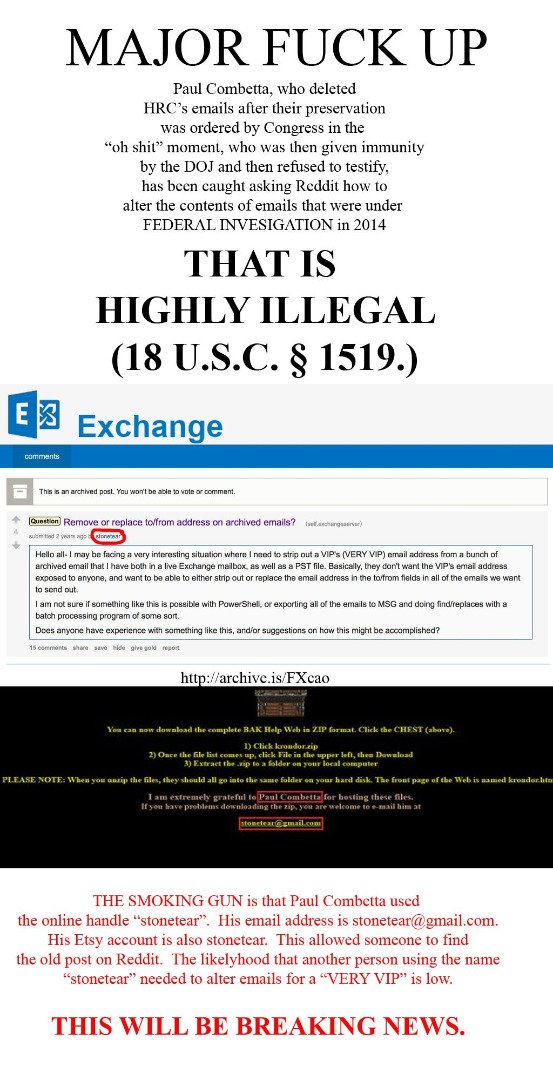
Paul Combetta: How It Should Have Ended
(With apologies to How It Should Have Ended)
Paul Combetta's actions as Hillary Clinton's IT wonk will become the staple of IT ethics training.
Having been in similar situations, I imagine that this is how things went down:
Combetta got the order to delete emails. He didn't do it. He probably intended to get around to it eventually.
Many times, when IT gets deletion orders we check if we need the drive space. If not, the order goes to the bottom of our stacks.
We get to deletions "if and when." There are always bigger issues to deal with. Exchange can be a particular pain in the ass.
In any case, users never complain when you don't delete their stuff.
Then the court sent down the order to hold the emails. Combetta got an order to retrieve and archive what was there.
At that point, he had a legitimate, "Oh, shit!" moment. His blood literally ran cold.
All the emails they'd wanted him to delete were still there.
It was immediately -- and terrifyingly -- obvious why they wanted them deleted months before. They knew this was coming and wanted to erase incriminating information.
Ethically, the situation seems straightforward. You have a court order. You turn over the emails, or you're violating the law. Simple.
Except that these are the emails of the most powerful woman on the planet.
Let me be clear: I'm not a conspiracy theorist. I generally believe that only the mob can carry off murders and get away with it. They do something that the government has a hard time doing: summarily executing rats.
However, the Clintons have run roughshod over the American -- and global -- political system for most of my adult life. Hillary has amassed power that probably exceeds that of the President in some areas.
(Were she not obsessively power-mad, Hillary might understand that it's better to be the puppet-master.)
Were I suddenly in possession of this data, I might fear for my life. At the very least, my personal and professional lives could be destroyed in any number of ways.
Imagine it: by mistake, you find yourself custodian of gigabytes of data that implicate the most powerful woman on the planet. Its exposure has global political ramifications. Exposing it means exposing yourself. There is absolutely no question that if you expose it, your name will be dragged through the mud of the international press.
You're sitting there, alone in front of your keyboard, your blood cold and your heart pounding. Your mind is racing.
Nobody knows this but you. What do you do?
Honestly, think about it:
What do you do?
Do you delete the emails the way the most powerful woman on the planet wants -- thus avoiding the mess?
Do you turn them over, watch her take a beating, and in the process take a beating yourself?
Do you take the chance that you'll live to see her trial?
Do you take the chance that she'll even go to trial?
I know one thing: I'd've not gone on Reddit looking for accomplices.
(That's how I know I didn't train Combetta. He'd've known how to find the info himself.)
The thing is -- and I'm sorry to tell non-sysadmins this, but it's true:
Sysadmins own you.
More specifically, we own your data. More and more, data is what defines you and your ability to interact with the world. With the right equipment in the right places, we can see all of it. We can see everything you've ever typed, every IM to every lover, every bad breakup, every text message.
We can see it all.
We own your data. If we like, we can own you.
Laws, policies, and procedures are in place to limit this. They are successful -- to an extent. At the end of the day, however, some human being(s) has access to your data. In order to do their job, they must have access.
As a rule, we don't use this to our advantage. We are possessed of personalities more comfortable with machines than humans. We tend to think of IT systems as "our babies" and are highly protective of them. As a sysadmin, the most difficult part of leaving a job is losing touch with the system(s) you've been babying for years.
