanme.nmap.org
echo 'IP address = 192.168.0.1' > recon-scanme.txt
cat recon-scanme.txt
It is good practice to write down any relevant information discovered about a target, as this can come in handy in many situations. Finally, we use the cat command to ensure information was written to file. I will not be discussing this step again through this guide.
Scan The Targets Address
Now that we have acquired our targets IP Address, we have everything we need to start the Reconnaissance Phase of an attack. This guide focuses on using Nmap to enumerate services, ports, addresses, and more. The first thing you will need to know about nmap is that there are many different types of scans you can perform, for many different situations. Since we know that this is a free server, open for us to test on, lets just go ahead and do a plain scan and see what we get.
nmap 45.33.32.156
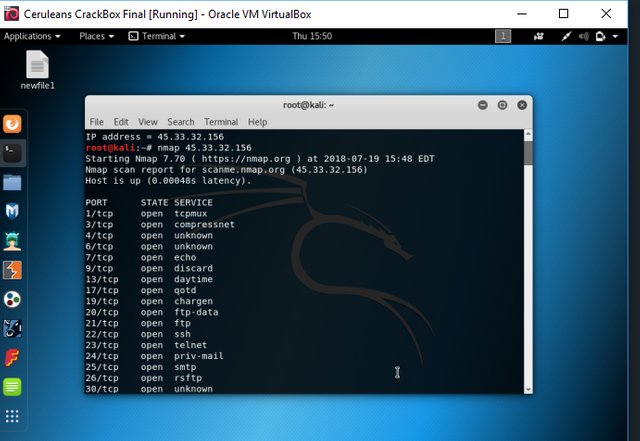
Screenshot
As you can see in the above image, this web server has quite a few open ports, in fact some would say too many. The reason there are so many services running on this web server, is because it was designed with you in mind! :P This server has been designed for you to be able to test as many things as you're able to on it. Being realistic, We would only jot down the major services to start, like port 21, 22, and 23, the ftp, ssh, and telnet protocols.
There are several other options to note down here, however this is not a real attack, therefore lets move on to some more interesting methods of scanning. On a real target in the wild, there will often be defenses such as firewalls, IDS/IPS services (Intrusion Detection/Prevention), and often several network administrators, all tasked solely with stopping people like us from gaining access to their systems.
Alternative Scanning Methods: UDP, Firewall Evasion, and Decoys
There are so many different scanning methods, and unfortunately we cannot discuss them all here, but I have selected a few different ones to discuss with you for now. The first thing I'd like to mention, is that this far, we have only scanned TCP services, and it is always a good idea to do a UDP scan as well. To do this, we will use the '-sU' argument for Nmap, which will then scan for UDP services instead.
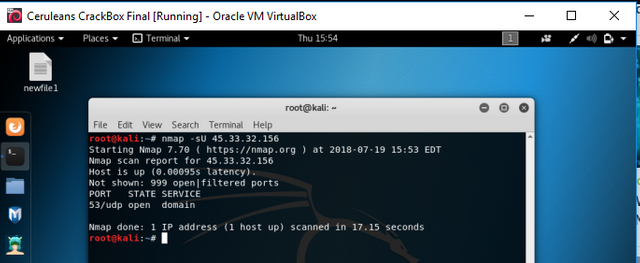
Screenshot
Cool, so at first glance it looks like there is only one service running using the UDP protocol, and that appears to be DNS related, meaning there are most likely many possible exploits to attempt. Again this is all just reconnaissance for now, so lets 'cat' that into our recon file and carry on to the next type of scan.
Using this server, isn't very fun for firewall evasion, as there are no firewalls set up unfortunately. This makes it easier for us to test on, however not very feasible for learning. Once we go through the mains steps of an attack, we will use these tools on a real world service, so just hang in there. Never jump in to something like this before your ready, and prepared for the consequences. Though I will not bother to include pictures of this step, there are several scans you can use to get nmap through alot of firewalls.
