7 days Writing challenge day 3 Cryptography
What Is Cryptography?
"Cryptography is a method of protecting stored information and communications through the use of codes, so that only those for whom the information is intended can read or process it.Source
Terminologies
Plaintext:
information written in a readable form or language.
Cypher:
A specific techniques or method uses in scrambling plaintext into an unreadable form with the possibility of reobtaining the original plaintext. In classical Cryptography it is an algorithm used to transform any plaintext in to a cipher text.
Encryption:
The act or process of using a Cypher to scramble information.
Cypher text:
This is the unreadable text you get after encrypting a plaintext using a specific Cypher.
Decryption:
The process of changing cypher text Back into its original form as a plaintext. This process is also know as deciphering
Key:
This is some kind of password you attache to a cypher when encrypting plaintext into cypher text. Once data is encrypted using a key, it can only be decrypted using a key.
If the locking system requires that the same key that encrypt [locked it] should be used in opening it, such is called a symmetric key. But if one key is used to encrypt and another special key is needed to decrypt it, this type of key is asymmetric.
In most cases, the strength of a key is in its length. Example is your Steemit key.
While Cryptography is interested in Concealing information for secure communication and storage using and developing new cyphers. There is a branch of Cryptography called steganography.
Cryptanalysis tries various techniques to unveil the hidden information without the key being provided. Both of the are under Cryptology.
This post shall be looking at a specific Cypher: the free merson cypher used in making this information unreadable
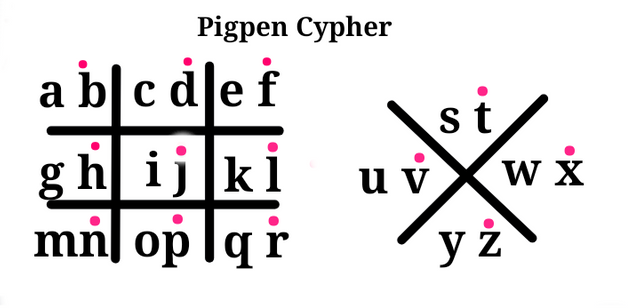
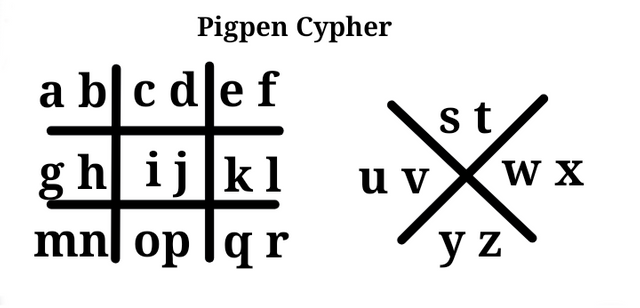
To read this information you will have to understand the pigpen cypher. We earlier defined a cypher as a specific techniques or method uses in scrambling plaintext into an unreadable form.
Here the alphabet have been replaced with this signs and this will help you understand how the signs are derived
It is an adaptation from the free merson cypher, now called the has pigpen cypher. here is a link to a cypher that was considered in an earlier post. Known as a column disposition cypher
After arranging the alphabet it groups of two, the second alphabet are all given a dot as shown below.
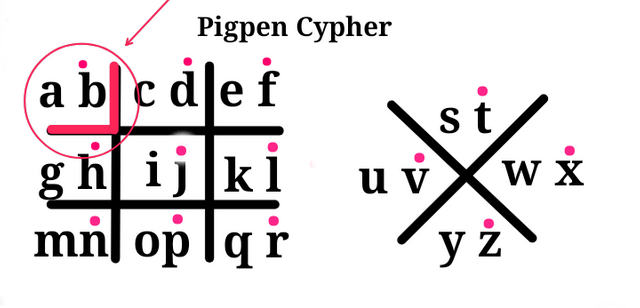
Because latter a is at the top left corner, this sign that corresponds with its position is used to represent latter 'a'
The same sign is used for latter 'b' but a dot is added to distinguish it from latter 'a'
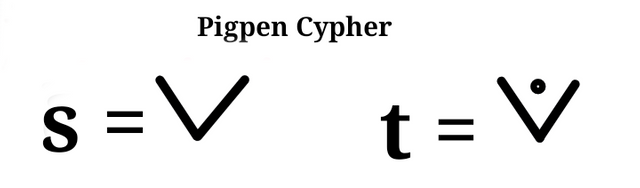
To get letter s and t, the v like shape of tis location is used as shown below.
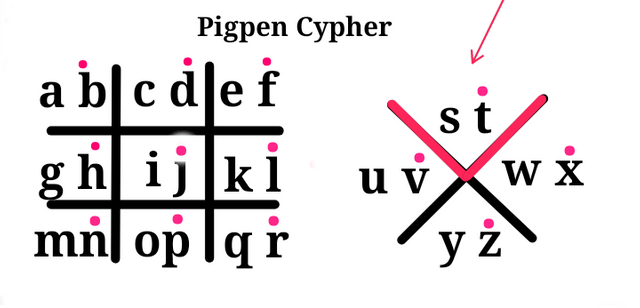
This gives us the following.
