[Deep Dives] - Wikileaks | Topic : CIA hack tools

Source
Though I feel I am late for the party, I also feel I have something tangible to contribute. Following the post made by @deepdives which in fact is a challenge, I got to know about Wikileaks. I just bought one private VPN client and decided to make a trip to the website and as an ICT lover, the first thing that caught my eyes was the leaks made on CIA cyber weapons and I must say, I am happy to share what I learnt from that page and some of my personal researches.

Image source pixabay. Creative commons license
The leak on the CIA's hacking tools was made available in Wikileak's popular Vault 7 archive which was released on the 7th of March 2017 but the part of the vault which is of interest to this very blog is the Year zero section which contains thousands of compromised documents on the US central intelligence agency.
If someone has told me my iPhone device is probably tapped, I won't believe that. Same goes with my Samsung smart television
Devices that has been exploited by these tools
Apple IOS
Yes, I have to give it to apple, they build the best phones that are commercially secured but how truly secured is you apple device? There's a very popular saying that no matter how secured something in your possession is, there's someone on this planet capable of taking it if he so pleases and in this case, that someone is the CIA.

Image source Wikimedia. Creative Commons Attribution-Share Alike 4.0 International license.
The security of the IOS is high for two reasons; Sandbox and application verification. The Sandbox makes works by isolating every application on your apple devices thereby making sure every application does not have access to resources that is not within its domain. Application verification is done by Apple themselves and they make sure no application is permitted on their store without proper scrutinization.
Yet there are some security vulnerability in the Apple operating system and this is due to the availability of mobileconfig files which are used for provisioning applications. Provisioning profiles allows Apple developers to test applications that has been in beta mode, under simulation environment, in real devises. Officially, each developer can test as much as 100 devices using the provisioning profile. The CIA makes use of Malicious provisioning profile to route information from their targets to a secured server. Information such as voice calls, bank details, images, etc.
Android Devices
))
image source Wikimedia CC3.0 license.
It is no surprise that android is in this list since more people patronize android more than any other mobile operating system. Whatsapp boasts of an end to end encryption to your whatsapp chats but what if I told you the CIA have compromised your chats even before it was encrypted?
According to Wikileaks zero days, the CIA has even developed "weaponized" android phones up to the tune of 24 which was developed by cyber crime contractors. According to Telegram, the hacks on chatting applications is due to the its operating system and not from the application itself, this claim has not been debunked by any android phone company.
Samsung Smart TV and the Weeping Angel
Your costly Samsung smart television in your home could be your greatest undoing as the CIA can turn it into a potential microphone which keeps sending encrypted voice messages from you to their secure server. According to the Wikileaks, the attack on Samsung TV was done in conjunction with the United Kingdom's intelligence agency.

