Homework Task || Grassroot Crypto Education (Vol.4) - Cryptography: Private-Key Encryption, Public-Key Encryption and Hash Functions | 20% payout to @steemkidss
Designed With Pixellab
Questions
1. Define Cryptography. Explain Private-Key Encryption, Public-Key Encryption, and Hash Functions. What is the distinctive difference between Private-Key Encryption and Public-Key Encryption?
2. What happens to outsiders if a message is encrypted? Give a brief example. Visit https://andersbrownworth.com/blockchain/hash, enter two different inputs, and show your observation. (Screenshot required).
Answers
Cryptography
Cryptography can be defined as the process of transferring information between individuals in a confined method that only the sender and the receiver can view the hidden contents. In other words, it's a secured way of passing information from the Encoder(Sender) to the Decoder (Receiver) without exposing the Contents of the information to outsider.
Types Of Cryptography
There are three types of Cryptography which are: Private-Key Encryption, Public-Key Encryption and Hash Functions.
Private-Key (Symmetric) Encryption
Before we dive into this category we must know the meaning of Encryption and Decryption. Encryption can be defined as a process of securing readable messages or texts with passcode or it means a way of converting Messages to a code that prevents unwanted guest from viewing the contents of the message WhileDecryption means to reverse the Encrypted information back to the original state. Now you know the meaning of Encryption let's move forward. Private-Key Encryption make use of a single key(Private/Secret Key) to encrypt (lock/hide), and also make use of the same key to decrypt (unlock/unhide).
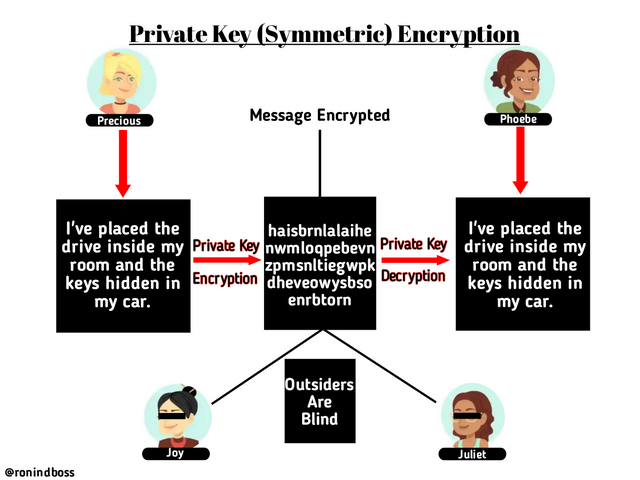
In addition, the sender of the message encrypts with the private key and gives that same key to any trusted receiver who the decrypts it. Using this method, the message is not exposed to any outsiders. Here's am illustration below.
This illustration shows how Precious sent an encrypted message " I've placed the drive in my room and the keys hidden in my car" to Phoebe using the private key. Joy and Juliet are outsiders in the transaction, as such they were blinded from seeing the details. At the Destination, Phoebe used the same private key to decrypt the message. In conclusion, a Single keu (private key) is used for both encryption and decryption in this of cryptography.
Public-key (Asymmetric) Encryption
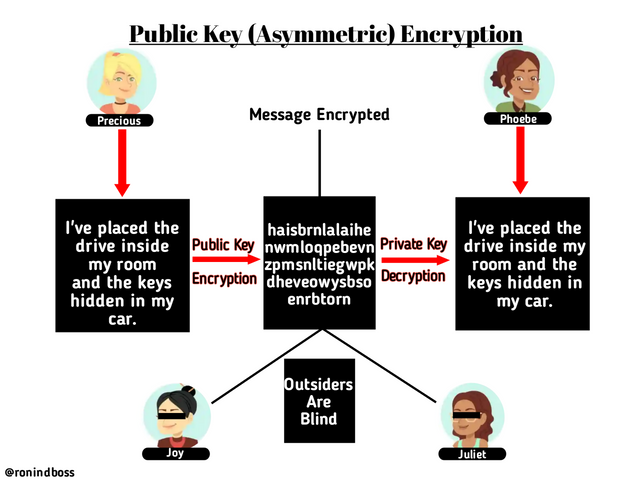
In this type of encryption, instead of using the same key for encryption and decryption, two keys are involved in Public-Key encryption. In total, there's a key used for encryption while the other is used for decryption. In this type of cryptography, the public Key is used to encrypt(lock/hide) the message by the Sender (Encoder) while the private key is used to decrypt (unlock/unhide) the message by the reciever(Decoder). Here's a illustration below to help understand better.
