BitFence

About BitFence
The purpose of this Article is to present BitFence and HNY Token to potential token holders in connection with the sale of the proposed Token. The information listed below may be incomplete and does not imply any element of any contractual relationship. The sole purpose is to provide relevant and sensible information to the potential token holders in order for them to determine whether to conduct a thorough analysis of the company to purchase HNY Token.HNY Token is a utility token. This product is not a digital currency, security, commodity, or other type of financial instrument and has not been registered under the Securities Act, US securities laws or other state securities laws, including securities laws from any jurisdiction token holder potential is a resident. HNY tokens can not be used for any purpose other than those provided in Whitepaper, including but not limited to, any investment, speculative or other financial purposes. HNY Token is not intended for sale or use in jurisdictions where the sale or use of digital tokens may be prohibited. HNY Token does not grant any rights in any form, including but not limited to ownership, distribution (including but not limited to profits), redemption, liquidation, ownership (including any form of intellectual property), or other legal or other rights specifically described in white paper. The statements, estimates, and certain financial information contained in this Whitepaper are forward-looking statements or information.
WHY BitFence?
BitFence Cyber Security is a global intelligent contract-based Cyber threat prevention system that offers a direct and unmatched advantage over existing network security solutions. In addition, in addition to the zero-day defense, BitFence also provides incentives (1) to those who deploy BitFence configure honeypots (2) to attract distributed hackers around the world. When a hacker breaks into BitFence Honeypots, the system captures and analyzes an attacker's signature using specially designed Artificial Intelligence software and alerts / sends threat protection to all of its customers. For example, if a 'A' Company that is already a BitFence customer located in the United States is attacked by a hacker; customers of other systems residing in other regions (eg in Europe, Asia or Africa, etc.
BitFence Detects, transfers and prevents unauthorized use of the information system and gives your security team an unfair advantage to hackers.
mission
BitFence Cyber Solution is to reduce the average detection time of zero-day malware and to adopt and deploy a proactive defensive approach / solution to reduce other systems from similar cyber threats.
CONCEPT OF HIGH LEVEL CONCEPT
BitFence offers its users the tools necessary to measure the growth of cyber threats and protect the network proactively, before any damage occurs to networks and related assets. The BitFence ecosystem consists of following three main sections:
Installation of BitFence designed Distributed Sensor Network (also known as Distributed HoneyPot). BitFence offers incentives to anyone who runs software designed by BitFence and or "miner" hardware. This miner will automatically detect and report related suspicious virtual activities. The miners will be rewarded through the distribution of BitFence 'HNY' Tokens.
Dangerous and suspicious data collected by miners will automatically be analyzed, processed and ranked (according to risk factors) by artificial intelligence algorithms in real time. Therefore, the list of signatures will be updated.
Finally, once the data is processed and the malicious perpetrator (hacker) is identified, the information is directly provided to all BitFence customers to mitigate them with similar threats.
EXAMPLES OF USECASES
To understand the operational concepts of BitFence Cyber Threat Intelligence solutions, several Use Cases with different scenarios are illustrated below:
Use Case # 1 - Small Enterprise Scenario 'A'
Company 'A' is a small business that produces toys for children. The company has an eCommerce business hosted in the cloud. Company websites, eCommerce stores along with their servers and databases are constantly being attacked by hackers using different techniques - such as port scanning, flooding, SQL injection type attacks, PHP exploits, etc. Due to this constant attack, the availability of websites, personal customers information, and company assets are always at risk.
To address this threat, BitFence offers the most effective and fully integrated protection solution at a minimal cost compared to competitors such as FireEye, McAfee, RSA. Competitor solutions are very complex with a minimum cost of at least $ 5K per month for integrated protection.
The protection provided by BitFence will be able to block high-risk, malicious payload and high-risk IP addresses that connect automatically within seconds after threats are identified and assessed by BitFence miner intelligence and intelligence software with very reasonable monthly subscriptions.
Use Case # 2 - Company Scenario 'B' with multiple cloud service providers
The 'B' company is a consulting firm with several offices located in different places using several cloud service providers hosted by Amazon Web Services, Microsoft Azure, Google Cloud and IBM Cloud etc. VPN with F5 gateway has also been used. The company notices that this service is always attacked by hackers. Because of these attacks, company-sensitive information such as intellectual property data, network loss, security breaches may occur.
The company employs a proactive Information Systems Administrator who regularly monitors the network and updates Firewall policies of the company. Most Commercial-Off-The-Shelf (COTS) gateways and routers contain the ability to integrate threat feeds from external sources and can therefore be blocked. The majority of threat feeds can be purchased and contain good information about malicious hosts. However, this information usually contains old information for follow-up. For example, it is possible that the same attacker will use an existing IP address and leave the same footprint for very low search destinations.