Image source flickr. CCv2.0 license
The weeping Angel was specially developed for the Samsung smart TV and will turn your television into CIA's microphone. Even when the television is in the off mode, the weeping angel also goes a fake off mode with the same capability as when the television is in normal operating mode.
Though there is some limitations to what the weeping angel can do. For instance the weeping angel only affects a particular series if the smart TV which is the F-series and the hacker needs to have access to the USB terminal of the smart TV. Recent statement made by Samsung shows they cannot really do much about the attack as it is taking ages for a security patch against the weeping angel and even if they succeed, it means your smart TV can be your greatest undoing.
The CIA's Playground
Brutal Kangaroo
The brutal kangaroo was developed specially for air-gapped computers. One might ask what is an air-gapped computer? Well, an air-gapped computer are computers which are completely isolated from unsecure networks such as public internet. They are regarded as the most secure network in the internet.
The air-gapped computers are becoming the target of the CIA lately and little wonder they developed a special hacking tool for it. The brutal kangaroo works by first infecting nearest computer that is connected to a public network. Since this infected computer is within the organization where the target computer is, it will be base end of the attack. If there is no reachable computer within the organization that is connected to the internet, an employee could be used to facilitate the attack by inserting a USB flash disk to his computer.
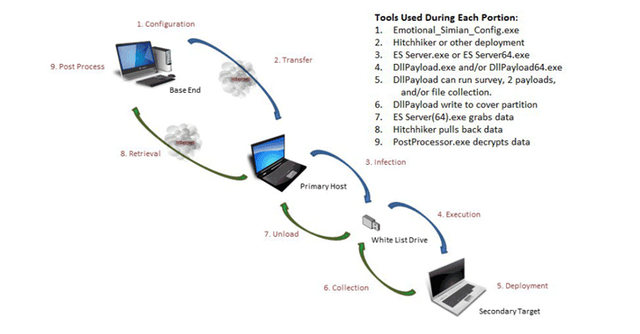
Image source Wikimedia. Creative Commons Attribution-Share Alike 4.0 International license.
Once the system has been infected, brutal kangaroo is then install in it. If the offline access was used in the attack with help of an employee’s USB connection, a further infection is required, this is called a Shattered Assurance. This is a server tool that installs another malicious ware on the USB drive called Emotional Simian though the earlier version was referred to as the Drifting Deadline.
This attack is made possible due to two vulnerabilities in the Microsoft environment. Wonder why most viruses leaves files with extension “*.lnk” after it has been flushed out of the system? That is called a link file. The kangaroo exploits a special link files called the hand crafted link file alongside the DLLs extensions which can be executed without owner’s intervention.
When an infected drive finds its way to an air-gapped system, the kangaroo automatically spreads itself like the HIV virus infecting as much computer as possible. When multiple computers has been infected, the malware forms a covert network which it uses to coordinate data transfer between the infected computers.
The Hive
The Hive was introduced in Wikileaks’ vault 7 but much information about the hive including its source code is available in the vault 8. The hive unlike kangaroo is compatible with many operating systems. The malware works by introducing implants and html source codes into operating systems like windows, Linux, Solaris, etc., and then runs a C2 command (command and control) on these compromised computers which is then used to communicate to CIA servers.
When the malware first enters an environment, it continually communicates directly with sites which appears to be harmless. Its operation also includes secured communication using commercial virtual private server which also appears to be harmless. However as harmless as these communications are, once the malware authenticates with the webserver, it begins hosting fake sites, these sites in turn keeps forwarding information from there host servers to CIA server over a secure connection. This secured server is called Blot, this blot is not an end server as it also forwards traffic it receives to a management server known as the honeycomb.
The local administrators won’t suspect the activities of this malware as its operation is covered by fake Kaspersky antivirus digital certificate.
The HammerDrill
The HammerDrill is a malware to watch out for. It is targeted at computer CD and DVD drives. It collects information about computer directories and files and sends these information to a preconfigured directory on the host computer with filenames that is very difficult to detect.
))
image source sftextures creative commons license
It also keeps records of CD and DVD activities such as removal and or insertions of DVDs and CDs into host computer. The hammerdrill exploit was later exposed which prompted the CIA to quickly make an upgrade called HammerDrill 2.0 and works a bit like the brutal kangaroo explained above. According to wikileaks:
the v2.0 adds a gap jumping capability that Trojans 32-bit executables as they are being burned to disc by Nero.
The hammerdrill works with three files, these are:
The functions of each file is almost self explanatory. The HammerDrillKiller.dll automatically terminates the activities of the malware when it seems its identity has been compromised, the HammerDrillStatus.dll updates the HammerDrillCollector.dll on the condition of its exploits and saves any information it obtains with the HammerDrillCollector.dll which sends obtained information to the CIA server.
The list is so vast but for simplicity and privacy sake, I would love to stop here.
Curated for #informationwar (by @openparadigm)

Relevance:Security
Our Purpose
This post has been upvoted and picked by Daily Picked #42! Thank you for the cool and quality content. Keep going!
Don’t forget I’m not a robot. I explore, read, upvote and share manually 😊
You can upvote, resteem, follow, delegate or join my curation tail to support me, good creators and minnows.
@curie needs to see this
Wow
This is brilliant bruh. Keep uo
Holy crap. Conspiracy theorists have always been a lot more accurate than we suspected.
Wow. A lot of ahcking information that i never know about smart tv. Thank you for the sharing. Much appreciate.
Really good job here. You really took on the spirit of the #deepdives challenge.
It makes happy you've dived into Wikileaks. It's a whole world of interesting information. I wish you many more enjoyable hours reading it. It will change your life. :)
Thank you very much for your support! Really appreciate it!
Of course! I get more knowledge in wikileaks about the world! Thanks for #deepdives team for great challenge !