SiZ Education|| Modern Cyber Security Requires AI || by faizan222
Hi everyone!
This is my first post in this community.Recently i completed my course thats about webs and modern security thats why i want to share some my knowledge with you and hope so u like this.
Why Modern Cyber Security Requires AI
Cybersecurity has been important considering that even earlier than the age of dial-up Internet whilst viruses unfold thru inflamed floppy discs. The struggle among adversaries and IT specialists is ever escalating. Adversaries create new and distinct forms of malware or assaults, and IT groups installation new or advanced forms of defenses to guard their developing information stockpiles. In the ultra-modern spherical of statistics safety (InfoSec) assaults, adversaries are deploying new forms of threats thru new vectors and improving the ones assaults with the strength of AI. The most effective manner to realistically counter those assaults is to installation the strength of AI in cybersecurity defenses as well.
The cybersecurity risk is constantly developing Attack surfaces are:
In the "antique days," computer systems stood with the aid of using themselves or related to 3 different machines the usage of closed networks. Then got here neighborhood place networks, WAN, and Internet get admission to. Now, 1/2 of the packages are jogging withinside the cloud, and 1/2 of (or perhaps all) the customers are running from domestic and having access to the community with cell devices. This offers attackers many extra capacity access factors to the community with the aid of using first hacking a user’s computer or telecellsmartphone or with the aid of using invading a cloud-primarily based totally software instance. Supply chain assaults pose any other sort of risk wherein software program from a depended on supplier can also comprise embedded malware. Adversaries then use that compromised software or tool as a beachhead to invade the relaxation of the network. Data is developing exponentially, which isn’t news, however now IT is predicted to guard maximum or all of it. In the antique safety model, InfoSec most effective required screening packages and different executable files, together with a record or spreadsheet with macros enabled, to make certain they didn’t deliver malware. That turned into possibly 5% to 10% of the information. But nowadays, even non-executable information desires to be covered in opposition to ransomware and theft — you want to guard 100% of it. Distributed software architectures and hybrid cloud multiply the quantity of conversation required among servers, whilst community speeds have multiplied 2,000X withinside the final 25 years (from 100Mb Ethernet in 1995 to 200Gb Ethernet in 2020). More information is transferring quicker than ever throughout the community. There is exponentially extra information to guard with exponentially extra site visitors to display and examine. Regulatory compliance in addition will increase the InfoSec burden with the aid of using including necessities on what to guard and a way to guard it. Additional information encryption, get admission to controls, privateness protections, authentication methods, and reporting have to be done, relying on which rules have an effect on your agency. Cybersecurity specialists have to now put in force each the protections they deem vital and further protections the regulation calls for and face consequences or disclosure necessities if they are hacked. Adversaries will quickly be the usage of AI to enhance their assault--in the event that they aren’t already. Researchers have already proven how AI can customise phishing assaults to cause them to extra powerful or create “deep-fake” voices that mimic celebrities or sound precisely like your boss. Domain-technology algorithms routinely manufacture new URLs that could unfold malware with out being blacklisted with the aid of using DNS-primarily based totally safety gateways. Botnets already use easy AI standards to are looking for out the maximum inclined machines and paintings round cyber defenses. Newer viruses already regulate their very own code, again and again extrade their location, or even disable or adjust anti-malware software program at the inflamed machines to keep away from detection. These are all examples of fundamental or easy AI getting used to beautify cyber assaults, and it’s secure to anticipate that extra state-of-the-art gadget studying and herbal language processing fashions could be brought to adversaries’ arsenals quickly. To pinnacle off the assignment of the collection risk storm, there may be a excessive scarcity of IT safety specialists. According to a current look at performed beneathneath a US Department of Commerce Grant, there are about 950,000 human beings hired in cybersecurity however over 450,000 unfilled cybersecurity task openings throughout the country. So you can’t lease your manner into safety and compliance.
Why AI is needed
There are 5 regions wherein AI can assist hit upon and save you safety threats as they happen:
1) Screen extra information than humanly possible
The quantity of information that desires to be checked is overwhelming, and it is turning into extra than any person, or maybe group of human beings can moderately display. Human InfoSec research commonly occurs most effective after a breach has been showed or as a minimum suspected. When threats had been extra limited, some human beings may want to moderately react to all of the antivirus and firewall signals and experience assured that they'd a hand on maximum safety threats. But now, all information on all servers and all site visitors on each community connection is probably suspect, and depended on customers blend with untrusted customers connecting thru the VPN, internet software gateways, and cloud-primarily based totally apps. Humans with conventional logging or telemetry gear can at high-quality pattern some gigabytes of information consistent with day, however AI-powered cybersecurity can evaluate and examine terabytes of information every day to hit upon malware, hacking attempts, information exfiltration, or proof of a a success or ongoing assault.
