How I got 'hacked', recovered my accounts and improved the Steemit account security

Incorrect Password
Recently I've noticed some of my accounts return 'Incorrect Password' when I try to log in. I haven't given it much attention, since those accounts are just test ones, and they have no funds on them.
A few days ago, I've stumbled across this post.

It has become crystal clear to me, that my accounts are no longer mine.
How it happened
I was negligent. When I created the accounts, I chose to just repeat the username 3x and add a 2 to the end.
So my username would be flymetothemoon and my password flymetothemoonflymetothemoonflymetothemoon2.
I don't know exactly how the 'attacker' got my password, but if I was malicious and wanted to steal a bunch of steemit accounts, this is what I'd do.
Get all steemit usernames
This is pretty easy, and only takes a 1 line of code:
all_usernames = steem.rpc.lookup_accounts('', 10000000)
Now that we have the usernames, we can try generating private owner keys.
Each owner key is generated from the following seed:
username + role + password
So in our case, we can get our owner key from:
flymetothemoonownerflymetothemoonflymetothemoonflymetothemoon2
We have the username, and the role. All we have to do is find the password.
To find the password, we bruteforce all potential password combinations.
Every time we generate a private key, we simply check if its public key corresponds with the real public key. If it does, we found our password.
To get the real public key, we can simply look at steemd.com/@yourusername.
When we do the bruteforcing, we can use password lists and most commonly used methods that people use. Unfortunately, humans are very predictable. Repeating a username 3 times and adding '2' to the end seems to be one of the patterns.
To learn more about password bruteforcing, check out this video:
If you haven't changed your steemit password to the new randomly generated one, please do so asap.
Account Recovery
Fortunately, Steemit allows for pretty painless recovery process. Since all the accounts are created via Reddit/Facebook, we can use that to verify the ownership.
This however only works with accounts that were created on Steemit. If you've created your account trough mining, or from existing account, this recovery method won't work. You can find your Recovery account on [steemd.com/@yourusername][https://steemd.com].
Recovery Process
Open a new 'incognito' window in your browser. For maximum security, make sure you have no other tabs open, or any 3rd party plugins enabled.
Go to https://steemit.com/recover_account_step_1.
Type in your old username/password.
Then, you will be prompted to confirm your Reddit/Facebook account. Make sure you're logged into the same account you used to create the Steemit account.
Afterwards, Steemit will generate a new secure password for you. Save that password somewhere safe (not in your browser).
How I do security now
I have re-generated the passwords for ALL of my Steemit accounts. All of the passwords are long, randomly generated ones.
Storing the password
I have decided to keep passwords somewhere safe. You don't really need your password to use Steemit after all.
All of my computers run Linux, and all of my SSD's are encrypted using LUKS.
All of my computers share some folders between them (over encrypted sync), however those folders are encrypted using encfs.
And lastly, in my keys folder, I have an encrypted KeePassX database. (keepass is a free, cross-platform password manager).
So, my passwords are pretty safe.
You don't need a password
You don't need your password, or the owner key to use Steemit.
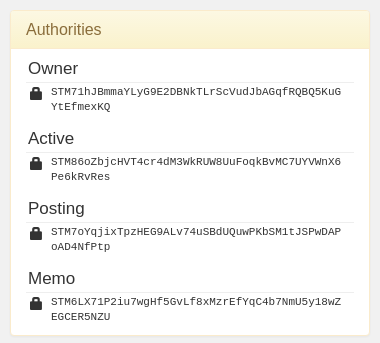
| Key Type | Action |
|---|---|
| Posting | Comment, Vote, Follow |
| Active | Send Funds, Power-Up, Power-Down, Trade |
| Owner | God mode. Change any other key including itself. |
You can login into steemit.com just using your posting key.
For maximum convenience, I have added all of my accounts with their posting keys as a password to LastPass:
This way I can login into my account with a single click, from any computer I own. This will allow me to post, vote, comment and follow people.
If I want to send money, or power up, I will be prompted to enter the active key.
If someone steals your active key, they could steal your STEEM and Steem Dollars. They will however not be able to steal your Steem Power.
I keep my active keys outside of the browser as well. Most of my accounts only have Steem Power, and thus, even if I lose my active key, I am still safe. I can re-generate my active key from the password.
