Crypto Academy Season 3 | Advanced course : Let's Open The CryptoGraphy | Course by @stream4u
Thank you very much professor @stream4u, your courses are always amazing to me
1 Blockchain CryptoGraphy and Blockchain platforms
Cryptography is a method of keeping information save and communications with the use of codes, for only those that the information is meant for, or the person you intended can read and process it. The phrase crypt simply mean vault or hidden -- and the phrase graphy mean for writing.
Cryptography refers to secure communication and communication method that derived from concept of mathematical and a rule set that based on calculations named algorithms, to change messages in ways that are difficult to decode. These mathematical determined algorithms are used for generating key for cryptograph, verification to protect data privacy,digital signing, internet web browsing, and confidential communications like email and credit card transactions
The techniques
Cryptography relates to the method of cryptoanalysis and cryptology . It includes techniques like merging words with images, microdots, and other ways to make information out of sight, in transit or storage. Today's computer-centric world make cryptography often associate with scrambling cipher or clear text into encoded tex.
The objectives are
Confidentially, integrity, non-repudiation, and authentication are the objectives
Confidentially : The message information can't be understood or cleared to anybody, that is unintended
Integrity : The message or information can't be change in transit or storage between the sender and the receiver with no change being found
Non reputation : the information sender can't later deny that he didn't make the transmission of the information
Authentication : The information sender and the receiver are able to confirm themselves identity and the information destination
Blockchain platforms
With high demand of blockchain, everyone has begin to experience the noumenon of this technology. At first, blockchain brought interruption in the financial industry, but now its usefulness have been examined across various sectors that include software development.
Blockchain platforms give permission the development of applications that are blockchain based. It's either they given permission or not permitted. EOS,Hyperledger, Ethereum, R3, and Ripple are some platforms that been built on the blockchain frameworks, it allow people to host and create applications on the blockchain.
2 Public Key CryptoGraphy.
You can open a message with the use of intended receiver's public key, but that encrypted message can only be converted with the receiver's private key. For example, a server program to beget a cryptographic key which is intended for a suitable symmetric-key cryptography, to use a customer's openly-shared public key to encrypt that newly generated symmeric-key. The server can send this encrypted symmetric key over a secure channel to the customer, only the customer can convert it with the customer's private key. The customer and the server both have same symmetric key, they can securely use symmetric key encryption to message each other over an insecure channels.
How public key works
Different public keys are used for decryption and encryption. It's a property that set scheme in a different way than symmetric encryption scheme.
Each receiver are in control of unique codebreaking key, it's generally referred to as his private key.
A receiver have to publish an encryption key, that is referred as his public key.
Assurance of the genuineness of a public key is required in this systematic plan to avoid phishing by adversary as the receiver. This method generally involves in trusted third party that certifies that a particular public key belongs to each person or an entity only.
Encryption calculation is composite enough to disallow the attackers from taking away the plaintext from the ciphertext and the encryption which is the public key.
3 Private key Cryptography
Private key is a secret key, that eable to vary in cryptography, it is used with an algorithm to conceal and convert data. You Private keys should be close, it shouldn't be given or shared with anybody, only the key's generator or parties are authorized to decrypt the data. Private keys can play a necessary role in asymmetric, symmetric cryptography, cryptography and cryptocurrencies.
Private key is typically long, random or fake-randomly generated series of bits that can't be guessed easily. The entanglement and length of the private key would determine how easily an attacker can make a brute force attack, where they keep trying different kind of keys until the right one is discovered.
How private key works
Key management: Private key management is needed in order to avoid making use of any individual key for too long. It securely retire keys after their lifetime of useful lapse.
Generating a new private key : Anterior to encryption, it generate another key which is as random as possible and the encryption software is commonly to generate private keys.
Securely storing the private key : Once new key is generated, the private key must be saved securely. The keys may be stored in offline or on the computer that was used to generate it, encrypt and decrypt data. It can be protected with password, hashed for security, encrypted, or all the three.
Key exchange : Private key can be use to encrypt, as well as to decrypt, so if you use it for symmetric encryption, it would need a key exchange to share the key in a secure way with trusted parties that have authority to data exchange secured. Cryptographic software is always used to robotize this process.
4 Digital Signature and signing of transactions/message
Digital signature is a cryptographic quality that is compute from the data and a private key known by the signer only.
