Goldilock - The best option you can have

We all know how important it is to keep our data, passwords, money and, among other things, private files, to have them protected so that we do not have to worry about them, we trust those who are in charge of managing this system of protection, we give you the vote of confidence to take care of these belongings.
So these service providers have to be constantly improving their protection system as technology advances so it becomes more common to use digital files and data, sadly we also see increasing as people we usually describe as hackers are capable of more time to infiltrate security systems and steal our belongings and data that are of utmost importance.
That is why I will speak in this publication of how Goldilock is coming to change the entire digital security system, making it more secure and more trustworthy for us users and so that in this way large companies adopt this type of security system that Goldilock can provide them to create a much safer system.


The problem that we have today is that we do not have a completely secure digital protection system and that it is reliable, this is an inconvenience for the complete adoption in the market of cryptocurrencies.
This is because the technology implemented today has its weaknesses, not even the Blockchain technology is totally safer than any other traditional security method, in both cases there are equally attacks against the digital files found on the network.
Investors and administrators do not have a wide variety of options to take in terms of security, they have to use what is cold storage or hot storage.

Both have many negative aspects, such as in the case of cold storage that have a fairly limited accessibility, which does not fully cover the security needs of the institutions.
In the case of hot storage, it is not the safest way to keep the data and keys protected, being connected to the Internet these files or personal data may be stolen or hacked, and there are already records that this has happened unfortunately.
The crypto keys, documents, financial records and digital identification require a great security, so that Goldilock is here to provide that security, Goldilock is not a hot storage, it is not a cold storage, it is the correct storage, it allows your to stores in cool your private keys and other confidential data in a secure remote location.


Goldilock is a platform created with the purpose of resolving security problems that exist today. Goldilock innovates the way in which data was stored.
This is possible through the construction of an ecosystem capable of protecting cryptocurrencies and all the keys and digital assets of institutions and individuals.
With its innovative secure storage without connection and the convenience of accessing your assets remotely and safely at any time you want, it makes an incredible solution and definitely a big one in the market.

Currently to protect cryptocurrencies or protect your confidential and valuable digital files, both economic and personal, there are several methods used.
As is the case of centralized storage which is a single database in a cluster that provides a central data location but has many deficiencies, which does not make it very reliable.
We also have the personal cold storage, but it presents many problems such as the fact that the files can be stolen, lost, confiscated or pirated in the worst case, this is a method not very known for those who do not handle this method very well or who are very well informed about the technology, what makes the adoption in the market of this is impossible.

Goldilock considers three points of great importance to solve what is the low protection of digital data, which are:
It is necessary that the user can have immediate access when they require it to their personal data, but only a short period of time.
This is because any reserved information or personal data that are constantly in use are easier to be hacked, since being long periods of time online pirate cybernetics can use all the tools at their disposal to get this data.
All personal data such as private keys, medical files, financial records and any kind of documents, must be isolated.
In backups for full backup copies, being thus protected from physical contacts and any human error.
To be able to access all private keys, any private data, either financial records and, among others, digital identification, only when necessary.
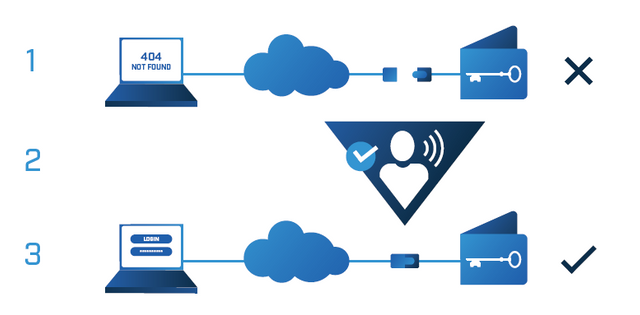

"Goldilock offers a remote physical disconnection of internet data", they take advantage of the following points:
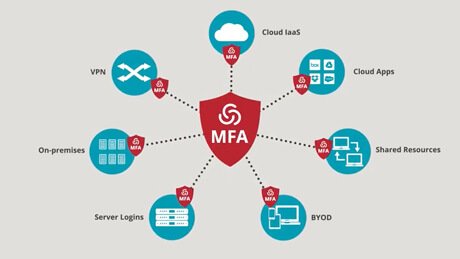
Multifactor Authentication (MFA), this is a security system that needs several authentication methods to verify the legitimacy of a process.
The function of the MFA is to create a solid defense by layers, which makes it an almost impossible income for that person who is not authorized to enter a network or database.

