STEEMIT needs 2FA
Hi STEEMers!
In the light of the above, with a cyber attack on STEEM, when about 260 accounts were compromised and in addition to this post about security and risks
SteemIt.com is to be hacked? Security advisory I propose to discuss such an important moment, as two-factor authentication also known as two-step verification (2SV) and necessity of adding them on STEEMIT.
Two-factor authentication or 2FA - is a user identification method in which a service where two different types of authentication data are used. The introduction of an additional level of security provides better protection for your account against unauthorized access.
Two-factor authentication requires user have two of three types of identification data.
- Something, you know;
- Something that you have;
- Something inherent to you(biometrics)
1st is passwords, PIN codes, secret phrases, and so on - something that the user remembers and enters into the system when requesting.
3rd authentication using biometric devices and authentication methods. This may be, for example, face, fingerprint or retina scanners.
Discuss in more detail in 2nd paragraph.
It is a token that is a compact device that is in the user's property. The most simple tokens do not require a physical connection tocomputer - they have a display that shows the number that the user enters into the system for entry - the more complex are connected to computers via USB and Bluetooth-interface.
Today, as a token can act smart phones, because they have become an integral part of our lives. In this case, the so-called one-time password is generated or using special applications (eg Google Authenticator, Authy? e.t.c), or comes on SMS - is the most simple and user-friendly method, which some experts estimate as less reliable.
Theoretically, that makes it much harder for a crook to get enough information to take over your account, because any login codes he steals today are useless tomorrow.
Problem is, these 2FA systems all work a bit differently, and they all have different strengths and weaknesses.
This post helps you understand these differences.
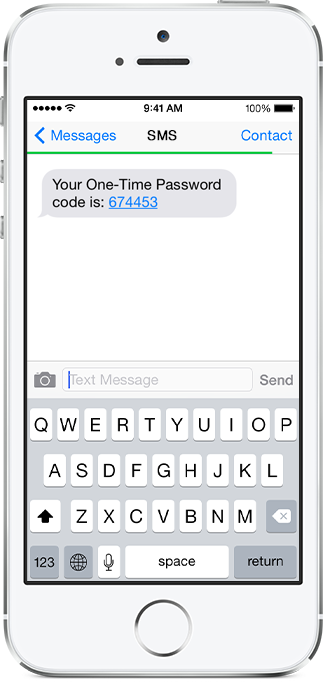
One-time passwords via SMS
This is where you are prompted to enter an additional numeric code after authenticating with your username and password.
The code is sent to your mobile device as a text message (SMS).
Once the code is received you enter it in the field provided and the login proceeds.
It’s important to point out, specifically for this type of two-factor authentication, that SMS codes do not always work for everyone.
The server might not have your country on its list of supported regions; your mobile provider might not be able to deliver the messages; or you might have unreliable mobile coverage.
For obvious reasons this won’t work with landlines either, but there is a slightly different version that will call you and read out the code.
Advantages and disadvantages
+ The code is different every time, so if your regular password is breached or stolen, it’s not enough for a crook.
+ The code is tied to your phone number, which can’t be changed by malware on your computer.
- If your mobile network is down or you are out of the coverage area, you can’t receive the code.
- Crooks may be able to port your phone number (also known as a SIM swap) through an accomplice in a mobile phone shop, and receive your calls and messages until you notice your own phone is dead.
- If you are logging in and receiving the SMS on the same device (e.g. a tablet or smartphone), your login codes are as much at risk as your password.
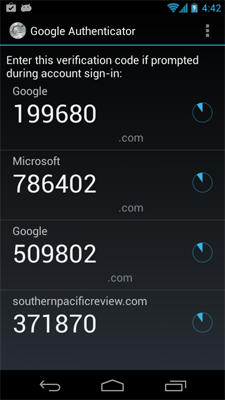
Authenticator Apps
Authenticator apps perform the same type of service as SMS 2FA but instead of the login codes being sent to you, they are generated locally on your smartphone or tablet.
