The role of QUERLO concerning INTERNET PRIVACY, YAHOO! BREACHES and 6 of the most WANTED HACKERS in the history

The role of QUERLO concerning INTERNET PRIVACY, YAHOO! BREACHES and 6 of the most WANTED HACKERS in the history
I have been wanting to write about this topic but was hesitant to start I honestly don’t have concrete background and substantial knowledge on IT or computer/internet related concerns although the issue at bar can actually be learned so I did made a lot of research. And here I am, hope this blog will be something interesting in the eyes of everyone here.
Just like in the real world, people need to keep or protect their privacy such that intrusions or encroaching on someone’s confidentiality would mean or could be considered as criminal offense which is punishable by law.

Now the online world is not exempted even Steemit from any breach or destruction of privacy from those lawbreakers who are after of the money they could get from infringing to someone’s privacy that is why this issue is given utmost importance by the government such that violators would face trials and once proved to have been committed the crime will be punished in accordance with the existing law of the land.
The following crimes could be what a hacker will be facing if caught or charged to suspected culprit:
Conspiring with a hostile agency such as competing corporation or foreign countries to commit computer fraud and abuse, this also include economic spying, illegally accessing a computer for the purpose of commercial advantage and financial gain, theft of trade secrets, access device fraud, aggravated identity theft, wire fraud, etc. All these encompasses what we call a data breach.
What is DATA BREACH?
According to Wikipedia, a data breach is the intentional or unintentional release of secure or private/confidential information to an untrusted environment. Other terms for this phenomenon include unintentional information disclosure, data leak and also data spill. Incidents range from concerted attack by black hats associated with organized crime, political activist or national governments to careless disposal of used computer equipment or data storage media.
Wikipedia added that a data breach is a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorized to do so." Data breaches may involve financial information such as credit card or bank details, personal health information (PHI), personally identifiable information (PII), trade secrets of corporations or intellectual property. Most data breaches involve overexposed and vulnerable unstructured data – files, documents, and sensitive information.
Now private personalities, celebrities, business entities, and government agencies around the world are all vulnerable to such online vindictiveness and whose privacy might be intruded or violated anytime hackers wish.
According to Privacy Rights Clearinghouse, a non-profit consumer organization, a total of 227,052,199 individual records containing sensitive personal information were involved in security breaches in the United States alone between January 2005 and May 2008.

What is INTERNET PRIVACY?
According to Wikipedia, Internet privacy involves the right or mandate of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information pertaining to oneself via of the Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large scale computer sharing.
Privacy can entail either Personally Identifying Information (PII) or non-PII information such as a site visitor's behavior on a website. PII refers to any information that can be used to identify an individual. For example, age and physical address alone could identify who an individual is without explicitly disclosing their name, as these two factors are unique enough to typically identify a specific person. - Wikipedia

Yahoo! Data Breaches
Yahoo! for one is a victim of data breaches which occurred sometime in the year 2013 and 2014. These incidents considered as the largest discovered in the history of the Internet affected more than 1.5 billion accounts. However both incidents were made known to the public few years later which caused the internet service company to be criticized and even faced several lawsuits contending that Yahoo failed to provide sufficient protection of its users’ personal and confidential information.
Another data breach occurred on Yahoo! servers in August 2013; Yahoo! stated this was a separate breach from the late 2014 one and was conducted by an "unauthorized third party". Similar data as from the late 2014 breach had been taken from over 1 billion user accounts, including unencrypted security questions and answers. Yahoo! reported the breach on December 14, 2016, and forced all affected users to change passwords, and to re-enter any unencrypted security questions and answers to make them encrypted in the future. In February 2017, Yahoo! notified some users that data from the breach and forged cookies could have been used to access these accounts. This breach is now considered the largest known breach of its kind on the Internet. – Wikipedia

Due to the existence of data breaches, authorities have passed data breach notification laws, requiring a company that has been subject to a data breach to inform customers and take other steps to remediate possible injuries. I believe that relevant information being delivered promptly could help everyone protect their privacy and keep away from a more serious injuries.
I agree that it is a critical matter for companies to redefine their own strategies to collect data and establish a direct conversation with consumers. And this can be achieved with QUERLO chatbot technology.