As one of my college professors put it, "We all want the newest, biggest, fastest, sexiest machines we can lay our hands on."
All that stuff you see in Mr. Robot? It's not far off the mark -- except that in real life, it's neither as difficult nor stressful.
We can own you. We just don't care enough to bother (most of the time). Working with our machines is infinitely more fascinating than the petty details of your existence.
On a practical level, keeping one's prying eyes out of the data is simply smart. What you don't know can't be used against you in a court of law.
Imagine that Combetta had deleted the emails when directed in December. All he'd be able to say in the hearings was:
"Senator, in December I received an email deletion request. It came from a source within my employer's company who had administrative authority to make such a request. Per company policy, I deleted the emails as requested."
In terms of ethics, IT people are drilled early and often:

When you get into the political arena, you enter a whole new ball game. Here, all the big-name players make you feel weird. You keep as silent as possible around them. If they shake your hand, it never seems genuine.
It's all very, very creepy.
If you're a sysadmin for any public figure, it's important that you recognize the truth:
You are their unknown, unseen owner.
Learn to embrace it, because it's true.
Most sysadmins have a hard time acknowledging this to themselves. We're really not comfortable wielding that kind of power. Combetta certainly wasn't -- to his ultimate demise.
Unknown to both, Combetta owned Hillary. While Hillary believed herself the most powerful woman on the planet, Combetta could own her any time he liked.
How should this have ended so the sysadmin didn't wind up as the fall guy for the entire mess?
How It Should Have Started was with Combetta's internal acknowledgement that he owned Hillary.
How It Should Have Ended: Political Thriller Edition
If Combetta wasn't ethical and if he didn't mind living in that rather horrifying world, he owns Hillary. It's as simple as that.
He immediately made multuple copies of the Exchange database and squirreled them all over the Internet. Anyplace offering a free shell account got copies. Any misconfigured FTP or HTTP server got copies. Any home router/NAS device infected with Dyre got copies.
He put them everywhere .
He then demanded a meeting with Hillary and got one. He rather got their attention when he said that he was in possession of evidence implicating Hillary in multiple Federal crimes; several of which carry the death penalty.
At the meeting, Combetta explained the situation. Hillary screamed her lungs out. She showered him with threats. Combetta remained resolute:
Give him a nice, cushy Cabinet position after Hillary is elected, or Combetta rats her out.
And if she ever double-crosses him, he rats her out.
Oh, and FYI: there are cronjobs out there that require Combetta to send a manual "heartbeat" signal. If he doesn't, emails with links to the Exchange database are sent to every member of the press that Google can scrape.
That includes the foreign press.
Hillary caved. Combetta could be Secretary of IT, whatever. As long as she doesn't have to see him except to nod.
How It Should Have Ended: Mr. Robot Edition
If Combetta were ethical -- and possessed the appropriate amount of paranoia regarding his employers -- then we must first look to ...
How It Should Have Started
A few years ago, Combetta discovered he'd be working for Hillary.
Combetta's not stupid. Everyone knows that Hillary Clinton is dirty. She's really dirty. Hillary Clinton is the most corrupt politician to ever run for the Presidency. Even Richard Nixon comes in a distant second.
Because of this, the discovery of Hillary's nefarious schemes is a legitimate and ongoing business risk.
When you have a legitimate business risk, you don't ignore it. You plan for it and hope that it never happens.
Because of the risk, Combetta did a lot of groundwork. Specifically:
He set up multiple fake identities. He obtained forged (or forged his own) foreign passports with entirely bogus names on them.
He simultaneously opened off-shore bank accounts in those names.
He then liquidated most of what he owned (homes, expensive cars, etc). Most he converted to US Dollars held at a variety of randomly-chosen domestic banks. A few thousand dollars were converted to physical gold and silver; and a variety of South American currencies.
Unobtrusively, Combetta began keeping a sledgehammer, a gasoline can, and a bug-out bag in his car.
How It Should Have Ended
When Hillary was discovered, Combetta was in the position to make only ethical choice available:
Dump the data and bug out.
In so doing, he would instantly make enemies of both the most powerful woman in the world and the US Federal Government. By extension, he would make enemies of most of the Governments on the planet.
When the day came, Combetta checked his "bug-out bag" to make sure it was stocked. He made sure his passports, gold, and currencies were unobtrusively wrapped in his towel.

These were all kept in the shielded false bottom of Combetta's bug-out bag. He had tested it twice: once domestically as checked baggage and once internationally as a carry-on. Turning the bag on its side made the false bottom and contents completely invisible to the x-ray machine. On the domestic flight, TSA had searched it. They'd stolen the $100 in cash he'd intentionally planted, but the false bottom went undetected. Similarly, US Customs had done a thorough search and found nothing.
Combetta turned on his TV, setting the volume low, then turned out the lights. When they came to ransack his home, he wanted them to be worried that someone was there. It would simultaneously spook them and make them hope for a fast collar.
It wasn't much, but it would slow them down a little. From here on out, the clock was ticking.
Not bothering to do anything else, Combetta grabbed his bug-out and laptop bags and left forever.
