HOME TASK WEEK 5 FOR PROF. @gbenga || SECURITY PROBLEMS WITH CRYPTOCURRIENCIES
Hello everyone !!
This is my post in the regard of the hometask for crypto-academy for prof. @gbenga for Nigeria. I have read the whole post of dear sir about the Security Problems with Crypto-currencies and I have understand the whole of the lesson. So, let me explain the topic of today.
Introduction about security :
As you know that , Security and privacy is the basic thing in our dailylife to prevent ourselves from the action of being hacked or plagiarized by someone other. Without security all of us are not assured about the guarnted privacy and safety of our things. The same case is with the users in the crypto currency world. This is a basic problem with all users to being satisfied about their proper security and privacy of their accounts as well as their wallets. All of the Block chains are decentralized and as you know that there is no any centre from where the whole of the activities made on these blockchains are being controlled. So it is difficult for the organizers to keep constant eye over the basuc security and safety of one's wallet.
Wallet Security :
Same like as the wallets we use in our daily life to keep our money secure and protected, in the crypto world there is also a wallet known as Crypto Wallet in which the user is capable to access his crypto coins as well as to keep a view on the transactions and transfers made by his wallet. One should be well- awared about the security of the wallet to keep his currency protected from the reach of the third party.As per type there are different kinds of wallets. One is the which whose keys and accessibilities are under the control of the owner of the wallet as well as the organized thirt parties (mostly the crypto exchangers). The second one is the kind in which the accessability of the wallet is just under the control of the owner of the wallet and no one can access to his wallet without his permission or without his awareness.
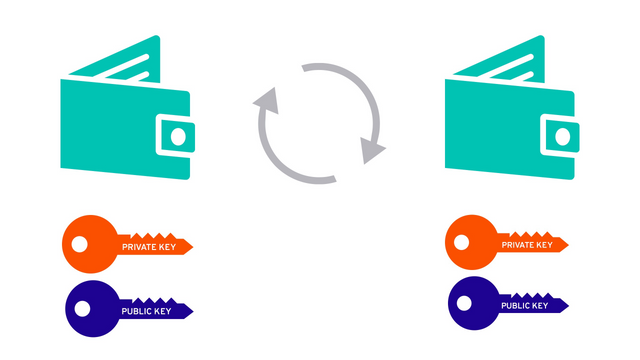
Wallat Keys:
In the regard of the protection and security of the wallet of the assest, different keys are assigned to the users to keep the control of their wallets under their influnce. These keys are the set of the organized characters as well as the different cryptographic elemnts including numbers and figures. These keys are given the name as the Private Keys. As the name of the keys represents their work , these keys are privately used by the users to keep intouch with their wallets as well as to made different transactions from their wallets. Steemit Blockchain also provide a private key to its users which one must keep secure and safe, as once lost never be recovered. So first ensure your keys to keep them in place where you think that they are protected and also keep a hard copy of the keys in order to utilize this copy if you have unfortunately lost your keys.
Crypto Jacking (Milicious Cryptomining) :
Crypto jacking is one of the most mind blowing phenomenon in the world of crypto curriencies. Can you think or just imagine that someone can use your computer as a site of his cryptomining? Yes, it is possible through cryptojacking. The cybercrimanal use of your devices, like laptops, mobiles, computers or other devices for the mining of crypto curriencies is called as Cryptojacking. It is the unauthorized and unusual use of your computer for the mining of the crypto curriencies without the permission of the owner of the computers. The hackers and the cybercriminals hack the computer and use the power of the victim computer for the mining of crypto coins.