With this you can now decrypt the following pigpen encrypted data.
This massage says www.steemit.com
Going back to the first encrypted data in this post. If you tried to decrypt it, you probably got some random alphabets that really did not make any sense.
That is because the pigpen used in this case was reinforced with a key to make it impregnable. First the key must be carefully selected, It must be a Heterogram. Heterograms are words that use each alphabet only once.
So a word like 'moon' is not good for a key, Data is not a good key, it has a two times
Examples of good keys are:
Authorised
Amplitudes
Mistakenly
Volkswagen
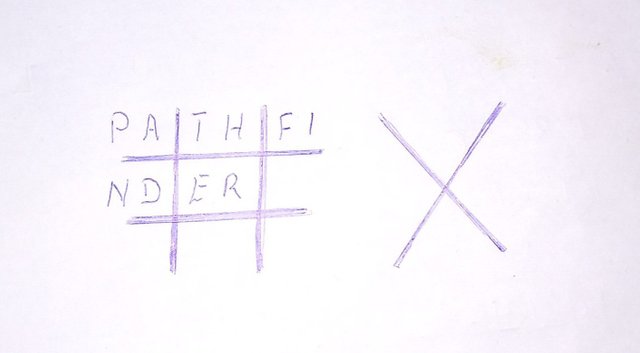
Pathfinder
When encrypting the data I used 'Pathfinder' as my key. I started by putting in the word Pathfinder which will greatly alter the position of the alphabet in the pig' pen.
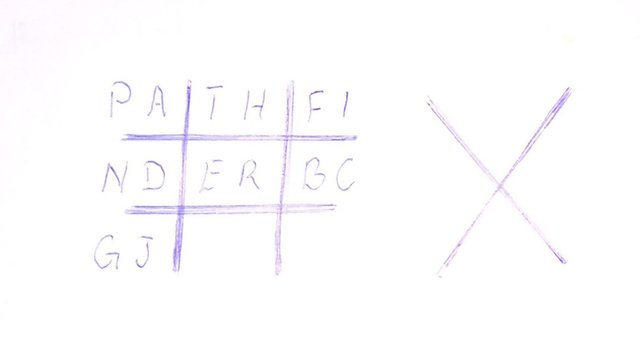
then other alphabet followed in alphabetical order.
Make sure you don't use an alphabet twice.
We could start with 'a', because 'a' has already been used we take 'b'. Latter 'b' has not been used so we write it down and move to 'C', followed by G and J.
And now the table is completely filled and dots in place. With the help of this table, You can now decipher the content of the opening message. Please Attempt solving it using the key and place your answer at the comment section below.
You can also drop any questions if you need clarifications.
My achievement 1 link
Invited to participate
@akhtarbadar2 @nickjon @arau @padmore
You can use this link to the contest
#writingchallenge #contest #cryptography #steemexclusive #krsuccess #steemit #nigeria



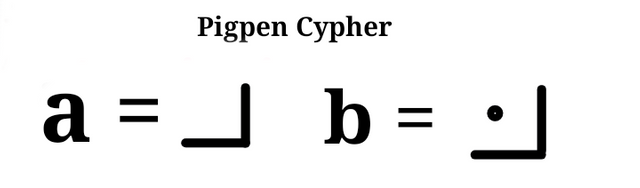
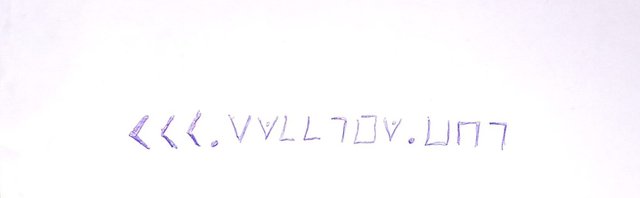
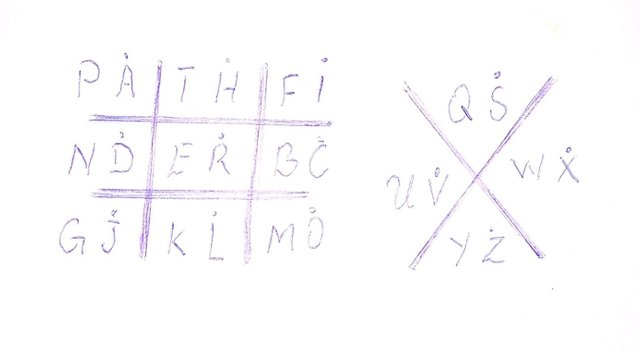
These things I know not. You are a great teacher. You gave a clear breakdown of this knowledge.
Thank you for sharing with us.
Am happy you liked my post. My art of teaching is still being developed. But thanks for appreciating.