Crypto Academy / Season 3 / Week 8 - Homework Post for Professor [@stream4u] : Advanced Course : Let's Open The CryptoGraphy
This is my homework post for Steemit Crypto Academy Season 3 Week 8 for Professor @stream4u’s lesson Let's Open The CryptoGraphy.

TASK 1
1.a. The Blockchain CryptoGraphy Explanation
1.b. Examples of Blockchain
1.a. The Blockchain CryptoGraphy
1.a.1. A Brief History of Cryptography
Literally, "cryptography" can be interpreted as the science and practice of keeping secrets (maintaining the confidentiality) of a data or document. In cryptography, maintaining data secrets is done by changing the entire information in a data (whether in the form of writing, pictures, sounds, etc.) into a series of other information that is completely different and random so that unauthorized people are not expected to understand it, and only those who entitled and have a code or key that can translate it back.
Cryptography technology has experienced a long historical journey and continues to evolve with the times. The history of cryptography can be traced to 400 BC in the heyday of the Ancient Greek Empire. The Greeks at that time had a tool called Scytale to create encrypted messages. Scytale is a cylindrical ingot, has a combination of 18 letters.

Cryptography was also used intensely during the reign of Julius Caesar in the Roman Empire. The Romans used encryption techniques that were not as complex as those used by the Greeks, but deciphering messages from the Roman system was said to be very difficult.
In the second world war, the cryptography system built by NAZI Germany has become so famous, even to this day. They created a typewriter-like machine that scrambled each typed message into a series of unread messages. The machine was called the Enigma. To decipher the message, it required the correct cipher to be entered into another Enigma machine (the "translator" one) before retyping the random set of messages to generate the actual message.

The main goal of cryptography, whatever era it comes from, is to protect sensitive, confidential information from the reach of uninterested people, or adversaries. In terms of statehood, this means maintaining the security and stability of the state.
1.a.2. Cryptography in Blockchain
The principle of benefits and how Cryptography works is also the same in the Blockchain world. Blockchain technology as a distributed digital ledger adopts cryptography to provide security to everyone who uses the technology. This is done so that data cannot be changed easily, and thereby guarantees the rights of every user are fulfilled.
Blockchain secures every data by using a technology called Hash Function. Hash Function, functionally, is practically the same as the Scytale used by the Ancient Greeks or the Nazi Enygma machine. The difference:
- in the form of technology, the Hash Function is in digital form, while Scytale and Enygma have a physical form, and
- the Hash Function is a one-way function, which means there is no way to decrypt the hash into the original message. By this, the original message will never be altered, unless all users agree to do so.
The diagram in the following figure will simplify the way we understand cryptography in blockchain.
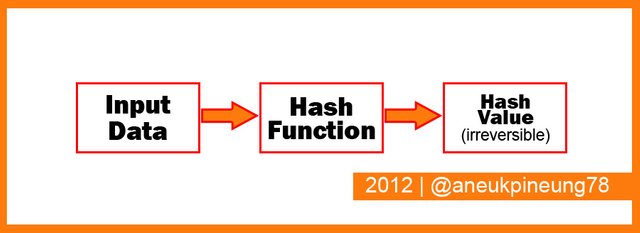
Examples of cryptographic algorithms that use hash functions:
- MD2, MD4, MD5. (MD is short for Message Digest).
- Secure Hash Function (SHA). This might be the popular one.
- Snefru.
- N-hash.
- RIPE-MD (MD is short for Message Digest).
-----oOo-----
1.b. Examples of Blockchain Platform
Since blockchain technology was introduced into practice in 2008, we have witnessed rapid developments in this technology. There have been a lot of blockchain platforms available to date with a variety of uniqueness of each. Some are public blockchains, some are private blockchains. Some blockchain platforms are engaged in cryptocurrencies such as Bitcoin. Others are not, for example, IBM Blockchain, which until now has only developed platform technology for public use and does not have its own token. Others are engaged in cryptocurrency (having native tokens) and also developing technology for other needs, an example of this type of platform is Cardano which has a native coin with the symbol ADA.
Here are examples of some blockchain platforms.
- 1.b.1. Bitcoin Blockchain: The Father of All Blockchains
When we talk about blockchain technology and related topics, we shouldn't forget the very first Blockchain platform has ever been established: the Bitcoin blockchain.

Bitcoin logo as seen here.
The domain, bitcoin.org was registered on August 18th 2008 by someone named Satoshi Nakamoto. Five months later, on January 3rd 2009, Bitcoin was mined for the first time. This first block is then known as Bitcoin block 0 or Bitcoin Genesis Block. The second block began to be mined on January 9th 2009 (six days after the first block). The second block is called Block 1.
Bitcoin Blockchain is a cryptocurrency blockchain with a native token called Bitcoin symbolized by BTC. - 1.b.2. Ethereum: Popular and "Busy"
Ethereum is a second generation blockchain platform. Ethereum is arguably the most popular and “busy” blockchain network. Many blockchain-related projects have been built on it. The website is at https://ethereum.org/en/.
Ethereum was developed by a programmer named Vitalik Buterin in 2013 with four other people: Charles Hoskinson, Anthony Di Iorio, Amir Chetrit, and Mihai Alisie. They are the initial five developer of Ethereum. Later, some other programmers joined this project, Hoskinson left to develop Cardano (ADA).