- Biometrics presents a better user experience and greater security. Biometric authentication is a form of security based on the recognition of a physical and non-transferable characteristic of people, as it would be a facial recognition.
Cryptography are the techniques or algorithms which seek to encrypt messages to protect them and make them incomprehensible for those who do not have the authorization to read it.
This is responsible for providing some type of security, which is of the utmost importance since transactions carried out on the Internet can be intercepted.
When reading and analyzing these important points in the operation of Goldilock, we notice how they have made an effort and in charge of creating an impenetrable security method.
Using all this together with the triggers in regressive technology create a compact security system, thus reinforcing and innovating the methods used today.
Each touched point that Goldilock take advantage of, they make us see the good work done, and how they came to revolutionize the protection system at the moment.

To understand all the points hitherto hitherto in a better way, it is important to know which is the backbone of Goldilock.
This is your security system "air gap" which is pending patent, which has the protection offered by this registry.
"Air gap" is responsible for exposing the integrity of a computer system based on the logical and physical separation of any other network. This method is used in order to achieve the security of a computer network so that it is physically isolated from unsafe networks, such as the Internet.
Pending patent in the United States, so that by virtue of the protection it offers, no future company can use it without first having Goldilock's authorization.

Today we see examples of the insecurity that exists in the protection of cryptocurrencies, having already stolen these.
All this due to the low security that some companies implement, which means that data protection is not seen with good eyes.
There is a very important regulation in the European Union that applies to any European company or companies that have business with the European Union, such as the General Data Protection Regulation (GDPR), in order to better protect the data of the consumers.

That's where Goldilock enters the scene, since it offers them a better protection for those companies that do not find a better method of protection and also for those companies that are willing to invest.
Goldilock is the best way to invest because it is cheaper and more reliable than investing in expensive protection systems that do not provide the same solution Goldilock.
In this way people can opt for a massive adoption to the use of cryptocurrencies knowing that their data, keys and their capital are being well protected.


Goldilock offers consumers an encrypted storage device, which is stored in a secure data center. It is beneficial both for consumers and for insurance institutions since it is responsible for protecting files and personal data in the best way.
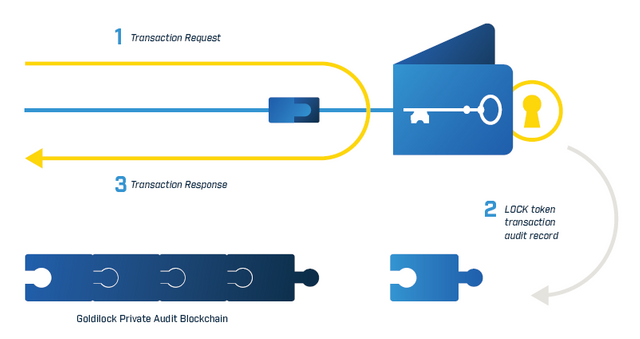
All this is possible because the only way to access the data is through an authorized command without IP that the individual emits through the switched telephone network.
So they can only access through encrypted channels, a great advantage is that it can be accessed almost immediately, and when the client has finished accessing their data, the device responsible for managing the keys and files is physically disconnected from the Internet.

Goldilock offers the same benefits to institutions, such as cryptocurrency operators, that they are offered an on-demand online environment which helps to reduce the processing times of transactions.
This change is very useful because in recent years they have been victims of robberies for up to billions of dollars in cryptocurrencies, this is because they did not find better security methods, but this ends now that Goldilock is here.
It is important to note that Goldilock has no access to keys or stored data, Goldilock aims to be an essential option for those who wish to improve.

It is a Blockchain platform, NEO is the use of blockchain and digital identity to digitize assets.
NEO combines several factors that are fundamental to the premises that lead to the operation of Goldilock, such as:
Digital assets that are programmable assets which are in the form of electronic data.
The digital identity that is the identity of individuals, organizations and other entities.
And the smart contract system which is the most important of the perfect integration of the developer ecosystem.
NEO is different from other intelligent contract platforms, which has attracted Goldilock's attention, and is that NEO offers:
1. Pretend to comply with the regulations.
2. Use a superior consensus mechanism.
3. Process transactions more quickly.
These are the reasons that make NEO the ideal platform for a secure wallet utility token. That goes hand in hand with Goldilock's ideal, which is to achieve better and faster transactions in the chain of blocks.


