Steemit Crypto Academy Season 3 Week 6 | Homework Post for Professor @stream4u - Blockchain

Good morning everyone and let's start a positive activity today. I will start today with enthusiasm, this morning I will continue my writing activities in the Steemit Crypto Academy community. This week, I will only be taking a class given by professor @stream4u, one of my favorite professors, and this class is about “Blockchain”. There are seven main questions that must be answered in this homework and in this post I will try to answer these questions as much as possible. Let's get started...

Q1.) What is Blockchain and What are the types of Blockchains / Explain in detail the types of Blockchain?

In general, Blockchain can be interpreted as a series of Blocks that are interconnected and form a complex network. These blocks contain information that has been encrypted and interconnected in a decentralized manner with high security standards. Its decentralized nature makes every cryptocurrency transaction details able to be duplicated and distributed throughout the network using DLT (Distributed Ledger Technology) technology and all digital records cannot be edited or deleted by anyone because everything is interconnected and this is what distinguishes Blockchain and Database systems. .
These blocks are connected by chains of cryptographic functions called Hash and each new block will be generated in a certain time frame constantly, for example, the creation of a new block in the case of Bitcoin (BTC) is every 10 minutes while in the case of Litecoin (LTC) it is every 2 minutes 30 seconds. Miners will validate every transaction on the Blockchain network by running Nodes consisting of computers around the world that act as Hosts on the Blockchain network. Based on their use, the following are four types of Blockchain that have been widely adopted to date.
A. Public Blockchain
By using an internet connection, this Blockchain can be accessed for free by anyone to connect to the network and this is the Blockchain that is generally used in the cryptocurrency ecosystem. To support the valid data distribution process, this Blockchain uses DLT technology so that the data can be distributed to all Nodes connected to the network.
That way, this Blockchain becomes very transparent because every Nodes that has been connected to the network can access all the information contained in all blocks in detail. In addition to transparency, this Blockchain is also supported by high security because this system is fully decentralized and uses Hash as a cryptographic function. But the threat of hacking is always there, especially the 51% Attack that can occur if the hackers manage to control 51% of the mining power.
With the increasing number of users because they can be accessed widely, the number of Nodes connected to the network is also increasing, causing this network to be a little slower. To obtain a faster data transmission, higher bandwidth is required at a cost that is not small. Miners will generally use devices with high computing power to carry out the mining process on this Blockchain.
B. Private Blockchain
This is a Blockchain that is used on a smaller scale because its access is limited to a certain number of nodes and every data that is here will be stored in all nodes connected to the network. This blockchain is generally created and managed by individuals or groups of people in certain communities so that they can only be accessed by authorized parties. Due to its limited access, this system runs with high security standards and excellent network speeds.
Despite using DLT technology, this Blockchain is not fully decentralized because the authorized party here is the party who has full permission to determine which nodes can connect to the network. In addition, the data here can also be edited by the authorized party. Therefore, this Blockchain is more suitable to be used for the benefit of companies in controlling the various resources they have.
C. Hybrid Blockchain
This blockchain can be said to be a combination of Public Blockchain & Private Blockchain. Although it cannot be accessed widely because the authorized party has full permission to determine which nodes can be connected, this Blockchain still allows every connected node to access all the data that has been stored here. In addition, each user can also determine whether the transactions they make will be made public or not and all the data that has been stored cannot be edited by anyone.
With limited access and not too many connected nodes, it will be difficult for hackers to enter here and the network speed here is also very good at a lower cost of course. This blockchain is generally used by a certain organization to guarantee confidentiality with high security, such as trade, banking, and other institutions. While in the world of cryptocurrencies, XinFin (XDC) and Ripple (XRP) are two examples of cryptocurrencies that have used this type of Blockchain.
D. Consortium Blockchain
Almost the same as Hybrid Blockchain, this Blockchain also combines Public Blockchain & Private Blockchain and each Nodes of a different Blockchain Consortium will verify every transaction and validate every block here. Anyone can view transactions here, but blocks can only be added if they have been confirmed by all connected Nodes. With a lower cost, this Blockchain is very suitable for collaboration between organizations.
Although not publicly accessible, this Blockchain can provide access for certain organizations at once so that there are several parties who can play a big role here. This blockchain also allows each Nodes to be able to connect with other Nodes from different Blockchain networks. However, this Blockchain is not fully decentralized, in addition to limited login access, there are also certain data that cannot be seen. In addition, this Blockchain also provides a high level of security and very good speed of course.