In physical world, receiver of a message needs an assurance that the message is from to the sender and he should not be able to deny the origination of that message
Digital signatures are public key that permit message validation. In the real world, it is common to use our handwritten signatures on written or typed messages. They are used to bind signatory to the message.
In a similar way, a digital signature is a method that binds an entity or a person to the digital data. This kind of binding can be verified by a receiver independently as well as third party.
How digital signature works
Each entity that adopt this system has a public private key pair.
The key pairs used for decryption or encryption and verifying or signing are different. The private key is useful signing and it's is referred as the signature key and the public key is referred as the verification key.
The signer gives data to the hash function and beget hash of data.
Value of Hash and signature key are then given to the signature calculations which produces the digital signature on hash that was given. Signature is signed to the data and they are both sent to the verifier.
Verifier give data to the digital signature and the verification key into the verification calculation. The verification algorithm then gives some value as an output.
4 Digital Signature and signing of transactions/message
Digital signature is a cryptographic quality that is compute from the data and a private key known by the signer only.
In physical world, receiver of a message needs an assurance that the message is from to the sender and he should not be able to deny the origination of that message
Digital signatures are public key that permit message validation. In the real world, it is common to use our handwritten signatures on written or typed messages. They are useful for to binding signatory to the message.
In a similar way, a digital signature is a method that binds an entity or a person to the digital data. This kind of binding can be verified by a receiver independently as well as third party.
How digital signature works
Each entity that adopt this system has a public private key pair.
The key pairs used for decryption or encryption and verifying or signing are different. The private key is useful signing and it's is referred as the signature key and the public key is referred as the verification key.
The signer gives data to the hash function and beget hash of data.
Value of Hash and signature key are then given to the signature calculations which produces the digital signature on hash that was given. Signature is signed to the data and they are both sent to the verifier.
Verifier give data to the digital signature and the verification key into the verification calculation. The verification algorithm then gives some value as an output.
5 Symmetric and Asymmetric cryptography?
Symmetric cryptography is also known as secret key cryptography, it is useful for a just a single shared secret to share encrypted data in between two or more parties. In this category, Cipher are called symmetric simply because you can use the same key to decrypt and encrypt the data. In an easy terms, the sender disclose the information with the use of a password, and the recipient must know that password to have access to the data.
Symmetric encryption is process in two ways. First one is with a block of plaintext and a key, symmetric ciphers always make the same ciphertex. Second one is using that same key on ciphertext, which will always make the original plaintext. This encryption is useful for guiding data in between two or more parties with a created shared key and is also used frequently to save confidential data.
Asymmetric cryptography or Public key Cryptography is a key system that uses pairs of keys: which are public keys and private key. Public key (that may be known to others you pass information to), and private keys (which should never be known by anyone except the owner). This key generation depends on cryptography platform that based on problems of mathematics termed One way function. Very good security is needed to keep the private key in a private place but the public key can be openly distributed with no compromising security.
If you are to send an encrypted message, you can pull the intended receiver's public from a public addresses and use it to conceal the message before you send it. The receiver of the message can then convert the message with the use of Private key. If the sender conceal the information with their private key, the message can be decrypted with only that sender's public key, this way validating the sender. Users don't need to physically close and open the message, it happens in an automatic way.
6 How Blockchain Wallets CryptoGraphy works
Blockchain wallet and Cryptography works in a way that you can share your wallet address with anyone, they can't access your money or cryptocurrency token just like real life Bank operate with account number. With your account number, no one can have access to your money and with your blockchain receiver wallet, no one can access your money or your coin.
Cryptography Blockchain wallet is even saver more than bank account today, there are hackers that can hack into your money in real life Bank and withdraw all your money but no one can hack your cryptocurrency wallet, only if you give out your private key. Like your steemit wallet key.