BitFence solutions offer midsize companies with multiple locations by granting them access to zero-day vulnerabilities by miners who subscribe to BitFence. By utilizing BitFence miners, such companies do not deal with the outdated information they get from external sources.
Use Case # 3 - Large Corporate Scenario with Information Security Section of reasonable size
Large companies contain special security teams in each location. The company adopts various intelligence detection and mitigation threat devices from a number of providers such as FireEye, Infoblox, LookingGlass, McAfee, RSA, SecureWorks, Symantec or VeriSign. The company also contracted security vendors of its choice with security packages and complex threat intelligence solutions. In addition, companies face problems with extensive data traffic even after many "data rejection". For data mining and log review, Hadoop Solution is used. Given the enormous data collection, it is difficult to review logs that correlate with some real-time zero-day type threats.
BitFence API and worldwide feed threats run by miners, will be seamlessly integrated into custom software solutions to provide zero-day vulnerability prospects to existing threats to dramatically improve system security
Use Case # 4 - Opportunities for Miners to Generate HNY Token
If someone wants to earn passive income and the options he is looking for are cryptocurrency and mining. Most mining hardware typically becomes overextended without even a reasonable return on investment (ROI) after all related expenses such as equipment purchases, real estate, routine maintenance, electricity and related costs.
BitFence offers the opportunity to mine a 'HNY' token by running cost-effective software applications or microcomputers (Raspberry Pi, BeagleBoard) connected to the Internet. The software designed by BitFence will create a virtual environment to attract Hackers as an invite. When a hacker tries to hack this specially designed mining system, he will leave it with footprints that will be communicated to a BitFence System called Honeynet or HoneyFarm for further analysis. The information / data collected is then processed by the classification of Artificial Intelligence (AI) and then processed into a threat of actionable intelligence intelligence. Once this process is registered, special miners will be rewarded with HNY Tokens that can be redeemed to BitCoin (BTC), Ethereum (ETH / ETC),.
PLATFORM ARCHITECTURE
BitFence Cyber Security Threat and Intelligence comes in two different artifacts - Assessment / identification / detection of threats and threat threat assessment, signature spread and mitigation. Mining will be performed by globally dispersed individuals using BitFence devices and software. The mining platform is integrated with a BitFence centralized server where risk assessment of threat signatures is evaluated. Once the threat is evaluated, signatures are deployed for individual subscriptions and business subscription systems to reduce them from zero-day malware and other cyber security threats.
The following organizations and / or individuals are affected by the implementation of the BitFence Threats Intelligence solution and are therefore identified as BitFence stakeholders:
From a product development perspective, BitFence stakeholders are: Inventor & Developer, System Engineer, Maya Security Engineer, Software Engineer, Product Maintenance Personnel, Test Engineer, Sales & Marketing, etc.
From a user point of view, BitFence stakeholders are: small, medium and large businesses, corporations and companies, Finance & Health industries, Banking sector, Defense & Aerospace companies, Academic Institutions such as Universities and Colleges, Oil & Gas Industries, internet Individual users, NERC CIP Fulfillment of electric utility rules, Miners etc.
The cornerstone of this system is a distributed honeypot network with a globally-positioned sensor - miners. Miners will work by misleading hackers into thinking they are accessing legitimate and valuable systems. However, BitFence StingMiner software platform will record hacker actions, IP addresses, and all related pertinent information that will be used to hijack hackers. Information from these miners will be analyzed on centralized BitFence servers and also share them with BitFence customers.
Two or more honeypots on the network consist of HoneyNet. Typically, HoneyNet is used to monitor larger and / or more diverse networks where a single honeypot may not be sufficient for the network traffic experienced. Honey and Honeypots usually
implemented as part of a larger network intrusion detection system. BitFence "HoneyFarm" is a collection of honeypots analysis tools and centralized threats.
Some examples that show hacker malicious activity that HoneyNet can detect are:
- SQL Injection Attack
- Brute Force Attack
- OS Injection command
- Web Protection Efforts
vision
BitFence is providing zero-day threat intelligence solutions to protect people from hackers.BitFence will help companies and individual users to choose the appropriate security solutions to meet their needs. BitFence will help implement and integrate solutions with existing networking hardware and software with minimal modification or configuration changes. Once installed, the BitFence system will create landscape threat reports to meet compliance / regulatory requirements.
On the other hand, BitFence miners around the world will contribute as Eye & Ear to Intelligence BitFence Intelligence Network. Miners will use BitFence designed software called 'StingMiner' to attract hackers and forward threat information to BitFence. After a successful risk assessment and evaluation, the miners will be rewarded.