Ethereum logo as seen here.
Crowdfunding was carried out in the following year, 2014. Network went live on July 30th 2015 with the launch code name Frontier. Since Frontier, twelve protocol upgrades have been carried out, the last one was on August 5th 2021, code-named London.
Ethereum Blockchain is a cryptocurrency blockchain with a native token called Ethereum symbolized by ETH. - 1.b.3. IBM Blockchain: Blockchain of the Pioneer Company
IBM Blockchain is a blockchain platform developed by renowned computer hardware company IBM (International Business Machines Corporation). The website is accessible here.

IBM Blockchain picture as seen here.
IBM Blockchain is a blockchain platform that frees its users to do almost unlimited customization to support their interests. This platform is open-source and community-based. Several articles on the internet have named IBM Blockchain as one of the top ten blockchain platforms to be reckoned with.
IBM Blockchain is not a cryptocurrency blockchain, that's why it does not have any token. - 1.b.4. TRON: Better Rewarding System and Value for Content Producers
TRON was established in 2017. It was founded by Justin Sun under currently Singapore-based non-provit organization TRON Foundation, where Justin is the CEO. Tron was first listed on the CoinMarketCap crypto asset market on September 13, 2017 with an initial price of US$0.002. On that day the trading volume was USD48,512.

Tron logo picture as seen here.
The main goal of the TRON blockchain is to develop a technology that will help content creators get better rewards for their works. This platform also allows users to have full control over the data they have, so that data leaks can be avoided.
TRON Blockchain has a native token called TRONIX symbolized by TRX. - 1.b.5. Quorum: An Ethereum Customized Blockchain
JPMorgan, a well-known financial service company, established this platform in 2015. Quorum is a customized version derived from Ethereum. The core work on the Ethereum blockchain platform has been the advantages that was taken to build a hardened environment that suitable for banks, in which has been optimized to support high speed transaction on private networks like insurance companies and banks.

ConsenSys Quorum logo as seen here.
Unlike Ethereum, Quorum does not use the Proof of Work (PoW) consensus mechanism to execute thousands of operations per second, but instead uses vote-based methods and other techniques.
In August 2020, a New York-based Ethereum venture studio, ConsenSys has acquired Quorum.
Quorum Blockchain is not a cryptocurrency blockchain, it does not have any token. - And there are so many more blockchain platforms available these days, each with their uniqueness in characteristic, purposes, development.

TASK 2
The Public Key CryptoGraphy
Public Key Cryptography is the practice of cryptography that uses two keys, namely the Public Key and the Private Key. The Public Key as the name implies is a key that can be known by the public, while the Private Key is not.
In Public Key Cryptography, the Public Key is used to encrypt data, and the Private Key is used to decrypt the data. An encrypted data can only be decrypted with a private key that matches the public key used for encryption. A Public Key always has a Private Key as its pair: a Public Key A is paired with Private Key A and so on. There is impossible using Private Key A to decrypt the data encrypted with Public Key B.
The working scheme of Public Key Cryptography can be explained in the following figure.
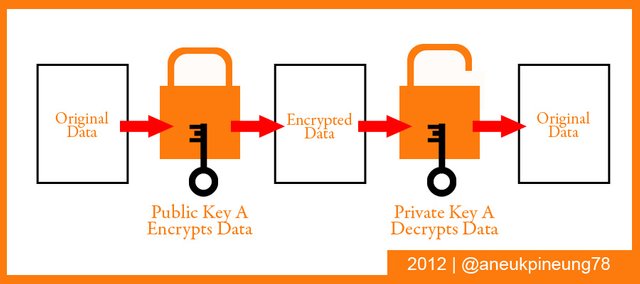

TASK 3
The Private Key CryptoGraphy
Private Key Cryptography uses only one single private key to encrypt and decrypt data. The process of handling data with this method becomes easier and faster, but has a higher risk in terms of security when compared to Public key Cryptography.
The picture below shows the working scheme of Private Key Cryptography.
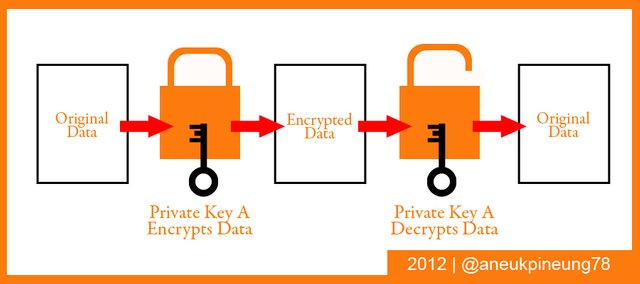

