The Steemit Crypto Academy Week 5: All About Blockchain Security


Course Outline
Introduction
Wallet Security
- Private Key
Digital Signature
Basics of Cryptojacking
- How to detect and prevent Cryptojacking
Dusting Attack
Denial of Service Attack (DoS Attack)
Distributed Denail of Service Attack (DDoS Attack)
Eclipse Attack
Conclusion
Task

Introduction
Since the blockchain is decentralized, there is no central government that controls the activities on it, neither is there a middle man to be held responsible for any flaws (if they occur), which means that we are all responsible for our security as individuals and as entities.
It is true that the blockchain is secured, thanks to cryptography, decentralization, and consensus, but then, there are several security attacks on both individual and corporate entities thereby causing so many people to be vulnerable. Securing a network and wallet is important on the blockchain and in this class, I will be explaining security on the Blockchain in full. My name still remains @gbenga, and I am your distinguished professor for this class.


Wallet Security
Your safety in the cryptocurrency world as a user starts with your wallet. A wallet is an app where crypto assets are kept and it can interact with the blockchain at all times 1. Wallets could be custodial or non-custodial, with custodial wallets being wallets that the private key is kept by a third party (especially exchanges) while non-custodial wallets are wallets whose private keys are kept by the owner of the wallet 2. Hardware wallets, software wallets, mobile wallets, paper wallets, and multi-sign wallets, all fall into one of the following; custodial or non-custodial wallets.
You would have noticed that in the explanation above, one thing keeps coming up and that is the Private key. What are private keys?
Private Key
A private key as the name implies, is a set of alphanumeric cryptographic digits which serves as an authority to perform transactions. It is referred to as private because it is should be kept as personal property. For security purposes, the private key is used to prevent theft from unauthorized access to funds 3. Other security features to keep your wallet safe include seed phrases, and mnemonics.

Digital Signature

Just like your handwritten signature is needed to approve withdrawals of funds on your account, so is a digital signature required to approve transactions. Digital Signatures are cryptographic fingerprints or signatures used to approve transactions on the blockchain. Digital signatures are important for data integrity, authenticity, and non-repudiation 4

Security on the blockchain goes beyond keeping your private key, mnemonic, or seed phrase safe from another user, it goes down to securing your computer, the network, and so on. So, let's do justice to the topic "All About Blockchain Security"

Basics of Cryptojacking
Would you have ever thought that someone could be using your computer power to mine cryptocurrency without your approval or you knowing about it? Cryptojacking is the unauthorized use of an infected computer through malicious ways by cybercriminals to mine cryptocurrencies without the knowledge of the victim 5. This is often achieved by tricking the victim install software into their computer. The software uses the computing power of the computer to mine cryptocurrency.
This is often achieved when victims click on phishing links which allows them to install the mining code which runs a crypto mining script on the computer. Another way is to inject the script on ads, and once the victim clicks on the ads, the script automatically begins to work and mining occurs without the knowledge of the victim.
How to detect and prevent Cryptojacking

As usual, it is better to prevent than to cure, and in preventing yourself or your organization from being a prey to cryptojacking, you have to do the following thing;
- Download an ads blocker
- Do not click on links you are not certain about.
- Limit chats with people you are not familiar with but come with a profitable link to click on
- Do not download applications that are not from a trusted source.
- If you are not using your computer for any form of crypto mining, then you can download an anti-crypto mining extension on your web browser
- Disabling Java script while browsing is another way to prevent cryptojacking.
We can never be too careful and in some cases, people can fall victims to crypto-jacking and when this happens, it is best to find a solution to it. Detecting crypto-jacking can be very difficult and when not detected, it could cause a lot of loss for both individuals and organizations. There are a few ways to detect cryptojacking and they include;
- Overheating
- Decrease in Performance
- Increase in CPU usage
- Using artificial intelligence such as SecB to detect cryptojacking
After detecting, the next step is to find a solution and in doing that, a few steps can be taking such as;
- Delete script related to cryptojacking
- Block website-delivered scripts on your browser.
- Update the browser being infected or the operating system being infected.

Dusting Attack

Have you received tiny amounts of crypto assets in your wallet and you become really happy? With Dusting Attack, cyber attackers send a tiny amount of coins to wallets and use this tiny asset is traced along with the other coins so as to determine the owner of the wallet. If you have a wallet with little funds, you might notice the transfer but for wallets with large funds, they would not notice this tiny amount of funds. After sending the tiny funds, the cyber attackers start to monitor the transfers done on these wallets to identify the owners of the wallet. Once the owners of these wallets are identified, phishing links are sent to the wallet owners 6

Denial of Service Attack (DoS Attack)
This is an attack by cyber attackers on a network or web thereby hindering the use of the service provided by the network or web. DoS requires overloading the network with excessive requests thereby making the service misbehave or crash.
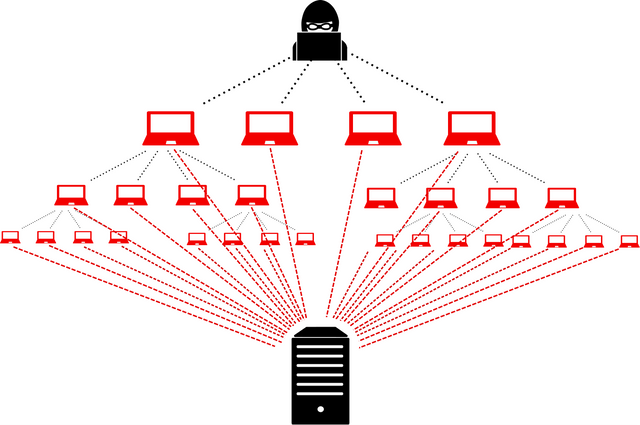
Distributed Denial of Service Attack (DoS Attack)
Unlike the DoS, DDoS is an attack on a service from several malicious sources instead of from one source. DDoS has been very common in the cryptocurrency world, although it cannot change transactions on the chain, it can affect servers of companies that utilizes the blockchain. eg, crypto exchanges.

Eclipse Attack
There have been several attacks trying to break decentralization and Eclipse Attack is one of them. With Eclipse attack, certain nodes are attacked/isolated thereby preventing them from seeing the real chain and activities going on them. The major purpose of eclipse attack is aimed at double spending there are two types of double spendings; 0-confirmation double spends, and N-confirmation double spends. With doubble spending, attackers are able to profit from the Eclipse attack 7.
With double spending and Eclipse attack, an attacker can isolate a node and then send coins to both the running nodes and the isolated nodes at the same time thereby causing double spending. In cases where the transaction needs immediate conversion for other coins, the attacker sends the double spent coin and if the victim doesn't wait for confirmations, the coin doesn't get confirmed and cancelled as other active nodes will correct the eclipsed node.

Conclusion
Individuals and enterprises need to keep their wallets, servers, nodes, and platforms safe from attackers, there are malicious attackers everywhere. For individuals, keeping your private key, mnemonic and seed phrase is a major security safety tip but there are more things to keep safe in other not to lose our funds to attackers.

Task
The Rules
- Everyone is eligible to participate in this task.
- The Post should be a minimum of 300 words and should be submitted in the crypto-academy community for visibility.
- You should include the exclusive tag #gbenga-week5, #cryptoacademy, and a tag of your country (for example #nigeria).
- Post should be your original content. Show references for images used when writing your post.
- Task runs until Sunday, March 14th, 2021

Hello again @gbenga, this is my post and task of the week. Sorry for delay, I had some internet problems at home this week.
https://steemit.com/hive-108451/@allbert/the-steemit-crypto-academy-week-5-gbenga-all-about-blockchain-security-security-problem-with-cryptocurrency
Thanks professor @gbenga. Your lecture was a great one. I present my entry link below. Thank you, sir.
https://steemit.com/hive-108451/@fredquantum/steemit-crypto-academy-week-5-task-all-about-blockchain-security-security-problem-with-cryptocurrency-or-lecture-by-gbenga
Hello, @gbenga, my homework has been pending for days without any review. Thanks.
https://steemit.com/hive-108451/@xkool24/crypto-academy-week-5-homework-task-or-or-lecture-by-professor-gbenga-or-or-done-by-xkool24-or-or
Dear professor @gbenga, I've submitted my task 5 link for review earlier a few days ago. This is to remind you about it again. Thank you sir.
https://steemit.com/hive-108451/@fredquantum/steemit-crypto-academy-week-5-task-all-about-blockchain-security-security-problem-with-cryptocurrency-or-lecture-by-gbenga
Here is my task
https://steemit.com/hive-108451/@okoyejoshua/crypto-academy-week-5-homework-post-for-gbenga
Professor please review my post
hello sir here is my homework a bit late but done thaks for class
waiting for next week
https://steemit.com/hive-108451/@azizulhassan/steem-crypto-academy-week-5-homework-post-for-gbenga-by-azizulhassan
https://steemit.com/hive-108451/@akashhassan/steem-crypto-academy-week-5-homework-post-for-gbenga-by-akashhassan
this is my homework
Dear sir @gbenga my home work is here
https://steemit.com/hive-108451/@steemlover63/home-task-week-5-for-prof-gbenga-or-or-security-problems-with-cryptocurriencies
Please visit my post and check it out.
Hello teacher my Homewook number 5
https://steemit.com/hive-108451/@yorma/publicacion-de-la-tarea-de-la-semana-5-de-cryptoacademy-para-gbenga
Good evening @ gbenga my task week 4 assignment hasn't been reviewed. How will i know am doing well. It should. Here is the link
https://steemit.com/hive-108451/@jennykel56/cryptoacademy-week-4-homework-post-for-gbenga-of-cryptoprofessor-submitted-by-jennykel56
Will submit week 5 later am on it.
Thank you prof