Combetta drove aimlessly until 2am. He then made his way to an Urgent Care facility he'd once visited. He'd clocked the guest network's speed at over 100Mb/sec -- during business hours. They'd never notice his traffic.
Combetta parked, connected to the network, and logged-in to his various bank accounts. He transferred money from his US accounts to all but one of his fake IDs. He then transferred the money between them several times. It might not stop them from figuring out where the money went, but it would slow them down.
He logged-off and then got into Hillary's Exchange server. Combetta copied the entire Exchange database without looking at its contents.
He created a torrent out of the raw data. It was totally uncompressed and unencrypted. Any competent sysadmin would be able to load it.
It was entirely unredacted. It would destroy Hillary and everyone connected with her. It would expose corruption at every level of government. It would expose secrets considered vital to national security.
He logged-into AWS GovCloud and fired up his bittorrent server instance. He double-checked that the server was set to capture no snapshots and that there were no prior backups of it.
Combetta logged-in to the server just long enough to copy the torrent and enable two functions :
On a controlled boot or shutdown, the server would write binary zeros to the instance disks.
This is particularly useful in AWS. Such a task would occur during the boot or shutdown cycle. During this time, the server's console is completely unavailable -- even to AWS. They'd assume the server was taking an unusually long time to boot or shut down and force a restart. By that point, the server would never boot again.
Using a shell account on one of the many free services, Combetta enabled a cronjob. It tested the torrent server for a heartbeat. If it found none, it used AWS APIs to terminate the instance and delete its disks.
Left alone, the server would seed for hours - perhaps days! -- before AWS got an order to shut it down.
If it was shut down, the cronjob should terminate any footprints. If not, they'd find that the disks were rendered useless.
They might be able to recover it, but by the time they got everything sorted-out there'd be no point.
Combetta had seen WikiLeaks swarms accumulate hundreds of seeds in only minutes. At that point, nothing could repair the damage.
The fact that it would be run from a server within GovCloud was just twisting the knife.

Combetta drove aimlessly for a couple of hours. When the time seemed right, he parked near the dumpster behind the local Best Buy. He removed the contents of his computer bag.
Using the sledgehammer, Combetta carefully smashed everything to fragments. He took particular care to reduce his phone, SSDs, and thumb drives to gravel.
Combetta carefully collected the remains and placed them in a black garbage bag; this he stowed in the passenger's seat of the car. He tossed the sledgehammer in with it.
Combetta pushed the dumpster away from the building. He placed the backpack between the dumpster and building, soaked it with gasoline, then put the gas can in the passenger's seat.
He set fire to the backpack. Being largely composed of plastics and nylon, it generated hideous black smoke. Combetta pushed the dumpster over the top of the flaming backpack, then drove off -- taking care to obey every speed limit and traffic sign.
He drove into a distant residential neighborhood. He ditched the gas can at the first convenience store. He poured the destroyed contents of his computer bag out the window at random intervals throughout the neighborhood. Combetta ditched the sledgehammer at a home construction site.
He drove to the opposite side of the city, parked his car, grabbed his bug-out bag. and strolled to the nearest bus stop. As directly as possible, he went to the airport. There, he assumed one of his fake IDs and boarded a flight to Panama.
Once in Panama, he used a second fake ID to book passage on a tramp freighter working the South American Pacific Coast. After several months, he booked passage on a long-hauler headed for New Zealand
Along the way, he grew his hair and beard long, changed his glasses, obtained tattoos all over his body (in some of seediest parlors on South American wharfs), and developed an affected limp. Nobody would recognize him without a DNA sample.
In New Zealand, he closed out the foreign account in which his money was stashed.
He then burned all of his belongings save the one passport that had never been used. He scattered the ashes of his former life into the Pacific.
For the rest of his life, he maintained the identity on his last forged passport.
From New Zealand, he took a small tramp freighter to his final destination: a small island in the South Pacific. It was here that he'd spend the rest of his life.
He would never again touch a computing device -- not even a phone nor ebook reader. When questioned, he would display the IT expertise of the most hopeless "Twelve O'Clock Flasher."
(A "Twelve O'Clock Flasher" is a user so inept that all the appliances in their home constantly flash "12:00".)
That's How It Should Have Ended -- for both Edward Snowden and Combetta. It's too late for Snowden, and Combetta never did the appropriate prep work. He'd need to bug-out under his own name, while under scrutiny.
No doubt there's some country without extradition agreements who'd take Combetta. But he really needs to stop kidding himself that he can win this.
Combetta is on Hillary's enemies list. Congress is now pissed-off at him. Public sentiment is against him.
Combetta is in a Kobayashi Maru scenario. We all know that the only way to win is to cheat.
In this case, cheating means getting out of Dodge in the dead of night; and hoping that you have a head start on the posse.
welcome if you are new ; you are follows : )
https://steemit.com/steemit/@crok/college-level-steemit-education-we-simply-must-respect-and-value-others
sending you recognition reward ; )
Congratulations @wrstone! You have received a personal award!
Click on the badge to view your Board of Honor.
Congratulations @wrstone! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Good thoughts