TASK 4
4.a. The Digital Signatures CryptoGraphy
4.b. Signing Of Transaction/Message
4.a. The Digital Signatures CryptoGraphy
Digital Signatures Cryptography is cryptography which uses digital signature to validate data. And what is digital signature?
Digital signature is a cryptographic tool, a mathematical technique used for validating the authenticity and integrity of a digital (or in other word: electronic) message, document, data, and software. Digital signature works based on the public key encryption (public key cryptography) which requires a pair of key (public and private keys) to process. In encrypting a signature-related data, a signer uses a Private Key, and the only thing that is able to decrypt the data is the signer's Public Key (the private key's pair). If the Public Key is not able to decrypt the data, then there is something wrong with the document or the signature.
Digital signature guarantees:
- Message (or data, document, software) integrity, it provide proof that the message (or data, document, software) was not altered after the signing.
- Message (or data, document, software) authentication, it provide proof that the sender (private key owner) has created and signed the Message (or data, document, software).
- Non-repudiation, it guarantees that the signer (sender, private key owner) can never deny the signing once a signature is created.
Digital signatures are now very popular. Some examples of the use of digital signatures are:
- PINs, passwords, codes. The easiest example for this is the equivalent of a username and password when someone wants to login to a site or to an email.
- Cyclic Redundancy Check (CRC). It is a method of detecting changes to raw data.
- Certificate Authority (CA) validation. CA is a third party that issues digital certificates and ensures their authenticity so as to avoid counterfeiting.
Below is the simple diagram to describe how digital signature works.
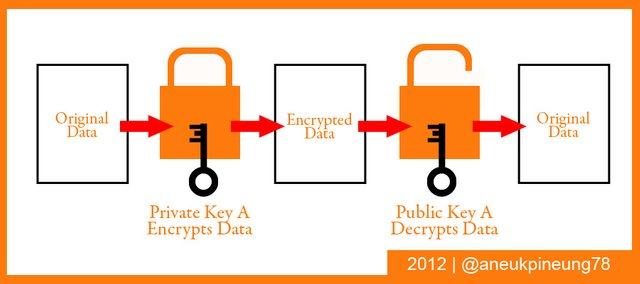
-----oOo-----
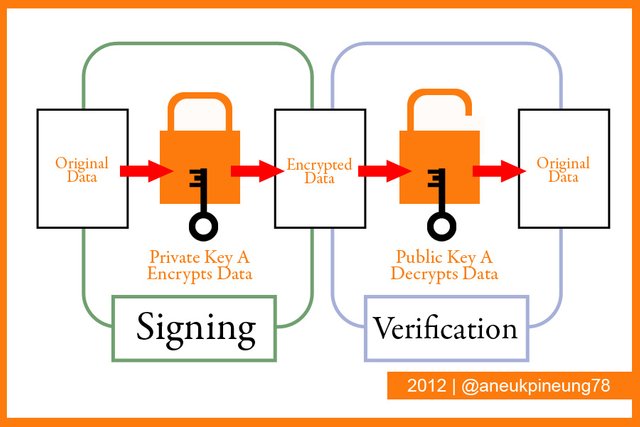
4.b. Signing Of Transaction/Message
Transaction/message signing is when someone encrypts a message (or data, document, software) using a private key. Meanwhile, the process of decrypting messages (or data, documents, software) using the correspondence public key is called "transaction/message verification".

TASK 5
Symmetric and Asymmetric Cryptography
Symmetric Cryptography (also called Symmetric Encryption) is a cryptographic method that uses an identical private key to encrypt and decrypt messages (or data, documents, software). The sender and receiver must both have the same Private Key. Another name for Symmetric Cryptography is Private Key Cryptography (or Private Key Encryption).
Meanwhile, Asymmetric Cryptography (also known as Asymmetric Encryption) is a cryptographic method that uses two different (asymmetric) keys to encrypt and decrypt data (or messages, documents, software), namely a pair of Private Key and Public Key. If the Private Key is used to encrypt data (as in digital signature cryptography), then the Public Key will be useful for verifying the data. And if the Public Key is used to encrypt the data, then the correspondence Private Key is used to decrypt it. Asymmetric cryptography is also known as Public Key Cryptography (or Public Key Encryption).