The '-f' argument for Nmap, can be used to send our packets in tiny 'fragments', making them much harder for firewalls and other prevention systems to inspect. This is mostly used on older systems, though is still prevalent in the wild at times. Another similar option is the '-mtu' type scan, where you can specify the size of the packets created by Nmap. Some more interesting tactics, are the Zombie/Decoy scans.
Zombie/Decoy Scanning Techniques
Past a certain point, it becomes less about being detected, and more about staying anonymous. Web servers are hit with attacks from all over the world, on a daily basis, varying greatly on their popularity. Knowing that, once we have done all we can to to prevent the system from knowing that they are under attack, the main issue becomes preventing them from learning who is attacking them. In this way they can not lock us out, or prevent us from getting further in our attack.
The zombie scan, is an Nmap scanning technique that uses an idle device on a network, so as to originate the scan from a location that is not your computer. This scan is used with the '-sI' argument, though unfortunately requires an idle device to be running on the network, thus we will not be using this today, though definitely fun to play around with, especially on a NAT.
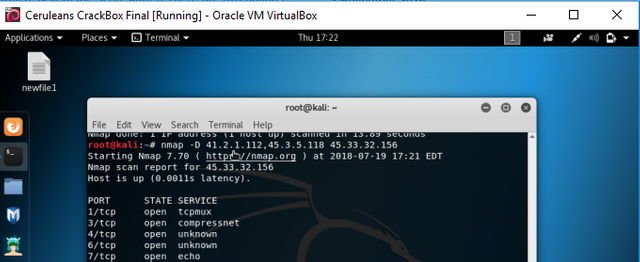
Screenshot
When zombie scans cannot be used, the Decoy scan is an equally good option, as it generates random IP addresses for the source of the packets, or allows you to choose your own, should you so wish. This allows you to make it appear as if the attack is coming from all over the world, when really it is just one computer. The decoy scan can be used quite simply, with the '-D' argument, followed by the IP addresses you choose, or for random use, 'RND:5' where 5 is equal to the number of addresses you'd like to include.
(I wanted to add guys, these same scans can be used on any internal addresses within your network, or to scan an entire network, but for now I just wanted to get the external stuff done, as theirs not much interesting to scan in my house. But feel free to try this out on any device you own to your hearts content.)
Conclusion:
Nmap is quite a useful tool, that has so very many different use cases, and we will be using it throughout these guides, so keep all of this info in mind, and honestly it would be best if you try the tool out as well :) Give it a little practice, and you'll have the hang of it in no time. For now, I must go, as my rabbit has been bothering me for the last ten minutes -_-, however we we'll be back shortly with our next guide, carrying on the reconnaissance steps, only this time using Metasploit, an even more wicked tool in my opinion. Can't wait to see you all then.
Happy Hunting,
Cerulean.
Nice series you have here. Maybe you can also write something about how unsafe open networks are :)
Thats a great Idea, there are several techniques that involve open networks, I will try to work that in, in the near future. Thank you so much for the suggestion, and I really hope you've been enjoying these so far :)
Hi @ceruleanblue!
Your post was upvoted by utopian.io in cooperation with steemstem - supporting knowledge, innovation and technological advancement on the Steem Blockchain.
Contribute to Open Source with utopian.io
Learn how to contribute on our website and join the new open source economy.
Want to chat? Join the Utopian Community on Discord https://discord.gg/h52nFrV
:o Thank you guys so much! Its amazing to see some Utopian/Steemstem support. I have been greatly enjoying being a part of both of these awesome communities, and I hope to only produce better and better content for each them. Thank you both for the appreciation, and I hope you guys know how much you do for the Steem community in general!
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by ceruleanblue from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
Congratulations @ceruleanblue! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Do not miss the last post from @steemitboard:
SteemitBoard World Cup Contest - The results, the winners and the prizes
Congratulations @ceruleanblue! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOP