Goldilock - Crypto Key custody and Digital Asset Storage

Source
Introduction
It constantly happens that with each new system that emerges, we must be saving the passwords to access them. The banking systems, the email accounts, blogs, all our private keys of our digital wallets and all kinds of confidential information, are constantly threatened by external (theft) or internal (loss, forgetting, corrupt data, etc) reasons, so we must always look for a way to keep this information safe, secret and at hand.
That is why I have come to present Goldilock as a solution to securely protect our most important digital information, always having it at our fingertips.

Wallets and Cryptocoins
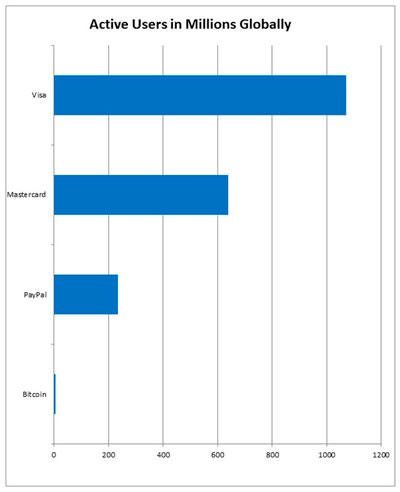
It’s amazing the rise of cryptocurrencies and so far this year (2018), according to Bitinfocharts.com, there are more than 22 million users with digital wallets (4 times more, compared to the amount that existed at the beginning of 2017). Cryptocurrencies have become a new form of fiduciary money, approximately more than 5.8 million users are active exchanging cryptocurrencies, that is, using this type of currency to buy and sell services, items and/or investing in other cryptocurrencies.
However, in developed countries, this is a very low percentage ahead of representing those who use PayPal (over 200 millions), Mastercard (about 600 millions) and Visa (more than 1000 millions). But for underdeveloped countries, cryptocurrencies are becoming a solution whose tendency will revolutionize the world economy, since this type of currency is available to anyone, anywhere in the world, freely without relying on a central entity that controls it.
And there are many ways to obtain cryptocurrencies, mining by yourself, using your own computer or renting a mining service, or simply doing work online to companies who pay with cryptocurrencies (which are increasingly more each day).
The problem may not be getting the cryptocurrencies, but how or where to keep them and this is where digital wallets comes in play.
Digital wallets are the means (software or hardware) that will allow us to save, transfer or receive cryptocurrencies. Digital wallets consist of two elements: a private key and a public key. It is important to know how each element works.
The public key can be viewed as a bank account number. As the word implies, it is public and serves as an address where the cryptocurrencies that we earn or generate can be deposit . Unlike the previous one, the private key is the one that allows us to make transactions with our money, that is, it allows us to transfer or withdraw cryptocurrencies from our wallet. This can be compared to your PIN code that you use to withdraw money from your bank account.
You are already getting how important the private key is. Like your PIN number, you must jealousy keep your private key in a secure place where no one has access to it. Generally these keys are codes of 64 alphanumeric characters (letters and numbers) or 256 bits. I can barely remember my PIN from my bank account which is 4 numbers, imagine remembering 64 characters for each type of cryptocurrency that you keep.
An example of a private key is:

However, generally private keys are transported in a shorter format, using a wallet import format, Base 58, which would make our previous private key look like:
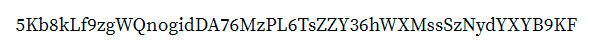
In my opinion, it is even harder to remember.
Type of Wallets
Digital wallets can be hot wallets or cold wallets

The hot wallets
They are those which are constantly connected to the Internet, are easier to use and can be accessed anywhere and anytime. They are responsible for saving and secure your private key, so you never see your private key.
Most of these type of wallets are exchange sites, they allow you to exchange your cryptocurrencies into another kind of cryptocurrencies (investing). Among them are: Blockchain.info, Coinbase, Kraken, Okcoin, etc.
The disadvantage of these kind of wallets is that they are prone to attacks from malicious entities or hackers due to they're always on line 24/7. So, they steal all private keys and consequently all the cryptocurrencies. There have already been many millionaire losses of this type of wallets.
It is generally recommended to keep a minimum amount in them to make operations quickly and easily. So, do not deposit all your cryptocoins in this kind of wallet.

The cold wallets
Unlike the previous ones, they are not connected to the internet. They are more secure since you have control over your private key. They usually encrypt your private key to offer more security. They can come in physical format (hardware) or software (applications).
These include:
Ledger Nano S

Source
Trezor

Source
They also come in a version to be stored on your computer (applications) or on paper. The last one is considered the best way, however, is the slowest.
The problem with these kind of wallets is that they can get lost, damaged or being stolen. So you could lose all your money if you are not careful enough. And at the time of being used, you must carry them with you in order to use them. So, you can put them into a bank vault to keep your money safe but you can't use it. It's a uncomfortable situation.
From what we have already seen, both alternatives have their advantages and disadvantages. And that's why I come to present Goldilock, a system that provides a secure solution to solve these problems and keep your data secured and protected (and obviously your money).


Goldilock
Goldilock is an ecosystem based on blockchain technology that protects private keys (hence cryptocurrencies) and sensitive data of people and institutions through a hybrid system that combines the advantages from hot and cold storages.
Goldilock physically disconnects your sensitive data and your keys from the internet and makes use of a multi-factor authentication to connect your data back to the internet when you need it, no matter where you are. Thus they remain assured, away from the danger of intruders and hacker who live attacking the systems that are online.
Goldilock not only can safeguard your private keys, It can also protect other digital assets such as: personal information, credit data, bank accounts, medical records and more.
How It works?
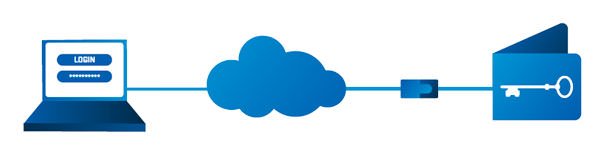
First, your data (keys or passwords) or your sensitive digital information are completely isolated from the internet, through a proprietary mechanism Goldilock called “airgap” (keep it in a hardware device encrypted).

Source
Second, you activate your wallet through an authorization mechanism via telephone that uses techniques to ensure your identity: Two-Factor Authentication, Biometric gateways, Device recognition, Personal generated codes, among others.

Source
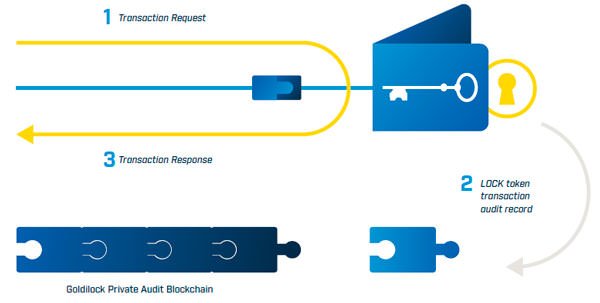
Third, once your identity is confirmed, your wallet is connected to the internet through an encrypted channel and it is kept online for you to do your operations. The transaction or transactions you make with the wallet will be verified with Two-Factor Authentication mechanisms. Each transaction you make is recorded in their own blockchain (Private Audit Blockchain).
Source
Once you finished making your transactions, Goldilock mechanism returns to "separate" or physically disconnect your sensitive data from the internet.

Source
This way, Goldilock offers an innovative hybrid system (patent pending) that takes advantage of the cold and hot schemes of the wallet, ensuring your data and allowing you to access them from anywhere and at any time.
Application Layer
Goldilock Wallet

The Goldilock wallet will be launched during the second quarter of 2018. Initially it will work with NEO, GAS tokens and NEP-5 tokens. Later it will work with other cryptocurrencies.
This wallet will initially come for web version and will work in the same way as explained above, that is, all your sensitive information (private keys), are separated or offline until you reactivate it via telephone. Goldilock will take care of saving your keys in an encrypted way in a unique physical wallet (hardware). This wallet will be accessed via the web through an exclusive personalized url.
Goldilock API Services
Once the wallet is finished, Goldilock will create API services, along with its libraries and documentation so developers or organizations can improve their security using the Goldilock hybrid service and its "airgap" solution (patent pending).
These APIs can also be integrated into dApps (decentralized applications).

NEO Blockchain
Goldilock implements their ecosystem into NEO blockchain for several reasons and in short words is because NEO establishes an "intelligent economy" that combines digital identity, digital assets, and smart contract.
NEO can verify digital identities using the X.509 digital certification standard, verification is done using all types of media, such as: Voice recognition, facial identification, SMS, fingerprints, among others.
NEO uses a more "green" consensus mechanism since it has less energy consumption, since it does not use the PoW (Proof of Work) nor the PoS (Proof of Stake) but has its own mechanism called "Delegated Byzantine Fault Tolerance" (dBFT) where a governance system is defined with delegates who decide by consensus to accept transactions.
Obviously, the previous reason makes the transactions in the NEO blockchain much faster. NEO can perform 10,000 transactions per second no transaction cost. Allowing thus to create safe and efficient transactions.
Another peculiarity of NEO, smart contracts can be programmed using known languages (such as C or javascript), which makes it easier for developers to create them without learning a new language from scratch.
NEO manages two tokens, the NEO and the GAS token.
There are many other advantages of this blockchain technology over other existing ones, however, if you want to know more about NEO you can visit the following link.