Q2.) What are the benefits of Blockchain?

There are various benefits that can be provided by Blockchain and it has been proven to date. Some of these important benefits include the following.
- Decentralization, everything is connected to each other without a central point making this network stronger.
- Data Traceability, by using DLT technology then all data will be available all the time and can be tracked because everything is stored properly here.
- Transparency, each data will be duplicated and distributed to all connected nodes so that it can be accessed in detail by many parties.
- Immutability, all data will be stored in the original and no one can change or delete it.
- Bookkeeping Efficiency, every transaction record will be documented more quickly and automatically without the need for paper and does not require manpower.
- Smartcontract Automation, all transactions run automatically based on smartcontract and without intermediaries, when everything has been fulfilled then the transaction will be realized automatically.
- Security, with a decentralized system and the use of Hash as a cryptographic function managed to create a high security standard here and it is very difficult for hackers to penetrate it.
- Reduced Cost, Cryptocurrencies generally use Blockchain technology and by using cryptocurrencies we can make transactions at lower costs around the world.
- Trust & Reputation, Currently Blockchain is increasingly trusted because it has been proven to be reliable by millions of users and with a very good reputation, the number of users also continues to grow every time.

Q3.) Explain Blockchain Distributed Ledger

Blockchain Distributed Ledger is a technology used to manage all data widely synchronized in real-time and all transaction copy data and block details will be distributed to all Nodes connected to the network. Distributed Ledger is a Ledger that is used in decentralized systems such as Blockchain, while centralized systems usually use a Database to store all the data they have.
Distributed Ledger Blockchain tends to be more secure because it is used in a decentralized system so that there is no central point that can cause potential failures and all data will be stored permanently on the network because no one can change or delete it. When a node is mining and successfully validating a block, a new block will be created, then the Blockchain Distributed Ledger will distribute a copy of the validated transaction and the details of the new block that has been created to all nodes connected to the network.
The Distributed Ledger Blockchain has several properties that need to be known and here are the properties to note on this Ledger.
- Distribution, ensure that all Nodes connected to the network have a validated copy of transactions and block details to create good transparency in the network.
- Immutability, ensure that all data will be stored permanently on the network and no one can change or delete it.
- Anonymity, ensure that the identity of the Nodes and the identity of the user remains hidden to maintain the privacy of each user.
- Programmable, This technology runs automatically based on a smartcontract and every sale and purchase transaction will be realized if it meets the predetermined requirements.
- Security, guarantee high security by using Hash as a cryptographic function and this is the main advantage of course.

Q4.) What Is Blockchain Double Spending and how Bitcoin handles this problem?
Blockchain Double Spending
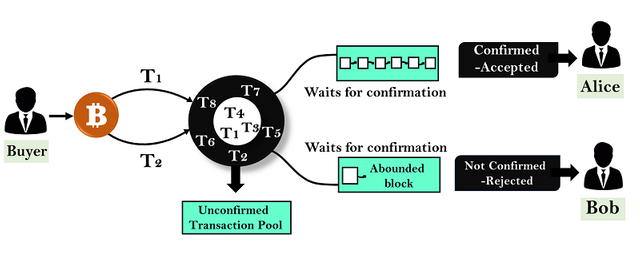
Double Spending is one of the problems that exist in the Blockchain network because it allows someone to use the same number of coins in several transactions at once to take personal advantage by tricking the system so that it can also be called an Attack on the Blockchain network and this can happen to any transaction involving cryptocurrencies. There are several examples of Blockchain Double Spending and some of them are as follows.
- Race Attack, This double spending occurs when a recipient decides to accept a transaction that has not been fully confirmed by the miners so that the hacker who sent multiple transactions with the same amount of coins manages to take personal advantage here which makes the recipient lose his assets. I'll cover that in the next question.
- Finney Attack, This Double Spending occurs when a miner makes a fake transaction using details from different blocks and it will work if the recipient decides to accept the unconfirmed transaction, then the recipient will lose the asset because the hacker has managed to steal it.
- Vector76 Attack, Double Spending occurs when hackers manage to create fake assets and send them to the recipient as a payment transaction using a software, then when the sent asset is verified by the Blockchain, the payment will automatically disappear from the recipient's wallet.
How Bitcoin Handles Blockchain Double Spending
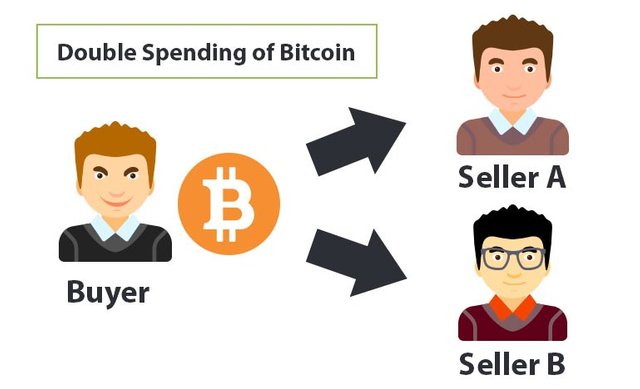
Through various transactions, Bitcoin continues to move from one wallet to another wallets and at each transfer Bitcoin will always carry all the previous transaction details in Hash form. The potential for Double Spending can occur in the case of 51% Attack because the hacker has managed to control 51% of the computing power, but this potential is less likely to occur in Bitcoin because the hacker must have enormous power to carry out this mission.
Bitcoin tackles this problem by implementing transaction confirmation by miners as validators and using DLT (Distributed Ledger Technology) technology. Every transaction that occurs must be validated before being added to the block and when there are users who do Double Spending then the transaction will be included in the unconfirmed transaction pool, but if one of the transactions has been confirmed then the other transactions will be deleted automatically from the Blockchain and will not added to the block so Double Spending can be prevented.
That way, the recipient will only receive payments sent by the sender after going through the validation, verification & confirmation process, and of course it has been added to the Distributed Ledger to be distributed to all Nodes connected to the network. When transaction details have been added to the Distributed Ledger, the data will be stored permanently on the network and cannot be edited or deleted.

