Privacy and Data Safety in 2019: A Layman's Guide
As anyone who has followed me here knows, I cannot speak highly enough of the internet and how it has made accessing and sharing the wonders of the world with an, at least in theory, almost unlimited audience, but you have been living under a rock the last couple of years if you have not noticed the hazards of conducting basically every part of our lives in the digital space, whose inner workings is beyond most of its normal users, using services provided by a very narrow group of de facto monopolist companies.

data security and online privacy is becoming an increasingly important issue - picture from techdissected.com
Hackers and Scammers
Data is increasingly becoming an important asset, representing a higher and higher monetary value and this is a fact that is known by both businesses and crooks alike. Like how good data on the behaviour and preferences of your customers can mean the difference between a successful product and a failure, access to, or just the claim of having access to people’s sensitive data can be an efficient vector for blackmailing both companies and private individuals.
As a personal anecdote, just before Christmas, I received the following mail with an old username and password of mine as the subject:
Isn't [An old password of mine] is one of your pass:) My name is Zonnya.
The XXX site you watched was infected with my backdoor which taped a video of your nasty stimulating actions with the help of your cam and also taped the video you were streaming. You really are appearing engaging in the video footage.
Malware also sent me each and every of your Facebook and mail contacts and the recording.
I'll email your recording to your friends unless you send me 1122 USD via Bit coin within the next 24 hours to the below address:
B I T C O I N Address: 137k89gCR5gYniSWFYBujnYsWZcwqJWNqj
Copy and Paste address because it is CasE SenSiTiVe.Once money is received by me, I will delete your recording and every other information I have about you.
If I do not receive the money, I will send your recording to every contact of yours. Just think about the awkwardness you feel. Not to mention if you happen to be in a relationship, how it will affect?
Want proof? Reply "Yes", & I'll email your recording to nine of your contacts instantly.
Respectfully yours
I was amused that my scammer were courteous enough to end his/her blatant attempt at blackmail with a respectfully yours.
I knew that there was no way that the claims in this mail could be true and that this password was most likely acquired from a data breach, but anyone less computer savvy could easily have been intimidated by such a mail and might even have ended up giving in to such blackmail. I know of many others who lately have received mails of a similar wording containing a password of yours and similar threats of disclosing incriminating videos, etc. of you if you do not pay the scammer.
The complexities of the internet and computers in general means that the less tech savvy end of computer users, which contains a large amount of the elderly and the vulnerable, are very susceptible to scammers claiming to be from tech support, who will gain access to your computer under the pretense of fixing some error and at best will scam you for money and at worst lock you out of your computer or delete all your files if you do not comply. There are several variations of the tech support scam. Some scammers simply just acquire lists of (usually) US/UK phone numbers and cold call people, while others pay for pop-up ads masquerading as security warnings, but once they have established control to your machine, they will show you completely benign error logs or even fabricate fake errors in order to get you to pay for an expensive security package you do not need or even try to get access to your bank account in order to empty your bank account.
Genuine hackers are much rarer and as a rule go after companies, where the amounts of data and therefore the monetary gain is much greater. Not just content with simply stealing data from companies, the modern hacker conducts his business by finding or obtaining exploits in the Windows OS (usually) that can be used to infect vulnerable PC’s with so-called cryptoworms: Software that encrypts all data on the infected PC’s hard drive, rendering it inaccessible unless the decryption key is purchased using Bitcoin.
Selling Personal Data by the Byte
You do not have to be more than an average user of social media in order to create enough data points to sketch a fairly detailed picture of you. As touched upon above, personal data is worth a lot of money, and the longer the time series and the more data points on your preferences, etc. the better. Therefore, it is no wonder that the large social platforms such as Facebook and Twitter, where a whole generation has routinely posted about their wants and likes for years have been able to create a lucrative business on making these comprehensive data series available. To be fair to Facebook, they do not sell your data directly (unlike Twitter), but simply offers to rent out space to advertisers on your timeline, third party developers have been able to extract a lot of personal data without the consent of the users due to the way Facebook is designed. The same can be said for the internet monolith Google, whose data sets on search histories have earned them billions of dollars in revenue over the years through their AdSense network.
