7 Methods to Fight Back Against Ransomware
Ransomware is a specific type of attack which involves malware that encrypts files and extorts money from victims. It is quickly becoming a favorite among cyber criminals because it is easy to develop, simple to execute, and does a very good job at compelling users to pay in order to regain access to their precious files or systems. Almost anyone and every business is a potential victim. More importantly, to the delight of extortionists, people are paying.
Ransomware can manifest in several ways. In its most benign form, it can lock an Internet browsing session with intimidating warnings of government surveillance and demands of immediate payment. These rely on fear tactics and deny the user the ability to easily navigate away from the warning page, thus appearing their system is locked. The problem can be solved by simply closing the browser application and restarting. This is how many of the original ransomware schemes began but did not result in much financial gain for criminals.
The use of encryption by attackers, to lock selected user files, is now the most common approach. Attackers either compromise the system via exploitation or simply by social-engineering the user into launching malicious software. Either way, once running on the target system, malware then seeks out specific file types and encrypts them with a public PKI key. The user is then notified that their precious files are encrypted and they must pay in order to receive the associated private key for the unlock process to work. Users are directed to send cryptocurrency to anonymous accounts. This practice has proven very successful as the encryption strength is exceptionally strong and the targeted files are meaningful to victims.
The third type of ransomware also leverages encryption, but targets the core operating system (OS) files, effectively holding the entire boot sequence hostage. This is done by encrypting the Master Boot Record (MBR) and deleting shadow copies (a feature in Windows) and other system recovery capabilities.
Overall, ransomware is a relatively new method of attack which traditional security controls are not mature in defeating. Attack methods include phishing, maliciously configured websites and online-ads, Trojans embedded in downloads, device compromise, and poisoned email attachments. It represents a shift in tactics from more traditional data breach exfiltration and website Distributed Denial-of-Service (DDoS) attacks. Ransomware undermines the integrity of specific files and systems, rendering them under control of the adversary, rather than jeopardize the confidentiality or general availability of environments. This change is troublesome for the current generation of security tools and practices, which are struggling to adapt to the new paradigm.
Industry Forecast
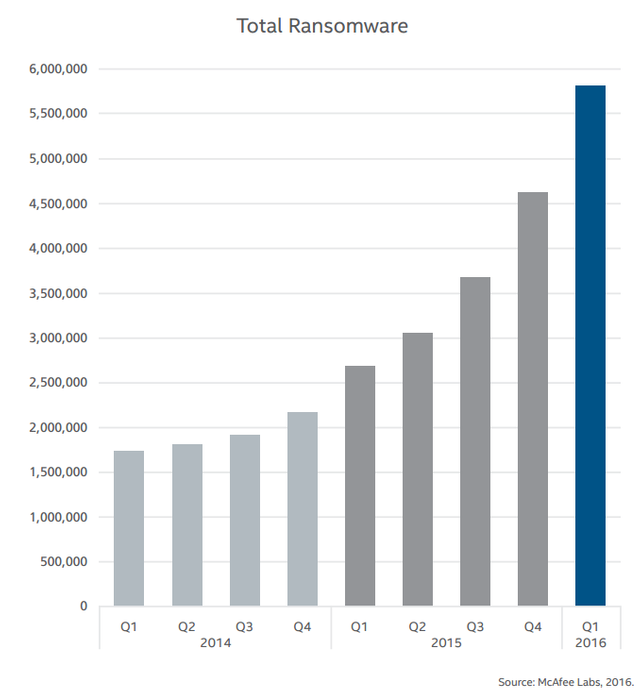
Ransomware, as a type of cyber attack, has risen dramatically over the past couple of years. The Intel Security McAfee Labs Threats Report March 2016 shows over 6 million unique samples of ransomware in the wild. Industry experts believe ransomware will remain a major and rapidly growing threat in 2016 and beyond. The financially motivated threat-agents are relishing in their great triumphs with this approach and significant sums of money are being made. Research by the Cyber Threat Alliance showed one variant in 2015, CryptoWall3, caused an estimated $325 million in damages. Success is reinforcing the incentives and fueling technical advancements, attracting more attackers, strengthening the support infrastructures, and enhancing targeting techniques.