Q5.) Practical plus Theory, Visit “Blockchain Demo SHA-256” (https://andersbrownworth.com/blockchain/) and check section Blockchain, then explain in detail how Blocks Hashes Work in Blockchain, what will happen when any middle of the block gets changed, try to give screenshot for each possible details
Hash Block in Blockchain
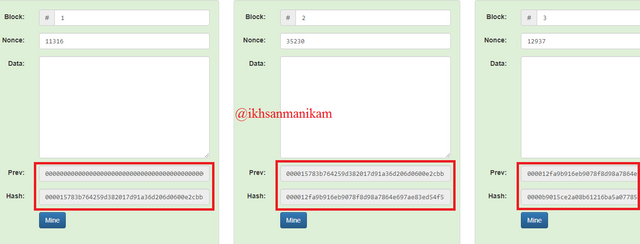
Block 1
Nonce: 11316
Data:
Previous Hash:
0000000000000000000000000000000000000000000000000000000000000000
Hash:
000015783b764259d382017d91a36d206d0600e2cbb3567748f46a33fe9297cf
Block 2
Nonce: 35230
Data:
Previous Hash:
000015783b764259d382017d91a36d206d0600e2cbb3567748f46a33fe9297cf
Hash:
000012fa9b916eb9078f8d98a7864e697ae83ed54f5146bd84452cdafd043c19
Block 3
Nonce: 12937
Data:
Previous Hash:
000012fa9b916eb9078f8d98a7864e697ae83ed54f5146bd84452cdafd043c19
Hash:
0000b9015ce2a08b61216ba5a0778545bf4ddd7ceb7bbd85dd8062b29a9140bf
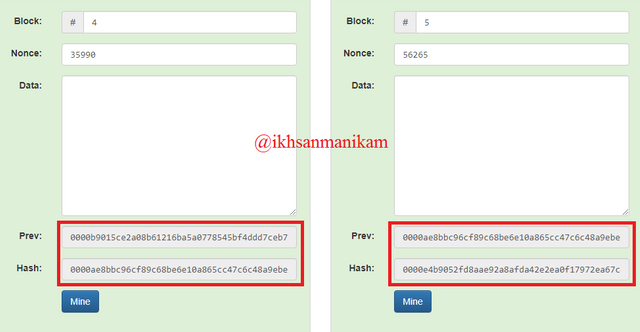
Block 4
Nonce: 35990
Data:
Previous Hash:
0000b9015ce2a08b61216ba5a0778545bf4ddd7ceb7bbd85dd8062b29a9140bf
Hash:
0000ae8bbc96cf89c68be6e10a865cc47c6c48a9ebec3c6cad729646cefaef83
Block 5
Nonce: 56265
Data:
Previous Hash:
0000ae8bbc96cf89c68be6e10a865cc47c6c48a9ebec3c6cad729646cefaef83
Hash:
0000e4b9052fd8aae92a8afda42e2ea0f17972ea67cead67352e74dd6f7d217c
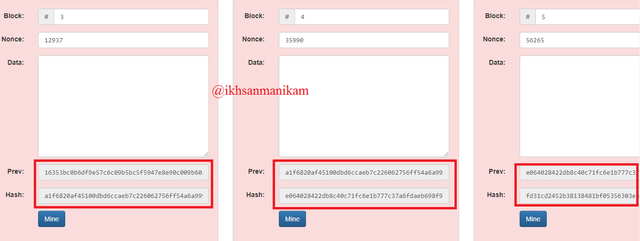
Based on these details and the appearance of the two images above, it shows a Blockchain consisting of 5 blocks and each block has a block number, nonce, data, previous hash, and hash. The blocks will be connected to each other based on the previous hash and this process continues. Block 1 becomes the first block on the Blockchain network or usually referred to as the Genesis Block so that the previous hash of Block 1 is 0, while the previous hash of Block 2 is the hash of Block 1, the previous hash of Block 3 is the hash of Block 2, and so on for next. That way, every Block contained in the Blockchain network will be connected to each other of course.
Add Data to a Block in Blockchain
In the previous illustration, there is no data that is filled in the "Data" column so that there is no data stored in the Block. Now we will try to input new data to be stored in Block.
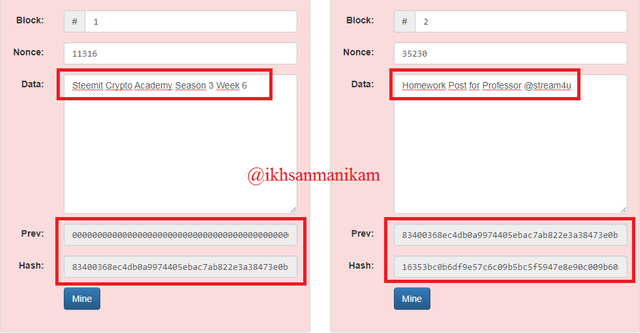
Block 1
Nonce: 11316
Data:
Steemit Crypto Academy Season 3 Week 6
Previous Hash:
0000000000000000000000000000000000000000000000000000000000000000
Hash:
83400368ec4db0a9974405ebac7ab822e3a38473e0b567f5c7c375a2cdffa475
Block 2
Nonce: 35230
Data:
Homework Post for Professor@stream4u
Previous Hash:
83400368ec4db0a9974405ebac7ab822e3a38473e0b567f5c7c375a2cdffa475
Hash:
16353bc0b6df9e57c6c09b5bc5f5947e8e90c009b60a1fc9ba24f7eec3ecbff5
Block 3
Nonce: 12937
Data:
Previous Hash:
16353bc0b6df9e57c6c09b5bc5f5947e8e90c009b60a1fc9ba24f7eec3ecbff5
Hash:
a1f6820af45100dbd6ccaeb7c226062756ff54a6a99974513035cf15c1ce1cb4
Block 4
Nonce: 35990
Data:
Previous Hash:
a1f6820af45100dbd6ccaeb7c226062756ff54a6a99974513035cf15c1ce1cb4
Hash:
e064028422db8c40c71fc6e1b777c37a6fdaeb698f9224bb251ed0df5cc20c0e