Keeping you and your data safe
Given the above, I will now present a small guide on how to easily secure your data and your computer against the hazards of the internet. This is by no means a comprehensive guide, more like a few steps that a person with an average knowledge of computers could make use of in order to make conducting your digital business and keeping your data safe just a little bit easier.
Leaving the Windows OS behind
Ever since I started using computers and up until recently, the Windows OS has been a permanent fixture of my computing experience. After all, all major games made for the PC are made to run, usually exclusively, on the Windows OS as is most if not all software that is used in a professional context. However, it is also the case, that due to the popularity of the OS and the way that Windows is still designed at its core, viruses and malware are designed almost exclusively to run on, and infect, Windows machines. The same goes for tech scammers, who always target users with Windows machines. In short, remove Windows from the equation and it will save you from a lot of trouble. The question is how to do it without losing the functionality and flexibility that comes with a Windows installation.
The obvious choice is to switch to an Apple mac computer, which has an ever expanding user base thanks to the elegant design of the hardware and a growing software library with many professional software suites that were Windows exclusive before being ported to OS/X. However, if Apple/mac is not your thing or if the price tag of a macbook seems a bit prohibitive, there is another alternative that does not require you to invest in new hardware, offers a wide variety of software and will not cost you a dime: Ubuntu Linux

Ubuntu logo - image from ubuntu.com
I like Ubuntu for all its out of the box functionality that provides everything that an average user would need completely for free and its flexibility in terms of its huge library of software and endless customizability, so whether you are designing a cool desktop environment for yourself or just creating a simple and cheap setup on older hardware, this is the OS for you. I can especially recommend installing Ubuntu on the computers of your elderly relatives, as they are much less likely to have a preference for Windows anyway and because it will save them, and therefore you by extension, a lot of trouble (and an antivirus subscription!).
I use a variation of Ubuntu called Xubuntu, which is Ubuntu with an alternative desktop environment called Xfce. It is faster and more reminiscent of the classical desktop environments that I enjoy working with:
My Xubuntu desktop
Curbing your social media presence
Chances are you are already on some kind of social media platform and even more likely, you signed up to that platform for free. However, one thing to always remember that when an operation like Facebook that requires large staff of skilled programmers and engineers for maintenance plus an extremely robust server setup in order to function is not providing its services out of their good hearts – it is a business, and when you are not paying, you are the product being sold. Therefore, keep your social media usage to a minimum or at least be mindful of what information about yourself that you make available on these platforms. The more you post, the clearer a picture of you will be made available when data is sold or leaked. When something is put on the internet, it is forever, and this is especially true on social media, where everything you post is potential revenue for the platform. Also consider switching away from Google as your default search engine to more privacy-oriented alternatives like DuckDuckGo or Qwant that do not track your searches.
Password Management
One of the main threats to keeping your data safe is neither hackers nor scammers, but ourselves and our management of our ever increasing number of passwords to our computers, tablets and internet accounts. Most of us tend to choose relatively short and easy password and tend to use the same password for multiple accounts, which makes your data very susceptible to data breaches, and thereby blackmail.
The internet web comic XKCD offers a great explanation on what makes a password safe and how you can create a strong password that is easy to use:
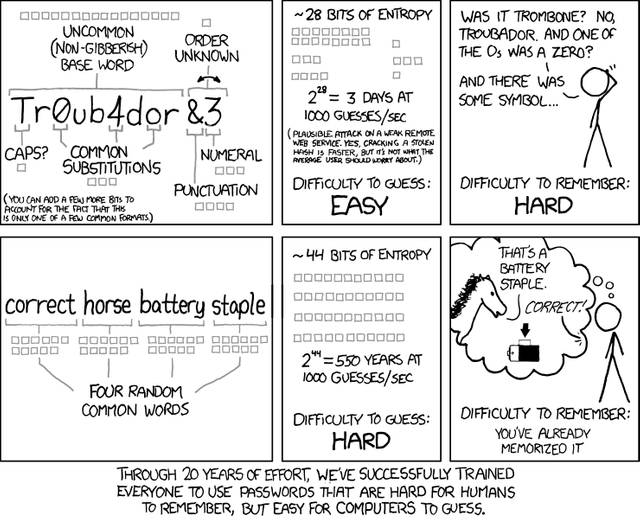
Most passwords today is required to contain numbers as well, so just choose a combination of numbers that are easy for you to remember, but is less obvious than your birthday. Another method, which is very handy if you speak more than one language is to choose a word and repeat it in two or more languages. The other part of the problem is managing a large number of long and complex passwords. The answer to this issue is a piece of software called a password manager.
