HOW ASYMMETRIC (PUBLIC KEY) ENCRYPTION WORKS
Source: Veet Vivarto
Breaking News ! |
Safety of Web Applications - TechTarget
TechTarget: Symmetric encryption is inexpensive in terms of computation time, due to the simplicity of its algorithms (matrix permutations and boolean XOR-type functions are applied to the data). However, they have a disadvantage: the sender and the receiver must ...Access Control Encryption 101 - SecurityInfoWatch
SecurityInfoWatch: Most cryptographic processes use symmetric encryption to encrypt data transmissions but use asymmetric encryption to encrypt and exchange the secret key. Symmetric encryption, or private key encryption, uses the same private key for both encryption and ...Why Quantum Computers Might Not Break Cryptography - Quanta Magazine
Quanta Magazine: Still, a terabyte-size key ... exactly easy to work with. (The largest RSA keys right now are a few thousand bits; a terabyte is many trillions of bits.) The authors report that generating a terabyte-size RSA key and carrying out the encryption ...Researchers warn of Infineon security chip flaw - bit-tech.net (blog)
bit-tech.net (blog): Researchers have published the discovery of a key generation flaw in security chips produced by Infineon Technologies since at least 2012 and which allows attackers to turn a public RSA cryptographic key into its private half. Public-key, or asymmetric ...China's Quantum Net Advance Offers a Glimpse into the Future of Enterprise Security - Data Center Knowledge
Data Center Knowledge: One organization in the US that does have a small test project in the works is the Oak Ridge National Laboratory, but ... not comparable to the Chinese effort, said Jayson Hines, project manager in the Computing and Computational Sciences Directorate ...What is quantum encryption? It's no silver bullet, but could improve security - Networks Asia
Networks Asia: ... why some people are looking to quantum encryption to protect data in the future. ... how encryption works on “traditional” computers: Binary digits ... and ... are systematically sent from one place to another, and then deciphered with a ...Quantum computing breaks encryption next decade; current data at risk - SC Magazine UK
SC Magazine UK: Public-key cryptography protects much of ... Internet traffic, providing security for banking transactions, encrypted chat, secure Web browsing, and so on. Breaking the codes currently requires too much conventional computer time and power to make ...and more ...Quantum encryption: no silver bullet - Corporate IT
Corporate IT: Here is how encryption works on “traditional” computers: binary digits ... and ... are systematically sent from one place to another, and then deciphered with a symmetric (private) or asymmetric (public) key. Symmetric key ciphers like Advanced ...and more ...Let's harden Internet crypto so quantum computers can't crack it - The Register
The Register: The work-in-progress suggests an optional IKEv2 payload “used in conjunction with the existing Diffie-Hellman key exchange to establish a quantum-safe shared secret between an initiator and a responder,” and it supports a number of suitable key ...Quantum Hacking Vs. Quantum Encryption: Winner Takes All? - PaymentsJournal
PaymentsJournal: “Here is how encryption works on “traditional” computers: binary digits ... and ... are systematically sent from one place to another, and then deciphered with a symmetric (private) or asymmetric (public) key. Symmetric key ciphers like Advanced ...Follow our Community for More ! |
ASYMMETRIC ENCRYPTION - SIMPLY EXPLAINED
SYMMETRIC AND ASYMMETRIC ENCRYPTION OVERVIEW (PRIVATE PUBLIC KEYS)
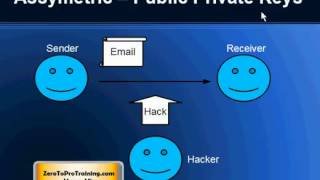
PUBLIC KEY ENCRYPTION
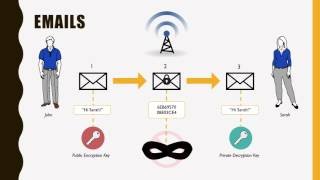
SYMMETRIC KEY AND PUBLIC KEY ENCRYPTION
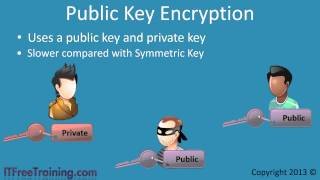
INTRO TO ASYMMETRIC KEY CRYPTOGRAPHY

Latest posts from our Community ! |
- BITCOIN MINER LIFE
- FORGET MINING BITCOIN, START MINING LITECOIN WITH HOME BUILT LITECOIN MINING RIG
- OPPORTY ICO | BLOCKCHAIN SERVICE MARKETPLACE L INITIAL COIN OFFERING
- LIVING, BREATHING, & BETTING ON BITCOIN | OUTLIERS EP. 2
- HOW TO MAKE MONEY ONLINE FAST 2 LEGIT WAYS ON HOW TO MAKE MONEY ONLINE FAST
- IS A DOS ATTACK A WEAPON? | IDEA CHANNEL | PBS DIGITAL STUDIOS
- IS GPU MINING STILL PROFITABLE? - MINING ADVENTURE PART 1
- THE MOST DANGEROUS EVENT IN CRYPTOS & DIGITAL CURRENCIES - MIKE MALONEY
- BITCOIN: HOW CRYPTOCURRENCIES WORK
- WHAT IS BITCOIN AND HOW DOES IT WORK? | MASHABLE EXPLAINS