LOCK Token
Goldilock will create its own native token called LOCK (NEP-5 asset within NEO), so that users can access the Goldilock wallet. The Goldilock ecosystem will verify that the user has LOCK tokens in their account to give access to the wallet platform; likewise, the LOCK tokens will be used to register audit records of each user’s transaction in the private Goldilock blockchain. These records may be consulted by the user at any time.
Source
The LOCK tokens will be used as payment method to subscribe to the Goldilock Security Suite.

Use Cases
Crypto Exchanges
The companies of cryptocurrency exchange, as I mentioned before, are a solution to have a digital wallet and to exchange cryptocurrencies, however, by being continuously connected are victims of theft due to attacks by hackers and malicious entities. Goldilock represents a solution for this type of companies because private keys will be more secure with the "airgap" mechanism, since they will be isolated from the internet, thus protecting the users' assets.
Your own Vaulted Wallet
One of the most important things that one should do (which I did not know until now) when creating a wallet or having cryptocurrencies is to protect the private key of your wallets. The problem, as we saw, the safest options (cold digital wallets) are susceptible to theft, loss or simply could be damaged. With Goldilock, we would not have that problem, since it would be in charge of protecting not only our private keys of our cryptocurrencies, but also could safeguard and protect another type of information or sensitive data of ours (passwords, credit card information, KYC, etc). Giving us the security of accessing them from anywhere and at any time.
Secure Digital Vault

Goldilock can safely store and physically disconnected from the internet, information such as IDs, all kinds of passwords, bank accounts, KYC information and other private data. The system also allows the user to securely share certain private information if necessary (such as medical records, contracts, etc), this function must be activated with LOCK tokens.
Credit Agencies
It is well known that credit accounts are constantly hacked. Approximately, last year, more than 150 million cardholders have been victims of theft. With the use of Goldilock system, it is avoided that user's credit information, kept by the websites of credit agencies, must be constantly online. In this way, only when necessary, the confidential information is put online for a certain period of time, while the credits are approved.
Banks

Representatives from one of the three largest banks in the United States informed the Goldilock team that they are interested in using Goldilock technology in the interbank transactions process. However, the implementation of Goldilock on banks is still to be discussed during the second half of 2018.
Digital Rights Management

SmartChain Media is a platform that combines audiovisual content (movies, series, short films) and social networks, facilitating interaction between fans and filmmakers. SmartChain Media is currently a GoldiLock customer and takes advantage of Goldilock technology to safeguard the copyrights of distributed content and also controls who is sending and receiving their publications.
Healthcare Records

The objective of Goldilock is to allow health professionals, patients and their families and insurance agents, not only to have secure access to medical records, but also to have the possibility of sharing them in a safe and immutable way among medical personnel, laboratories and administrative and insurance staff. Ensuring in this way that confidential information does not fall into the wrong hands or is stolen or altered.
GDPR Compliance

Governments nowadays are realizing the need to keep the confidential information of citizens safe. Therefore there are governments that are imposing personal data protection laws, with millions in fines for those companies that do not use security systems that protects the information. Such is the case of the European Union's General Data Protection Regulation (GDPR), which imposes fines of up to 20 million euros for not protecting the personal data of consumers. This represents an opportunity for Goldilock, to be able to offer its protection service as standard to companies and technology providers, once they patent their solution.
Voting Machines
Last month the hackers had the opportunity to hack into voting machines at Las Vegas' Defcon convention. Hackers from all over the world took advantage to crack the election system, an activity they achieved in a period of 2 hours, exploiting the weaknesses of the voting machines' operating systems. Link.
It is surprising how vulnerable the systems are, and even more so, a system as important as the election system. That is why it is necessary to use advanced protection systems such as the one offered by Goldilock (patent pending), which makes use of encrypted physical devices to protect confidential information and they can be isolated or keeping them out offline while they are not in use. In this way, it prevents malicious agents or hackers from breaking into the systems and change the fate of a nation.