From the illustration above, Precious sent a message "I've placed the drive in my room and the keys hidden in my car" to Phoebe, the message was encrypted with a public Key and that blinded Joy and Juliet from viewing the contents of the message. At the destination, Phoebe decrypted the message with a private key and the contents were revealed to her.
Note: the difference from the two types of encryption is that Private Key Encryption used a single key while Public Key Encryption uses two keys.
Hash Functions
Hash functions are an irreversible and one-way function, such that data stored about a particular cryptocurrency transaction cannot be reversed. In that case, the originally inputted data can't be recovered through tweak or editing or any form of altering.
Hashing is a product of the function such that the data of an entire transaction is converted into fixed-length string "Hash" which is an alphanumeric (alphabets and numbers) combination. In hashing, each input gives different outputs which means it becomes hard or impossible to make up a fake transaction. Let us take an example below.
- The website I will be using for the example is https://andersbrownworth.com/blockchain/hash . Now I will input two different inputs, consider inputs as transactions. Let's see how it goes.
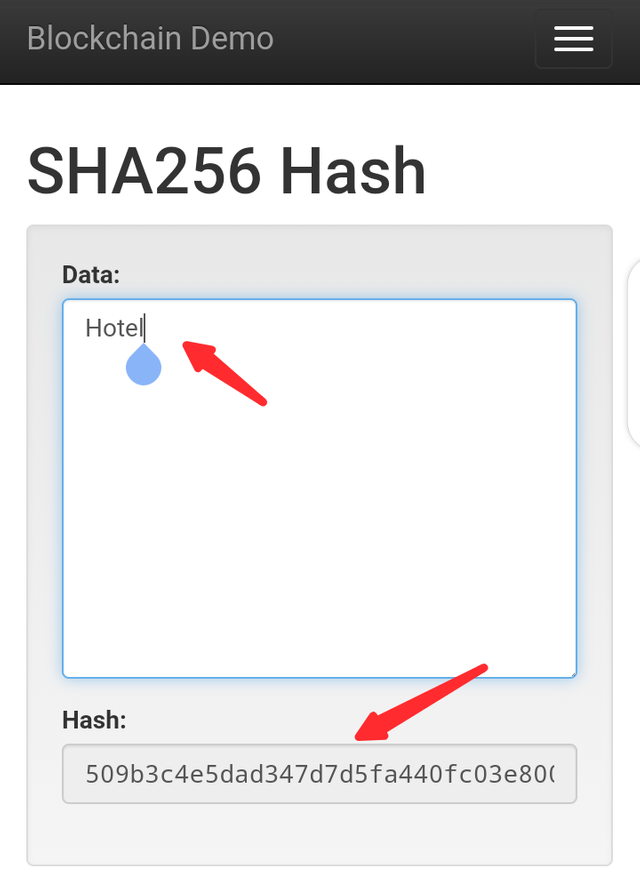
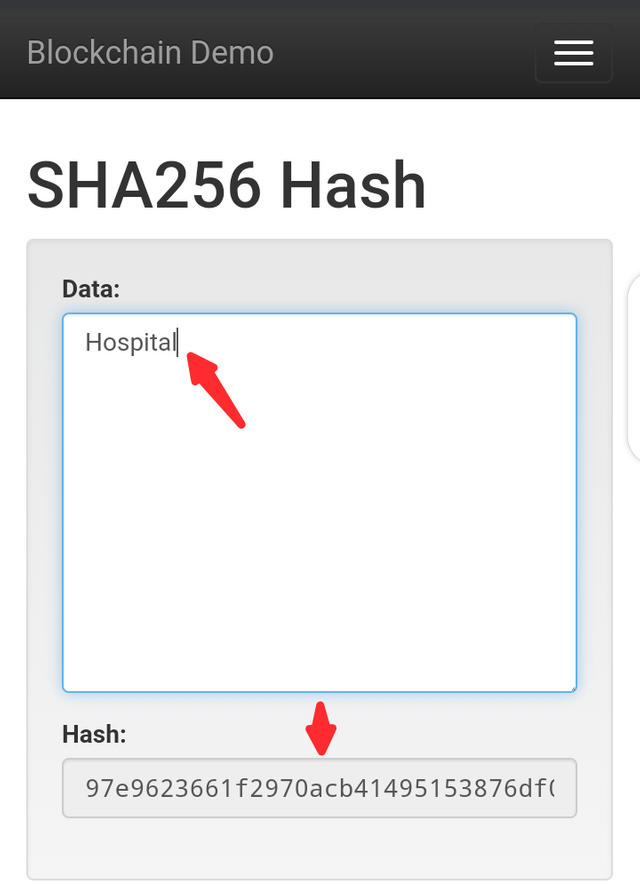
- For the first one, I inputted Hospital as the input and for the second one, my input is Hotel. Let's see the result below.
The Hospital input has the output hash "97e9623661f2970acb41495153876df0836f6894398e2c45bb5a29d109ba9a46" while the Hotel input has the output hash "509b3c4e5dad347d7d5fa440fc03e800e196e15eed6f3aa884534b65e8da0c24". From the results.
- Both input have different Hash which means two different inputs will always have different hash and in that way, it's not possible to reverse the input that produced the hash.
- No matter the length of the input, the output comes with a fixed length hash even though the length of the inputs differs. If you count both generated above, it is 64.
Conclusion
