The Shadow Brokers to NSA Equation Group: We is Gots Yo Sheeat, Pay Up or Done Get Doxed

Barely a month has passed since the Wanna Cry ransomware caused chaos for businesses, institutions and individuals using Windows XP. Most notably, Wanna Cry caused major difficulties for the National Health Services of the UK.
The Shadow Brokers, for a lack of a better word, are a shadowy hacker group believed to be responsible for leaking NSA cyber weapons.
On same day that the Shadow Brokers released their latest monthly service dump, a new outbreak of ransomware spread quickly across the internet and around the globe.
In a nutshell, the latest ransomware release, Peyta, encrypts your hard drive rather than encrypting individual files, bypasses the MBR and infects your operating system. The malware infects portions of your hard drive effectively blocking access to anything on the drive.
Although there have been reports that the Shadow Brokers were involved in the Wanna Cry ransomare release last month, it is yet to be determined if there’s any connection between the Peyta Ransomware outbreak and the group’s monthly dump. Different versions of the Peyta malware have been in circulation for at least a year.
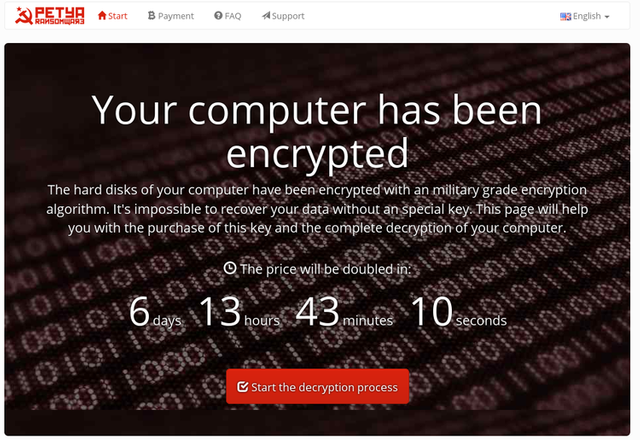
The price for unlocking the ransomware is currently 0.9 BTC, though officials are telling the public not to pay the ransom as there’s not guarantee you will get your files back.
July 2017 Monthly Dump Service
Earlier today the Shadow Brokers made this post in Steemit:
The Shadow Brokers Monthly Dump Service
Previously, the notorious hacker group requested a sum of 100 zec (Zcash) for its monthly subscription protection program but has now increased the amount to 200 zec. Congruently, a VIP service has been established for a single payment of 400 zec.
Last month, the Shadow Brokers announced to release more zero-days exploits and hacking tools developed by the US spy agency every month from June 2017, but only to private members who will subscribe for receiving exclusive access to the future leaks.
ShadowBrokers vs Equation Group Hacker
In their famously cryptic ebonics laced dialect, the Shadow Brokers also have threatened to reveal the identity of a member of the NSA’s elite hacking collective known as the Equation Group.
Naming the Equation member as only the ‘doctor person’, the Shadow Brokers describe the hacker as recently starting a security firm and who has been making , then deleting, disparaging tweets directed at the Shadow Brokers on Twitter.
"TheShadowBrokers is hoping 'doctor' person is deciding to subscribe to dump service in July. If theshadowbrokers is not seeing subscription payment with corporate email address of [email protected] then theshadowbrokers might be taking tweets personally and dumping data of 'doctor' persons hacks of China with real id and security company name."
The hacker group’s broken English can be hard to follow at times, but this threat is clear as day.
Pay up or get doxed.
It’s still impossible to know for certain what zero exploits will be released in the June 2017 dump but the Shadow brokers did mention the following:
- Compromised data from banks and SWIFT providers
- Exploits for Operating Systems including Windows 10
- Exploits for web browsers, routers, and smartphones
- Stolen network information from Russia, Chinese, Iranian and North Korea nuclear missile programs.
NSA Hacking Tools Obtained How?
A pressing question about the mysterious hacking group is just how were they able to obtain the NSA hacking tools? The answer to that question is just as mysterious yet there’s some speculation as to possible sources who could have supplied the cyber weapons.
It isn’t clear where the Shadow Brokers got the NSA hacking tools, but the arrest of former NSA contractor Harold T. Martin III last August for stealing a massive amount of data has made him the most likely suspect.

It has also been reported by former NSA officials that the hacking tools in obtained by the Shadow Brokers are, in fact, identical to those found in the possession of Martin.
Former NSA officials have claimed the Shadow Brokers’ tools are “identical” to those taken by Martin, reports The Washington Post.
The US government said it seized 50 terabytes of confidential data from Martin’s home which was stolen from the NSA and other intelligence agencies. A veteran contractor, Martin had access to classified information as part of his work in the intelligence-gathering division of the NSA named Tailored Access Operations.
He has been in custody since his arrest and is facing espionage charges. Another NSA employee was also arrested in 2015, but no information has been released about the individual.
(RT)
If Martin is indeed the source of the NSA cyber weapons then it is not inconceivable to expect monthly dumps from the Shadow Brokers for years to come.
Martin’s hoarding of NSA classified material at his home has been described as “breathtaking”.
Investigators allege they found documents marked "top secret" and "secret" within his house, storage sheds and a Chevrolet Caprice, which was regularly parked in his driveway. The material comprised "irreplaceable classified information," the document reads.
Martin engaged in "a course of felonious conduct that is breathtaking in its longevity and scale," prosecutors say. He is believed to have taken documents that dated as far back as 1996, when he first gained access to classified information with the U.S. Naval Reserves.
images
Zero Hedge, 1-news-softpedia, bank info security

It is great when huge national corporations with powerful tools get leaked to the public.
Sucks that everyone has to suffer from these malicious ransomware attacks.
It is great to have leakers of information but i agree that with the release of powerful cyber weapons we inevitably suffer and/or become the targets of these weapons.
thank you friend
Good post, thanks for sharing
Please come visit and read this interesting post https://steemit.com/news/@hamzaoui/wow-china-and-canada-sign-an-agreement-not-to-launch-cyber-attacks-against-each-other
Resharing @phibetaiota
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by v4vapid from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, and someguy123. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you like what we're doing please upvote this comment so we can continue to build the community account that's supporting all members.
Excellent post brother, thank you for the information, I would like you to give me your support as I am new to Steemit and my only goal here is to make known to the whole world the situation that is living in my country, Watch my blog as much as you can, God bless you.
Interesting stuff. This just goes to show the incompetence of the NSA. And why backdoors and programs to bypass security are never a great idea.