Your identity can be revealed with your bank account number but your identity remain unknown in cryptography and it doesn't stop you from receiving and sending tokens. We can only see how much is inside the wallet address and how many transactions that has been made, we can't ever know the owner's identity
I will make use of Bitcoin and ethereum as an example like
16UdXHztHAp27NTGsUowN3SoNy6QLGAka7
0x9f0c9d3412d03c8bb6afdaa3898814afbe9d9a14
The first wallet address is bitcoin wallet address and the second one is Ethereum wallet address. They would never look alike or look like another person own just like bank account number can't be same. The wallets are numbers mixed with letters, both capital letters and small letters
Banks operates with password, it's similar to blockchain wallets. Blockchain wallets own is private key, just like password that bank use and you can choose your bank password yourself but you Blockchain is the one that would generate private keys for you and it's possible to change just as you can change your password at bank
I will use Steemit as an example. Steemit have Master key that you can generate another password for your account if you sense anything suspicious. Steemit have posting key, private posting key etc but the Master key is the one you can use to change all the keys. You can give other keys out but don't give out the Master key
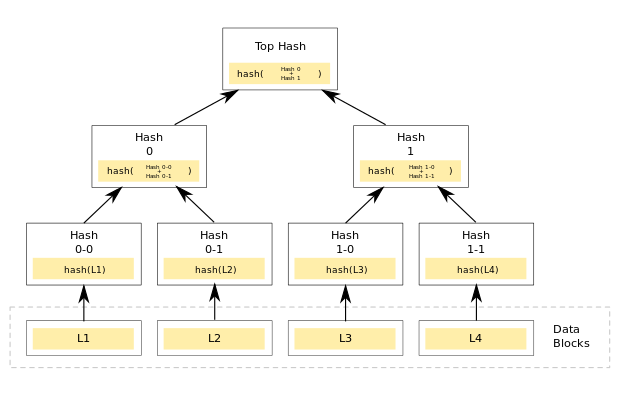
7 Merkle trees and What its importance in blockchain
Merkle tree is a tree which all leaf node is labelled with the cryptographic hash. In computer science and cryptography, all non leaf node is labelled with the cryptographic hash with the labels of its child nodes. Hash trees let's thorough and save verification of the contents of big data structures. Hash trees are a formulation of hash list and hash chains.
Merkle trees are thus thorough example of a cryptography guarantee scheme, the root of the Merkle tree is seen as a guarantee and leaf nodes may be shown and proven to be part of the original charge.