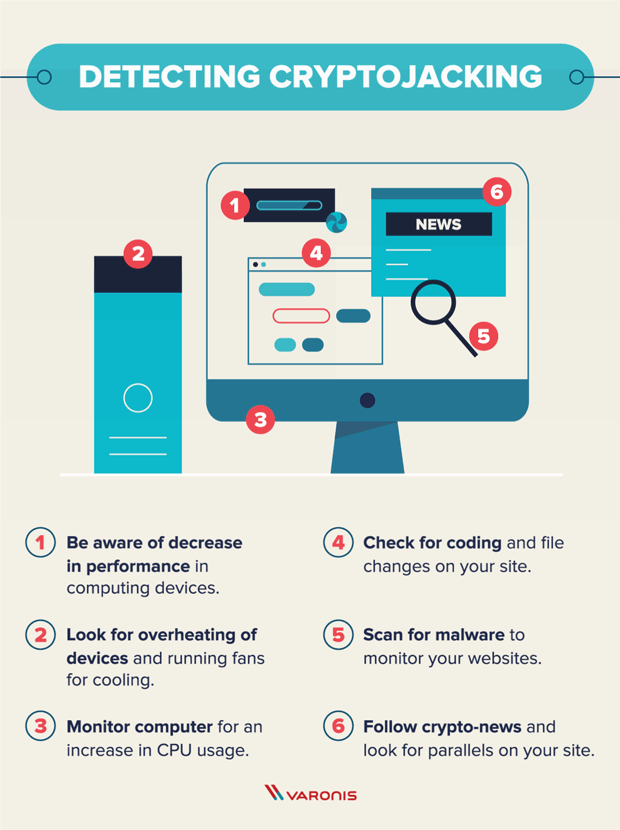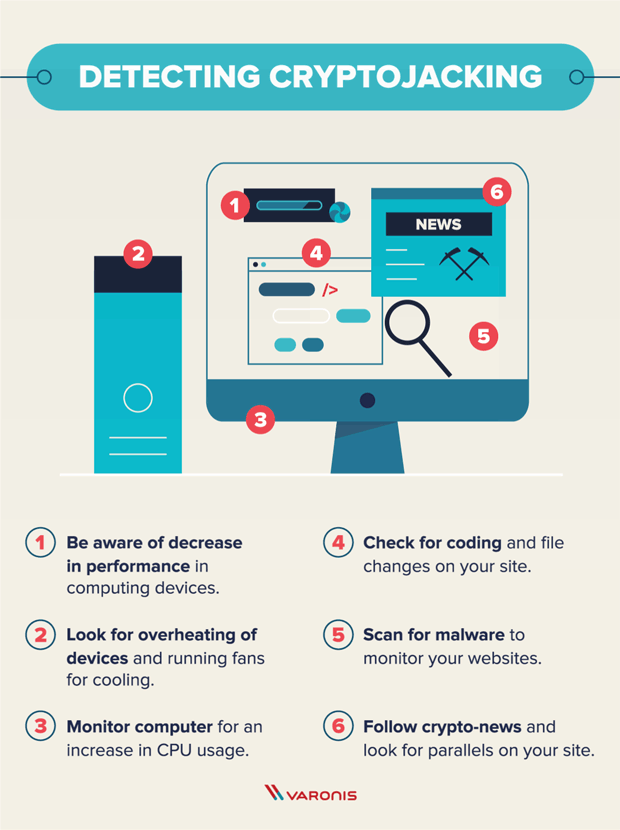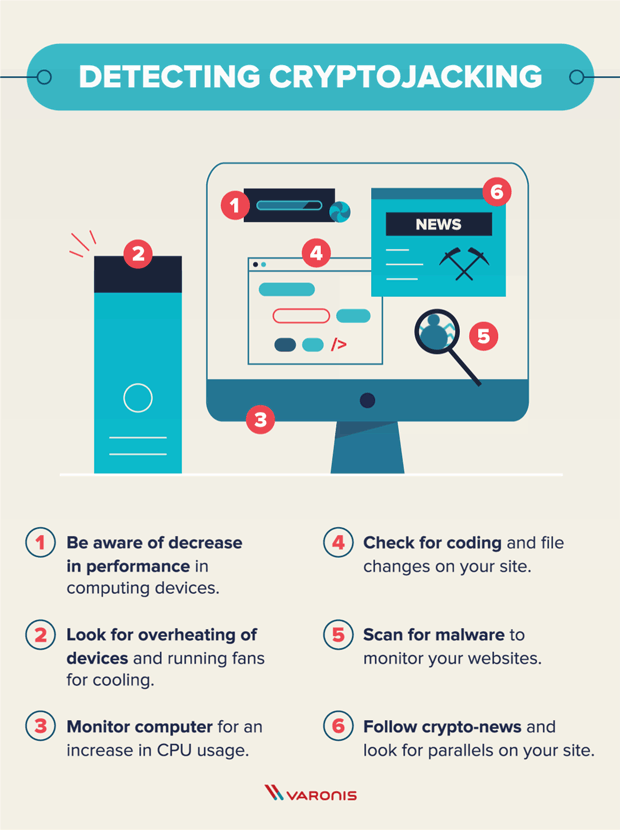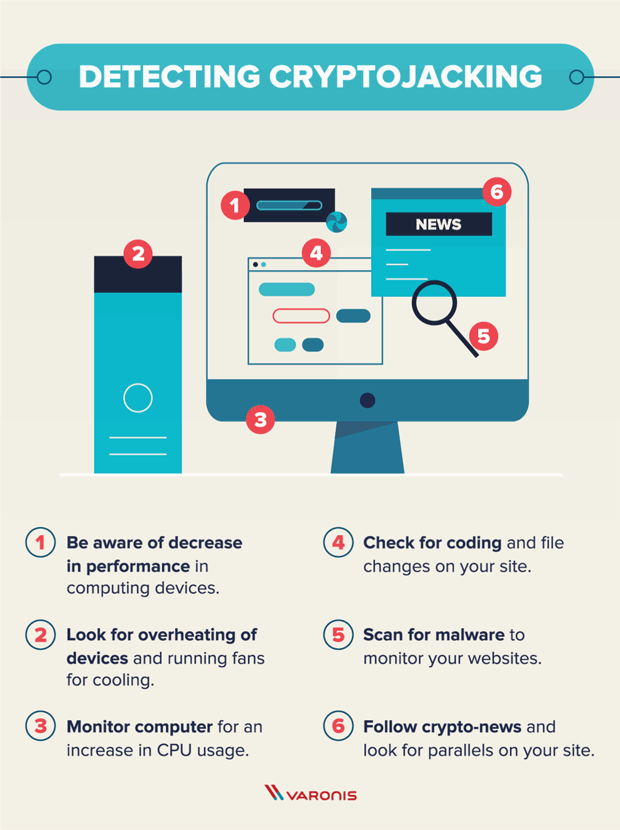
Finding out Cryptojacking:
The cryptojackers paste such urls or links where they become able to track the informations about the computer and the owner of the computer. On clicking these links one can lose access to its computer or even the hackers gain access to the wallet of the victim and track the transactions and transfers made by the owner . In a common it can be cleared with an example that if you are sending some tokens or crypto coins to your friends, you must have to provide the reciever address but in the cryptojacking case, the hacker will be well awared about the transaction you are going to made and he would clear the copied address from your clipboard and paste his own mining address in the place of your friend. In this way the money will be transferred to the authorized user. The person who are evolved in the cryptojacking cases are tracking the informations about the victim time by time and tried their best to get more and more mined coins. These links could be found randomly on the social media site and at other sources and all of we should avoid such scripted links and addresses. Such ads are also shown in different websites and by clicking on these adds our private wallet keys could be in danger. So we must avoid from such kind of acts.
Detection:
Some common symptoms which are found in victim computer or device are:
1.Overheating of the system ot the device.
2.Depletion in the normel performance of the device.
3.Increase in the normal CPU usage.
4.Changing of file and coding.
Preventive Measures:
The necessary measures to ensure your privacy and to prevent your device from cryptojacking are as follow:
- Download an ad-blocker extansion on your browser.
- Do not visit the unknown and randomly found links or ads.
- Don't over talk or chat with the unknown people and avoid to open the links they provide you for beneficial purposes.