At their core, password managers are encrypted databases where you can store passwords, that are unlocked by a master password, thus reducing the number of passwords you need to remember to one. Password managers comes in different flavours, from standard password managers like UPM and KeePass available for free with simple functionality for creating and storing password entries and random password generation, to paid services like Dashlane, who not only will create and store strong passwords for you, but also automatically log you in to your account when you open the corresponding page. Dashlane will even warn you when your e-mail has been confirmed to be part of a data breach and even comes with a VPN service as well.
Ad Blockers
Rather than simply cold calling, some tech support scammers purchase banner advertisements designed as big flashy warning screens urging them to call your number and are in the worst cases quite hard to close and get rid of. An easy way to get around this is to simply install and ad blocker extension in your browser of choice. The are a lot of ad blockers to choose from depending on your browser of choice, but if you are using Google Chrome(or one of its derivatives) or Firefox, most efficient ad blocker in my experience is Adblock Ultimate both in terms of its indiscriminate blocking of all ads and its ease of use.
...And Beyond
While all of the above covers easy steps that the layman user can take to make their data and online experience a little bit more safe, it is only scratching the surface. If you for one reason or another are very concerned about your privacy online, getting a VPN is indispensable. VPN is short for Virtual Private Network and is a technology that allows you to send and receive data across public networks as if you were connected directly to a private network, thus increasing security and obfuscating your online footprint. There are free VPN alternatives out there, but like with Facebook, always remember that whenever a product is offered for free, that data that is generated when you use it is most likely to be the real product, so be sure to check the terms of service, or subscribe to a VPN service like SkyVPN, that promises not to sell your data to third parties. As your browser is most likely to be the gateway to almost all of your internet experience, your choice of browser will affect the data footprint you leave behind when conducting your business online. There exist more secure versions of popular browsers, such as the Chrome-based Iridium Browser, but to get as close to internet anonymity as you can, the tor network, which redirects your traffic through a multitude of servers, and is associated browser is the obvious choice. The tor browser also comes as standard in high security OS’es such as Whonix and tails, which are made to be easily booted through a virtual machine or USB stick on demand in case you are in need of internet privacy beyond what a normal OS can provide.
Thank you for reading! If there are any good tips for the layman user that is concerned with his privacy or safety online that you think I missed, please leave it in a comment below.
For more information about how tech support scammers work, please visit Jim Brownings YouTube channel and check out his videos on the different types of scams as well as some hilarious videos on scam baiting.
For more information on how to install Ubuntu, please check out Ubuntu Tutorials.
Also, remember to check if your mail have been a part of a data breach on https://haveibeenpwned.com/
Congratulations! Your post has been selected as a daily Steemit truffle! It is listed on rank 4 of all contributions awarded today. You can find the TOP DAILY TRUFFLE PICKS HERE.
I upvoted your contribution because to my mind your post is at least 6 SBD worth and should receive 244 votes. It's now up to the lovely Steemit community to make this come true.
I am
TrufflePig, an Artificial Intelligence Bot that helps minnows and content curators using Machine Learning. If you are curious how I select content, you can find an explanation here!Have a nice day and sincerely yours,

TrufflePigThis is a well written and thorough article, @cogitecture ! And I think a lot of people would benefit from reading it and from applying the knowledge gained from it, as well :)
Thanks, I hope it can help some people to stay just a little bit safer online :)
This post was shared in the Curation Collective Discord community for curators, and upvoted and resteemed by the @c-squared community account after manual review.
@c-squared runs a community witness. Please consider using one of your witness votes on us here