TASK 6
6.a. How Blockchain Wallets CryptoGraphy Works
6.b. Available Types Of Crypto Wallets
6.a. How Blockchain Wallets CryptoGraphy Works
Every blockchain wallet (or crypto wallet) has one pair of key consisting of one Public Key and one Private Key.
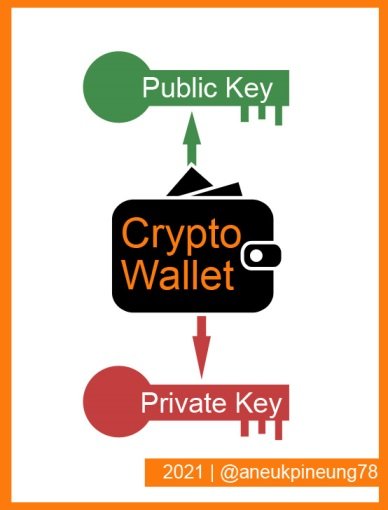
- Public Key, is a crypto wallet address that can be publicly shared and everyone can send the relevant token (crypto money) into it. It's like an email address that you can share with your friends so they can send you electronic mails whenever they need to.
- Private Key, is a password that allows the wallet owner to reach the funds stored in it. Private Key is confidential. If your wallet public key is like an email address, then the private key is like its password.
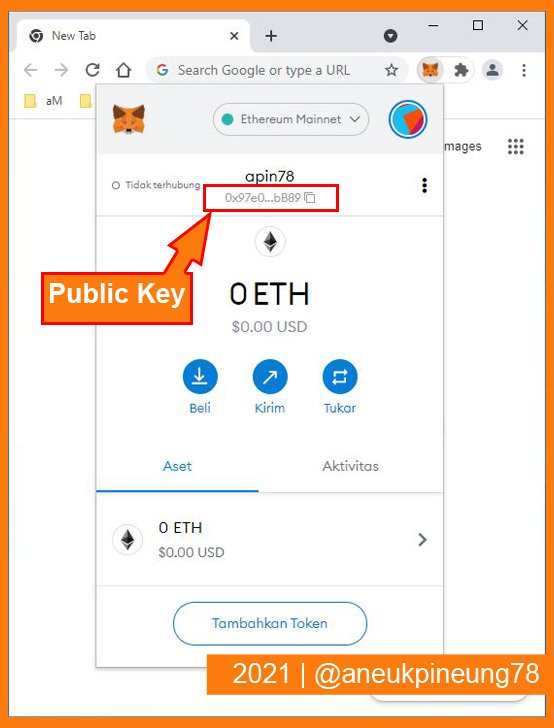
An example of how Crypto Wallet works: a friend of mine wants to send me some Ether (ETH), I give him my MetaMask Public Key (address) which is 0x97e036Cd4b72dC97189e338A33a36Be56E90bB89, after he gets my MetaMask Public Key then he can send the Ether. When I want to use the Ether in my MetaMask wallet to pay for something, I use my MetaMask Private Key to access it.
In addition to the Public Key and Private Key, there are also Token addresses, such as Bitcoin addresses or Ether addresses. Token addresses are usually given by crypto exchanges. The token addresses are public, can be distributed to anyone. People can send relevant tokens to the token addresses, for example, Bitcoin addresses can only receive Bitcoin and Ether addresses can only receive Ether.
-----oOo-----
6.b. Available Types Of Crypto Wallets
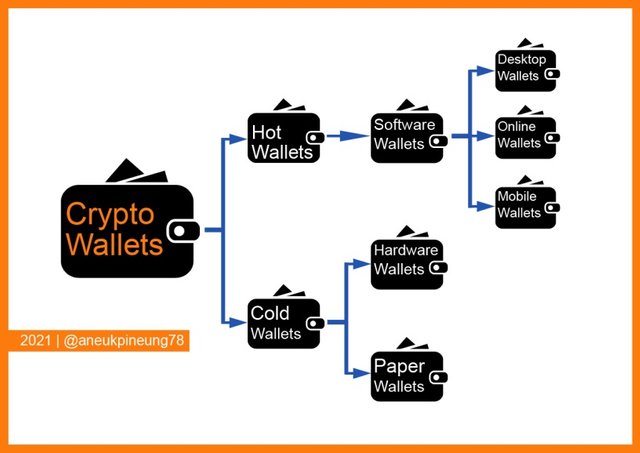
Broadly speaking, Crypto Wallets can be categorized based on internet connectivity and forms:
- Based on connectivity with the internet, there are two categories:
- Hot Wallets: wallets connected to the internet. Private keys are stored on the internet so they can make transactions faster, but have a risk of hacker attacks;
- Cold Wallets: wallets that are not connected to the internet, transactions are signed offline before being executed online, cold wallets are better than hot wallets in terms of security.
- Based on their forms, crypto wallets are divided into three types:
- Software Wallets; is software that can be installed on electronic devices such as PCs, laptops, or mobile devices (smartphones, tablets). In addition, included in this type are web-based wallets. Software Wallets are divided into three types:
1.1) Desktop Wallets, included in the Cold Wallets category, these wallets private keys are stored on a cold-server (on a computer), transactions can be done offline by unplugging the Private Key from the internet and after that it can be authorized online by re-connecting Private Key to the internet. When not in used, it can be disconnected from the internet. Most popular example: Electrum wallet.
1.2) Online Wallets, included in the Hot Wallet category (the wallets that are connected to the internet). This type of wallet can be accessed from various devices: laptops, PCs, tablets, smartphones. An example of this type of wallet is GreenAddress (Bitcoin wallet) which has a web version, Android OS, Windows, and iOS.
1.3) Mobile Wallets, is a type of online wallet but is only available for mobile phone devices. An example is Mycelium. - Hardware Wallets, included in the Cold Wallet category. Hardware wallets are in the form of storage devices in which the user's private keys are stored. This is similar to External Hard Disk Drives that can be connected to computers via a specific port (usually USB). Hardware Wallets that are famous today are: Trezor, KeepKey, and Ledger. Hardware Wallets must be connected to a computer device before they can be used to make transactions.
- Paper Wallets, as the name implies are a piece of paper on which a pair of Private Key and Public Key are printed in the form of a QR Code. Paper Wallets are used in the offline cryptocurrency storage process. Funds stored in the software wallet can be sent to a paper wallet by scanning the QR Code.
- Software Wallets; is software that can be installed on electronic devices such as PCs, laptops, or mobile devices (smartphones, tablets). In addition, included in this type are web-based wallets. Software Wallets are divided into three types:

TASK 7
7.a. What is Merkle Trees
7.b. What is Its Importance In Blockchain
7.a. What is Merkle Trees
Merkle Trees is a data structure system used in decentralized networks. Merkel trees help verify large amounts of data efficiently and consistently. In a centralized system, data can be accessed and verified from one copy (or source), but this is not the case in a decentralized system where each node has one copy of each data. That's where Merkel Tree comes in handy: share data, verify and certify it, efficiently and consistently.
Merkle Trees use hash functions and cryptographic techniques so that they can also facilitate transactions securely. In blockchain technology, Merkle Trees have been used since the beginning of blockchain history, namely when Satoshi Nakamoto used Merkle Tree in the blockchain of his creation: Bitcoin, the world's first blockchain ever.
In Merkle Trees, every transaction is encrypted with a hash function so that it becomes a "leaf". Then a pair of "leaf" is encrypted again using a hash function to obtain an advanced hash. This continues until a single hash is obtained which is called Merkle Root or Root Hash. See the following picture See the following picture, an image that describes simply a Merkle Tree formed from four transactions.
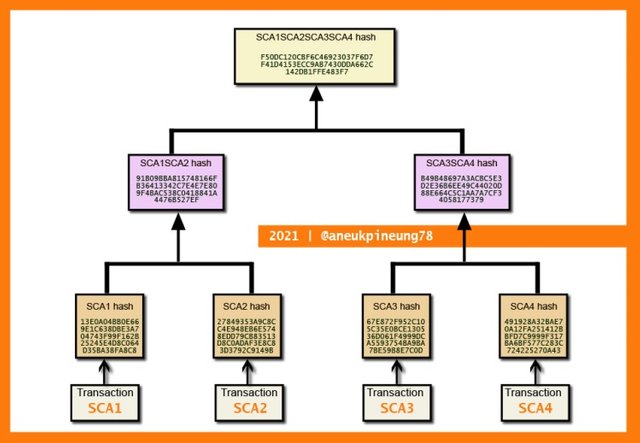
Merkle Trees theory was proposed by Ralph Merkle in his paper " Digital Signature Based on a Conventional Encryption Function" which was published in 1987. Not only Merkle Trees theory, Merkle aslo invented what we call now "cryptographic hashing". Another name for Merkle Trees is "binary hash trees".
-----oOo-----
7.b. What is Its Importance In Blockchain
The Merkle Trees play an important role in the blockchain, because they are useful for:
- blockchain data encoding efficiently and securely.
- recording all the transactions occurred on the blockchain.
- verifying whether a specific transaction was included in a transaction or not, without downloading the entire blockchain.
- data synchronization.
- easily verifying data integrity.
What Merkle Trees do, basically is strengthening the trust on the blockchain. Without trust, there will never be blockchain.