Block 5
Nonce: 56265
Data:
Previous Hash:
e064028422db8c40c71fc6e1b777c37a6fdaeb698f9224bb251ed0df5cc20c0e
Hash:
fd31cd2452b38138481bf05356303ea680b687768d4bf9d509f17c68d66de140
In the picture it can be seen that I have entered new data on Block 1 and Block 2. Then we will focus on the hash column, the data change turns out to make the hash in Block 1, Block 2 and so on also change automatically and now all the Blocks have been changed and has a new hash. With a little change like this, all Blocks will also experience changes because every Block in the Blockchain network is connected to each other. When the change occurs, the Distributed Ledger will also distribute the new copy to all Nodes connected to the network.
Mining a Block in Blockchain
Using high computing power tools, miners will validate the Blocks on the Blockchain and this is done by specifying the correct nonce value on a Block, a valid Block hash always starts with “0000”. Here are some experiments showing invalid Block hashes on Block 1.
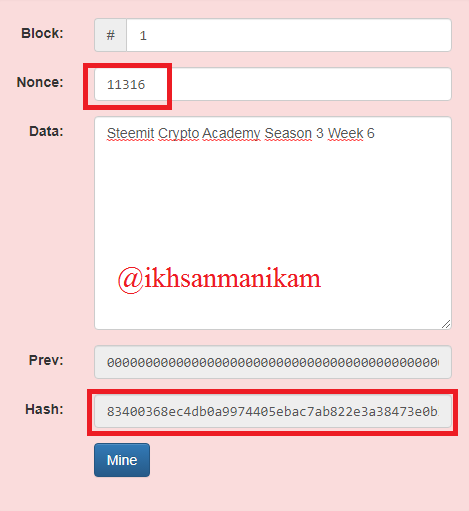
Block 1
Nonce: 11316
Data:
Steemit Crypto Academy Season 3 Week 6
Previous Hash:
0000000000000000000000000000000000000000000000000000000000000000
Hash:
83400368ec4db0a9974405ebac7ab822e3a38473e0b567f5c7c375a2cdffa475
In the picture above, it can be seen that the Block hash in Block 1 is invalid. Then we will try to change the nonce value to 11315.
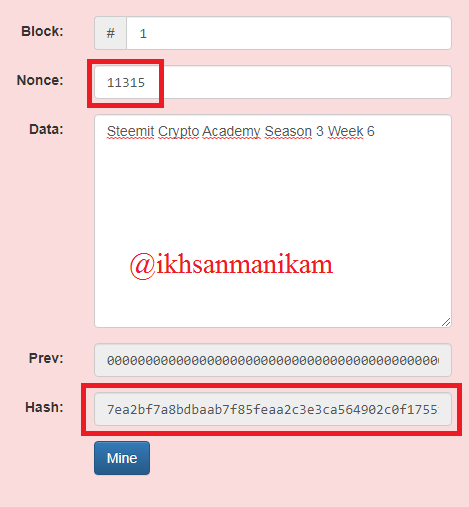
Block 1
Nonce: 11315
Data:
Steemit Crypto Academy Season 3 Week 6
Previous Hash:
0000000000000000000000000000000000000000000000000000000000000000
Hash:
7ea2bf7a8bdbaab7f85feaa2c3e3ca564902c0f1755195eec3ab2adbe717e8a8
After trying to change the nonce value, it turns out that the Block hash in Block 1 is not valid either. Then we will try to change the nonce value again to 11317.
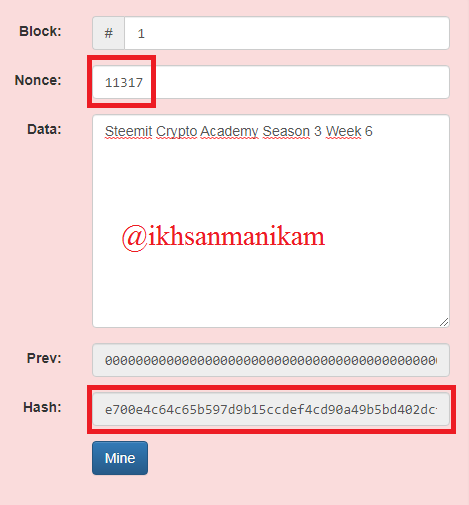
Block 1
Nonce: 11317
Data:
Steemit Crypto Academy Season 3 Week 6
Previous Hash:
0000000000000000000000000000000000000000000000000000000000000000
Hash:
e700e4c64c65b597d9b15ccdef4cd90a49b5bd402dcf2e48a22a4d4080e26acc
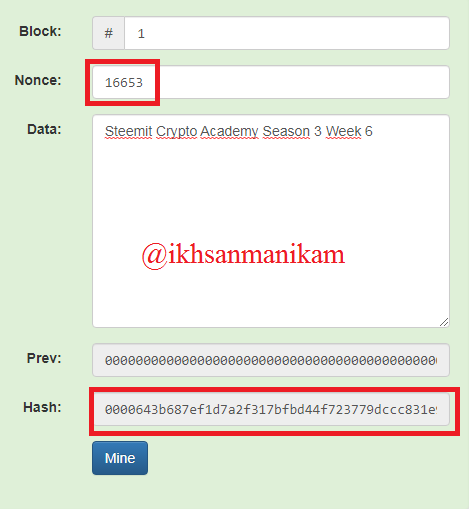
Based on the picture above, it turns out that we have not succeeded either and this process will continue until the correct nonce value is determined, but in this illustration we only need to press the “Mine” button to complete this operation. As in the following image.
Block 1
Nonce: 16653
Data:
Steemit Crypto Academy Season 3 Week 6
Previous Hash:
0000000000000000000000000000000000000000000000000000000000000000
Hash:
0000643b687ef1d7a2f317bfbd44f723779dccc831e92673884450bcc05843ae
Based on the picture above, we can now confirm that Block 1 has been successfully validated because the hash value in the Block is already valid and also starts with the number "0000". It turns out that the correct nonce value in this case is 16653. Using the same method, we can now validate the second Block, the third Block and so on.
For additional information about this, you can also visit one of my other posts on Link to Post.