The capabilities of BitFence's zero-day cyber threat solution are as follows:
- Detect, Prevent and Respond Cyber security threats - Receive threat information from miners and assess threats - Deploy and update threat information to subscription system to reduce system with similar threats - therefore protect the system from zero-day attacks - Offer mining to cyber defense forces - BitFence miners with proprietary software - Integrated gift solution for BitFence miners after threats assessed based on risk evaluation - Integrate with existing network architecture with minimal configuration changes - Create customizable reports
Risk analysis and risk assessment should be done by utilizing the BitFence Threat Intelligence Machine which uses several patent pending methods including AI: - Fuzzy matching of threat footprints using weighted probabilistic matching methods - Support Vector Machines (SVM), Bayesian techniques and decision tree classifiers - Neural Networks, which continues to be trained with peer-reviewed and peer-reviewed data
BITFENCE TOKEN (HNY)
BitFence HNY Tokens is designed to provide a comprehensive economic model to enable cyber threat prevention system functionality. Payments for subscription services will only be made by utilizing HNY Tokens. In addition, all prizes for BitFence Miners will also be distributed with HNY Tokens.
The HNY Token is a token based on the standard contract of Ethereum ERC20 which is also applied in BitFence Business Logic.
HNY Token brings together Threat Protection and Detection Services into a single ecosystem with a complete life cycle
EVENING OF TOKEN GENERATION (TGE)
BitFence HNY is a utility token for which only currency will be used to purchase products and services on the BitFence Cyber Store.
NOTE: BITFENCE HNY IS NOT SECURITY. SUMMARY OF GENERATION OF THIS TOKEN GENERATION DOES NOT SUPPLY SUPPLY TO SELL OR MAINTENANCE MAINTENANCE TO BUY BITFENSE 'HNY' TOKEN AND IS PROVIDED ONLY FOR INFORMATION OBJECTIVES.
NOTE: SUMMARY OF STANDARD REFLECTION SUMMARY AND EXPECT BITFENSE WRT TOKEN MECHANICAL AND SALES OF HNY AND SUBJECT TO CHANGE ANYTHING.
NOTE: HNY TOKENS SHOULD BE CONSIDERED AS A DOLLARIS CURRENCY.
HNY is the ERC20 Token printed on request during TGE.
BitFence HNY Token is potential for sale. As part of this token sale, the permanent collection of Token HNY is potentially generated. No more HNY Token can be made in the future. After the token sale event is completed, a portion of the HNY Token will be allocated and awarded to BitFence Core Team Members as an incentive for the success of the BitFence platform, future operational needs, and reserve funds and backup spending
HNY Utility Token Sale (TGE)
Token Type
ERC20
Token Minting Model
No pre-mint, printed on purchase, immediate delivery
Structure of TGE
30 days pre-sales + 60 days sales
Payment methods accepted
ETH, BTC, LTC, DASH
Absolute Max Number of HNY printed
1,000,000,000
Maximum HNY is available during TGE
50% or 500,000,000
Soft Cap (in USD)
$ 1,000,000
Maximum Hard Cap (in USD)
$ 50,000,000
HNY Price Base
1 ETH = 6000 HNY
Volume Discount
Starting from 10 ETH = 10%, 20 ETH = 20%, etc.
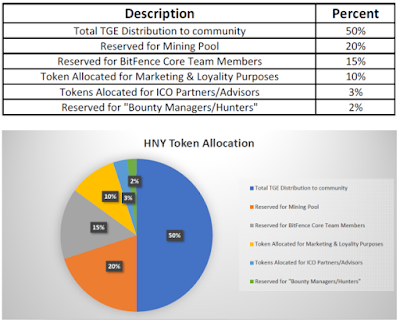
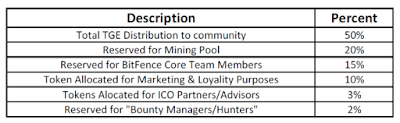
HNY TOKENS ALLOCATION
BitFence HNY Token is planned to be distributed as follows:
For more information click the link below:
Website: https://bitfence.io
Bitcointalk: https://bitcointalk.org/index.php?topic=3252856.0
Facebook: https://www.facebook.com
Twitter: https://twitter.com/BitFence_
Telegram: https://t.me/bitfence
Medium: https://medium.com/@bitfence
Github: https://github.com/BitFence
Youtube:
AUTHOR : meetdavis1157
profile: https://bitcointalk.org/index.php?action=profile;u=1564092
upvote for me please? https://steemit.com/news/@bible.com/6h36cq