Important of Merkle tree 🌲 in Blockchain
Blockchain is made up of many blocks which are linked with each other. The Merkle tree, convert or encode the blockchain data in an secure and efficient manner. It does instant verification of blockchain data, as well as instant movement of big amounts of data from a computer node to another on the P2P (peer to peer) blockchain network.
All transaction happening on the blockchain network has hash connected with it. Hashes don't save in a sequential order on the block, it stored in the form, like a tree structure, each hash is connected to its parent following a parent child, just like tree relation.
Since it has numerous transactions saved on a particular block, all the transaction hashes in the block are also hashed, which leads to a Merkle root.
The Merkle root further speeds up verification because it has all the information about the whole tree, you just needs to verify that transaction hash, its sibling-node, and then continue upward until it reaches the top.
Basically, the Merkle tree and Merkle root mechanism reduce the levels of hashing to be done in a significant manner, it enable fast transactions and verification.
8 Public / Private Keys & Signing
functionality of Key
A key is a thread of characters that is used within an encryption algorithm for changing data. The data appears randomly after changed, just like a physical key, it locks data so that only the person or entity with the right key can unlock it
How the key function according to the video
I would explain it one after the order or step by step just like its explained in the video
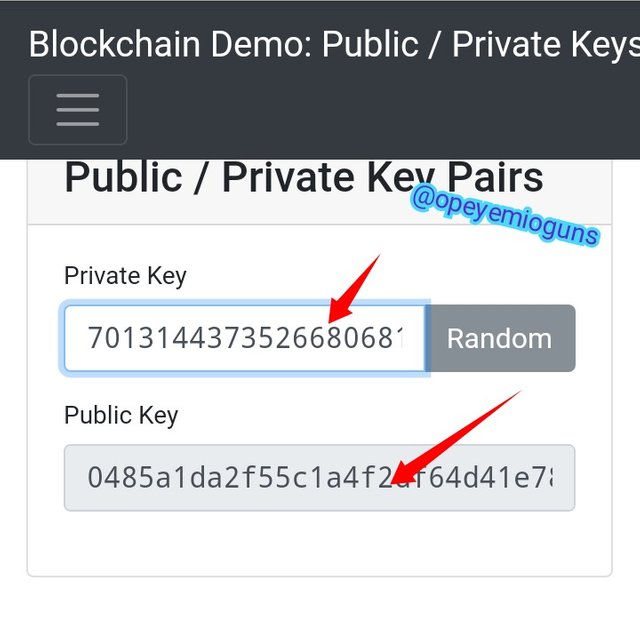
- You can create a Public key through private key
Every time or whenever you add a number to the private key, the public key would change
Your private key shouldn't be know to anyone, only you should know it