Cybercriminals, large and small, are fully embracing ransomware. Attackers canvas broad audiences with indirect campaigns, indiscriminately seeking easy targets of opportunity. Floods of phishing emails, malicious ads which lead to infected sites, and Trojans embedded in applications will happily infect the unsuspecting. A wide range of common file types are encrypted and a relatively low ransom is set to make the option of paying more attractive. Separately, some threat agents apply direct targeting techniques which single out specific victims. They may do more customized and elaborate phishing campaigns, waterhole attacks, or directly exploit system vulnerabilities to compromise individual hosts. Attackers can target victims through the use of exploit kits, such as Angler, Magnitude and Nuclear, to deliver ransomware payloads like CryptXXX and Locky. This allows ransomware to run, target files most valued by that particular victim, and establish a higher ransom equitable to the situation.
Technically, the encryption algorithms and implementation techniques have become stronger. Early variants were easily undermined by security professionals due to poor implementations, but nowadays most ransomware code is at a level which cannot be broken by anti-cryptographic methods or by identifying weaknesses in key management. Ransomware developers are also bundling their code with more features and capabilities. Advanced malware can look to see if it is in a security sandbox, establish secure connections back to command and control infrastructures, use unique Public Key Infrastructure (PKI) key pairs for each victim, combine multiple infection techniques, establish backdoors for later use, and destroy the system if attempts are made to evict the code. Attackers are creative and will maximize every opportunity. For example, the Petya ransomware was recently updated to include Mischa code. Petya attempts to encrypt the MBR but if it fails, then it reverts to using Mischa as a file encrypting scheme. Threats also mix ransomware with botnets to amplify the reach to victims. The Dridex botnet is well known to spread Locky and Cerber ransomware.
For the foreseeable future, ransomware will remain a major and rapidly growing threat, fueled by anonymizing networks and payment methods. The business models and infrastructure underpinning ransomware are becoming stronger. Most of these attacks continue to use the bitcoin cryptocurrency to anonymously transfer funds from victims to the criminals. Popular anonymous networks, such as The Onion Router (TOR), are used to mask the location and owners of command and control servers. With so much money at stake, attackers realize they are getting a lot of attention from law enforcement agencies, and they work very hard at remaining in the shadows. Other advances include less-than-scrupulous developers who offer the software and hosting services to upstart criminals seeking to enter into the ransomware arena. Ransomware-as-a-Service is now a real business opportunity. Anyone can purchase or rent such a service and the infrastructure host will handle all the back-end procedures in return for a slice of the profits. This allows for specialization and the recruitment of less technical fraudsters to join in the activities.
At its core, ransomware is about extorting money. Criminals tend to go where money can be made and cybercrime is no exception. Although targeting everyday consumers who blunder into their traps will continue, the more sophisticated threats are targeting industries which must maintain access to crucial data and are willing to pay larger sums. So far in 2016, the healthcare sector is one of several which has been aggressively targeted. Medical facilities need access to systems, care devices, and most importantly patient records. Several hospitals have been specifically targeted with ransomware causing a disruption to services. Transportation, financial, and legal sectors are other fields which share the same profile and are being pursued as well. New technology will also be victimized. As consumers and businesses rely on new devices and services, it creates an opportunity for this type of extortion. Imagine getting into your smart-car to drive home and seeing a ransomware screen appear. With vehicle operations blocked, you are now effectively stranded. How many people would pay a small ‘fee’ to get their car started?
Security Industry Advice to Fight Ransomware
Ransomware is very challenging and technical solutions must support the security priorities, end-user needs, and intertwined processes which provide protection. No one solution or practice can solve the problem. The development of tactics and tools by the criminals is extremely fast to target and victimize users. The ransomware development community is very agile in countering defenses introduced by security vendors. It is a highly dynamic situation where attackers are rushing and maneuvering to maximize financial returns. They will look for easy victims, targets with value, and even work to exploit new technologies in order to keep the money flowing in their direction.