- In the case of no usage of any crypto mining, just add an anti-crypto mining add on to your web browser.
- Disable Java script during and browser search.
- Do not download the applications or files from untrusted sources.
- After finding any of the above symptom, just delete or remove the content related to crypto-jacking.
- Block the unessential websites.
- Update the browser and the system after constant intervals to prevent crypto jacking.
Summary:
All of us must be well awared about the security and privacy of our crypto wallets. We must back up our private key to utilize it in the hour of need when we happened to lose it. One must keep his wallet, nodes and platform away and away from the milacious attackers and hackers. It is more effective to keep our things safe otherwise we could lose them. So it is recommended all of you to follow the above instructions to prevent from the cryptojacking and other problems.
So, that's all about my home work of week 5.
Special Thanks:
for his lecture and instructions.
Special Mentions:
@steemcurator01
@steemcurator02
@steemitblog





Hello @steemlover63, it is good to have you participate in this week's assignment. I must commend the effort put together to create a post. Learning is the goal of this school and in this light, I will like you to work on the few things I will be correcting.
Grammatical construction
It can be very difficult to mumble out correct sentences especially when there are clouded ideas and thoughts. So it is advisable to use digital writing assistants like Grammarly to check spelling and grammatical constructions.
Rating 6
Ok sir thank you a lot for checking my post and for mentioning out my mistake. I ensure you that I will try my 100% to prevent such type of gramatical mistakes and I'll surely use the Grammarly tool to avoid from these mistakes.
Hola profe @gbenga esta es un publicacion mia de la semana pasada que se le perdio porfavor revise
https://steemit.com/hive-108451/@risedaniel/publicacion-de-tarea-de-la-semana-5-de-cryptoacademy-para-gbenga-hakeo-de-criptomondas