Are You Ready to Protect Your Customers and Employees’ Privacy?
As the calendar counts down to May 25, 2018 when the European Union’s General Data Protection Regulation (GDPR) kicks in the $64,000 question is are companies ready?
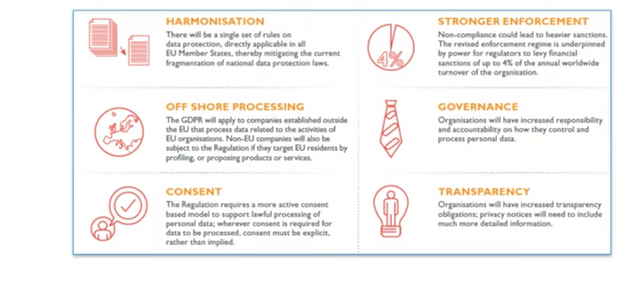
Under the EU Parliament’s GDPR, “all companies processing the personal data of data subjects residing in the Union, regardless of the company’s location” will need to protect EU citizens from privacy and data breaches.
If companies fail to protect individuals’ information, including names, photos, email addresses, social networking posts, medical information, bank details and IP addresses, they could get fined millions of euros.
GDPR Insights from the Experts
GDPR offers some clear-cut guidelines that countries must follow to protect individuals’ personal information (PI). And there are some GDPR Articles that can be interpreted by countries and their local authorities.
During a June 22, 2017 BigID webinar, Automating Data Protection & Compliance for GDPR, Paul Nemitz, principal advisor and directorate-general at the European Commission’s Justice and Consumers, explained some of the GDPR regulation.
“Now, it is very clear that the burden of proof–of you legally processing data–as a controller processor is on you,” he stated. “You must be able to show all your processing of personal data of individuals is in line with regulations.”
“That’s why it’s important that you ensure compliance and the starting point of ensuring compliance is, of course, is to know what personal data you have; where it is; what are risks related to this type of personal data, which you are managing; whether you have consent or not to use it and for what,” Nemitz continued after he said companies will have to pay four percent of world turnover (revenue) for failing to comply with GDPR, which follows the methodology of the EU’s competition law. Companies must also prove they deleted the data.
Gaston Gautreneau, IT expert, Commission Nationale de l’Informatique et des Libertés (CNIL), the French data protection authority, added that data protection authorities will consider the specifics of a data breach before imposing fines. These elements will include the gravity and duration of the situation; number of data subjects impacted by a breach; level of damage the breach caused; and whether the breach was intentional or if it was an act of negligence. He also cited any factors that contributed to any financial gains or losses from the incident.
How Should My Company Comply with GDPR?
Organizations must have a means to assess and track data subjects’ information in order to be GDPR-compliant, Gautreneau said. In addition to respecting the fundamental principles and rights (of individuals), organizations must manage the risks related to data security by identifying the technical and organizational measures to protect the personal data from data breaches. Enterprises must also show they are in compliance.
“This approach is a basis of the privacy-by-design approach,” Gautreneau explained. “In fact, because you have to manage the interpretation of the impact that could have these services or application on the people behind the application that have been deployed or will be deployed.”
The Legal Perspective
Patrick Van Eecke, partner with DLA Piper UK LLP and another webinar participant who specializes in explaining the GDPR rules to the EU Member State representatives, said GDPR is one European law for the whole of the European Union. But countries in the EU can customize the GDPR rules, as well.
“If you read the GDPR, you actually know this that there are more than 50 places in the GDPR that actually give the liberty to countries–member states–to deviate or bring some further details into the data protection legislation,” Van Eecke said.
He cited certain circumstances in which the GDPR states children need to be 16 years old before they can consent to give up their privacy. Until they reach this age, parents and/or custodians are only authorized to do this. GDPR also gives countries the option to lower the age to 13 years old before kids can give their permission to share their data. Countries will also be able to impose more detailed limitations on how companies can use genetic and health-related data.
“Yes, there is harmonization. However, countries are still gonna make use of their opportunities. Actually, it’s already happening now….They actually come up with local legislation, local kind of implementations, local flavors of the GDPR,” he continued.
Van Eecke also shared that data breach notification and related legislation is a new principle in the EU. Except in a few countries and industries like the Netherlands and telecommunications, there is no data breach and notification legislation.
Van Eecke’s slide on GDPR rules shown during the webinar.
