HOW TO PREVENT A DDOS ATTACK
Source: What's the Big Deal?
Breaking News ! |
When computers attack: Online criminals use DDoS to hijack computers all over the world - The Boston Globe
The Boston Globe: ... happening right now, somewhere in the world. The computer network of a company or government agency is clogging up, slowing down, becoming virtually unusable. ... not caused by a defect, but rather one of the crudest weapons in the ... ...and more ...74% of All Bitcoin-Related Sites Suffered a DDoS Attack - BleepingComputer
BleepingComputer: Multi-vector attacks are DDoS incidents where an attacker uses different protocols for the DDoS assault, such as SYN, TCP, UDP, ICMP, NTP, DNS, and others. Attackers usually probe companies with multiple vectors in the beginning and then focus on the ...and more ...When the retail chain is forged - ITProPortal
ITProPortal: The ramifications of a security breach for retailers cover both loss of trust and loss of revenue – the former if the breach includes customer data - the latter if the attack brings down the site (or in-store technology). To protect against this ...DDoS attack protection: When should it be taken seriously? - TechTarget
TechTarget: There are several key ways to successfully defend against an attack, yet the main defense revolves around being prepared. By always being at the ready, there is no chance of confusion among employees or departments about what to do when a DDoS attack ...and more ...Naked rower's site hit by DDoS following Russia ban - SC Magazine
SC Magazine: The calendar was banned from Russia for being what it called “gay propaganda.” The DDoS attack that sent 7,268 visits per second to their website was seemingly designed to prevent the calendar from being sold and was traced to a Russian IP address ...Cyber threats are growing in size and stature, but system compromises are the new weak spot for businesses - ITProPortal
ITProPortal: In a recent survey, conducted by the Neustar International Security Council (NISC), system compromises were unveiled as the greatest cyber concern for IT security leaders, with nearly one in four (23 per cent) citing them as the biggest threat to their ...and more ...FCC Must Investigate Fraud Before Voting on Net Neutrality - WIRED
WIRED: ... more, as many as half a million additional comments were filed from Russian email addresses. And 50,000 FCC consumer complaints are missing from the record, even though this is just the kind of data the FCC should be using to inform its efforts ...and more ...Damaging DDOS Attacks Becoming More Popular Study Finds - KoDDoS (blog)
KoDDoS (blog): Another prominent attack method utilizes service flood techniques. Services flood attacks operate, as the name suggests, by flooding a ... system. In turn, this will cause a temporary system shutdown. The firm concluded its report by emphasizing ...and more ...Corero: Number of DDoS attacks more than doubled in six months - DatacenterDynamics
DatacenterDynamics: “The Mirai-based DDoS attack was the perfect opportunity to target this issue and call out developers and manufacturers to take an open approach to security. Regulators should help by enforcing ISPs to temporarily block IP addresses known from being ...DDoS Attacks Decreasing, but Repeatedly Hammering Targets - Credit Union Times
Credit Union Times: There is a brighter side however. Overall the number Verisign saw a 17% decrease in the number of attacks, and a 70% decrease in the peak size of the average attack comparing Q3 2017 to Q2 2017. Nevertheless, DDoS attacks remain unpredictable and vary ...Follow our Community for More ! |
HOW A DDOS ATTACK WORKS AND HOW TO STOP IT
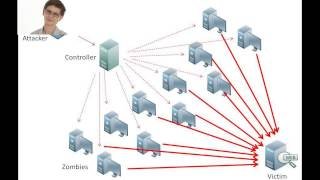
HOW TO STOP DDOS ATTACKS

DDOS ATTACKS: ARE YOU READY? - HOW TO PREVENT AND PREPARE FOR DDOS ATTACKS

COMPUTER FIGHTS HACKER ATTACK
HOW TO DETECT A DDOS ATTACK ON YOUR NETWORK! - WIRESHARK TUTORIAL

Latest posts from our Community ! |
- BLACK HAT USA 2013 - LESSONS FROM SURVIVING A 300GBPS DENIAL OF SERVICE ATTACK
- HOW TO MAKE ANY VENDING MACHINE PAY YOU! (GET FREE MONEY)
- WHAT IS BITCOIN? HOW TO MINE BITCOIN? ANY GOOD?
- HOW ASYMMETRIC (PUBLIC KEY) ENCRYPTION WORKS
- BITCOIN MINER LIFE
- FORGET MINING BITCOIN, START MINING LITECOIN WITH HOME BUILT LITECOIN MINING RIG
- OPPORTY ICO | BLOCKCHAIN SERVICE MARKETPLACE L INITIAL COIN OFFERING
- LIVING, BREATHING, & BETTING ON BITCOIN | OUTLIERS EP. 2
- HOW TO MAKE MONEY ONLINE FAST 2 LEGIT WAYS ON HOW TO MAKE MONEY ONLINE FAST
- IS A DOS ATTACK A WEAPON? | IDEA CHANNEL | PBS DIGITAL STUDIOS