Q6.) What Is Race Attack in blockchain?
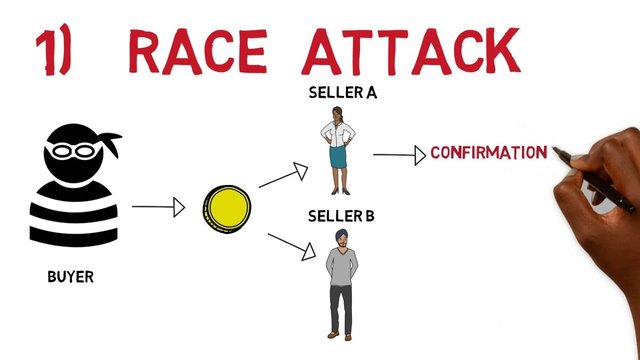
Race Attack is a type of Double-Spending Attack launched by hackers onto the Blockchain network to trick the system quickly. By using different Nodes, hackers will send the same coin to a number of different users quickly. That way, hackers can buy multiple coins using just one coin.
When hackers make several transactions on the Blockchain, the mining process will validate one transaction and cancel the other transaction so that the invalid transaction will be deleted automatically. This attack is generally successful if the buyer accepts the transaction without waiting for confirmation first and to prevent this we should wait for full confirmation from the miners before releasing the purchased asset.
As a simple illustration we will imagine that a hacker who owns 0.36 BTC then sends it to six different individuals on the Blockchain using different Nodes to complete payment transactions and when one of the sellers releases his assets while the transaction has not been fully confirmed by the miners then the seller loses his assets without getting any payment because the miners will only validate one transaction out of the six transactions and the rest will be automatically cancelled.