Don’t Even Think about Separating Your Assets
Van Eecke pointed out that companies that try to limit their risk of GDPR non-compliance by creating separate legal entities to absorb the fines and liabilities will not be able to protect these assets.
“Very often after having explained what the GDPR means and what could be liability exposure then somebody in the room says, “Well I found it. You know what you’re gonna do. We’re gonna put all the risk in one legal entity. So we’re gonna do the data processing activities; we’re gonna transfer that to one legal entity belonging to the group–a kind of shared service center. And whenever we screw up, we’ll it’s that legal entity that has to bear liability. And when we’re talking about four percent turnover rule, well it’s gonna be that turnover of that entity and actually, they’re not making that much of turnover, so we don’t need to bother too much.”
“I am afraid that this has been taken care of,” he said. “Paul and the other people at the policy-making level they took into account that actually you always need to look at the global picture of an undertaking. It’s not just one specific legal entity within an organization that would be held liable. It’s much broader and they’re gonna look at the circle of organizations, both controllers, both processors that actually have been involved and they could be solidarily–so, in solidum–could be held liable for any kind of infringement.”
IBM’s GDPR Solutions
For companies that need to evaluate whether they are GDPR-compliant, IBM offers its 5-Phase Security Framework for GDPR Readiness.
Invented by IBM Security’s CTO of Data Security and Privacy Cindy E. Compert, the framework recommends enterprises:
- Assess the GDPR practices of clients.
- Design governance, training, communications, processes, privacy, data management and security management standards.
- Transform by developing and embedding procedures, processes and tools.
- Operate by executing all relevant business processes; monitoring security and privacy using Technical and Organizational Measures (TOM).
- Conform by monitoring, assessing, auditing, reporting and evaluating adherence to GDPR standards.
IBM offers enterprises a “data protection GDPR accelerator” called Guardium that protects and monitors information, creates audit trails and workflow.
Its identity governance platform manages who has access. Its Resilient Incident Response platform has GDPR-specific program guidance, which adapts and incorporates any changes regulators make to GDPR.
BigID Connects Individuals’ Data Dots
BigID, the webinar’s sponsor, featured Nimrod Vax, the company’s chief product officer and co-founder, who concluded the panelists’ segment by detailing its GDPR solution.
RSA Conference’s “RSAC’s Most Innovative Startup 2018” addresses GDPR’s Article 17 (Right to Erasure or “Right to be Forgotten”), Article 15 (Right of Access by the Data Subject) and Article 20 (Right to Data Portability).
BigID automatically scans any data store and application housed within a company or off-site in the cloud to identify personal information, such as an IP address or a device identity.
Using its patent-pending machine learning and identity intelligence algorithm, it correlates data to specific individuals and the sources where their data is located. This allows BigID’s clients and their customers to see the locations like countries and file types that store their data, as well as the actual data that has been collected and associated with them. It also shows users data that identify a person’s country of residency.
All this information can be downloaded into a report for BigID’s clients and their customers.
No personal data is ever copied to the BigID software running inside the enterprise and no data ever leaves the company's environment.
We Need to Better Secure our Industrial Control Systems
Joe Weiss, managing partner at Applied Control Solutions, LLC and HACK NYC team member, underscored HACK NYC 2018’s focus on protecting infrastructure by discussing industrial control systems (ICS) security during his May 3, 2018 webinar, The Hole in Control System Security. The event was presented by HACK NYC 2018 and Proactive Risk.
The author of Protecting Industrial Control Systems from Electronic Threats emphasized that the security of industrial control systems (e.g., sensors, actuators, drives, controllers, analyzers and intelligent electronic devices used in electrical substations, water treatment and nuclear power plants, pipelines, trains, ships, etc.,) is “pretty poor.”
Weiss’ slide from the May 3 webinar.
He attributed security risks with this equipment to the lack of training, methodologies and understanding about this area of infrastructure. “If you don’t know how a system really works, it’s really scary to input a technology that impacts a system,” Weiss said.
He stressed that organizations need to analyze sensors for unusual activity before they become data packets.
Weiss also recommended that network security people need to involve engineers in ICS security. “Computer science and engineering need to understand what other disciplines are about!”





To the question in your title, my Magic 8-Ball says:
Hi! I'm a bot, and this answer was posted automatically. Check this post out for more information.