The best situation is to prevent ransomware before it can arrive on your system or block an attacker’s compromising attempts to gain access. The next best opportunity is to detect the malware and rapidly evict it before it can do damage. Downloading malware happens before it is launched, which provides a narrow window of opportunity to contain the threat, if it can be detected in time. However, detection is an area where adaptive attackers are successful at creating problems for security. Whether it is detecting an intruder to your network or trying to verify a file is malicious, it is a difficult endeavor.
After that, the situation gets grim quickly. Limited options exists when responding to ransomware after it has compromised the integrity of files. Most ransomware infections encrypt files in a way not recoverable without the private key, being held by the extortionist. Even if the victim pays the ransom, there is no guarantee they will get their files back, as they are dealing with less than trustworthy parties.
Recovery from ransomware is always painful, can be expensive, and is time consuming. If backups are available, then the best option is to remove the infected media and start fresh. Reuse of infected drives is not recommended for any severe malware infection as it is near impossible to know if everything is safe. It is better for everyone, especially businesses, to start with a new drive, a fresh OS install, and restore uninfected data files. For consumers, this may not be reasonable due to cost or technical challenges, resulting in a decision to attempt the cleaning and reuse of the infected drive.
Many choose to simply do without the encrypted files. They may not have been that important, could be recreated, or the victim just choose to suffer and learn from the experience. Paying the ransom is not recommended by security professionals. Regardless of cooperation with the extortionists, in the end, there is a risk the files may never be decrypted. What is certain, is the victim will be recognized as someone who is willing to pay. That makes them a preferred target in the future.
Best Practices to Protect from Ransomware
The following recommendations represent the basic controls which provide a good measure of protection against ransomware. However, as the threats constantly evolve, so must the defenses we present. Industry recommendations will change over time, evolving to align with the threats.
Ransomware attacks are a highly visible problem and growing global threat to businesses, governments, and consumers. The problem is not going away. Security and technology vendors are working to find ways to undermine this new tactic by cyber criminals, but it is difficult. Businesses and consumers should proactively take steps to minimize the risks and impacts. Those who don’t are likely to feel the sting of future ransomware attacks.
Interested in more? Follow me on Twitter (@Matt_Rosenquist) and LinkedIn to hear insights and what is going on in cybersecurity.


A friend recently had his house burn down. All of his backups were destroyed.
I now have an offsite backup as well as onsite. Just in case.
Having a back up should be first. That is the one thing that can save you from just about everything.
Backups, preferably offline, are the best option but also the most inconvenient. Security is a balance everyone must choose. I recommend regular backups of critical data + keeping up-to-date security on my system + making good choices when clicking links and opening files. That is my balance. To each their own.
Hard drives are cheap and you can get a hot swap drive bay for about $15. Easy to do a full image. 2+ spares for backups make it even more secure just rotate them.
I like the way you think! But most people are not that technically savvy, nor do they want to manage the grunt-work of dealing with a bunch of drives. The problem is compounded if you have multiple systems or are using devices like tablets and smartphones.
Well my method is even more complicated. I have a server and image everything to a raid set there then do a backup of the server to hot swap drives. I also keep all the important stuff on either the server or my NAS and back those up too. Only take 11tb to back up each month.
I think sandbox deployment is very secure. You can observe the effect of running a program before running on your device. However, it will be time-consuming if you run every programs in sandbox. Everything needs a trade-off.
Modern security software can handle a lot of this work in the background. It usually cost money for the most advanced version and then there is a system-performance overhead which can slow things down. It does reduce the risks, but does not eliminate it. Threats are evolving as well. Some are coding delays to trick sandboxes, others are trying to detect when they are put into such confined spaces so they can remain dormant, while the most advanced attackers are actually finding ways of breaking out of those sandboxes! Personally, I think sandboxes can be one of the best controls, but the battle continues to wage between security and threats.