TASK 8
Practical Research on Blockchain Demo and The Functionality of Key, Signature, Transaction, Blockchain
8.a. Key
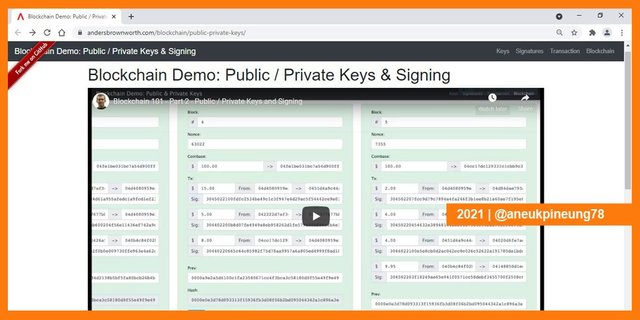
I opened the Blockchain Demo: Public / Private Keys & Signing.
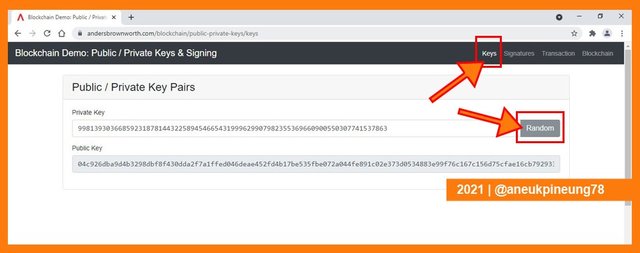
The default page was the [Keys] page as shown on the horizontal menu at the upper right section of the page. The idea was: this is the page of the keys creation. The [Random] button available on the right to Private Key column acted as the keys generator, clicking on it will generate new pair of key (Private Key and Public Key).
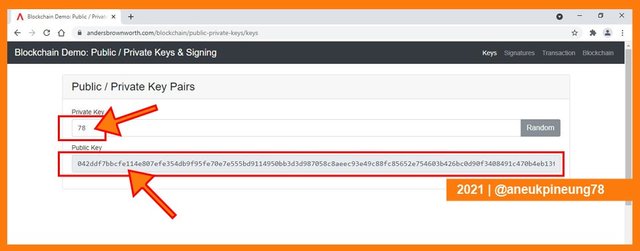
For this task, I typed my own Private Key. Yes it was possible to choose our own Private Key to our like, but the Public Key was not, the Public Key was automatically generated. When I typed it the Public Key was automatically generated and showed in the column. Now I had one pair of keys: Private Key (78) and Public Key (042ddf7bbcfe114e807efe354db9f95fe70e7e555bd9114950bb3d3d987058c8aeec93e49c88fc85652e754603b426bc0d90f3408491c470b4eb13f199399f4ec9). Computer system will always know this pair, each key can never be interchanged with another key.
-----oOo-----
8.b. Signature
The next thing to know was the signature. For this task, the example is I will sign a message. So I clicked on the [Signatures] in the horizontal menu at the top right of the window, and make sure the [Sign] tab was activated.
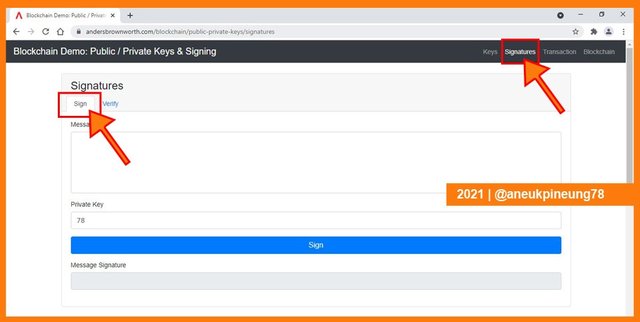
There were three simple steps to follow: 1) Write down the message to send, 2) Fill in the Private Key, and click [Sign] button. There was no recipient, the message would be accessible by and readable to anyone who has the correspondent public key and the signature.
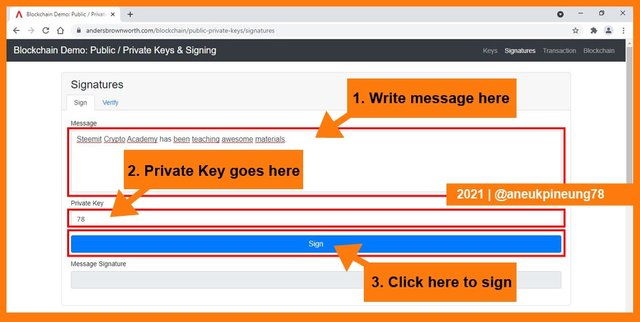
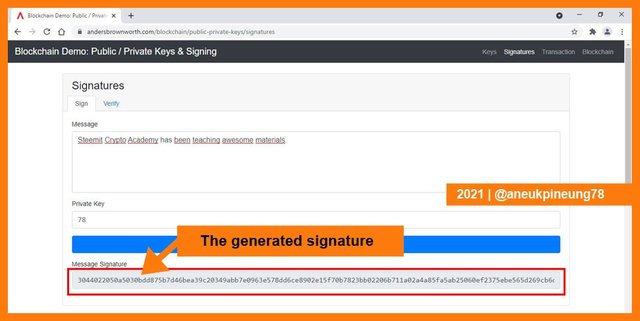
The message signature was generated. This signature is an integral part of the message and the keys used to send the message.
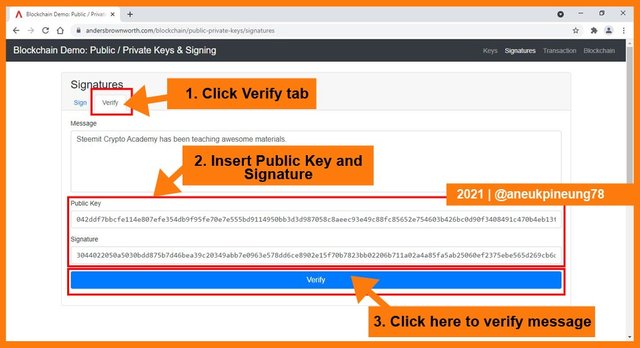
To verify a message, one will need a Public Key and the message signature. To understand this, I clicked the [Verify] tab on the Signatures window. The tab was right on the right side of the [Sign] tab. I inserted the Public Key of the sender, and the message signature. Lastly, I clicked [Verify] button.