Conclusion
We have seen that Goldilock is already making a protection system possible, although it's patent pending, which will secure in a extraordinary way our confidential information keeping it at hand anywhere and at any time. This new system uses the best benefits of cold and hot storage, allowing our confidential information (passwords, private keys, accounts, etc.) to be completely isolated from the internet through the "airgap" mechanism and they will be accesible whenever and wherever we need them. A great advantage to keep our digital assets protected.
Not only benefits users or individuals, the Goldilock system can be implemented in financial or exchange organizations, to give more protection to the data they keep online constantly.
Definitely Goldilock will impose a security standard that should be adopted by all types of organizations that handle our most precious information (medical records, KYC, credit information, etc.).

Annexes
My Video presentation
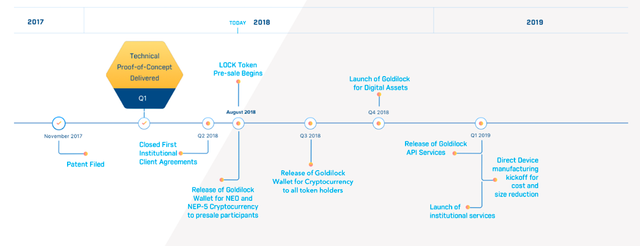
Roadmap
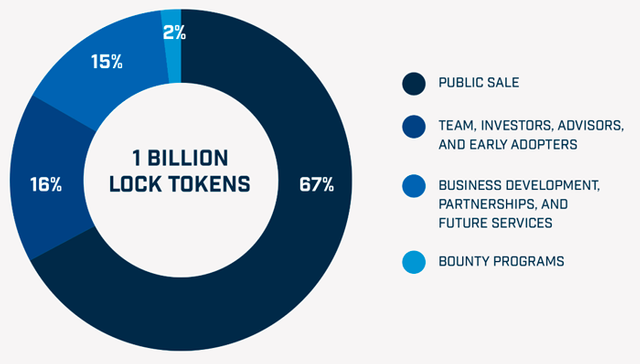
Token Allocation
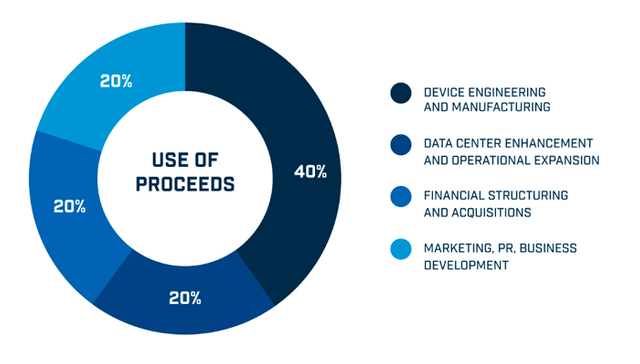
Use of Proceeds
Team


Advisors

Partners

More Information & Resources:
- Goldilock Website
- Goldilock WhitePaper
- Goldilock Tokenomics
- Goldilock Telegram
- Goldilock Discord
- Goldilock Linkedin
- Goldilock Facebook
- Goldilock Twitter
- Goldilock Reddit
- Goldilock Github
My Twitter Link
https://twitter.com/jadams2kx/status/1026983717078745089

If you want to participate in this contest, go to:
https://steemit.com/crypto/@originalworks/810-steem-sponsored-writing-contest-goldilock
goldilock2018


Congratulations! This post has been upvoted from the communal account, @minnowsupport, by jadams2k18 from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
You write well, @jadams2k18!
Thanks Mr. @surikowstepanuk
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Right thoughts you have @jadams2k18, and set them cool
Thanks Mr. igorsamo! It's important to know about private and public keys when we are in a cryptocurrency world. I didnt know about that until I read Goldilock
Security is extremely important nowadays, especially if it comes to the crypto world. How many ICOs have failed because of their troubles with security?
Thank you for sharing awareness with people @jadams2k18 :)
All the best
It's a pleasure to me
Thanks for passing by Mr @crypto.piotr
Interesting project.
I notice that you are writing a bit about the cryptosphere - Maybe you would like to earn some more by becoming a Trivial token analyst?
Basically, I want to create some up-to-date reviews of the more popular tokens, focusing on fundamentals and usage.
To build it out, I am crowdsourcing the initial content, and getting in touch with a few bloggers from Steemit who analyse crypto. I'd be delighted if you considered writing about a token that interests you, and will pay $40 in ETH or STEEM for your time and effort. You'll be free to publish on Steemit as well, so you can also earn whatever post earnings you get.
More details here: https://steemit.com/cryptocurrency/@sroka87/become-a-token-analyst-on-trivial-co-earn-steem-eth