OpenBSD up on the Alps, vmm and Alpine linux
Four days ago...
¡Hello there, dear souls! Days pass rapidly, exactly four days ago we're speaking about add another soldier, who's name was privoxy, in our personal battle with the infamous privacy cannibals, ¿do you remember?
Our new friend, could act like a layer 7 firewall, but in our last article we didn't any firewalling, only we rewrite the Refer HTTP header.
You have to know that some fantastic dudes maintained a public list of hosts that use our personal sensible data with the scope of monetizing it (¿have i give my permission to this abuse?) . The name of the list is easylist and you can navigate to the home site of the project here. Normally is used with browsers extensions to grant ad-free navigation to his users. But we're deep users and we want to use the list in ours privoxy rules. The problem is that this is not so simple. There is a project on the fantastic github that could help us in doing that, but it use a language not installed by default in our OpenBSD, the name of the language is haskell, a standardized, general-purpose purely functional programming language. Here is some links to the project:
Haskell can be installed on OpenBSD but adblock2privoxy want The stack package that i couldn't correctly compile under OpenBSD.
That's the reason why i take my OpenBSD and we go to the up of the Alps to meet with another good friend, another security guy, Alpine linux.
Install Alpine linux under OpenBSD vmm
We're lucky, or the karma is in love with us (we're also in love with you), because a few months ago OpenBSD introduce in his base tree the virtual machine monitor vmm. But karma help us more than this, because it's just very few months that under vmm we can virtualize linux, read here.
Ok, let's start with prepare the correct environment for our new friend:
Download Alpine minimal ISO image, to use in virtual environment, and create a virtual disk of 10GB:
$ wget http://dl-cdn.alpinelinux.org/alpine/v3.7/releases/x86_64/alpine-virt-3.7.0-x86_64.iso
$ vmctl create alpine-virt.img -s 10G
Enable routing in our OpenBSD:
$ doas sysctl net.inet.ip.forwarding=1
# echo "net.inet.ip.forwarding=1" >> /etc/sysctl.conf
Create virtual switch vether0:
# echo "inet 10.1.10.1 255.255.255.0" > /etc/hostname.vether0
# cat > /etc/vm.conf << EOF
switch "local" {
add vether0
up
}
EOF
Enable vmd on boot, enable it and download the virtual BIOS:
$ doas rcctl enable vmd
$ doas rcctl start vmd
$ doas fw_update
Indicate dns service of Tor to listen in the vether0 interface and restart it:
# echo 'DNSPort 10.1.10.1:53 IsolateDestPort' >> /etc/tor/torrc
$ doas rcctl restart tor
Create a dedicated privoxy for our new friend, Alpine:

And prepare pf for the new services opened on vether0:
# cat >> /etc/pf.conf << EOF
pass in on vether0 proto tcp from 10.1.10.2 to 10.1.10.1 port 8812
pass in on vether0 proto udp from 10.1.10.2 to 10.1.10.1 port 53
EOF
$ doas pfctl -f /etc/pf.conf
Notice that we don't NAT connections from Alpine linux vesta, it will only arrive in Internet by the use of our privoxy dedicated instance.
Alpine under OpenBSD, the video
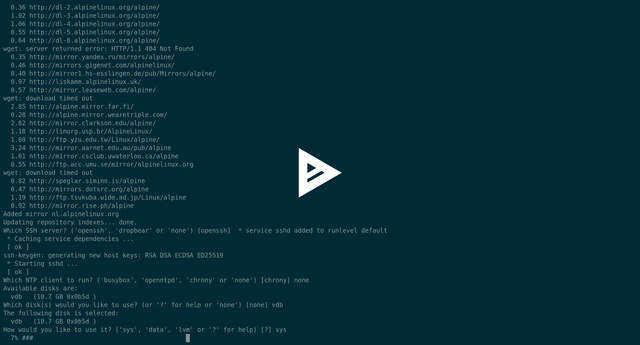
Now, using this guide we are going to install our Alpine under the OpenBSD
...to be continued... and yes I LOVE YOU

This post it's very well written npna thanks for this great tutorial keep going this way I like openbsd too, but i am more focused to FreeBSD since 1993 ;) a mater of taste only, both are BSD derivatives after all. You got my upvote and resteem! am also following you now!
¡Thank you! really appreciate your contribution. ASAP there will be in:
Nince to meet you, and keep in touch.
BSD Rules
I will! my best wishes for you and be pattient here in steemit.com is a resistance race! I have 6 months here in Steemit and i have 1000+ followers it wasn't easy!
@originalwork
@originalworks