That sums up everything in my homework tasks. Thanks to @fredquantum for conducting this topic. I'm looking forward to writing more of your tasks.


Hello, thank you for joining in the crypto education for the kids, but I must inform you that you do not meet the requirements for participating. You must be a kid in steemkids community before you can participate in this lesson. Thank you...
You can join the steemit cryptoacademy where everyone is allowed to participate in the assignments if you meet the requirements. For the meantime you can be reading the lectures just for learning sake.
Oh, how can I be a verified kid in this community?
@madilyn02
From what I observed from your blog, you must ba above 19 years old, right..? Verified kids are from the ages of 13-18 here. Thank you
Please don't be mistaken but I'm actually entering 17 this year. How can I become a verified kid please, I need to participate in this crypto class because I couldn't enter the main crypto academy because of low reputation.
Ok, I guess I was mistaken. Please follow the instructions in the post below to get verified:
https://steemit.com/hive-139765/@steemkidss/2qc9uu-our-new-kids-identification-verification-system-continues-or-or-get-your-label-kids-verified-kid-or-or-see-how-you-can-be
I've done that, awaiting verification.
Hello, @madilyn02. Kindly confirm the status of @ronindboss, I can see on hold on his label. Let me know if the user is a genuine kid in the community. Thank you.
He was found to be committing content faming, For now he is not accepted as a verified kid until he proves that he is not going to continue with that path.
Please do not rate his assignment for now...Thank you
Okay. Thanks.
.
Hello, @maliyn02. You should spend more time on verifying articles before marking it free of plagiarism. This user was involved in a plagiarism act while you marked his article free of plagiarism. Take note.
This is quite serious, the check I conducted on his post using the plagiarism checker gave me no results of plagiarized content except for the questions copied from the lecture.
I should be more careful next time while checking...thank you professor