Generating the Active/Posting Keys
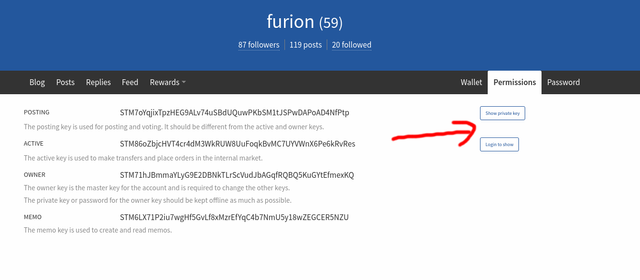
The easiest way to get your private active/posting keys, is to go to the Permissions tab on your Steemit account.
However, since I have multiple accounts, and I use them from Python as well, I've made a script that can generate my keys from passwords. It can also import the keys into Piston.
import subprocess
from pprint import pprint
import json
from graphenebase.account import PasswordKey
from common.helpers import update_json_node
def load_users():
with open("steemit_accounts.csv") as f:
lines = f.readlines()
return lines
def regen_keys(username, password, role):
pk = PasswordKey(username, password, role)
return format(pk.get_public_key(), "STM"), pk.get_private_key()
def import_key_into_piston(private_key):
subprocess.run(["piston", "addkey", private_key], stdout=subprocess.PIPE)
def run(write_mode=False, import_mode=False):
roles = ["posting", "active"]
accounts = load_users()
posting_keys = []
active_keys = []
for account in accounts:
for role in roles:
public_key, private_key = regen_keys(account.split(",")[0], account.split(",")[1].rstrip("\n"), role)
if import_mode:
print("piston addkey %s" % private_key)
import_key_into_piston(str(private_key))
key = {
"name": account.split(",")[0],
"role": role,
"public": public_key,
"wif": str(private_key),
}
if role == "posting":
posting_keys.append(key)
if role == "active":
active_keys.append(key)
# pprint(posting_keys)
if write_mode:
update_json_node("accounts.json", "posting", posting_keys)
update_json_node("accounts.json", "active", active_keys)
def update_json_node(filename, node, node_data):
data = load_json(filename)
data[node] = node_data
write_json(filename, data)
def write_json(filename, data):
with open(filename, 'w') as data_file:
json.dump(data, data_file, indent=4, sort_keys=True, separators=(',', ':'))
if __name__ == "__main__":
run(write_mode=True, import_mode=False)
TL:DR;
To sum up:
- change your password to the long, randomly generated one
- save your password somewhere super safe
- use posting/active keys to interact with steemit.com
Good post - I've had to do account recovery too, when my password suddenly became invalid. But nothing was taken from the account.
You made my account a bit safer now. Thank you :)
Nice "hack"))
And thank you for "steem.li"
It does not hurt to have the option to add another layer of security such as 2FA and let users decide if they should activate it or not. But even adding 2FA support can be trickier as if not properly implemented such as a case where you can login and disable it if you manage to get the password, without having to enter the 2FA code geneated on your smartphone, then it is rather pointless. For example if you just enable 2FA security for wallet related operations, but it is not required for you to login in your account...
2FA does not protect you from a stolen private key. This is why ideally you would keep the password somewhere safe, and only login to steemit with your posting key.
Yes, I know you can still use the private Owner key to import in the CLI wallet for example and run away with the SBD and STEEM tokens that a user has...
Using something like a U2F key, Trezor or Ledger would protect you from that, if the devs enabled support for it. Those devices can sign a transaction without ever exposing the private key to interception.
Nice find. 2 factor would also be welcome here. Because i never trust for 100% on a static password that is stored somewhere.
Brilliant post. I think everyone should read this.
I am new to steemit and my password was generated randomly so I guess I am safe from such attacks. Am I? I suppose steemit should implement 2FA
the 2 Factor Authentication is a must . Most sites have already implemented it. Steemit should implement it too
It doesn't work that way. With the password or keys a malicious hacker can do anything without loging into steemit.
Unfortunately 2FA is not trivial on a blockchain, you have to remember that any attackers do not need to use steemit.com to hack your account. There are initiatives underway for STEEM but they're not ready for mainstream yet.
Not only this. If you don't watch out your cryptocurrency wallets can get get raided as well. http://livestream.com/internetsociety/hopeconf/videos/130745035
Is the Steemit randomly generated password really random? I mean can we trust that it's not using some bad random library ?
This will become more of an issue for more of the community as the steem wealth is distributed, thanks for keeping the topic fresh.