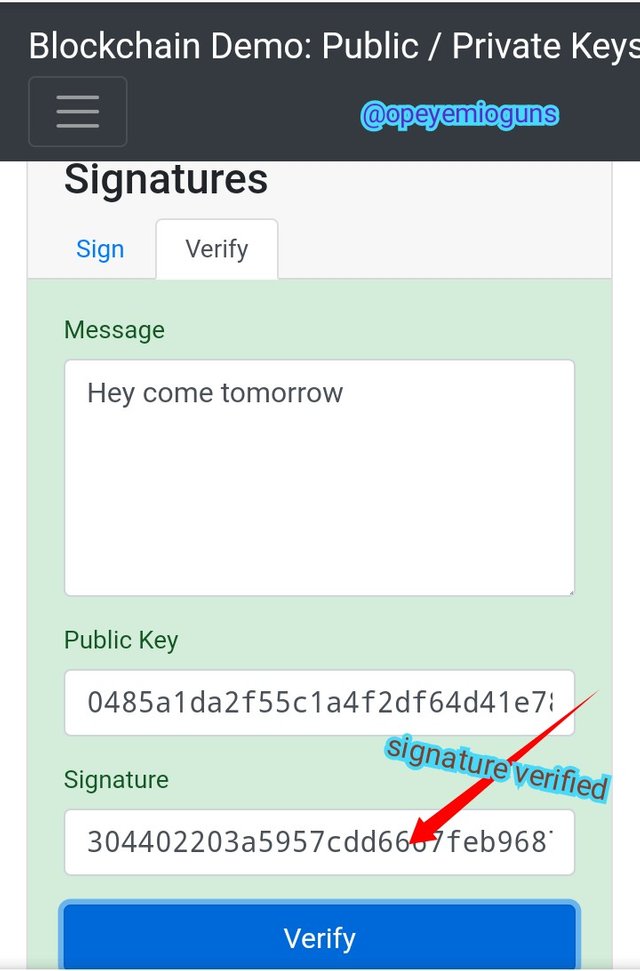
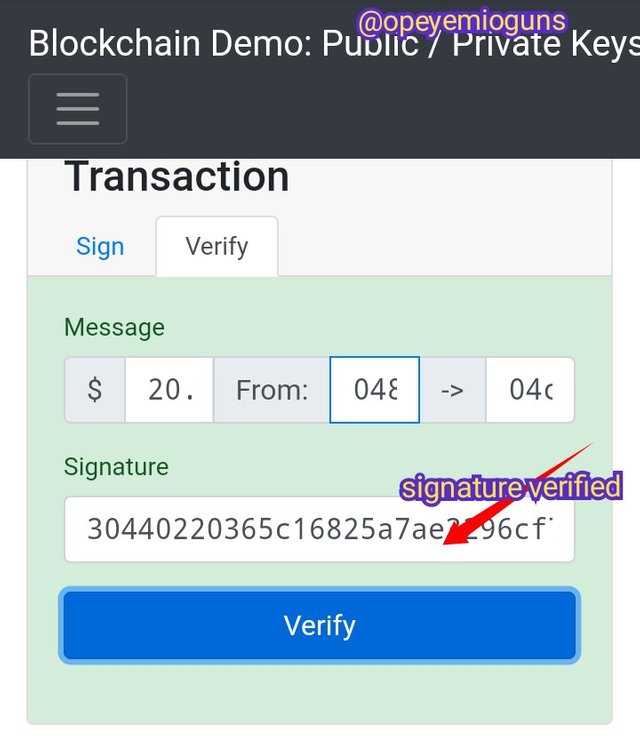
You can use your private key in the signature, once it's verified, the screen goes green
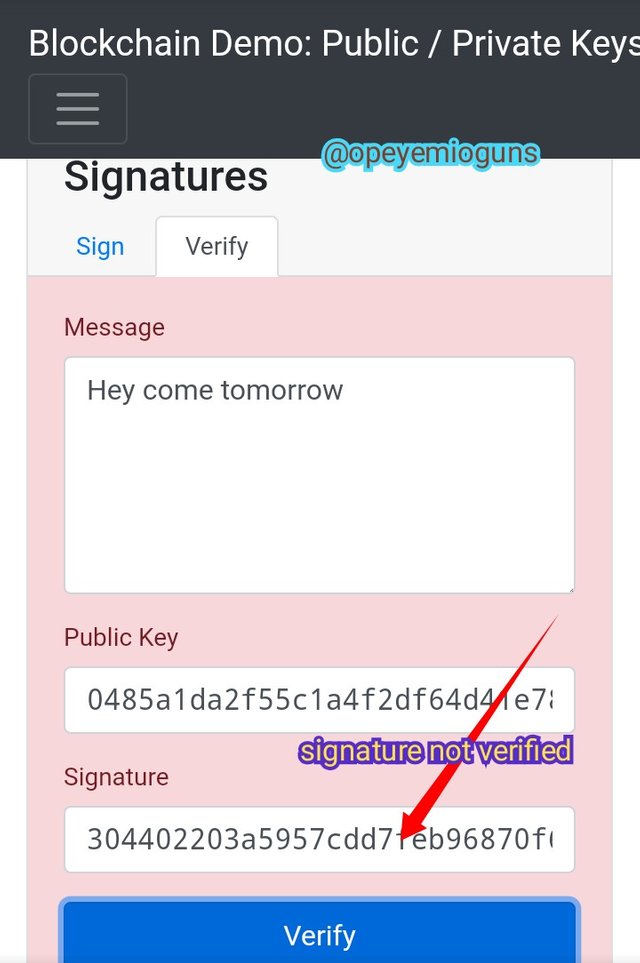
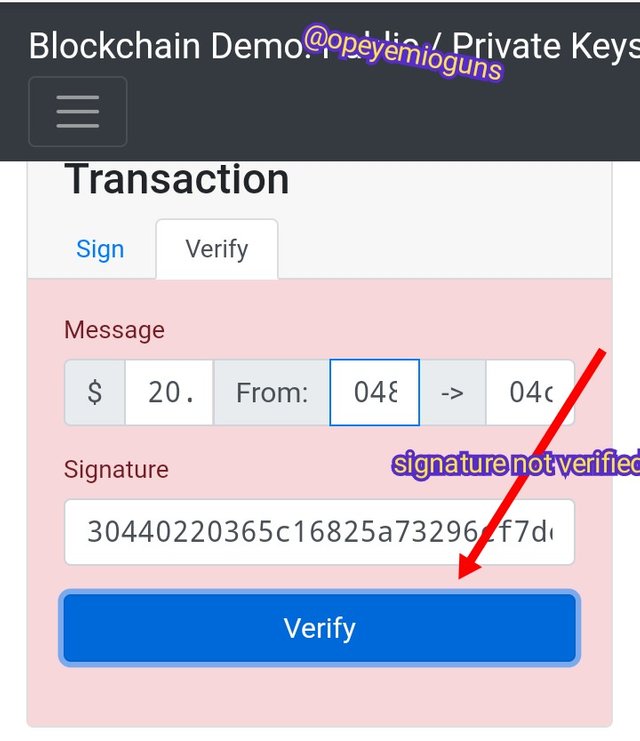
But the screen turn red if the signature isn't verified. I did this practical when I cleaned a character among the signature's random characters. If the key 🔑 isn't complete, then it won't verified.
In this demo screenshot, I tried to send 20 dollar to someone with the same private key. so private key can be use to send message and it can be use to send token as well. Just like it happens in sending message, if the private key is valid, then the screen goes green and goes red if not verified
the dame thing applies to sending message or transferring funds to multiple people or entity, if any of them didn't have the public key, they won't be able to open the message or have access to the fund
the screenshots are from blockchain demo and edited by me with imarkup
9 Conclusion
Cryptography works best in a way that's save or secure in sending message or transferring funds. This is the best format of sending messages this time around that Social media are censoring us and trying to kill our freedom of speech 💬. If platforms or applications can be build in a cryptography way or format, it would be best, I think this is a way one can chat or discuss freely.
Cryptography is decentralized in both transaction and messages, not centralized like bank and other means of chatting today





This content appears to be plagiarised as indicated by stream4u
If you have not already done so, you should head to the newcomers community and complete the newcomer achievement programme. Not only will you earn money through upvotes, you will learn about content etiquette;
Notification to community administrators and moderators:
@steemcurator01 ADMIN
@steemcurator02 MOD
@sapwood MOD Professor[Advanced]