Specific details of material taken include names, email addresses, telephone numbers, encrypted or unencrypted security questions and answers, dates of birth, and encrypted passwords. Further, Yahoo! reported that the late 2014 breach likely used manufactured web cookies to falsify login credentials, allowing hackers to gain access to any account without a password. – Wikipedia
There were a lot of speculations as to who were behind those breaches and what their intentions are. Yahoo! in their reports believes the breach that happened in 2014 was committed by "state-sponsored" hackers, although they did not name any country. Yahoo! also declared the hacker was no longer in their systems and that they are fully cooperating with law enforcement.
The November 2016 SEC filing noted that the company believed the data breach had been conducted through a cookie-based attack that allowed hackers to authenticate as any other user without their password. Yahoo! and its outside security analysts confirmed this was the method of intrusion in their
Wikipedia added that in February 2017, Yahoo! notified some users that data from the breach and forged cookies could have been used to access these accounts. This breach is now considered the largest known breach of its kind on the Internet.
Now I am wondering how Yahoo! reach out to its billions of users worldwide, I am Yahoo! user myself but I haven’t received any warning or information directly. I don’t even have idea about these breaches not until I read about this in on of the featured blogs on bitlanders. So that means the information drive may not be that effective or even successful.
Perhaps Yahoo! had made a series of announcements online but failed to reach most of their users. If you notice, both incidents were reported late and such late disclosure of the two major illegal intrusion to Yahoo! internet privacy caused them to be criticized and even face several legal complaints and until now still under investigation.
Now this made me think about the role of QUERLO, a chatbot with a human touch in the dissemination of relevant information that could help all Yahoo! users in protecting their individual accounts from possible damage.

What is QUERLO?
QUERLO is actually a program or a brand new technology owned by MTI USA a company established in New York in 1995, MTI USA is owned by a team of Italian technologists and the same company who owns bitLanders. In other words it is a chatbot which aims to collect sufficient data or allows data to be collected in an interactive way. It conducts a conversation via textual method although the conversation maybe via auditory also.
QUERLO’s chatbot technology is designed to:
- Establish a direct conversation and relationship with people
- Learn more about their passions and interests
- Educate them about the brand's or organization's initiatives Build, own and control a qualitative database and research - in Real Time
QUERLO provides a confidential one-on-one interactive conversation. And it is so amazing to note that QUERLO was able to launch more than 150 chatbots and were able to gather over 3 million pieces of “qualitative data” in just a span of 7 months.
QUERLO also had partnered with giant companies, participated in a worldwide campaign (Sustainable Development Goals with Unilever and GRBN), became major sponsor of some big events (2017 New York Open Judo Tournament). QUERLO clients includes HSBC, Tetra Pak, Phillip Morris, etc.
With QUERLO Yahoo! can reach out to their users and gather data in real time. This could help them discern and decide on things quickly and thereby providing them the ability or capacity to get rid of possible future damages. For more information please visit www.querlo.com
Why Yahoo! keep the information?
I for myself don’t know of the reason why Yahoo! kept the information with them not until after a year or two, but I find the importance or significance of QUERLO in such happening. QUERLO, a chatbot with a human touch delivers a state of the art technology in obtaining data from people around the world in just a very short time. QUERLO also serves as a perfect medium in disseminating essential information to people anywhere in the world.
So I strongly recommend that jurisdiction should advocate the use or application of QUERLO technology in order to spread relevant information quickly and accurately thus helping customers/users to take immediate action to protect themselves from possible injuries.
To know more about QUERLO you may watch the video below, it is a detailed "question and answer" way of explaining what does QUERLO really means and what it could offer to businesses or establishments especially those service oriented enterprise.
Top Most Wanted
Since I am discussing about Internet Privacy, Yahoo! Breaches and QUERLO I will also include in this article the top most wanted computer criminals in the U.S. history, since we are talking about hackers here, at least we will understand and be able to see the whole picture specially me who isn’t a computer wizard at all.
Perhaps looking up to the identities of those hackers would somehow help us comprehend why they do it and what benefit they could get in doing prohibited acts.