Q7.) Limitations/disadvantages of Blockchain

After discussing the various advantages in the previous question, to compare them we also need to know the various disadvantages, here are some Blockchain shortcomings that may need to be considered.
- Scalability, the number of connected Nodes is increasing every time so that the processing speed decreases and greatly affects the performance of the Blockchain.
- Irreversibility, transaction records cannot be changed and users can lose their money in case of wrong transactions because there is no way to reverse transactions that have already occurred and you need to be careful beforehand.
- Hacking, there is a possible hacking threat even if it is in a small potential.
- Mining Cost, it takes a number of devices with high computing power and all of that requires a large cost of course.
- Maintenance Cost, to obtain a faster data transmission, higher bandwidth is required with no small cost.
- High Resources, it takes a large amount of electricity to run it, with expensive electricity costs of course, and can have an impact on the environment.

Blockchain technology has succeeded in bringing rapid progress in technological development, especially the cryptocurrency ecosystem. Blockchain technology is able to present a system with a high level of security and is more transparent. By using DLT (Distributed Ledger Technology) technology, every data from various transaction details that occur on the Blockchain will be stored permanently on the network and then a copy will be made for distribution to all Nodes connected to the network, and all of that can run automatically. .
Using a decentralized system makes Blockchain very difficult to hack, but this potential will always be there even if it is less likely to happen. Every transaction made on the Blockchain network must also be validated and confirmed before being added to the block. Blockchain also uses Hash as a cryptographic function and this is almost impossible to manipulate. In addition, user privacy is also highly guarded here.
Last word, thank you Professor @stream4u who has shared interesting lessons that are very useful this week and increase my knowledge of course as a student at this academy.
See you....
Hi @ikhsanmanikam
Thank you for joining The Steemit Crypto Academy Courses and participated in the Homework Task.
Total | 8/10
Your Homework Task verification has been done by @Stream4u, hope you have enjoyed and learned something new.
Thank You.

@stream4u
Crypto Professors : Steemit Crypto Academy
#affable