This type of authentication relies on cryptographic algorithms for time-based one-time passwords (TOTP).
The basic functionality is that a secret starting key or seed is generated and stored by the server, and then scrambled up cryptographically with the current time and date whenever you login. This produces a time-specific code, usually valid for 30 or 60 seconds.
When you set up your account, this seed is sent to you (for example using a QR code) and imported into the authenticator app you are using.
As long as the date and time on your device is accurate to within 30 or 60 seconds, and the seed was imported correctly, the app will generate login codes that match the ones calculated on the server.
Even if crooks record your last 10, 50 or 10,000 passwords, there’s no way to reconstruct the sequence and work out what comes next unless they get hold of the seed.
There are many implementations of this type of service but Google Authenticator is probably one of the best known versions.
Advantages and disadvantages
+ Doesn’t rely on an SMS every time you login – you only need to be online when you set up an account so you can receive the seed.
+ One authenticator app can work for multiple accounts.
- If a crook gets hold of the seed (either from your device or by hacking into the server), he can calculate any future login codes.
- If you are logging in and running the authenticator app on the same device, your authenticator codes are as much at risk as your password.
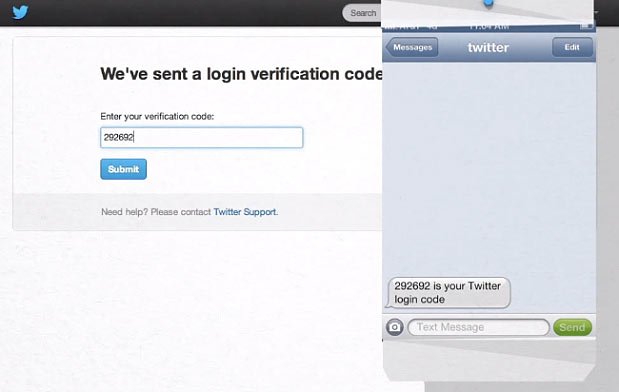
Login verification
Login verification is another variation on the above themes.
Now, instead of being asked to enter a code, a login notification will be sent to your mobile device. Once this has been approved you will be signed into the site.
This process doesn’t use a secret key, or seed, that has to be shared between your device and the server.
Instead, it uses public-key cryptography to verify your identity.
A private key is generated and kept in the app on your device. The public key is sent to the server and stored there for your future logins.
At login, a challenge will be generated by the site and a notification will be sent to your device.
If approved, your device will sign the challenge, send it back to the site to be validated (because only your device should be able to sign the challenge with your private key), and login will proceed in your browser.
For example Twitter implemented this type of system last year
Advantages and disadvantages
+ Doesn’t rely on an SMS every time you login.
+ One login verification app can works for multiple accounts.
- If a crook gets hold of your private key, he can masquerade as you.
- If you are logging in and running the verification app on the same device, your private key is as much at risk as your password.
True two-factor authentication
Earlier, we talked about 2FA and 2SV.
They are nearly the same, but note that the name 2SV carefully avoids stating that there are two separate factors in the system.
A proper “two factor” system, as the name suggests, needs two distinct authentication factors, not merely two steps.
So a web-based account that boosts security with one-time SMS codes is no longer strictly “two factor” if you run your browser and receive the SMS on the same computer or mobile device.
For something to be considered a true 2FA system, it needs two components that operate independently and avoid a common point of compromis
Common implementations of this are smart cards, login tokens such as the RSA SecurID, and Yubikeys.
Smartcards require a special reader to communicate with the chip on the card, but that chip acts as a tiny standalone computer with its own CPU, secure memory and cryptographic capability.
Yubikeys have their own cryptographic CPU, but communicate over USB by pretending to be a keyboard. When you plug in a Yubikey, it effectively “types in” a one-time login code that was calculated inside the key.
Tokens also have their own independent CPU, and generally don’t connect to your computer at all. Instead, they have a tiny LCD screen that displays your current login code.