The box turned greenish. In this simulation, green means that everything is good, in this case it meant that the message was successfully verified. That the owner of the Private Key has sent the message.
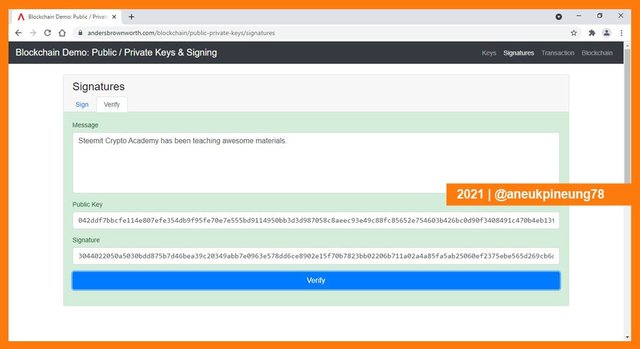
Below is the example of what will happen when not-correspondent Public Key and / or signature is inserted.
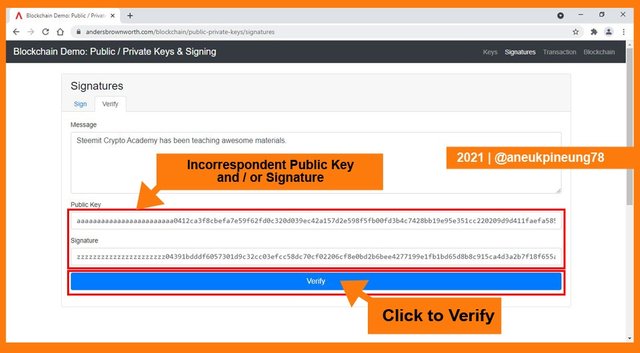
It came back with the reddish box color which meant that there was something wrong whit this message so it was not verified.
-----oOo-----
8.c. Transaction
The next step was to get a picture of how a transaction happened on the blockchain. Transactions on the blockchain can take the form of sending messages or transferring a number of tokens. The transaction must first be signed to send it on the blockchain. To get better knowing about this, I clicked the [Transaction] in the horizontal menu and made sure that the [Sign] tab was chosen. In this example, the transaction was in the form of sending 20 dollar tokens that I (the owner of Private Key 78) made to the owner of the Public Key 04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd9f369dca402d059f396dca402d059f396dca402d9f396. So the steps were: I filled in the amount of the token to be sent, 2) I filled in my Public Key and the recipient's Public Key, 3 I filled in my Private Key as the sender, and I clicked the [Sign] button. In this simulation, all of the necessary information had already been filled, I just needed to click the [Sign] button. I could change some parameters (the token amount and / or the recipient Public Key).
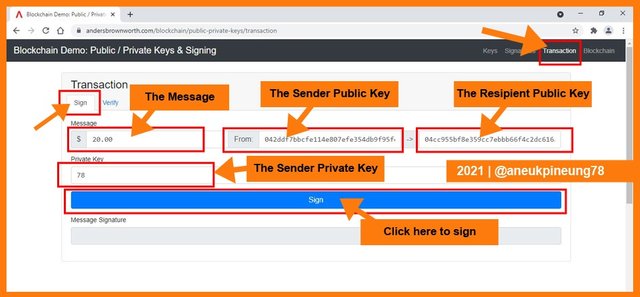
The signature was generated.
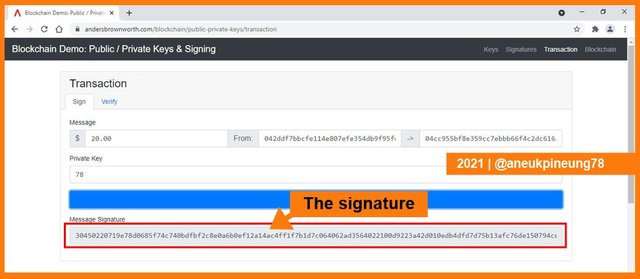
Now to verify the transaction, I clicked the [Verify] tab on the right side of the [Sign] tab. I inserted the relevant information to each column, and clicked [Verify].
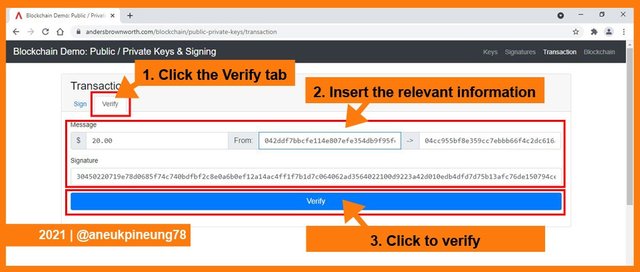
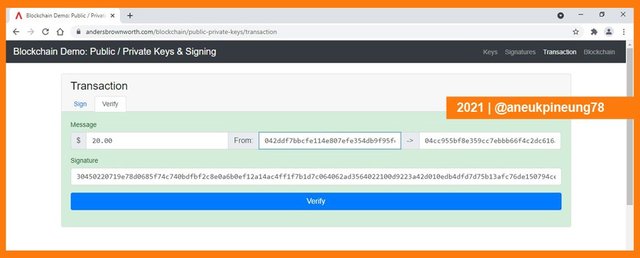
When all data was correspondent, the transaction would be successfully verified. In this simulation, it was shown with the greenish color of the box.