2) Catch suspicious conduct, now no longer simply suspicious bits
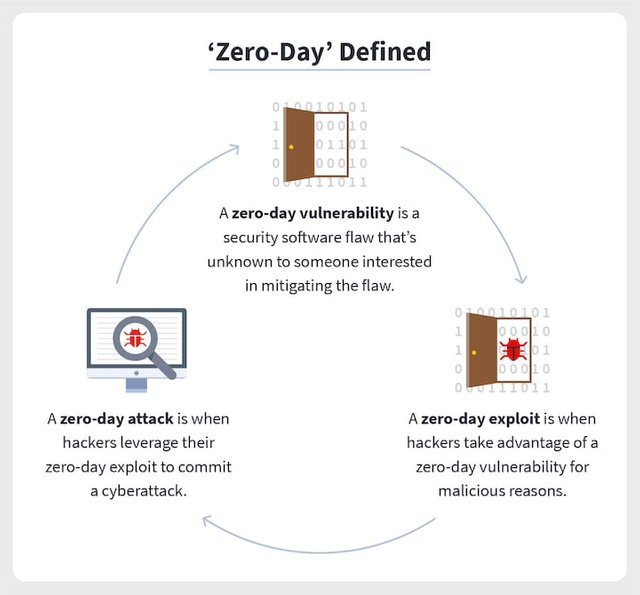
Old-college threats got here in constant, recognizable bureaucracy that failed to extrade as soon as launched into the wild. The big majority of companies could be covered so long as they often up to date their safety software program signatures. Now, superior malware modifies itself, and hackers' toolkits permit horrific actors create novel malware day by day or maybe hourly. New exploits and viruses frequently assault information facilities earlier than the safety agencies can distribute up to date signatures. These zero-day assaults have not been visible earlier than, so that they do not display up in any risk databases. AI-powered safety can hit upon those threats with the aid of using locating suspicious conduct in preference to most effective scanning for acknowledged signatures. AI may be skilled to apprehend suspicious software conduct or site visitors styles to hit upon new assaults, despite the fact that the precise assaults have in no way been visible earlier than.
3) Identify bugs, vulnerabilities, and errors in packages and networks
AI has the strength to enhance safety with the aid of using locating and resolving troubles past malware and leaked touchy information. It can test software, server, and community logs to perceive misconfigurations, old software program, or incorrect settings. AI also can test software code earlier than deployment or chip designs previous to tapeout to assist discover vulnerabilities earlier than the goods move into use. These makes use of don’t discover threats or viruses however dispose of system, software, and community vulnerabilities, making hacks and assaults much less possibly to succeed.
4) Identify machines performing as human beings and human beings performing as machines.
Users authenticate themselves to get admission to packages, and the diverse software, internet, database, and middleware servers additionally authenticate themselves to different machines to proportion information. But what occurs if a botnet learns to emulate what the human personnel are doing? What if an adversary pretends to be a depended on server? AI-powered safety learns the regular site visitors and information get admission to styles and might hastily hit upon whether or not machines are impersonating valid customers (machines as human beings). It also can hit upon whilst adversaries are impersonating depended on machines to benefit get admission to to touchy information (human beings as machines).
5) Identify in no way-earlier than-visible or zero-day threats
Traditional safety software program references a database of acknowledged malware signatures that need to be blocked from entering into the information center. The hassle nowadays is the databases of malware signatures, and touchy statistics can't be up to date quick sufficient to preserve up with new malware introduction or self-enhancing malware. Likewise, a set listing of touchy information to be averted from leaking out of the agency will constantly be out of date. AI-powered safety can perceive zero-day assaults with the aid of using spotting suspicious styles of conduct or community site visitors with out counting on constant signature databases. And AI can apprehend classes or forms of touchy statistics in preference to noticing most effective statistics that suits rigid, predefined lists.
As the quantity of information, assault surface, and quantity of threats maintain to grow, AI generation is the most effective possible response. AI-powered information technology offers the dimensions to cowl all of the applicable machines and community site visitors together with the adaptability to apprehend many new threats and vulnerabilities that InfoSec groups and their software program gear have now no longer visible earlier than.
Special thanks
@siz-official
@vvarishayy
@ashkhan
@cryptokraze
@arie.steem
@suboohi
@qasimwaqar

Why you don't reply me at discord.
And you didn't give me your achievement 1.
What happened? You also texted yesterday. If there is any mistake, you can tell me. Brother, I will send you the link of my achievement here.
Give me your achievement 1 link.
Here is the link to my brother Achievement One.Achievement 1 link
Please read these guidelines.
You cannot post Tutorials.
You can apply for course and after approval you can post such tutorials in form of a course.
You have to follow day-wise content creation guidelines.
https://steemit.com/hive-181430/@siz-official/siz-community-guidelines-on-daily-content-creation-categories