"Goldilock will register its LOCK token as an NEP-5 asset in the NEO blockchain"
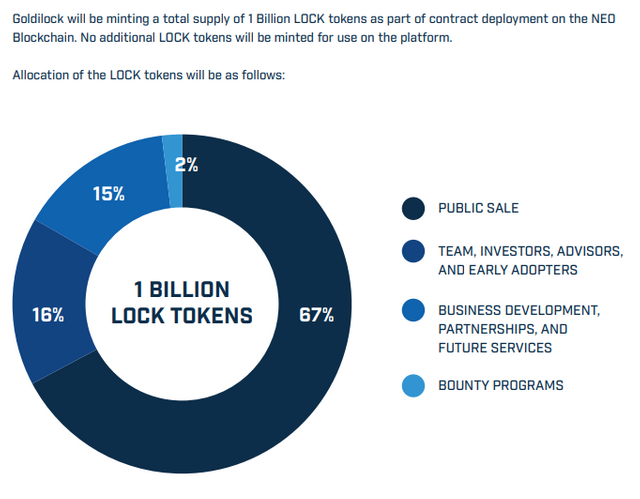
LOCK is very important, because with LOCK it is the only way to access the Goldilock wallet
There are several fundamental aspects of Goldilock's purse as it is that the keys of each purse will be segmented and encrypted disconnected from the internet.
The wallet will connect with a command without IP and a verification by PIN or voice, something of great importance is that when closing our wallet, it will be disconnected from the internet, thus avoiding any attempt of theft by some pirate of the network.
Upon entering the wallet, it performs a public consultation with NEO to confirm that the user has his token, by ensuring that if he possesses the wallet, Goldilock will open immediately.
The LOCK token provides users with their activity record in the nodes.

Personal
Going to the doctor is always tedious due to all the paperwork you need if you go to consultations with different doctors.
Let's suppose that Maria lives constantly traveling from city to city because of the duty of the trade.
Of course we do not want anything to happen to Maria, but in case of a medical emergency she would need to consign all these papers and data in order to be attended or the insurance can cover all the expenses.

With Goldilock this is not necessary, Maria does not have to carry all the paperwork with her, since she can store all these necessary papers with Goldilock.
In this way Maria could be more comfortable and without worries of any medical emergency, because she knows that all her documents are stored safely with Goldilock.
Commercial
There is a cryptocurrency company that has suffered several infiltrations, unfortunately has suffered robberies so their customers have begun to see them with bad eyes and fewer and fewer customers turn to them to protect their assets.
Tired of investing in expensive protection systems that do not give them results, a worker tells the bosses about Goldilock and how it works.
The heads of this company after looking for Goldilock and how they work were fascinated by its operation and its innovation, so they made an agreement to implement their security service.

Almost immediately the company began to notice improvements in its security system achieving the confidence of customers and new customers wanting to give their assets for them to protect them.
So thanks to Goldilock this company managed to climb to the top of security and return to get confidence in the market they had lost and finally get rid of those pirates who constantly stealing information from keys and personal data.

The companies of today will have to be calmer and not worry about possible infiltrations in their security systems or in the theft of data and keys, Goldilock comes to change that with its impressive and innovative security system.
Goldilock gives us a new opportunity to keep all our data more secure due to its large security system fully tested, with many points in favor of the operation, it is definitely a measure that should begin to ally with Goldilock to start implement them
With this the companies that decide to use Goldilock will take a step forward and gain the trust of all users by seeing how we can be calm and leave all our data in the hands of the companies in charge of security, without a doubt an incredible platform that It was necessary for it to reach the market.








- Goldilock Website
- Goldilock WhitePaper
- Goldilock Tokenomics
- Goldilock Telegram
- Goldilock Discord
- Goldilock Linkedin
- Goldilock Facebook
- Goldilock Twitter
- Goldilock Reddit
- Goldilock Github

This contest is offered by @OriginalWorks if you want to participate go to:
https://steemit.com/crypto/@originalworks/810-steem-sponsored-writing-contest-goldilock
Twitter Bonus
Click Heregoldilocktwitter
goldilock2018
This post has received a 3.13 % upvote from @drotto thanks to: @deyvich.
@contestbot
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Interesting project.
I notice that you are writing a bit about the cryptosphere - Maybe you would like to earn some more by becoming a Trivial token analyst?
Basically, I want to create some up-to-date reviews of the more popular tokens, focusing on fundamentals and usage.
To build it out, I am crowdsourcing the initial content, and getting in touch with a few bloggers from Steemit who analyse crypto. I'd be delighted if you considered writing about a token that interests you, and will pay $40 in ETH or STEEM for your time and effort. You'll be free to publish on Steemit as well, so you can also earn whatever post earnings you get.
More details here: https://steemit.com/cryptocurrency/@sroka87/become-a-token-analyst-on-trivial-co-earn-steem-eth