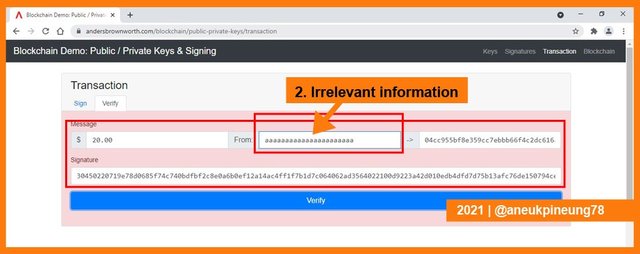
The picture below shows what happen when irrelevant information was inserted. The box turned reddish which meant that something is not right with the information.
-----oOo-----
8.d. Blockchain
The last menu on the andersbrownworth blockchain keys simulation page was Blockchain. Here we will get to know better about what is going on on a blockchain. I clicked Blockchain on the horizontal menu bar at the upper right side of the page.
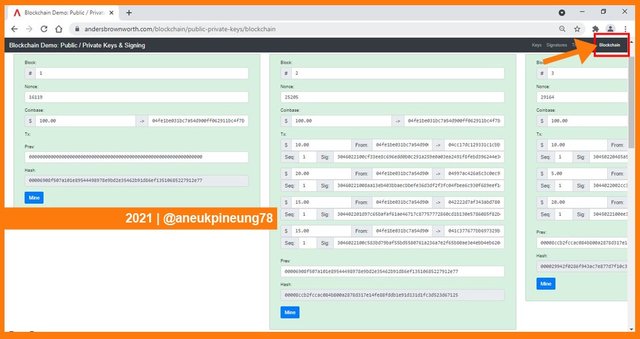
It showed three peers of a blockchain with five block-height. All the blocks had been verified, it was indicated by the greenish box color. The first block was named block #1. Every block contains:
- Block number;
- Nonce; nonce is short for number only used once. This is a number that is added to a hashed block in a blockchain. The miners work to solve mathematical puzzle in order to get this number. Any miner who found this number will be rewarded with token.
- Amount of token sent to block validator (miner) as reward for solving the nonce;
- Block validator's public key;
- Transactions included in it. The transaction was empty (no transaction) in the first block (Genesis block), while block #2 contained 4 transaction, and block #3 and #4 and #5 contained 3, 3, and 4 transactions, respectively.
- Previous hash, since the first block had no previous block, the previous hash was a series of zeros. The first block hash recorded in the second block as the previous hash, and so on for the next available blocks. The hashes are what link each block to the previous and the next block. It is like a chain link.
- The block hash. Current block hash will be recorded as the previous hash in the next block.
When I changed a value in a specific transaction in block #2 of Peer A, the signature turned to red color and the block box turned to reddish color, all the following blocks in Peer A also turned into the reddish color. It means that a change in a block will affect all following blocks.
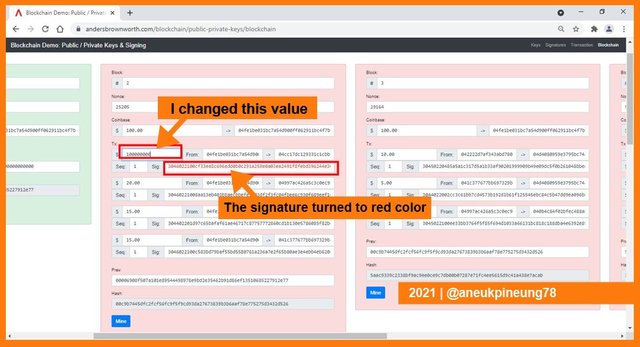
But nothing happened in another two peers (nodes). That showed how the nodes (peers) maintain each block since each block is distributed.
-----oOo-----

