Stay Safe - MyEtherWallet "DNS Hack" and BatchOverflow exploit
Hey Steemians! There were a couple of security news in the past week that I think all people in the cryptocurrencies market should be aware. First the "DNS Hack" involving MyEtherWallet, a very popular Ethereum web wallet used by many. Next, the BatchOverflow exploit involving Ethereum smart contracts.

MyEtherWallet "DNS Hack"
The first piece of news is the hack on MyEtherWallet (MEW). Why did I put those quotes on "DNS Hack"? Reason is that it is not really a DNS hack, it is more of the attackers exploiting a BGP misconfiguration. Also, MEW wasn't really hacked, rather users were being redirected to a fake site and got phished.
Through a BGP misconfiguration across multiple parties, some users were routed to a fake MEW site. Of which they provided their private keys and lost the funds stored in that address. The write-up by CloudFlare is by far the best one I have read. If you are really keen to learn what exactly happened, I recommend you to read the article. But in summary, this is roughly what happened and a total of 216 Ethers were reportedly stolen due to this hack.
The attackers used BGP — a key protocol used for routing internet traffic around the world — to reroute traffic to Amazon’s Route 53 service, the largest commercial cloud provider who count major websites such as Twitter.com as customers. They re-routed DNS traffic using a man in the middle attack using a server at Equinix in Chicago. From there, they served traffic for over two hours.
This is a rather odd case of hack where no single party is to be blamed. The BGP protocol is an old protocol which is ran in a somehow decentralized manner. There is no central party to make sure all the routes are correct and it is the responsibility of individual ISPs to make sure that the routes they are broadcasting are correct and legitimate. In this case, as Cloudflare had pointed out, there are multiple parties that are somehow responsible,
The ISP that announced a subnet it did not own.
The transit providers that did not check the announcement before relaying it.
The ISPs that accepted the route.
The lack of protection on the DNS resolvers and authority.
The phishing website hosted on providers in Russia.
The website that did not enforce legitimate TLS certificates.
The user that clicked continue even though the TLS certificate was invalid.
Ultimately, I think the onus is always on the user to detect if there is anything fishy about the website when sending sensitive information to the website. The MEW site is using an Extended Validation SSL (EV SSL) certificate which will appear as a fully named SSL green bar as such,
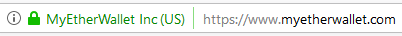
If you compare to what Steemit is using, you can tell the difference,
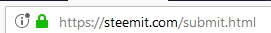
Having EV SSL proves the legal entity controlling the website or software package. Obtaining an EV certificate requires additional verification of the requesting entity's identity by a certificate authority (CA). Users of MEW should pay extra attention to such details as it is ultimately the users' money that are at stake.
BatchOverflow exploit
Next, the BatchOverflow vulnerability which was discovered by PeckShield and described in this article. The BatchOverflow vulnerability is a coding bug which involves the classic integer overflow issue. In most modern programming languages, such overflow issues are rare, as the language itself will take care of it. But in Ethereum smart contracts programming (Solidity), developers have to be mindful of it. Developers have to make sure they use the SafeMath library as much as possible and also implement checks the right way.
This bug led to trillions of ERC-20 tokens being created out of thin air which is likely to devalue the affected token greatly. This article lists out some of the known affected tokens:

With the discovery of this bug, I will like to highlight the importance of developing smart contracts right the first time. Smart contracts are immutable after deployment. That's why it is so important to get security right the first time. If all projects take security seriously and go through some kind of audit before deploying their smart contracts, there will be less problems.
Thanks for reading! What are your thoughts on all these security incidents that have happened in the past week?

As always, lit article brother.
Use Metamask or a hardwarewallet - these were safe, apparently; even "during the hack".
And I have heard that this Mew url only was "http" and not "https" but people did not "mind" haha.
Btw. I really do not like the situation of eth. This 'possible hardfork' definitely should not happen - I think it is called EIP 999 or something like that, not sure. But this is just not good for eth.
In regards to the batchoverflow exploit: Simply awful, negligent... Security is so essential (especially in crypto).
Cheers!
Thanks bro! Yea the EIP 999 is possible but it is still in discussion now.
Wow! It is so scary man. It is a relief that I did not invest anything on Ethereum but one must be on guard at all times and invest what you can afford to lose. :) Upvoted!
Yes my friend. Unfortunately, there are still a lot of work that needs to be done to ensure cryptocurrencies are properly secured.
To listen to the audio version of this article click on the play image.

Brought to you by @tts. If you find it useful please consider upvote this reply.