Advantages and disadvantages
+ Doesn’t rely on SMS.
+ Doesn’t need a phone or tablet.
+ Is an independent security device that is always separate from your computer, phone or tablet.
- You may end up with a keyring full of tokens, one for each account.
- May not be available from the service provider for free.
Now, consider the different methods of talk about how reliable two-factor authentication.
That's a good question. 2FA is not impenetrable to intruders, but it seriously complicates their lives.
"Using 2FA you exclude a large enough category of attacks", - said Jim Fenton , director of security OneID. "To crack the two-factor authentication "bad guys" will steal your fingerprints or access to cookie-files or codes generated by the token".
The latter can be achieved, for example, by means of phishing or malicious software. There is another unusual way: access to the account of journalist Wired (Matt Honnan) attackers gained with the account recovery feature.
Account Recovery acts as a tool to circumvent two-factor authentication. Fenton, after the story of Matt personally created an account with Google, activated 2FA and pretended to be "lost" data entry.
"Account recovery took some time, but three days later I received a letter that 2FA has been disabled" - Fenton said. However, this problem has a solution. At least they are working on them.
However, there is an interesting point. It should be borne in mind that two-factor authentication for the authentication process adds an extra step, and, depending on the implementation, this may cause some difficulty with input (or call them), and serious problems.
For the most part, associated with this, depends on patience and the desire to improve the security of your account. Fenton made the following observation:
"2FA is a good thing but it can complicate the lives of users. Because it makes sense to introduce it only for those cases when the input is from an unknown device. "
Two-factor authentication is not a panacea, but it helps to significantly improve the security of your account with minimal effort. The complication of life of hackers - it is always good to use because 2FA is possible and necessary.
I think, adding the ability of using 2FA is very important for STEEMIT, this will help avoid many problems in the future and users will not worry about the safety of their funds.
Thanks for your attention, share your opinion in comments


Good thanks
cool information! good job!
I don't think Steem needs this. Steemit already has multisig and 2FA only handles authorization. It would be better if Steemit made it easier to backup encrypted private keys or encrypted passwords on some distributed storage medium such as Storj.
But there probably wouldn't be much to gain from 2FA. Can you convince me why 2FA would do anything when multisig already exists?
Because once the keys are generated and stored on the user side, and likelihood of their compromising is much higher than the one-time code generated repeatedly by a certain algorithm.
I think that for secure all means are good, and service need provide users ability to use all of them, for example, in realization one project we using digital pin+ master password, two-factor authentication and multisig, and it really safe
Not only me raised the issue, it is therefore relevant
https://steemit.com/steemit/@blakemiles84/steemit-needs-two-factor-authentication
https://steemit.com/proposals/@thebatchman/supposedly-hacked-accounts-on-steemit-time-for-a-new-proposal#@mixa/re-thebatchman-supposedly-hacked-accounts-on-steemit-time-for-a-new-proposal-20160714t160009976z
I don't think it is necessary to have 2FA, it slows down the adoption.
slows down for 5 seconds, which are required to enter a code? that's funny))
let it remain as is, while cases of hacker attacks will only increase
Fully agree with you @on0tole.
"slows down the adoption" sounds like a joke
Do not make it mandatory. Leave as free option, as most sites do.
Someone who has nothing to loose - will not use.
Others will do
I need 2FA . Need badly. Please give it to us
Very deep and good research! Useful
Онотоле, а перевод будет?
comment pruned due to size
Google translate looks terrible
Если нужно, могу потом просто сделать на русском пост, но пока есть более приоритетные вещи именно для перевода на русский, те же ключи например
Megapost!
my hands up because I tend to agree.
I'm all for security, but have you read this post yet?
Hello.
Check out my guide for integrating LastPass with a free Duo account to secure your Steemit Account password: https://steemit.com/steemit/@robrigo/security-how-to-how-anyone-can-avoid-losing-access-to-their-steemit-account-with-lastpass-and-duo