TASK 9
Conclusion
From this class, I learned that the most important backbone of blockchain technology is cryptography. Data security is guaranteed primarily by cryptography, and therefore trust is provided between users. Crypto wallet security is also possible with the use of cryptographic technology.
There are two types of cryptography:
- Public Key Cryptography, also known as Public Key Encryption or Asymmetric Cryptography. That is cryptography that uses two different keys (Public Key and Private Key pairs) to encrypt and decrypt messages or transactions.
- Private Key Cryptography, also known as Private Key Encryption, or Symmetric Cryptography. That is cryptography that uses a single key (Private Key) to encrypt and decrypt messages or transactions.
The cryptographic technology used in blockchain makes things like sending messages and digitally signing them easy. Likewise when doing verification. Hash functions help to encode data so that large data can be smaller before being put into a block for verification. Merkle Tree uses hash functions to simplify complex data and encrypts it to be recorded in a block as a block hash. Thanks to the hash algorithm, data is almost impossible to tamper with, unless all nodes agree to do so.
Thanks
Thanks, Professor @stream4u, for the lesson titled Let's Open The CryptoGraphy.
Pictures Sourcing
- The editorial picture was created by me.
- Unless otherwise stated, all another pictures were screenshoots and were edited with Photoshop CS 3.
Sources and Reading Suggestion
- https://www.upgrad.com/blog/cryptography-in-blockchain/;
- https://101blockchains.com/blockchain-cryptography/;
- https://medium.com/brandlitic/cryptography-in-blockchain-explained-df11fe1bd0f7;
- https://www.investopedia.com/terms/b/blockchain.asp;
- https://www.euromoney.com/learning/blockchain-explained/what-is-blockchain;
- https://www.chathamhouse.org/events/all/members-event/chatham-house-primer-blockchain;
- https://economictimes.indiatimes.com/definition/cryptography;
- https://en.wikipedia.org/wiki/Enigma_machine;
- https://www.kompas.com/global/read/2020/12/05/082035570/mesin-enigma-pengirim-pesan-rahasia-nazi-jerman-ditemukan-di-laut-baltik;
- https://www.blockchain-council.org/blockchain/top-10-blockchain-platforms-you-need-to-know-about/;
- https://www.cnnindonesia.com/ekonomi/20210604142925-83-650415/sejarah-bitcoin-jadi-mata-uang-digital-yang-populer;
- https://zipmex.com/id/en/learn/apa-itu-tron-trx-pengertian-cara-kerja-dan-harga/;
- https://kriptologi.com/2016/02/18/ibm-mulai-berinvestasi-pada-teknologi-blockchain/;
- https://www.kaleido.io/blockchain-platform/quorum;
- https://www.coindesk.com/consensys-acquires-jp-morgan-quorum-blockchain;
- https://www.blockchain-council.org/blockchain/what-is-quorum-how-is-it-different-from-other-blockchain/;
- https://en.wikipedia.org/wiki/Public-key_cryptography;
- https://www.globalsign.com/en/ssl-information-center/what-is-public-key-cryptography;
- https://www.cloudflare.com/learning/ssl/how-does-public-key-encryption-work/;
- https://www.tutorialspoint.com/cryptography/public_key_encryption.htm;
- https://cheapsslsecurity.com/p/what-is-public-key-and-private-key-cryptography-and-how-does-it-work/;
- https://sectigo.com/resource-library/public-key-vs-private-key;
- https://koolspan.com/private-key-encryption/;
- https://www.preveil.com/blog/public-and-private-key/;
- https://www.ibm.com/docs/en/sdk-java-technology/8?topic=processes-secret-key-cryptography;
- https://en.wikipedia.org/wiki/Digital_Signature_Algorithm;
- https://jurnal.uisu.ac.id/index.php/infotekjar/article/view/1019;
- https://www.tutorialspoint.com/cryptography/cryptography_digital_signatures.htm;
- https://digisign.id/eng-3jenisdigi.html;
- https://cryptobook.nakov.com/digital-signatures;
- https://medium.datadriveninvestor.com/cryptography-encryption-hash-functions-and-digital-signature-101-298a03eb9462;
- https://searchsecurity.techtarget.com/definition/digital-signature;
- https://www.cryptomathic.com/news-events/blog/symmetric-key-encryption-why-where-and-how-its-used-in-banking;
- https://en.wikipedia.org/wiki/Symmetric-key_algorithm;
- https://www.ibm.com/docs/en/ztpf/1.1.0.14?topic=concepts-symmetric-cryptography;
- https://www.sciencedirect.com/topics/computer-science/symmetric-cryptography;
- https://www.bankrate.com/glossary/c/cryptocurrency-wallet/;
- https://en.wikipedia.org/wiki/Cryptocurrency_wallet;
- https://www.computerworld.com/article/3389678/whats-a-crypto-wallet-and-does-it-manage-digital-currency.html;
- https://www.investopedia.com/terms/b/blockchain-wallet.asp;
- https://azbigmedia.com/business/the-different-types-of-crypto-wallets-explained/;
- https://en.wikipedia.org/wiki/Merkle_tree;
- https://brilliant.org/wiki/merkle-tree/;
- https://www.investopedia.com/terms/m/merkle-tree.asp;
- https://www.investopedia.com/terms/n/nonce.asp;
- https://www.investopedia.com/terms/h/hash.asp;
- https://www.bitpanda.com/academy/en/lessons/what-is-a-hash-function-in-a-blockchain-transaction/;
- https://blockgeeks.com/guides/what-is-hashing/;




Shared to Twitter: https://twitter.com/aneukpineung78a/status/1429072601972891648.
Keren👍🏼
I believe that you could do better.
Thank you, hehe. But long way to go😁💪🏼