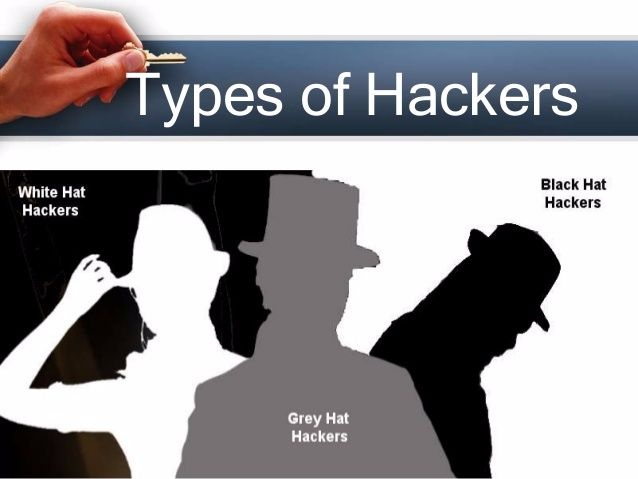
Not all hackers are bad
In my research I learned for the first time that not all hackers are bad. I mean there are hackers with good intention although from the word hackers alone, they still are violating some privacy. Anyhow it did sounds confusing but we will learn more as we go on with this blog. So continue reading.
The good hackers are called “white-hat hackers” the purpose of their action is to improve computer security. There are also hackers who are doing it just for the sake of fun, meaning they are having fun when they hack and they are called “gray-hat hackers”. But the malicious kind who intrude someone else privacy in exchange of money or simply with evil intentions, they’re called “black-hat hackers”. These black-hat hackers can cause serious harm and damage and one of their victims are the billions users of Yahoo! who were affected in the series of breaches that happened in the years 2013 and 2014.
At this point I would like to continue with the top 6 famous hackers what they did and what happen to them now. I believe that by being knowledgeable about these internet criminals we will be aware of what is happening over the internet and would know those possibilities that could still happen and thus provide us warnings, teaches us what to do, making us an instrument in passing information that could save someone from being hacked.
Let us check the 6 most wanted hackers in the history, what they did and what happen to them after committing the biggest mistake in their lives. Does such action made their lives better? Let's find out!
 )
)1. Kevin Mitnick
Number one in the list is Kevin Mitnick, an American computer security consultant, author and hacker, he was named as the “most wanted computer criminal in U.S. history”. Kevin Mitnick is very famous during that time such that his story inspired one writer, his story eventually become a movie entitled Track Down which was released in 2000.
What did he do?
Kevin Mitnick served a total of 6 years in prison, he was caught and convicted twice. He was convicted of hacking the Digital Equipment Corporation’s network, breaching the National Defense warning system and stealing corporate secrets.
Where is he now?
After fully serving 6 years, Kevin Mitnick became a consultant and public speaker for computer security. Currently he runs Mitnick Security Consulting, LLC.
2. Jonathan James
Second is Jonathan James. Jonathan commonly known as “comrade” is a native of South Florida and was only 15 years old when he committed his first offense. This American hacker was the first juvenile imprisoned for cybercrime in the United States.
What did he do?
Jonathan James was able to make a series of intrusions into various systems and the most renowned is that he was able to hack NASA’s network which caused damaged equaling to $1.7 million. Because of that NASA had to shut down its network for three weeks while they investigated the breach, which cost them an additional $41,000 just to check and fix their system.
Where is he now?
The story of James is somewhat tragic, he was caged even if he was still a minor and later in 2008 he committed suicide. According to the reports, he kill himself (using a gun) because he fears that he might be convicted with more crimes that he didn’t commit.
3. Albert Gonzalez
Third is Albert Gonzalez. He was born in America in 1981. Albert is a computer hacker who was accused of being the leader of the combined credit card theft and reselling of more than 170 million card and atm numbers. Their group was called “ShadowCrew”.
According to Wikipedia, Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP Spoofing) attacks which allowed him to steal computer data from internal corporate networks.
What did he do?
Albert Gonzalez spearheaded the stealing and selling of credit card numbers. He collected more than 170 million credit card and ATM card numbers in just 2 years. Their group also fabricated fraudulent passports, health insurance cards, and birth certificates for identity theft crimes.
Where is he now?
Albert Gonzalez was penalized to prison for 20 years and is scheduled for release in 2025. 8 more years and he can do the crime again if he wants to (LOL).
4. Kevin Poulsen
Fourth in the list is “Dark Dante” with legal name Kevin Poulsen. He was the first American to be released from prison (after 5 years) with a court sentence that barred him from using computers and the internet for 3 years after his prison sentence.
What did he do?
One of the things that he did was taking over a radio station’s phone lines and fixed himself as the winning caller for a brand new Porsche. He also hacked federal systems and stole wiretap information. Where is he now? After service his sentence he work as a journalist and later became a senior editor for Wired News. In 2006, he was able to help law enforcement to identify sex offenders on MySpace.
In October 2006, Poulsen released information detailing his successful search for registered sex offenders using MySpace to solicit sex from children. His work identified 744 registered people with MySpace profiles and led to the arrest of one, Andrew Lubrano. - Wikipedia
5. Gary McKinnon
The fifth famous hacker is Gary McKinnon, known as “Solo”. He allegedly coordinated what would become the largest military computer hack of all time.
What did he do?
From February 2001 to March 2002, McKinnon was able to unlawfully accessed 97 computers that belong to the U.S. Armed Forces and NASA. According to authorities, Solo deleted several critical files and made over 300 computers inoperable. This illegal action resulted to more than $700,000 in damages.
Where is he now?
McKinnon remained at liberty without restriction for three years until June 2005 (until after the UK enacted the Extradition Act 2003, which implemented the 2003 extradition treaty with the United States wherein the United States did not need to provide contestable evidence), when he became subject to bail conditions including a requirement to sign in at his local police station every evening and to remain at his home address at night. If extradited to the U.S. and charged, McKinnon would face up to 70 years in jail. He has expressed fears that he could be sent to Guantanamo Bay. - Wikipedia
6. Robert Tappan Morris
The sixth in line is Robert Tappan Morris. He was the son of Robert Morris, a computer scientist at Bell Labs and later the NSA. Morris is credited as the creator of the world’s first known computer worm.
What did he do?
While still a student at Cornell University he created the Morris Worm. The program was intended to gauge the size of the internet, but it had a flaw: computers could be infected multiple times, and each infection caused the computer to slow down even more. It rendered over 6,000 computers unusable. - Wikipedia
Where is he now?
Morris was found to have violated the Computer Fraud and Abuse Act in 1989. His verdict was three years of probation, 400 hours of community service, and a $10,050 fine. He is now a professor at the Massachusetts Institute of Technology.
I think I got to end up here for my blog is a bit long already. I hope you find this blog thought-provoking as I was really delighted to know about these internet privacy violators. Making me think of hacking a major bank in the Philippines and take all their money haha. I’m just joking.
Photo Credits:
https://www.slideshare.net
https://www.consumeraffairs.com
http://fortune.com
https://secnews.gr
https://nextcloud.com
https://bustos.house.gov
http://www.cityam.com
https://thenextweb.com
https://www.linkedin.com
Video Credit:
Sky High Advertising via YouTube.com
Credit to my inspiration:
To my mentors:
@antonette
@iwrite
@lebron2016
@purpledaisy57
@bobiecayao
@bloghound
@lynrogan
To my gif designer:
*REFERENCES:
Wikipedia
My own blogs on bitlanders (http://www.bitlanders.com/TRB)
Yahoo News
.gif)
Data breach and IT security is the number one problem nowadays
WOW!! Do you have any update about Onel De Guzman?. hehehe
Please try to add credit to and source url for images. You have put much effort and that will crown it and give curators more freedom to curate. I have tips for photos in my last post too.
Thank you so much @surpassinggoogle have to check your post to be able to provide correct credit and source url for the images I used I thought what I put at the bottom is enough.
You are welcome. Yes, just to be on the safe side and to have more people voting freely
I think so too man. Thank you for telling him
Resteemed your article. This article was resteemed because you are part of the New Steemians project. You can learn more about it here: https://steemit.com/introduceyourself/@gaman/new-steemians-project-launch
This post recieved an upvote from minnowpond. If you would like to recieve upvotes from minnowponds team on all your posts, simply FOLLOW @minnowpond.
@royrodgers has voted on behalf of @minnowpond. If you would like to recieve upvotes from minnowponds team on all your posts, simply FOLLOW @minnowpond.
As a follower of @followforupvotes this post has been randomly selected and upvoted! Enjoy your upvote and have a great day!
So much IT info. I didn't know all about these. Thanks, kuya!
well done long888, once again!
@originalworks
The @OriginalWorks bot has determined this post by @long888 to be original material and upvoted it!
To call @OriginalWorks, simply reply to any post with @originalworks or !originalworks in your message!
To enter this post into the daily RESTEEM contest, upvote this comment! The user with the most upvotes on their @OriginalWorks comment will win!
For more information, Click Here! || Click here to participate in the @OriginalWorks sponsored writing contest(125 SBD in prizes)!!!
Special thanks to @reggaemuffin for being a supporter! Vote him as a witness to help make Steemit a better place!